Gorka Vicente
Security teams are responsible for finding and remediating vulnerable dependencies within applications that are built from large ecosystems of frameworks, SDKs, and utilities. What makes this task especially challenging is that these dependencies can pull in dozens or even hundreds of transitive dependencies through complex dependency chains. Even when scanners identify what’s vulnerable, teams still often lack the information they need about the dependency chain to safely address the issue.
Datadog Software Composition Analysis (SCA), part of Datadog Code Security, helps teams move from finding transitive vulnerabilities to fixing them. It identifies the dependency chain that introduced the vulnerable library and recommends root library upgrades that safely remove the vulnerable dependency.
Why transitive vulnerabilities are so hard to fix
When you lack visibility into dependency trees, remediating transitive dependencies is a challenging and error-prone task. For example, a scanner might identify log4j in a library without clearly naming the direct dependency that introduced it. This means that teams typically lack key contextual information such as:
- Which dependency introduced it into my repo?
- What’s the right upgrade to remove it without breaking the build?
- If I upgrade the root dependency, what else will that fix or change?
Without this information, it’s also harder to keep dependency trees updated. Datadog’s 2025 State of DevSecOps found that the median dependency was 215 days behind its latest major version. When dependencies grow outdated in this way, vulnerabilities are more likely to surface.
How Datadog SCA connects transitive vulnerabilities to root dependencies
Datadog SCA analyzes your dependency graph so that when a vulnerability is detected in a transitive library, you can see the contextual information you need to take action. It surfaces the vulnerable library and version, the root library that introduced it, and where it was detected in your codebase, including the repo and file. It also provides a recommended fix, which is often an upgrade to the root dependency that removes the vulnerable transitive library.
This functionality builds on Datadog’s broader SCA approach, which combines visibility across code with runtime context to help teams prioritize and remediate vulnerabilities.
Walkthrough: From Log4Shell detection to a root dependency upgrade
To see how this works in practice, let’s walk through a Log4Shell remediation example in the Datadog platform by following the path from detection to a specific, actionable upgrade.
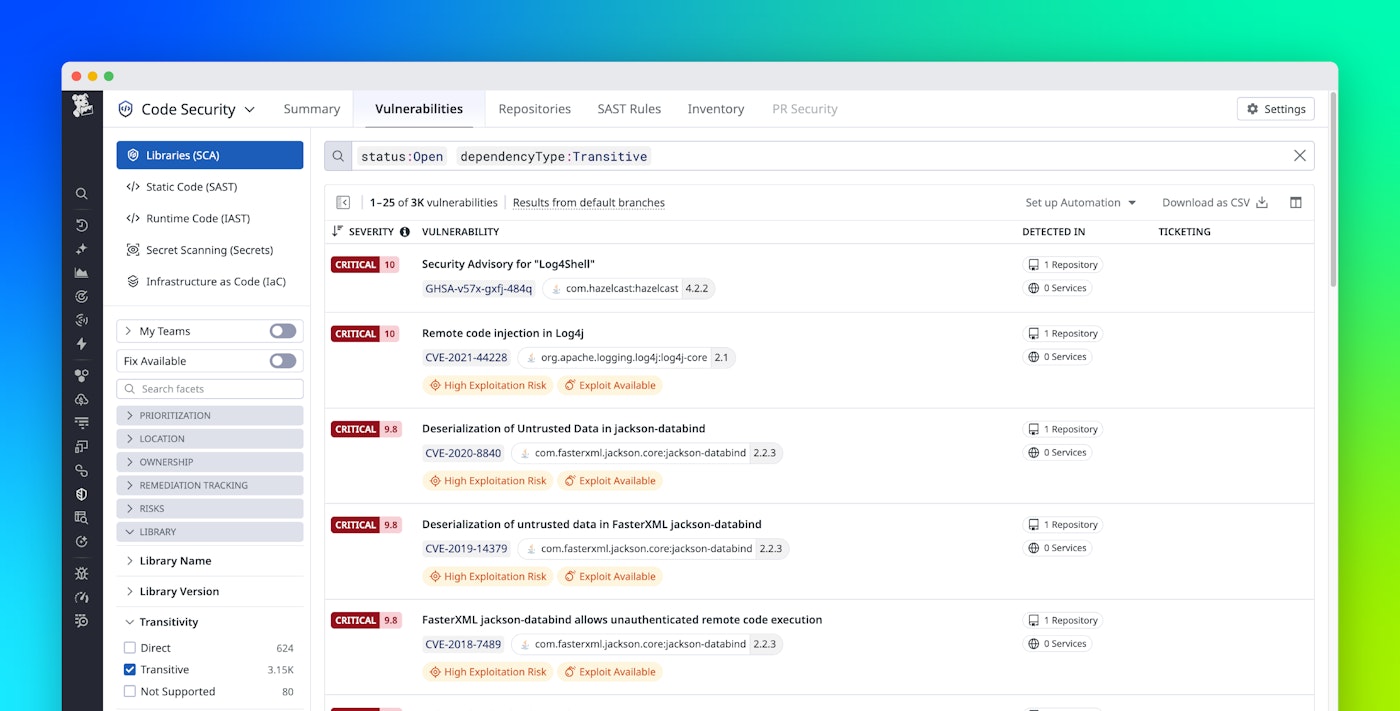
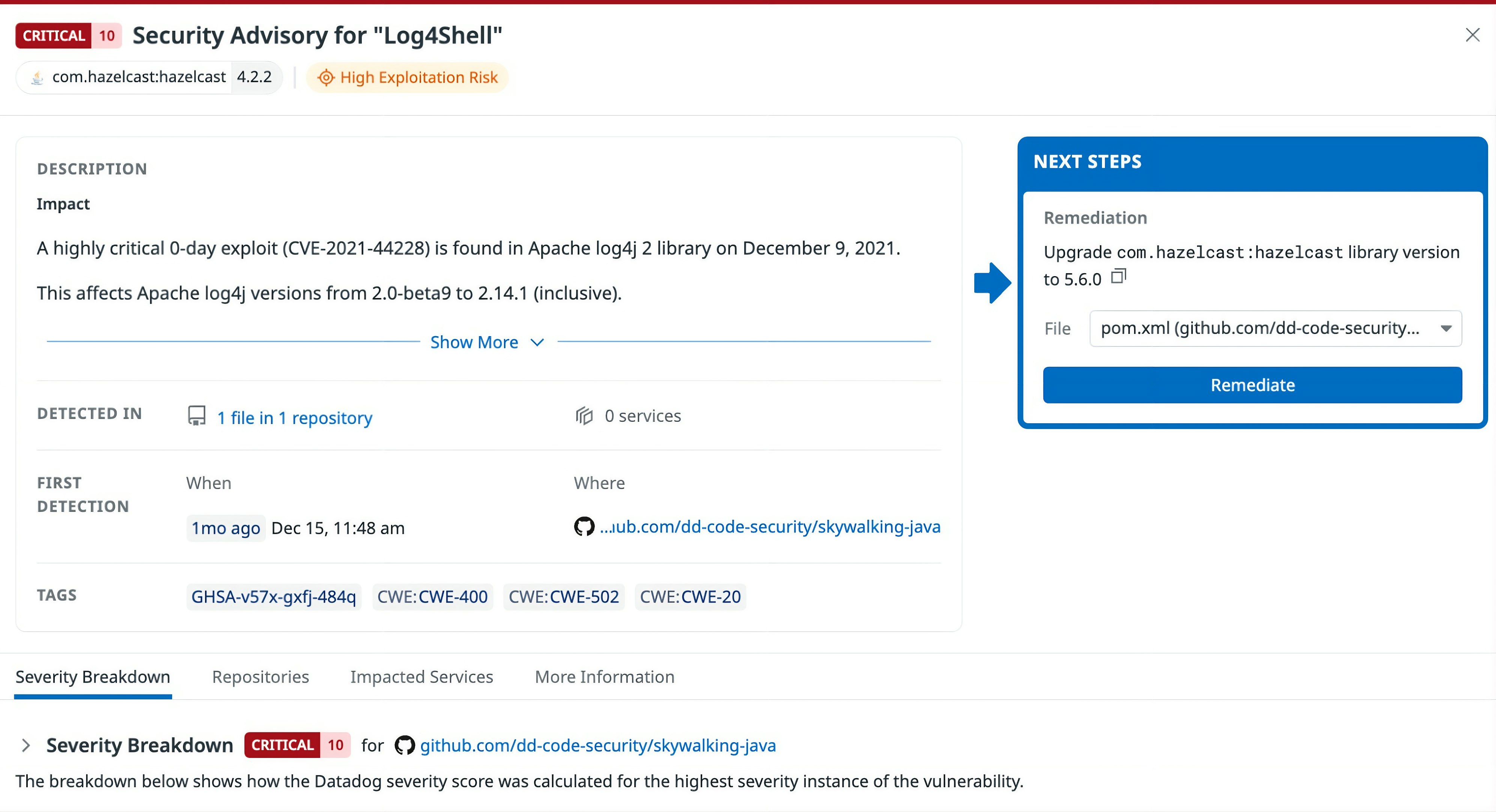
Step 1: Review the detected vulnerability and remediation guidance
When Datadog detects a vulnerability such as Log4Shell, the vulnerability details view in Code Security provides full context about the affected dependency along with a “Next Steps” section. This window gives you remediation steps for upgrading the relevant dependency, pointing directly to the file where it is declared.
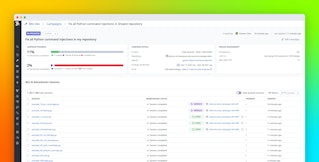
Step 2: Identify the root library that introduced the vulnerable transitive dependency
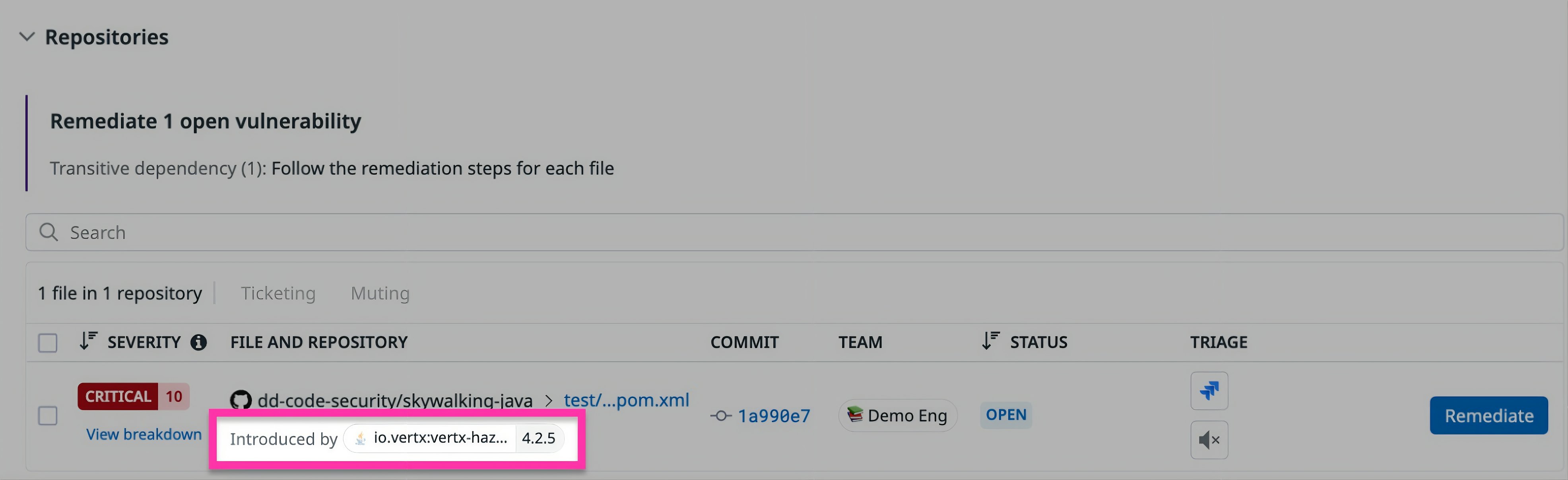
The next step is connecting the vulnerable package to the dependency that introduced it. In the repository-level breakdown, SCA displays an “Introduced by” field that shows the root library responsible for pulling in the vulnerable transitive dependency.
Step 3: Open guided remediation to see exactly what to update
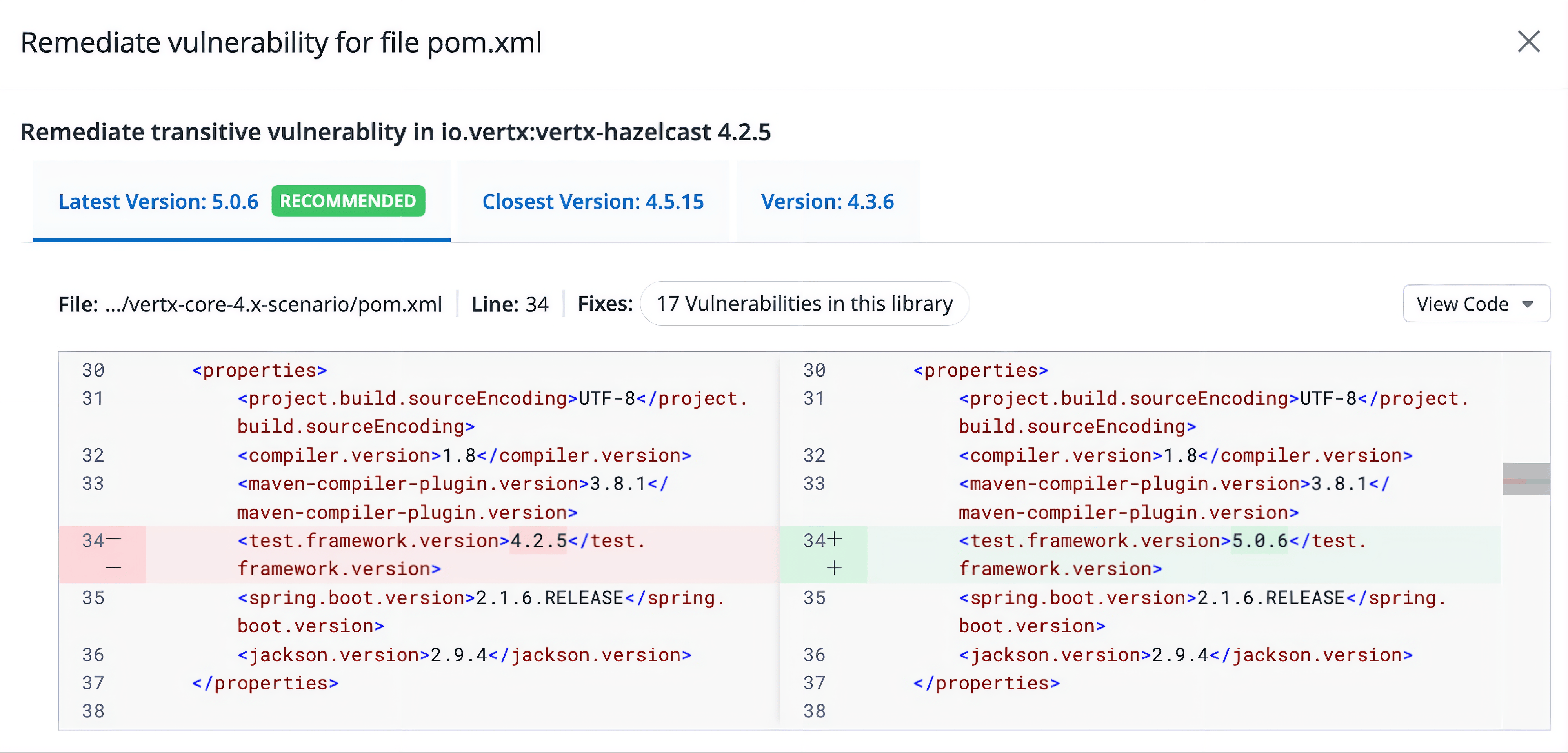
From there, engineers can move directly into guided remediation. When they click the Remediate button, a remediation view opens. This view includes a recommended version upgrade path, alternative upgrade options, and the exact file and line where the dependency should be updated. A side-by-side diff shows the proposed change so that the fix can be applied quickly and reviewed with confidence. This is especially helpful in Maven or Gradle projects, where version alignment across related components can make dependency changes harder than they appear.
Step 4: Review the broader impact of upgrading the root library
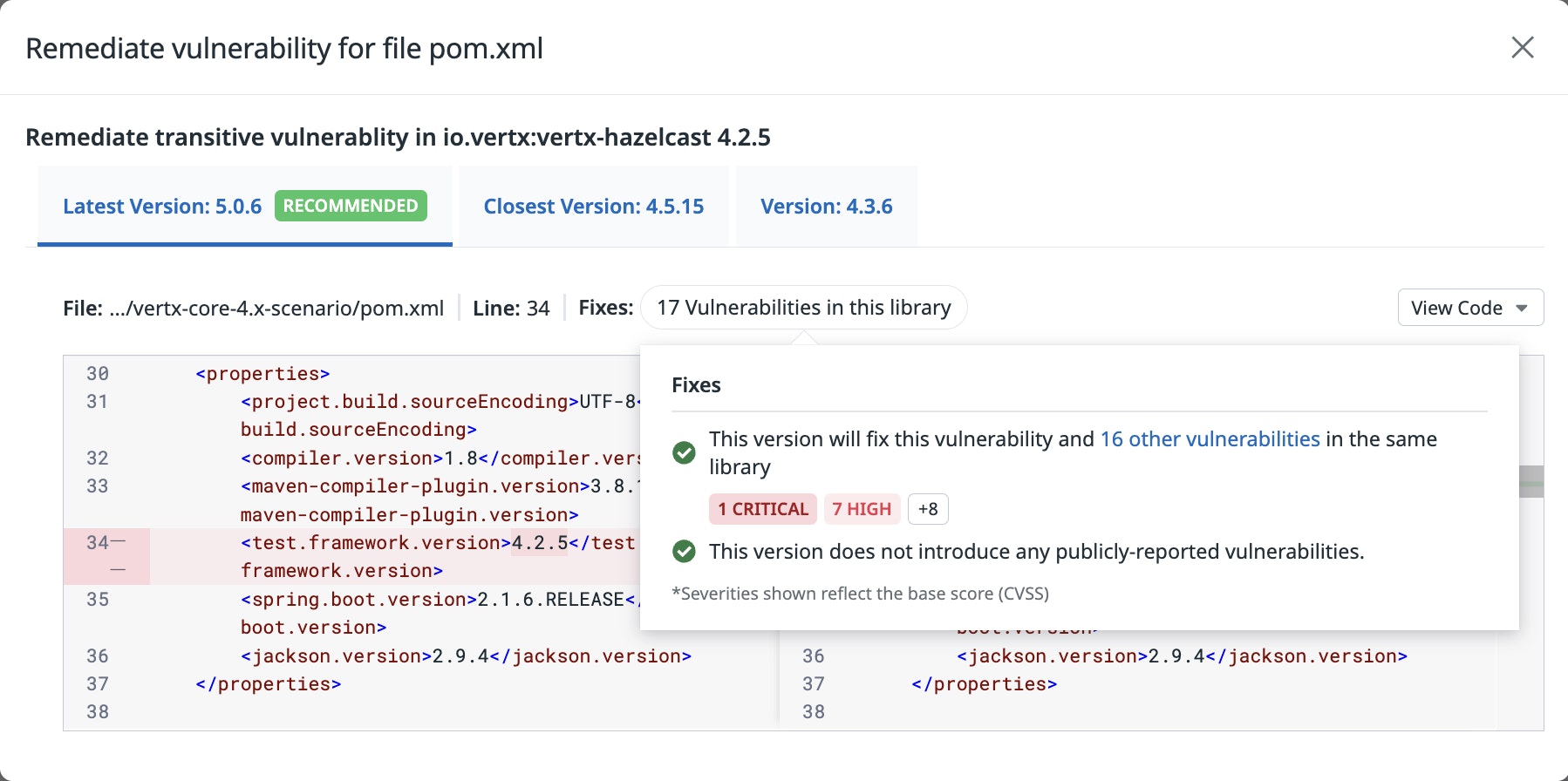
Upgrading a root dependency often does more than remove a single vulnerable transitive library. It can cascade into newer versions of additional transitive packages, sometimes fixing multiple vulnerabilities in the process. Datadog highlights this impact directly in the remediation flow, showing which additional findings would be addressed by the recommended root upgrade.
Step 5: Validate the outcome on the Vulnerabilities page
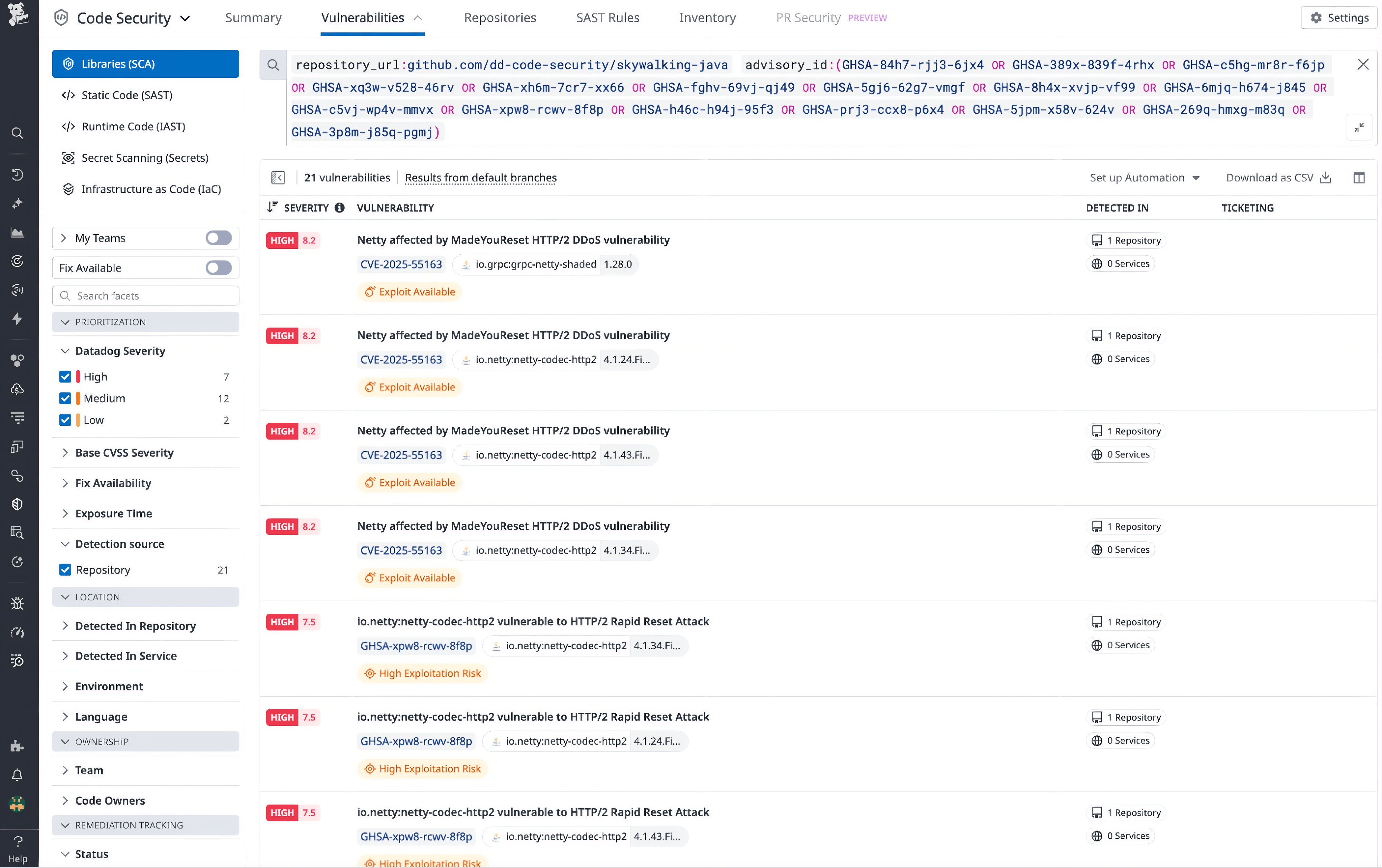
After identifying the appropriate root upgrade, teams can use the Vulnerabilities page in Code Security to review the full set of findings affected by the change. This helps security teams track remediation progress and gives engineers confidence that the upgrade addresses the intended risks.
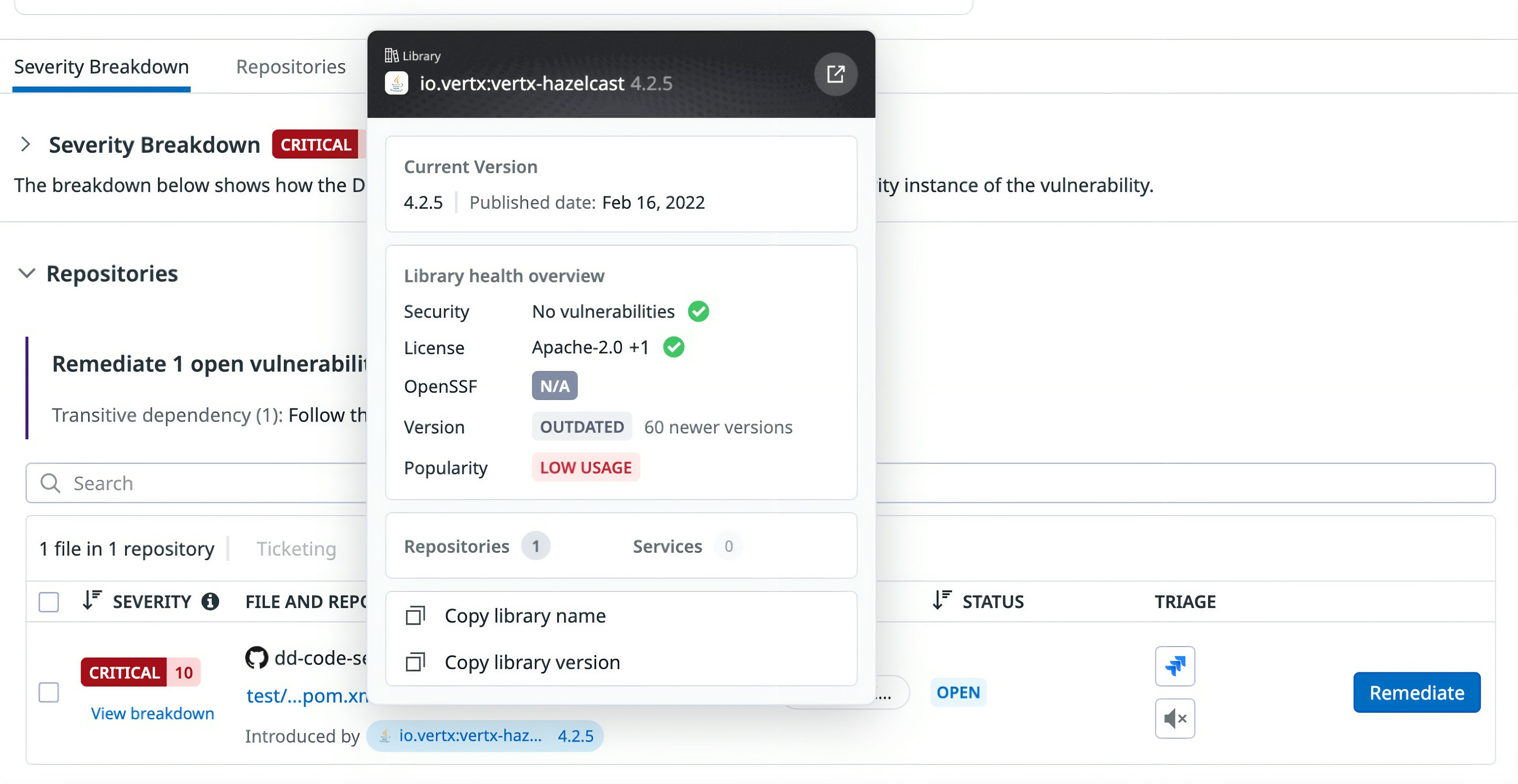
Step 6: Get additional context about the root library before upgrading
Finally, remediation decisions are not limited to counts of Common Vulnerabilities and Exposures (CVEs). Teams often want additional context about a root dependency before upgrading, especially if it sits high in the dependency graph. Datadog surfaces metadata such as publish date, license, and other health indicators so engineers can evaluate the broader implications of a version change before committing to it.
This end-to-end workflow moves teams from a vulnerability alert to a specific, reviewable change in the codebase, with visibility into both the direct fix and its broader impact.
Reduce triage time and ship safer dependency upgrades
Transitive vulnerabilities are a fact of life in modern software, and Datadog internal research suggests that about 70% of customer vulnerabilities originate from transitive dependencies. Remediation often stalls because teams can see what’s vulnerable but still lack the context for a safe fix. They need to know where it entered the repo, which upgrade removes it, and what else that change will affect. Datadog SCA closes that gap by tying transitive findings to the root dependency and recommending an upgrade path. It includes diffs and impact context, which makes fixes easier to review and apply.
As part of Datadog Code Security, Datadog SCA helps you detect and remediate vulnerabilities in third-party libraries and the dependency graph in your codebase. To learn more about Datadog Code Security and how it prioritizes and accelerates remediation, see our blog post on this topic. If you’re new to Datadog, sign up for a 14-day free trial.