Danila Ivanov
Threat detection and runtime posture monitoring are related but different jobs. Security teams already rely on Datadog Workload Protection to detect threats in real time across hosts and containers. But the actions that lead to those detections (file manipulation, process execution, network calls, or kernel activity) can be indicative of compromise or simply of risky behavior—like running compilers in production containers. When threat detections and broader runtime behaviors are handled in the same workflow, teams must make prioritization decisions across different levels of urgency. Some behaviors are inherently risky and worth fixing, even when they don’t indicate an active compromise.
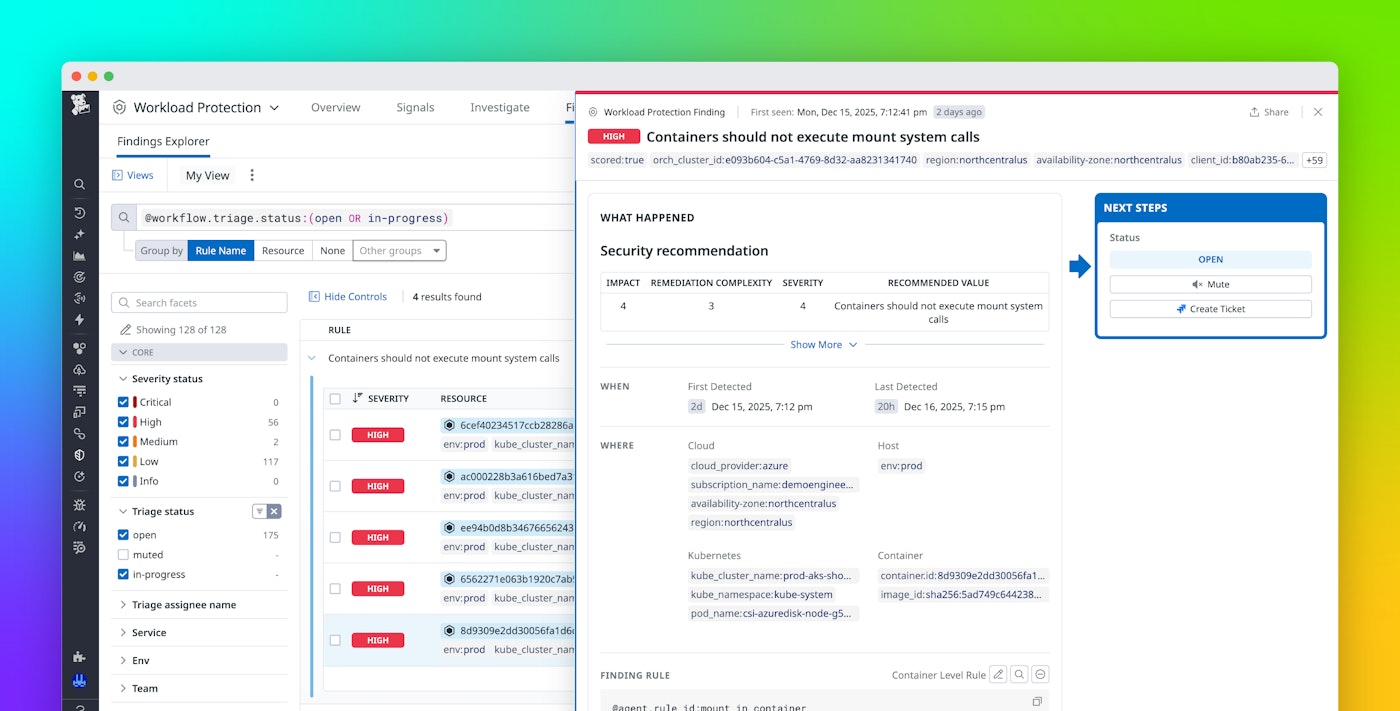
Workload Protection Findings, now available in Preview, gives runtime posture monitoring its own dedicated space in Datadog. The Findings feature surfaces risky but not necessarily malicious behaviors in a separate view, tracks them across hosts and containers, and turns them into actionable remediation work through Datadog Case Management. It helps your teams stay focused during incident response while they continue to address underlying risk.
In this post, we’ll show how Findings can help you:
- Separate posture findings from threat signals
- Gain visibility into issues at the host and container level
- Resolve issues directly from Case Management
Separate posture findings from threat signals
The Datadog Agent collects rich runtime telemetry data, including events tied to unsafe behaviors such as running compilers in production or using legacy metadata services. When these behaviors overlap with activity indicative of a compromise, they contribute to threat detections. In many other cases, however, this telemetry data reflects broader runtime risk and can be systematically used for posture improvement. Before Findings, teams had to repeatedly assess urgency and prioritize across these different concerns.
Findings collects unsafe runtime behaviors and groups them into a separate posture view. This process retains your underlying threat detection coverage while surfacing how to harden your environment and improve your security posture. Teams no longer need to assess each occurrence of unsafe behavior as benign or malicious, and they can address and resolve these posture issues in a dedicated workflow.
Gain visibility into issues at the host and container level
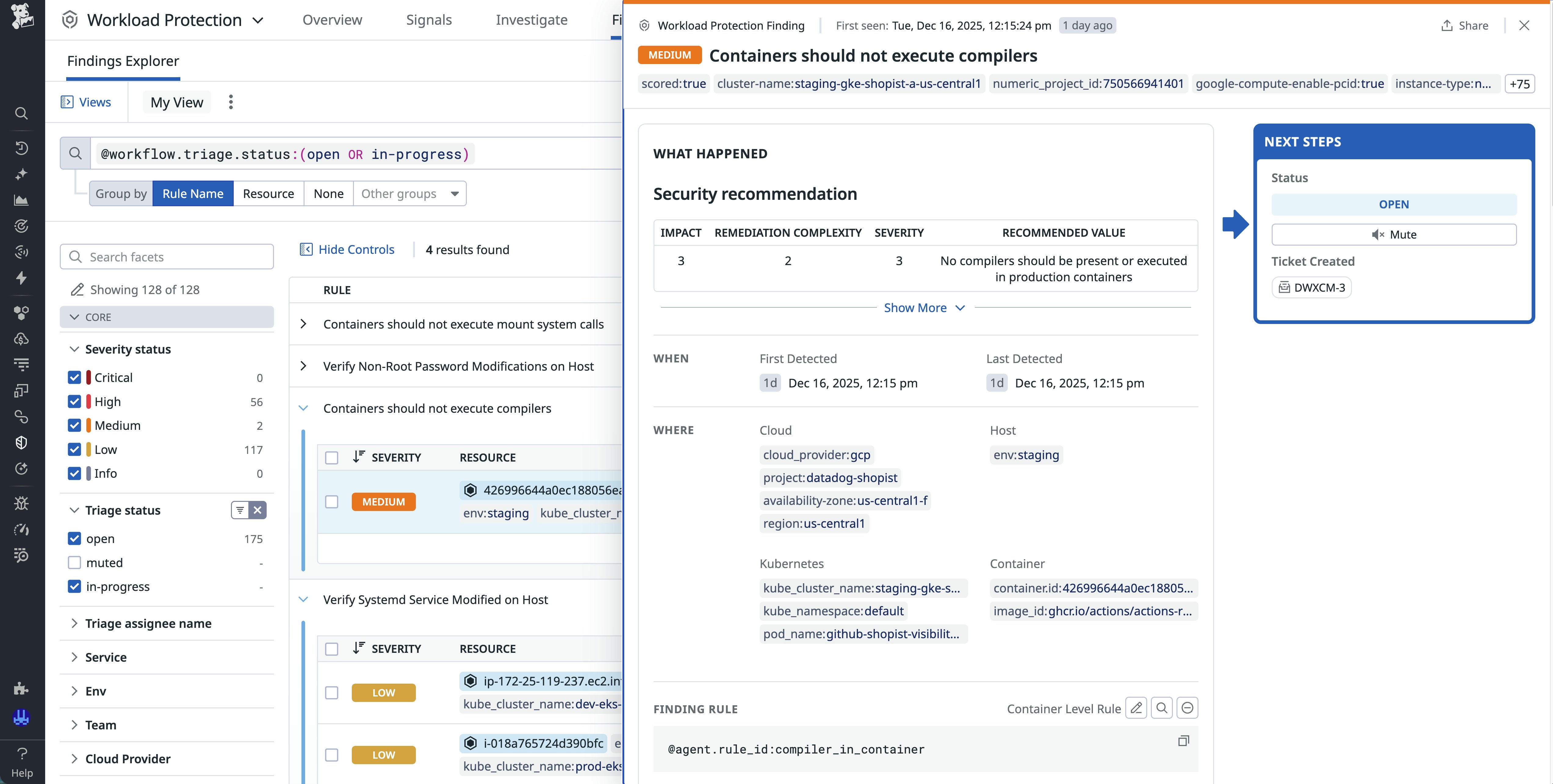
After these behaviors are classified as posture issues, Findings helps you understand where they originate and which resources are affected. Many posture issues, such as outdated Linux control groups, originate on the node. Others, such as package manager activity in production images or interactive remote shells in long-lived pods, appear only inside containers. Traditional scanning tools often miss part of the picture because they focus on build-time or periodic scans, but Findings uses runtime data to connect these behaviors to the hosts, containers, pods, and services involved.
For example, consider a case where Workload Protection detects compiler usage in production containers. Production images should include prebuilt binaries and run as immutable artifacts, so build systems like Make or compilers such as GCC, G++, and Clang should not be present at runtime. When they are, it can indicate a compromise, a misconfigured image, or drift from container best practices.
With Findings, each invocation of a compiler binary becomes a posture issue associated with the exact container, pod, or service where it occurred. The affected container remains flagged until it stops emitting compiler-related events for a defined period. Because Findings tracks both host-level and container-level signals, you can see posture issues across your environment in a single view rather than scattered through detection history.
Resolve issues directly from Case Management
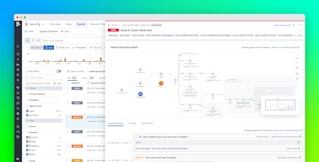
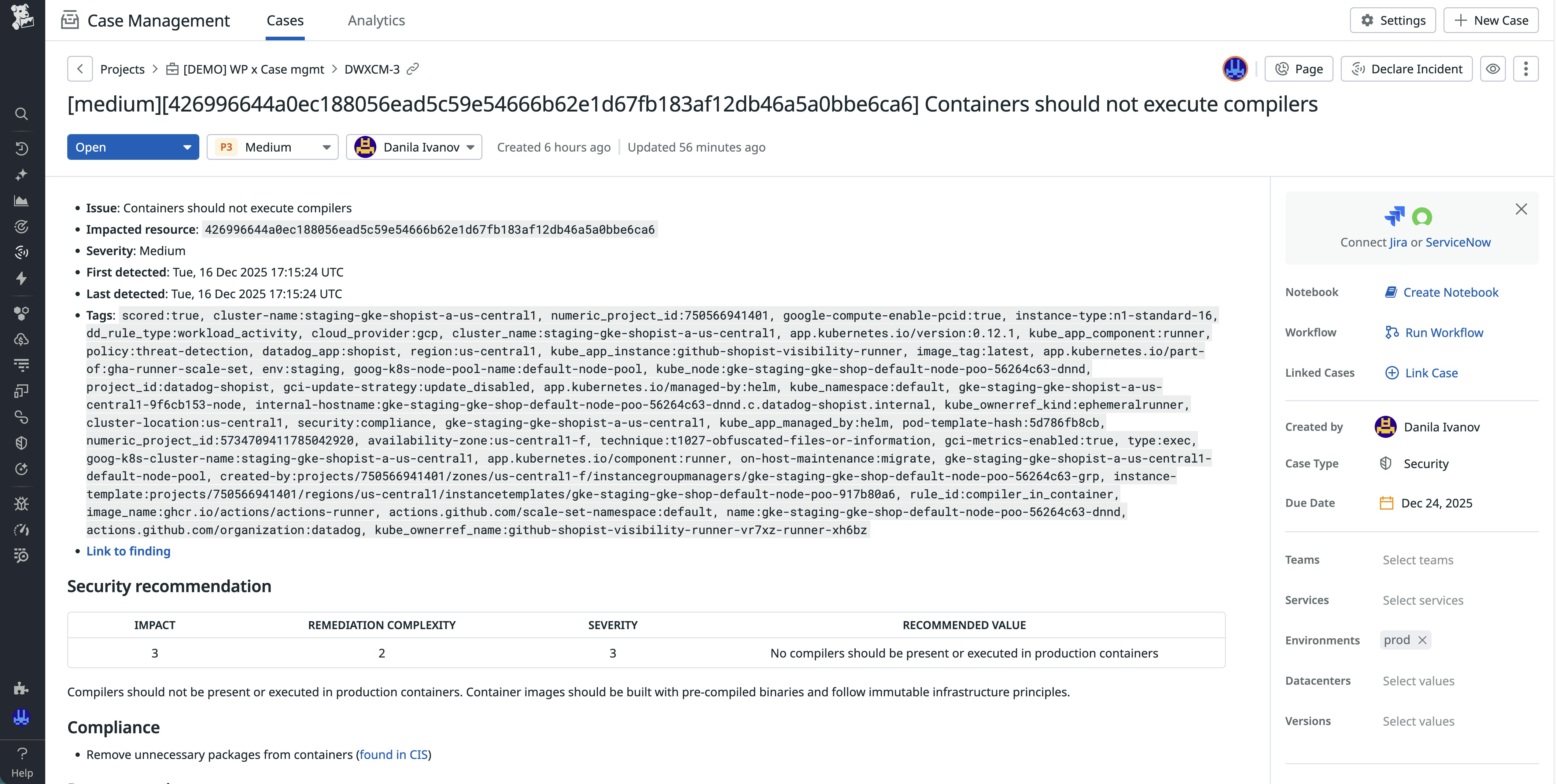
Findings integrates directly with Case Management to turn posture issues into actionable work. From a finding, you can create a case, assign it to the right team, and document remediation steps without leaving Datadog. This process establishes a clear, repeatable life cycle from detection and triage through remediation and verification. Security, SRE, and platform teams can collaborate in a shared workflow built on runtime evidence rather than separate ticketing systems.
If we revisit our example of the production containers where compiler usage is occurring, you don’t need to evaluate each individual event. You can treat the behavior as universally unsafe and work toward eliminating it. When the case is resolved and the affected containers are rebuilt, the finding clears after a quiet period confirms that the fix persisted.
Case Management also provides an audit-ready record of posture work. Each case includes timestamps, owners, and remediation notes, making it straightforward to demonstrate to auditors and internal stakeholders that runtime issues were identified, investigated, and resolved.
Bring runtime posture and threat detection into focus
Workload Protection Findings gives threat detection and runtime posture monitoring their own workflows, so teams can stay focused during incident response while still addressing underlying risk. By treating unsafe behaviors as posture issues to fix and track, teams avoid suppressing rules and creating visibility gaps that increase risk. With its integration with Case Management, Findings supports a complete posture life cycle from detection to remediation to verification and gives teams shared visibility across hosts and containers.
To get started with Findings, join the Preview by reaching out to your Datadog representative or by requesting access through the banner at the top of the Workload Protection Overview page. To learn more about Workload Protection, check out the Workload Protection documentation.
If you don’t already have a Datadog account, you can sign up for a 14-day free trial.