Jordan Obey
HashiCorp Vault is a secrets management tool that makes it easier for organizations to securely store and tightly control access to tokens, passwords, certificates, encryption keys and other sensitive data. Instead of spreading confidential data like authentication keys and passwords throughout your infrastructure, Vault keeps data hidden and safeguards against secret sprawl by providing a centralized storage solution, robust auditing, and encryption services. And with Datadog’s new integration, you can monitor Vault and make sure your secret management service is running properly along with the rest of the development architecture that relies on it.
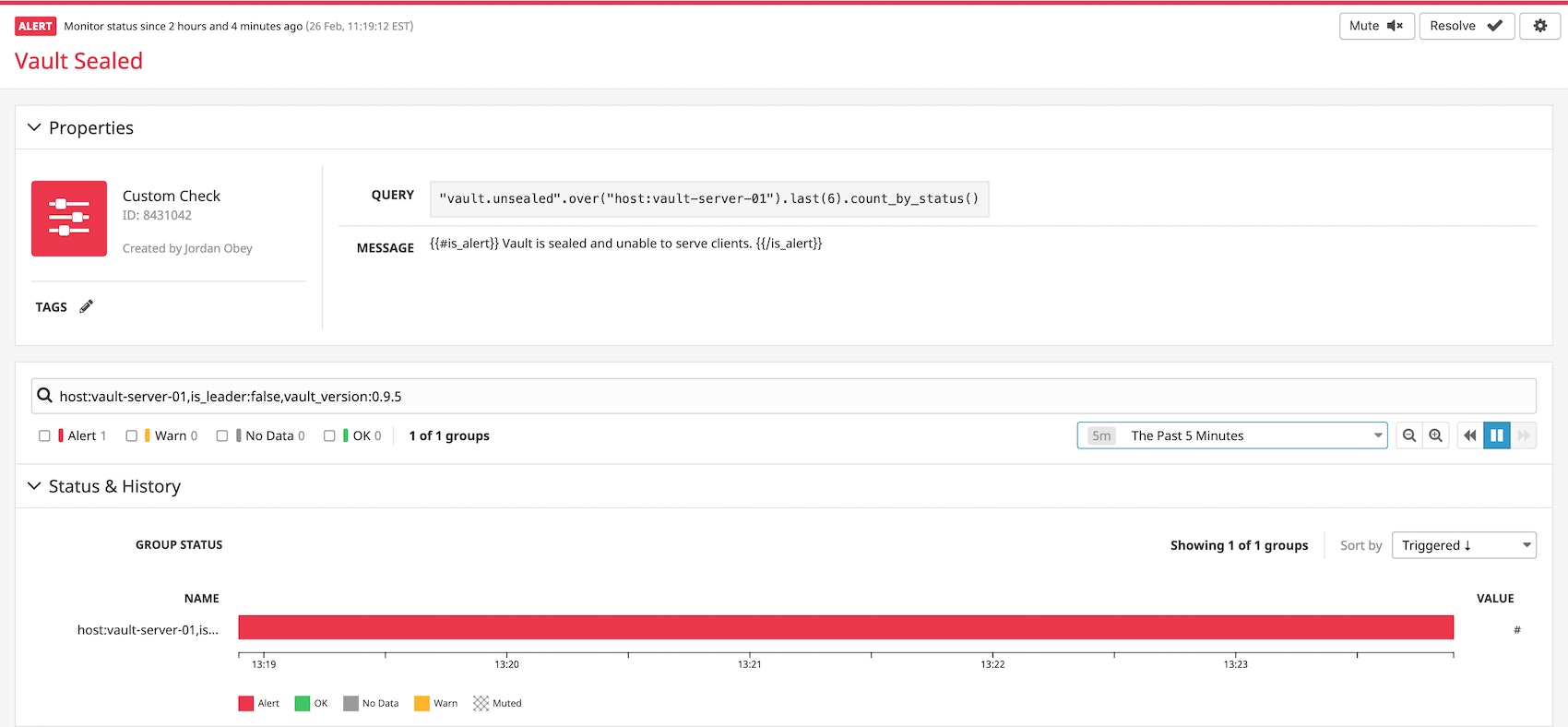
Get notified if a Vault unexpectedly becomes sealed
Vault servers can exist in two states: sealed and unsealed. While sealed, Vault keeps storage data encrypted and does not allow any operations to be performed on it. When Vault is unsealed, stored data is decrypted and accessible through an API.
An unsealed Vault server will become sealed again, and thus inoperative, if it restarts unintentionally. You can set up an alert to tell you if a Vault that is meant to be unsealed (identified with one or more tags) has become sealed and is no longer serving clients. In the example below, an alert triggered on host:vault-server-01, and lets you know a Vault was sealed, so you can immediately begin to investigate why.
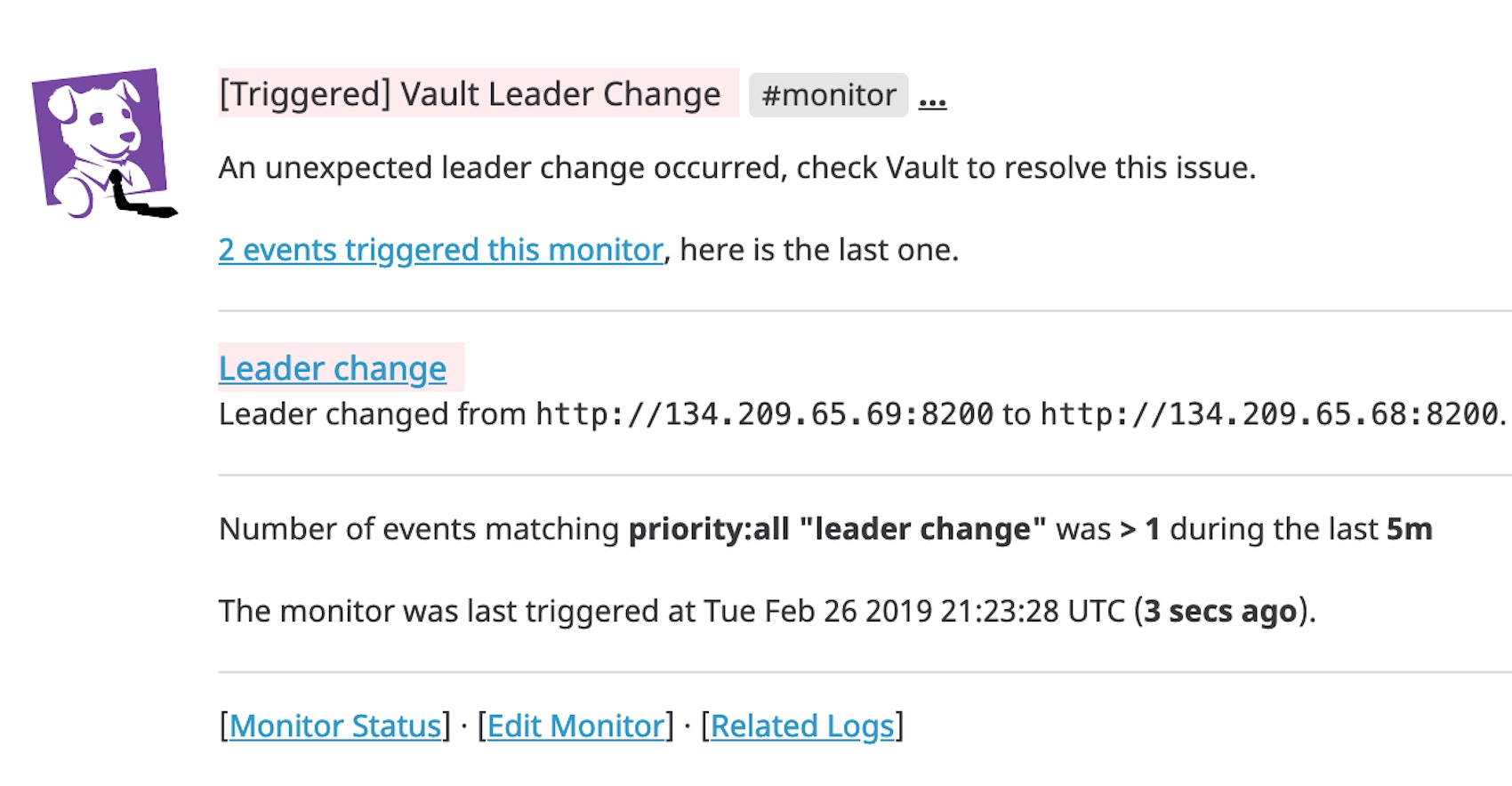
Alert on leader changes
Vault can be configured to store data on the local filesystem or using a compatible storage backend like MySQL, PostgreSQL, Azure Storage, Google Cloud Storage, or AWS S3. Some storage backends, like HashiCorp Consul, allow Vault to run in high-availability mode. A Vault cluster in high-availability mode consists of a single active leader and at least one standby node.
If the leader node fails or becomes sealed and stops serving requests, a standby node will take its place. This event is important to monitor because many leader changes occurring in a short span of time could indicate a potential security risk. For example, it could mean that either many Vault servers are failing at the same time, or that someone on your team has sealed Vault servers, perhaps in response to a detected security vulnerability. In each scenario Vault servers are rendered inaccessible to the clients that depend on them. With Datadog, you can track each leader change and set up an alert to notify you if it occurs with unusual frequency.
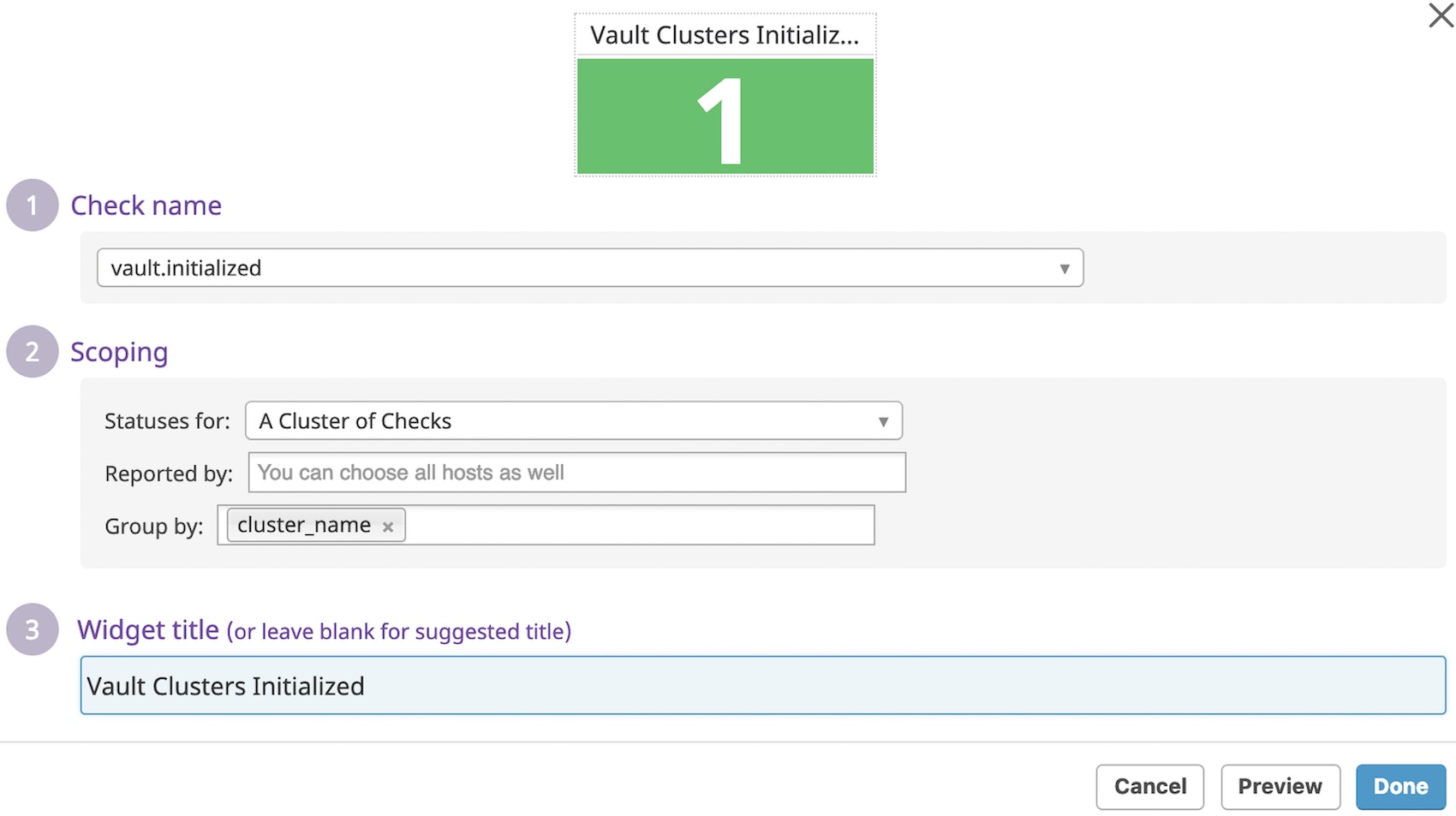
Verify Vault was initialized
If you want to keep track of how many Vault clusters have successfully initialized, you can run a service check to add a count of them to your dashboard. This check will return a value of CRITICAL during startup, and a value of OK after the Vault cluster has been properly initialized. A check that continues to return CRITICAL indicates a startup issue with your Vault server, which can occur because of obstacles like configuration errors and permissions-related issues.
Monitor Vault with Datadog
Once you’ve integrated HashiCorp Vault with Datadog, you can start automatically monitoring your secrets management system with other integrated services such as Consul and Kubernetes in one place. As Vault safeguards your environment against secret sprawl, Datadog will monitor its status and alert on unusual activity, providing visibility into Vault along with the other technologies in your stack.
If you aren’t already using Datadog, get started with a 14-day free trial.