Candace Shamieh

Derek Brown

Matt Mills
As Windows organizations migrate toward cloud-based environments, they often lose context of their full stack. In addition to securing their on-premises servers, they now need to deal with virtual servers, managed services, and platform-as-a-service offerings. Cloud-based resources require organizations to relinquish control over physical infrastructure and limit their access to underlying operating systems. This new dynamic is especially foreign to administrators who have long benefitted from direct access when something goes wrong in their environment. A modernized landscape can lead to insufficient visibility into the attack surface, an inability to detect threats, and ineffective risk management.
To mitigate those risks, Datadog Cloud Security for Windows provides complete visibility into the security posture of all cloud-native and on-premises workloads via real-time threat detections. Cloud Security for Windows enables you to detect security threats, respond to incidents promptly, optimize resource utilization, and maintain your system’s overall integrity and reliability.
In this post, we’ll discuss how you can use Cloud Security for Windows to:
- Monitor suspicious activity on your Windows servers
- Contextualize security signals with observability data for quick remediation
Monitor suspicious activity on your Windows servers
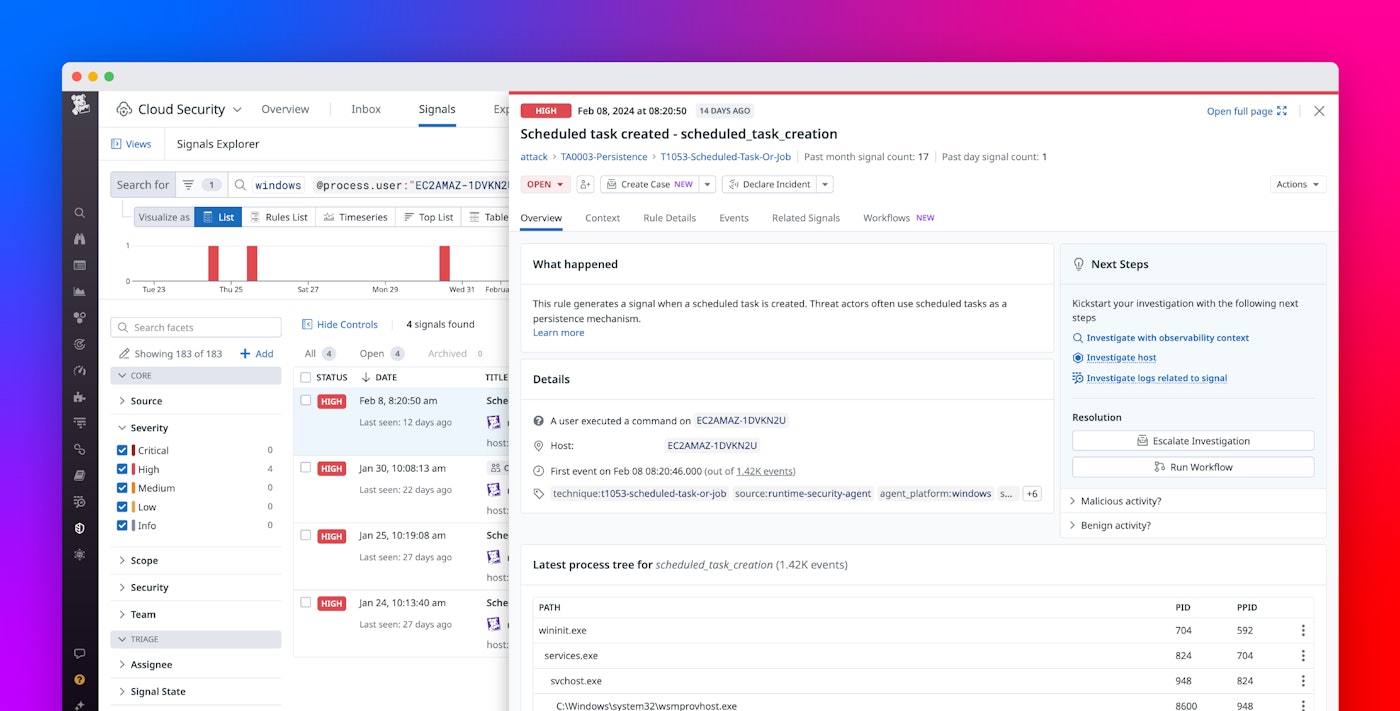
Cloud Security for Windows enables you to quickly identify suspicious process, network, file, and registry activity, such as an unauthorized user running a known penetration testing tool or the appearance of a new scheduled task that will execute outside of regular maintenance hours.
When Cloud Security detects a threat, it will generate a security signal that contains the steps or commands that triggered the threat, the impacted host name and location, the process or user that initiated the threat, and more. You can also view the service, applications, network, and teams that interact with the impacted host. This information will help you decide whether you need to initiate an investigation or deem the security signal as benign.
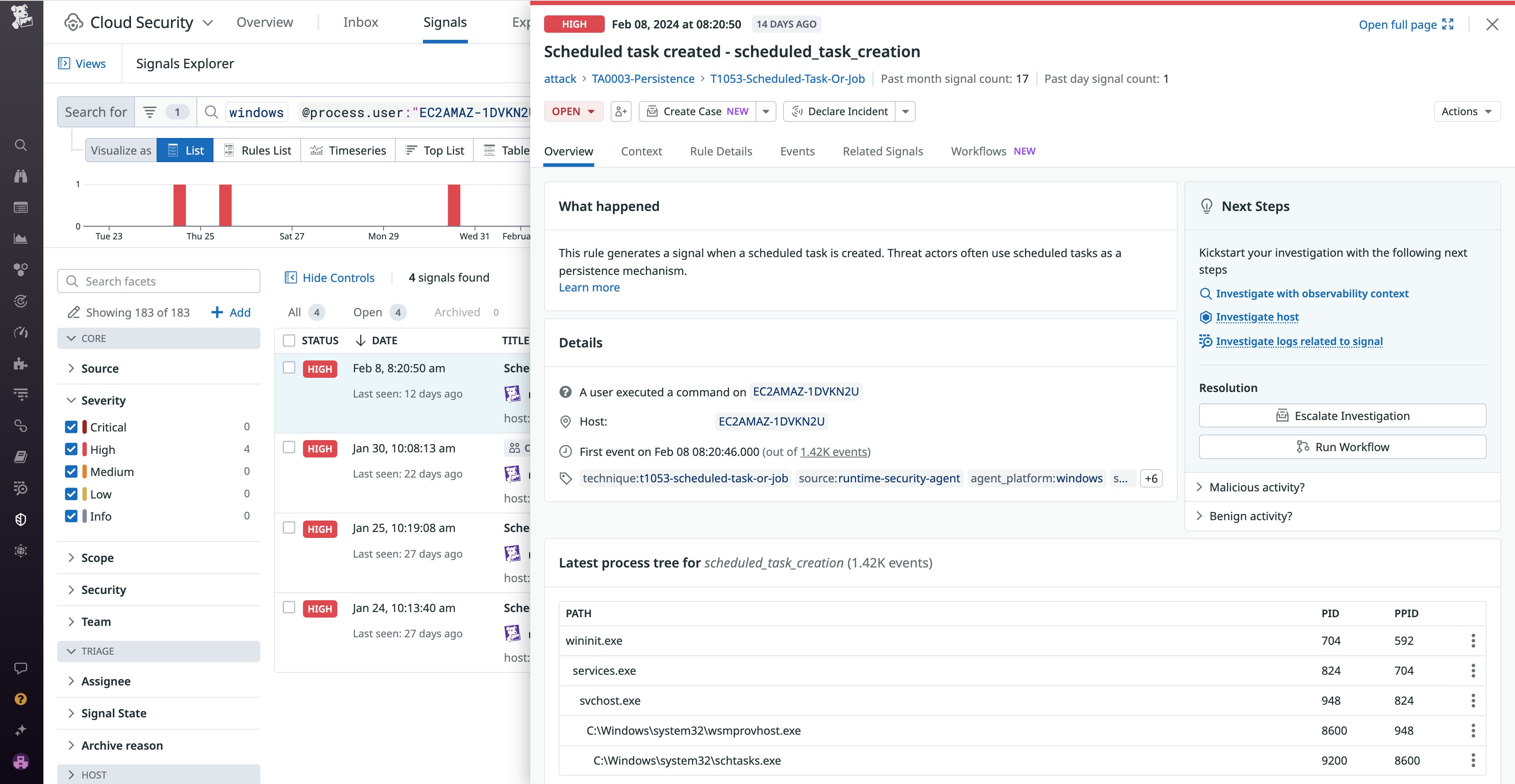
For example, let’s say you’re a systems administrator responsible for managing a network of Windows hosts in your organization. Because your organization has notification rules based on specific security signal parameters, you receive a Slack notification from Cloud Security indicating that a new scheduled task was created on one of your hosts. The task aims to execute a script outside of regular business hours. You know that a scheduled task is one of the most common persistence methods used by malware, so you investigate. You’re unable to verify if the account is an authorized user from Microsoft Entra ID or your organization’s on-premises domain. After seeing that this is a unique task attached to a suspicious user, you isolate the targeted host from your network and follow your organization’s internal protocols to escalate the issue.
Contextualize security signals with observability data for quick remediation
By enabling Cloud Security for Windows, you can leverage the Datadog platform to see and prioritize threats, investigate, and accelerate mean time to resolution. Within each security signal, Datadog will automatically pull in the relevant observability data so you can view the threat in its full context. As a result, you can easily correlate the security signal’s information with the relevant host dashboard, infrastructure map, metrics and logs, and more. This observability context enables you to quickly pinpoint the signal’s root cause and resolve the issue. You can also create cases, declare incidents, or integrate security signals with Slack or PagerDuty for convenient collaboration.
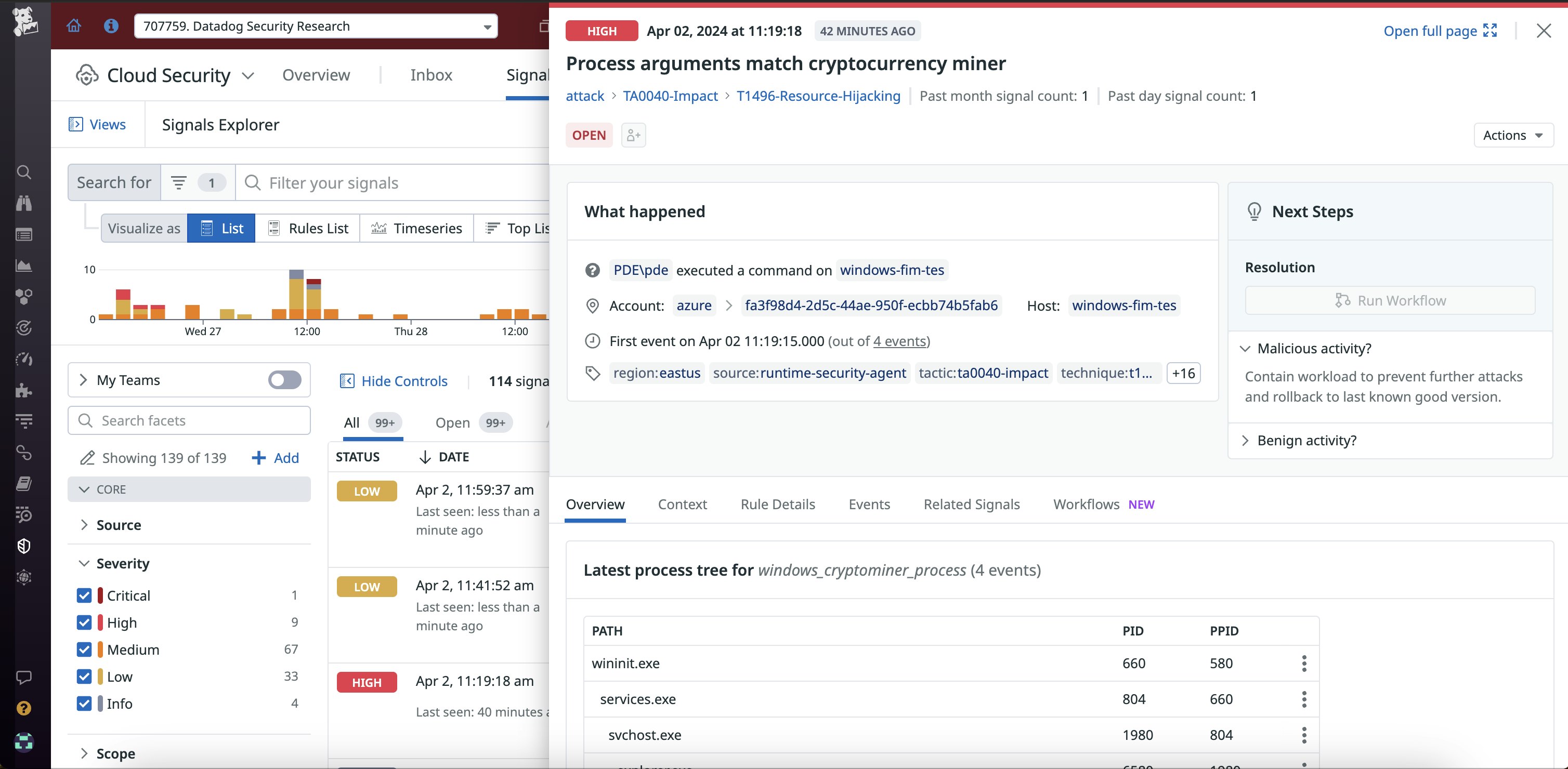
Say you’re a security analyst and receive an alert from Cloud Security about potential cryptomining activity. You view the security signal, which includes process command line arguments consistent with known cryptominers. This prompts you to investigate further by examining observability data. As you review metrics, you notice that CPU utilization spiked at the same time that the cryptomining event was detected. You examine the list of running processes on the host and confirm that several unapproved, suspicious processes are consuming CPU resources. You terminate the malicious processes and proceed to review the process tree, logs, and related security signals. This helps you identify the attack’s initial entry vector so your organization can prevent future incidents.
Secure your Windows workloads today
Datadog Cloud Security for Windows lets you monitor suspicious activity on your Windows servers in real time. With visibility into your Windows workloads, you can investigate threats and contextualize them alongside observability data to remediate issues quickly. Check out our documentation for more information about getting started with Cloud Security.
If you don’t already have a Datadog account, sign up for a free 14-day trial today.