- Product
Infrastructure
Applications
Logs
Security
Digital Experience
Software Delivery
Service Management
AI
Platform Capabilities
- Customers
- Pricing
- Solutions
- Financial Services
- Manufacturing & Logistics
- Healthcare/Life Sciences
- Retail/E-Commerce
- Government
- Education
- Media & Entertainment
- Technology
- Gaming
- Amazon Web Services Monitoring
- Azure Monitoring
- Google Cloud Monitoring
- Oracle Cloud Monitoring
- Kubernetes Monitoring
- Red Hat OpenShift
- Pivotal Platform
- OpenAI
- SAP Monitoring
- OpenTelemetry
- Application Security
- Cloud Migration
- Monitoring Consolidation
- Unified Commerce Monitoring
- SOAR
- DevOps
- Shift-Left Testing
- Digital Experience Monitoring
- Security Analytics
- Compliance for CIS Benchmarks
- Hybrid Cloud Monitoring
- IoT Monitoring
- Real-Time BI
- On-Premises Monitoring
- Log Analysis & Correlation
- CNAPP
Industry
Technology
Use Case
- About
- Blog
- Docs
- Login
- Get Started
Detect security threats with the monitoring data you already collect
Datadog’s Cloud SIEM provides out-of-the-box threat detection and security analytics solutions based on the full set of monitoring data from its more than 900 turn-key, vendor-supported integrations. Cloud SIEM is part of the Datadog Cloud Security Platform, which protects an organization’s production environment with a full-stack offering providing threat detection, posture management, workload security, and application security. The Datadog-supported integration set includes key technologies like AWS CloudTrail, Okta, and G Suite, giving you end-to-end security visibility and deep context around possible threats. This insight is provided by leveraging all of the metrics, logs, traces, and synthetics tests that organizations are already collecting with Datadog. Cloud SIEM is fully integrated with all of Datadog’s application and infrastructure monitoring products. This allows any user to seamlessly pivot from a potential threat to associated monitoring data to quickly triage security alerts using a single pane of glass.
At Instacart, we care about unauthorized access, and with Datadog's Cloud SIEM we've been able to track down malicious third parties and protect our users more quickly.

Blaine Schanfeldt
Site Reliability Engineer, Instacart
Full, cost-effective log ingestion and analysis
Traditional security analytics tools require that all ingested data also be retained in hot storage for analytics and alerting. This pricing structure becomes prohibitively expensive, ultimately leading to applications and environments that are not fully covered. Datadog’s Cloud SIEM incorporates Datadog’s Logging without Limits™ pricing structure, which separates log ingestion and indexing. Thus, Datadog ingests every log at a low cost and analyzes them in real time for malicious and anomalous patterns. Datadog users then choose to index and be charged only for the logs needed for investigations. All logs are compressed and archived at low cost in long-term cold storage and can be “re-indexed” at any time in the future with Log Rehydration™, for example to support compliance audits or forensics. For security teams, this provides full security analytics coverage across all applications and environments without the performance or cost-related concerns of retaining all log data in hot storage.
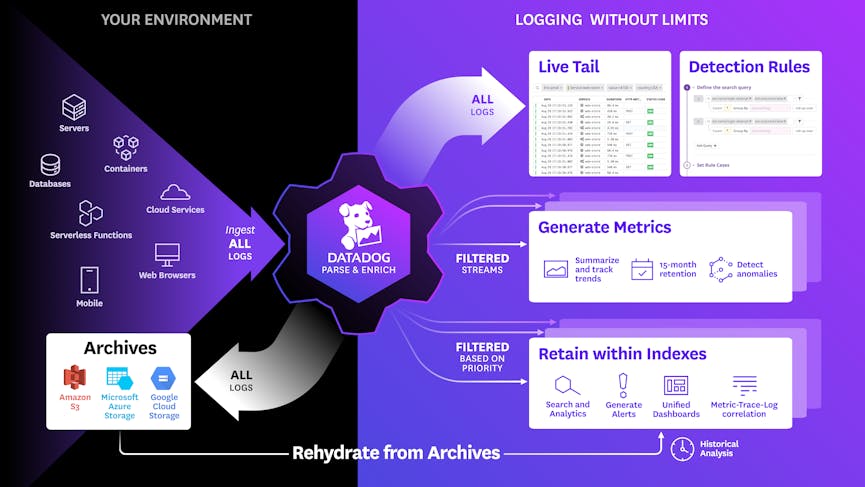
Real-time, out-of-the-box security analytics
Datadog's Detection Rules provide a powerful way to automatically monitor and detect security threats across any environment in real time. Use configurable out-of-the-box rules—mapped to the MITRE ATT&CK™ framework—to track common attacker techniques, such as a VM enumerating all storage buckets in your account; Datadog Cloud SIEM will provide threat detection immediately after installation. Engineers can also easily write their own sophisticated rules without having to learn a proprietary language: for example, engineers can create rules that look for possible account takeovers, root user activity, and more by using a simple but flexible editor. Datadog applies Detection Rules to the full stream of log data as it’s received, surfacing threats as soon as they occur.
Unified visibility for faster triage and cross-team investigation
Security threats in cloud-native environments move fast, which means that security teams need to have the same visibility into their infrastructure, network, and applications as developers and operations. With Datadog Cloud SIEM, all engineering teams now have end-to-end security analytics coverage of their environment from a single, unified pane of glass. And, because everyone is using a single platform, when a threat is detected, security teams can quickly and easily loop in the relevant engineers and share related observability data using the same monitoring system they are already familiar with, leading to faster investigations.
Featured content

video
Instacart: resolving development, operations and security issues with Datadog's unified platform


