Eitan Moriano

Vera Chan

Martin McCloskey

Edith Méndez

Nolan Hayes
Security teams rely on SIEMs to aggregate and analyze data from a wide range of sources, including cloud environments, identity providers, endpoint protection platforms, network appliances, SaaS apps, and more. But every source delivers logs in its own format, with different field names, structures, and semantics. This fragmentation makes it difficult to build scalable, reusable detection rules or correlate threats across systems. As a result, threat detection engineers spend valuable time writing custom parsers, manually mapping fields, and reverse-engineering unfamiliar log formats instead of focusing on threat detection and response. The lack of a consistent data model also forces security analysts to switch between tools and logs, slowing investigations and increasing the risk of missed signals.
To help solve these challenges, we’re introducing the OCSF Common Data Model in Datadog Cloud SIEM. The model provides a unified schema that aligns your security data with the Open Cybersecurity Schema Framework (OCSF) and automatically normalizes data across sources by enriching logs with standardized attributes.
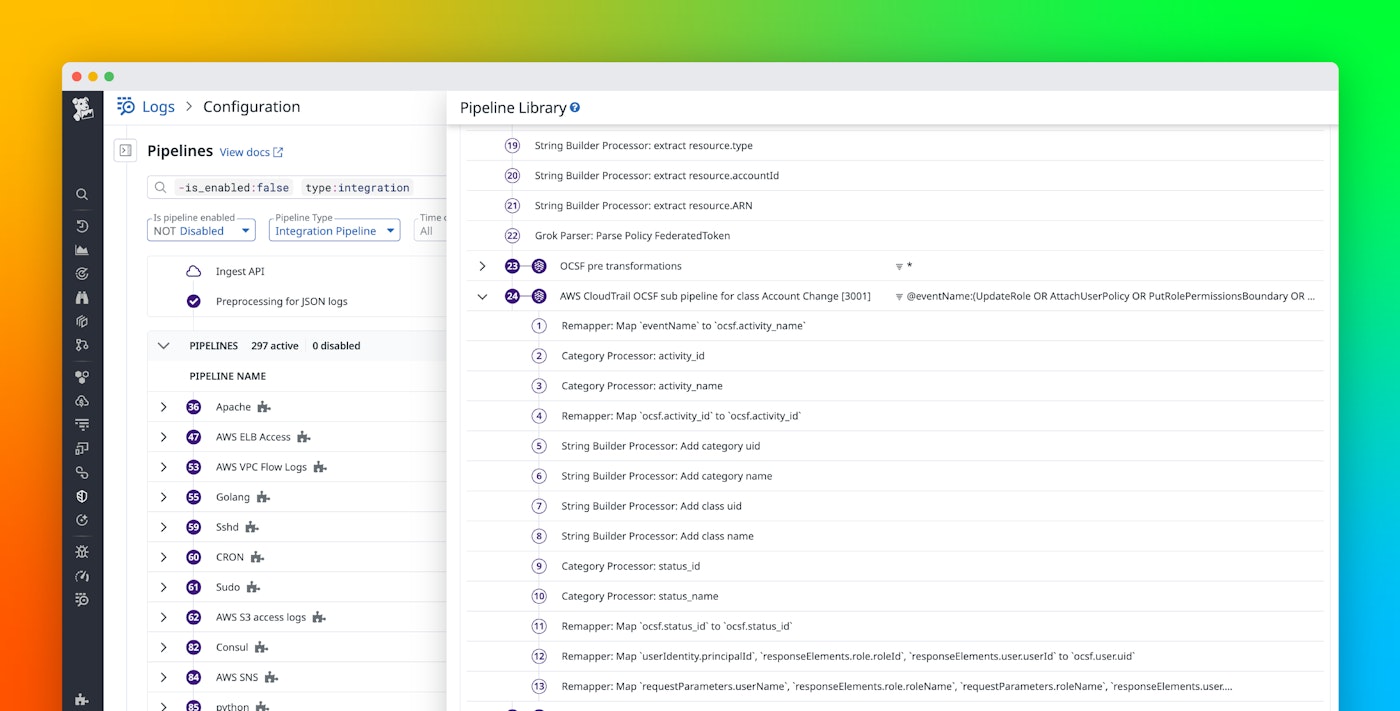
As data flows into Datadog via built-in integrations with sources such as AWS CloudTrail, Okta, and GitHub, Datadog Log Management pipelines map key fields to the OCSF taxonomy. And if you’re exporting logs to destinations like Amazon S3 or an external SIEM, Datadog Observability Pipelines lets you normalize to OCSF before routing so that you get consistent, schema-aligned logs regardless of whether you ingest them into Datadog. In addition, the OCSF processor enables teams that are unfamiliar with the OCSF framework to map any source to OCSF through a guided user experience.
The OCSF Model gives your teams a consistent foundation to build detections, investigate incidents, and correlate activity without custom parsing or manual field mapping. In this post, we’ll explain how the OCSF Model helps you:
- Apply prebuilt detection rules across normalized data
- Transform raw logs into structured data
- Normalize logs for CloudTrail, Okta, and GitHub
- Cover multiple attack surfaces with a single rule
- Detect cross-platform login anomalies
Apply prebuilt detection rules across normalized data
With the OCSF Model, prebuilt Content Packs include detection rules designed around OCSF attributes. The Content Packs reduce the time it takes to onboard new data sources and automatically apply generalized detections across integrations. Normalization is handled automatically for many sources, so these detections work with no manual schema mapping or rule rewrites needed. A brute force login attempt, for example, will match the same detection logic whether the source is CloudTrail, Okta, or GitHub.
Transform raw logs into structured data for advanced analytics and targeted investigations
The OCSF Model strengthens foundational capabilities for behavioral analytics, such as for the detection of anomalies in login patterns, file access, and privilege escalations. By standardizing how login events, file access, and privilege escalations are represented, Datadog provides more powerful analytics and anomaly detection across user behavior.
The OCSF Model also speeds up root cause analysis by helping analysts pivot across datasets without the need to juggle multiple schemas, tools, and interfaces. The model makes security data easier to ingest, query, and act on by using the fast-growing, vendor-agnostic OCSF standard. Datadog contributes to the OCSF initiative by sharing its attribute remappings with the broader community, helping drive transparency and adoption of the standard. You can explore these mappings in public GitHub repositories, which include examples for CloudTrail logs, Okta system logs, and GitHub audit logs.
Standardize cloud activity logs with CloudTrail
CloudTrail provides detailed logs of API activity across AWS services, making it essential for understanding user and service behavior in your cloud environment. These logs help security teams track account activity, detect suspicious changes, and investigate potential misconfigurations and unauthorized access.
Normalize CloudTrail logs to OCSF
When CloudTrail logs are ingested into Datadog Cloud SIEM, they are automatically normalized to align with OCSF event classes such as API Activity, Account Change, and Authentication, depending on the action. This standardization gives your teams a unified way to analyze AWS activity alongside logs from other cloud providers and services.
OCSF normalization makes it easier to filter high-risk actions, correlate API calls with other events, and build consistent detection rules, no matter which AWS service is involved.

Standardize identity logs with Okta
As a leading identity and access management platform, Okta produces logs that are critical for understanding user behavior, sign-in patterns, and potential credential-based threats. Security teams rely on identity telemetry data to investigate suspicious access and correlate activity across services.
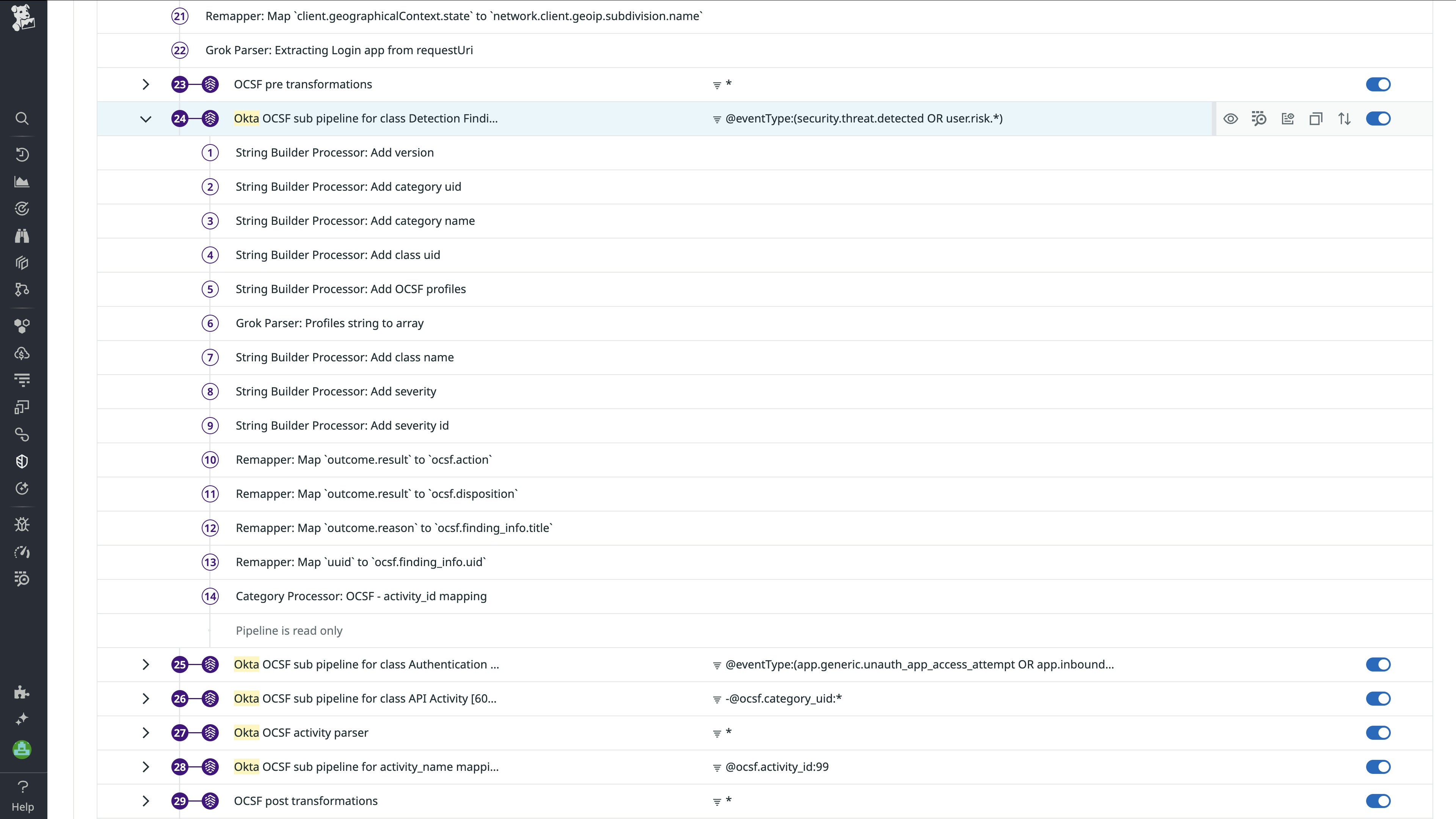
Normalize Okta logs to OCSF
When Okta logs are ingested into Datadog Cloud SIEM, they are transformed to align with the OCSF API Activity, Account Change, Authentication, Detection Finding, Entity Management, and Group Management event classes. This feature lets your teams analyze identity data by using a consistent schema, whether the data is from Okta or another identity provider.
OCSF normalization eliminates the guesswork of parsing JSON logs from Okta. It enables faster triage and easier rule creation, especially when you need to combine identity data with signals from endpoint protection platforms or cloud providers.
Improve security of code and collaboration with GitHub audit logs
GitHub is a cornerstone of modern software development and DevOps workflows, making it a valuable data source for detecting suspicious or risky activity tied to source code, repositories, and CI/CD pipelines. From unauthorized access to secrets exposure, GitHub audit logs provide rich context for identifying threats in the software supply chain.
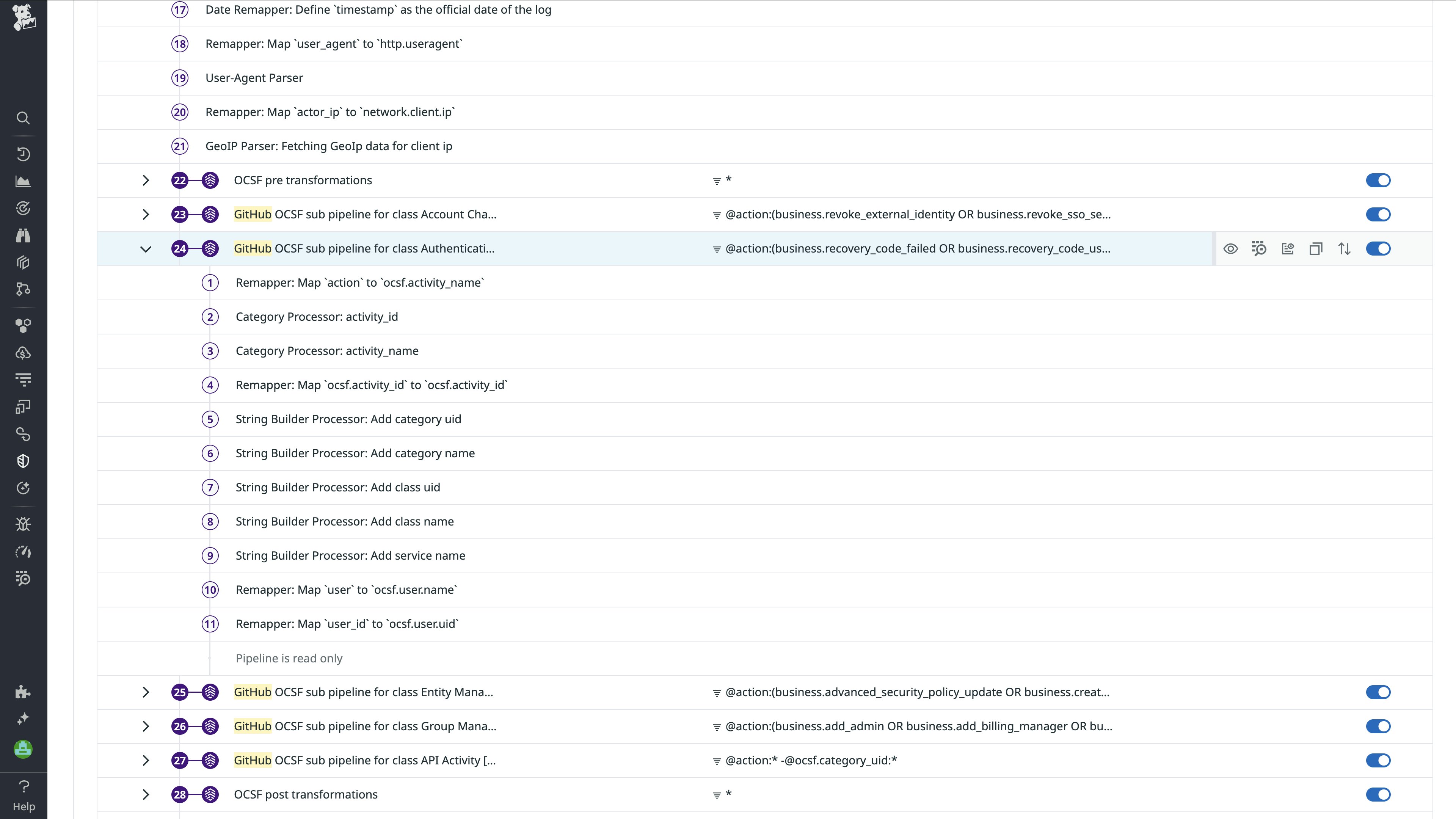
Normalize GitHub logs to OCSF
GitHub audit events are normalized into the OCSF API Activity, Account Change, Authentication, Entity Management, and Group Management event classes, depending on the action type. This structure allows your teams to correlate repository-level actions with identities, endpoint protection platforms, or cloud activity without needing to configure and parse GitHub’s complex JSON schemas.
GitHub logs are a key source of telemetry data for insider threats, misuse, and misconfigurations. By mapping these events to a common schema, Datadog empowers your teams to surface high-impact code security signals and write detections that span engineering and security domains.
Cover multiple attack surfaces with a single rule
Now that we’ve seen how logs from CloudTrail, Okta, and GitHub are mapped to OCSF, it’s worth looking at the impact of normalization beyond easier log parsing. One of the biggest detection advantages of using a common schema is the ability to scale detection logic across multiple sources. You can write a single rule to detect suspicious behavior that applies equally to cloud activity in AWS, identity logs from Okta, and code changes in GitHub.
Just as importantly, normalized logs reduce friction during investigations. Analysts don’t have to learn the structure of every log source, so they can focus on the signal. This unified view makes it easier to correlate indicators such as IP addresses or user identities across different services, accelerating response.
Detect cross-platform login anomalies
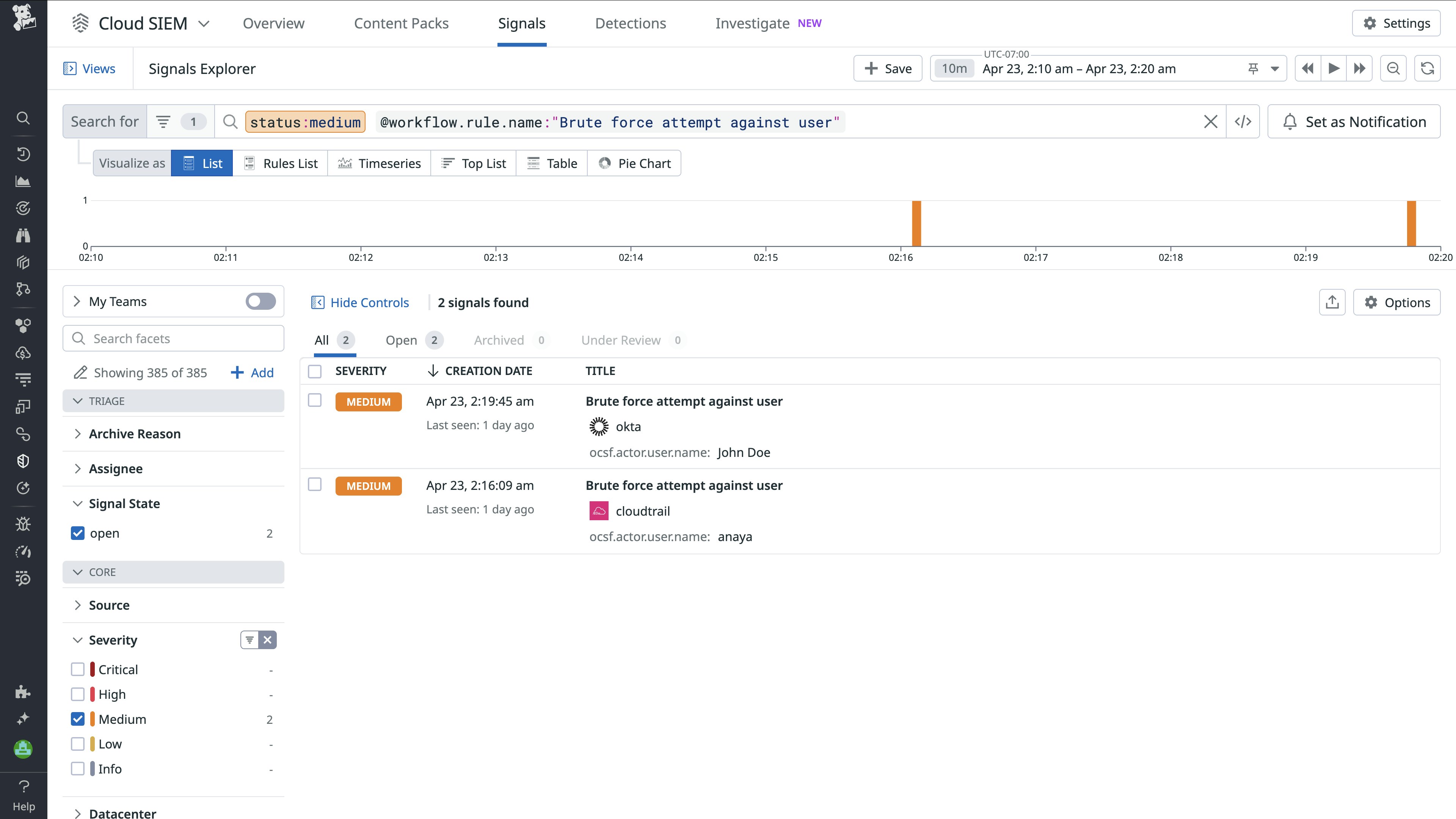
To detect suspicious authentication activity across identity and infrastructure layers, you can write a detection rule that spans multiple sources, such as Okta and CloudTrail, by using the OCSF Model. For example, the following rule looks for a sequence of failed login attempts followed by a successful login. This pattern can indicate brute force activity or credential stuffing behavior, especially when signals originate from different systems.

The following search shows the Okta and CloudTrail signals that were triggered by a single brute force detection rule. Thanks to normalization, Datadog automatically correlates these events across systems, making it easy to detect login anomalies that span identity and cloud infrastructure.
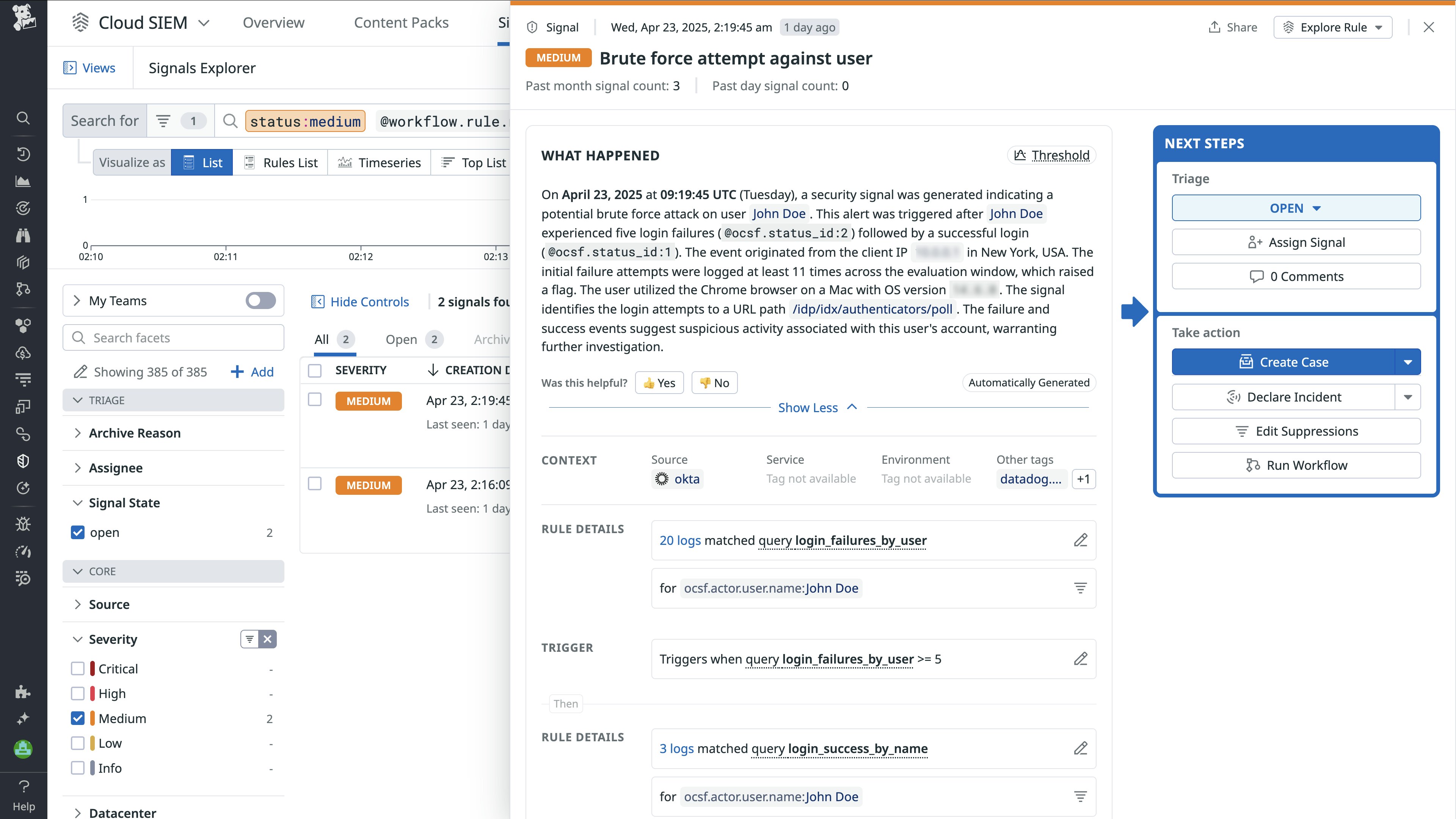
To give you deeper insight, the signal side panel shows you all the details and context about the signals. For example, the following Okta signal helps you understand what happened and when, which is critical evidence for an investigation.
Build a stronger security foundation with normalized data
The OCSF Common Data Model in Datadog Cloud SIEM standardizes security data to help your teams speed up investigations and write reusable detection rules that work across diverse sources. The unified schema provides interoperability between different tools and vendors, in addition to reducing the chances of missed signals that can result from data inconsistencies.
Check out our documentation to keep up with additional supported native sources and custom sources as they become available. You can also explore OCSF-normalized logs in a demo or view the CloudTrail, Okta, and GitHub log pipelines.
If you don’t already have a Datadog account, sign up for a 14-day free trial to get started.