Vera Chan

Edith Mendez

Melanie Yu

Nimisha Saxena

Anthony Randazzo

Will Roper
Many organizations face significant challenges with onboarding teams to a new or existing SIEM. Security teams grapple with escalating expenses tied to data ingestion, storage, and retention at scale. Steep learning curves can make setup an ongoing and frustrating chore, leading to mistakes and gaps in coverage. Further, SIEMs with constrained ecosystem integrations block users from the tools and customizable workflows they need and are comfortable with.
A modern SIEM should offer flexible data ingestion from any source, quick out-of-the-box tools to get started, and robust integrations that enable teams to onboard quickly and scale without sacrificing flexibility. This culminates in a de-risked migration path from legacy systems, so organizations can modernize at their own pace without operational disruption.
Datadog Cloud SIEM offers an intuitive onboarding path, allowing you to reroute your logs from any source into Datadog and immediately tap into over 900 built-in integrations. Whether you’re using custom APIs, Observability Pipelines, or prebuilt Content Packs, Datadog accelerates time to value.
In this post, we’ll highlight some of the ways you can avoid onboarding complexity and immediately get the most out of Cloud SIEM, including how you can:
- Manage security log costs effectively with flexible ingestion, retention, and routing
- Retain your tools and workflows with integrations and custom APIs
- Rapidly activate and onboard your SIEM team with Content Packs
Manage security logs effectively with flexible ingestion and routing
Security engineers often struggle to control the volume, quality, and sensitivity of the log data entering their SIEM. Without fine-grained control at the point of ingestion, they face ballooning costs from high-volume sources, increased risk from unredacted sensitive data, and limited visibility due to rigid or one-size-fits-all log forwarding tools. These challenges make it difficult to balance compliance, cost efficiency, and threat detection needs, especially in multi-environment architectures.
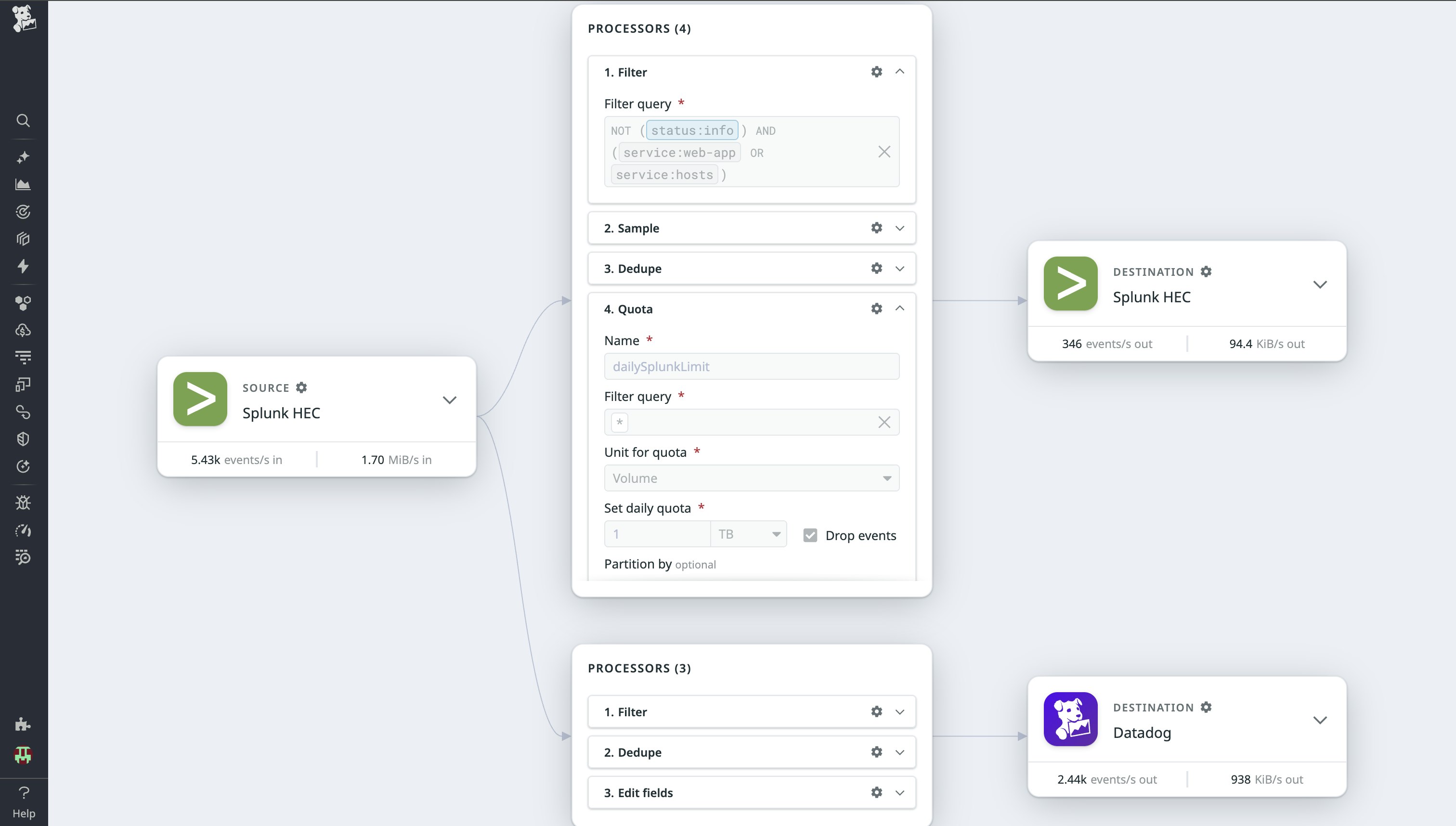
Datadog Observability Pipelines enables teams to aggregate, process, and route logs before directing them to cloud platforms, SIEM tools, data lakes, or other analytics solutions. It allows you to filter, deduplicate, and transform logs on-premises, ensuring only valuable data is sent to downstream systems. This feature reduces costs and increases efficiency by enabling log-to-metrics conversion, rule-based quotas, and dual shipping (sending logs to two destinations) using built-in templates for flexible migrations, all while maintaining access to critical insights.
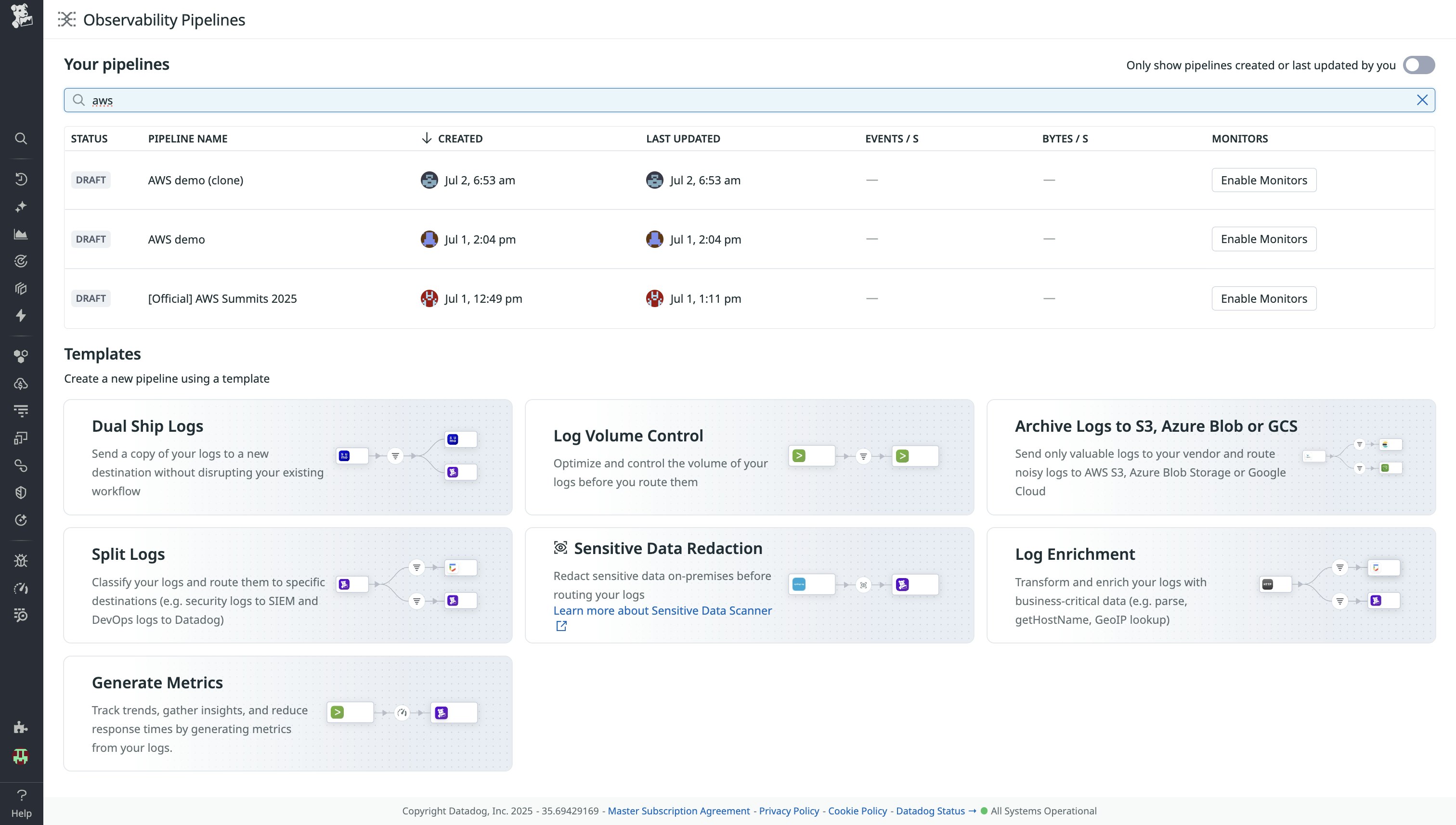
For example, a security team can redact sensitive data from on-prem environments before logs leave their network. By using built-in transformations, they can ensure compliance with privacy standards and internal security policies, including masking, hashing, or removing sensitive fields such as personally identifiable information (PII) or proprietary data. This helps organizations mitigate risks while maintaining operational transparency and regulatory adherence.
Observability Pipelines can also enrich logs with contextual data and apply advanced parsing rules for actionable insights before ingestion. With an intuitive control plane, live data capture, and centralized monitoring, teams can design, deploy, and manage their log pipelines efficiently.
As soon as your logs land in Datadog, Log Management allows for the centralization and retention of logs from virtually any data source. With out-of-the-box pipelines for over 900 integrations and the ability to create custom log pipelines, you can easily collect logs from sources such as cloud audit logs, identity provider logs, SaaS and Google Workspace logs, and third-party security integrations like Amazon GuardDuty.
Retain your tools and workflows with integrations and custom APIs
As environments grow more complex, security teams often struggle with fragmented telemetry and inconsistent log coverage. Many SIEMs require manual configuration or can’t ingest data from niche tools, making it difficult to unify signals across cloud platforms, SaaS providers, and on-prem systems.
With over 900 prebuilt integrations, Datadog Cloud SIEM connects to the tools and platforms your organization relies on. These integrations enable immediate visibility across your environment, eliminating the need for complex configuration or learning new workflows. From AWS and Microsoft Azure to Kubernetes and third-party security tools, Datadog simplifies monitoring and log ingestion, giving you comprehensive coverage with minimal effort.
For organizations with unique requirements, Datadog’s flexible custom APIs provide a way to build bespoke integrations and workflows. These APIs facilitate connectivity for even niche systems, offering adaptability and customization.
Flex Logs lets you further dial ingestion and retention up or down to match each security use case, whether that’s real-time detection on firewall traffic or 15-month look-backs for compliance. You can configure which log streams Cloud SIEM should analyze right from the UI, then cost-effectively scale storage without losing investigation context.
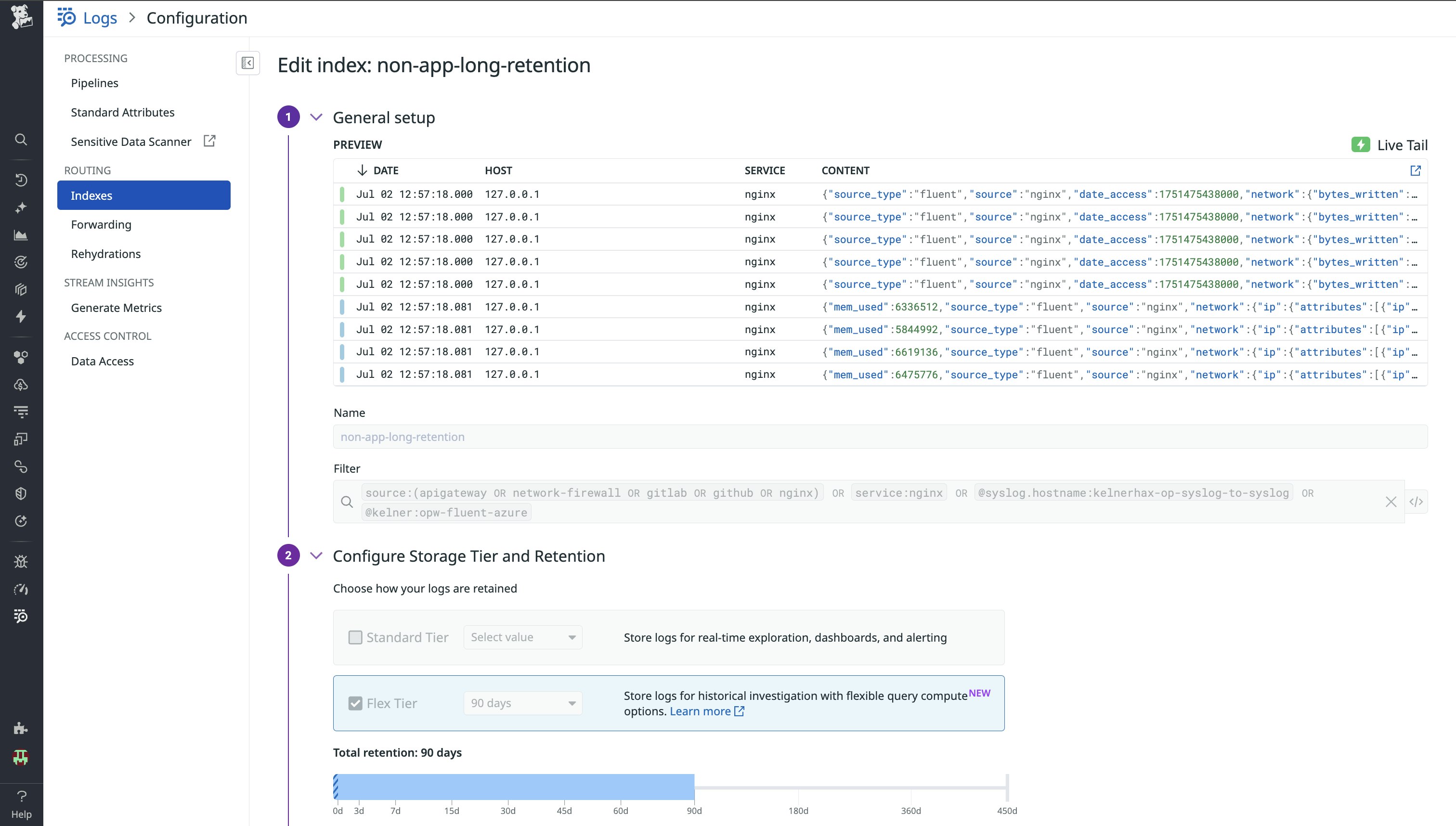
For a deeper dive into Flex Logs strategy and advanced use cases, see our Flex Logs and SIEM use cases post.
Rapidly activate and onboard your SIEM team with Content Packs
Even after successfully migrating logs and integrating familiar tools, security teams often face a final hurdle: getting up to speed quickly. Whether onboarding new analysts or transitioning from a legacy SIEM, teams can struggle to operationalize the platform due to steep learning curves, limited documentation, and fragmented content scattered across different sources.
To accelerate adoption and reduce friction while ramping up, teams can activate Cloud SIEM by accessing Content Packs. Content Packs include bundled prebuilt threat detection rules, dashboards, graphical investigative tools, automated workflows, and written content such as blogs, configuration guides, and more, all related to specific integrations.
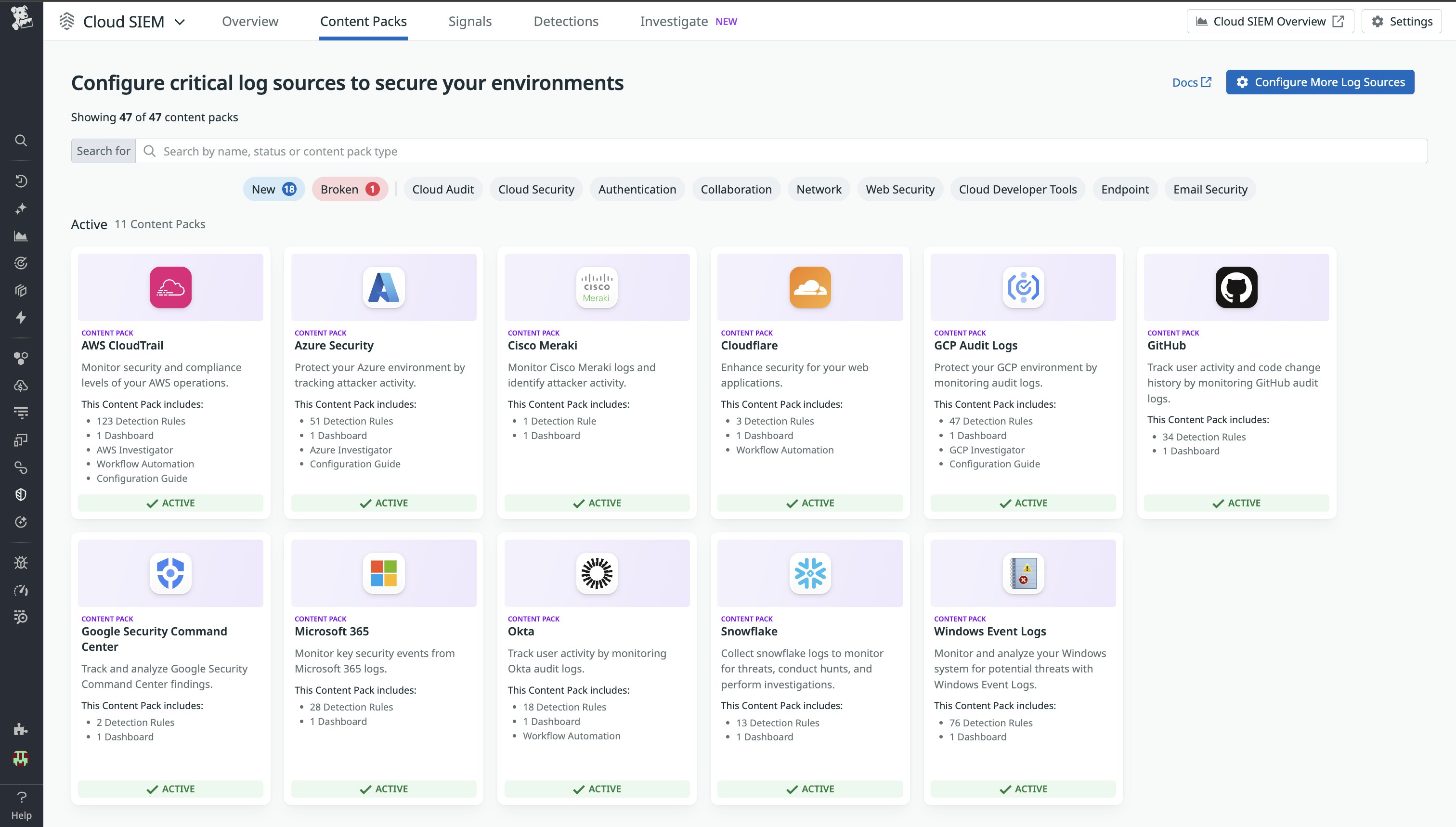
Imagine a security analyst on day three at a new company, tasked with monitoring a large distributed AWS environment before the week is over. They need immediate visibility into CloudTrail activity, baseline detections, and investigative dashboards so they can triage alerts with confidence. Let’s walk through how they can get there in minutes with the AWS CloudTrail Content Pack.
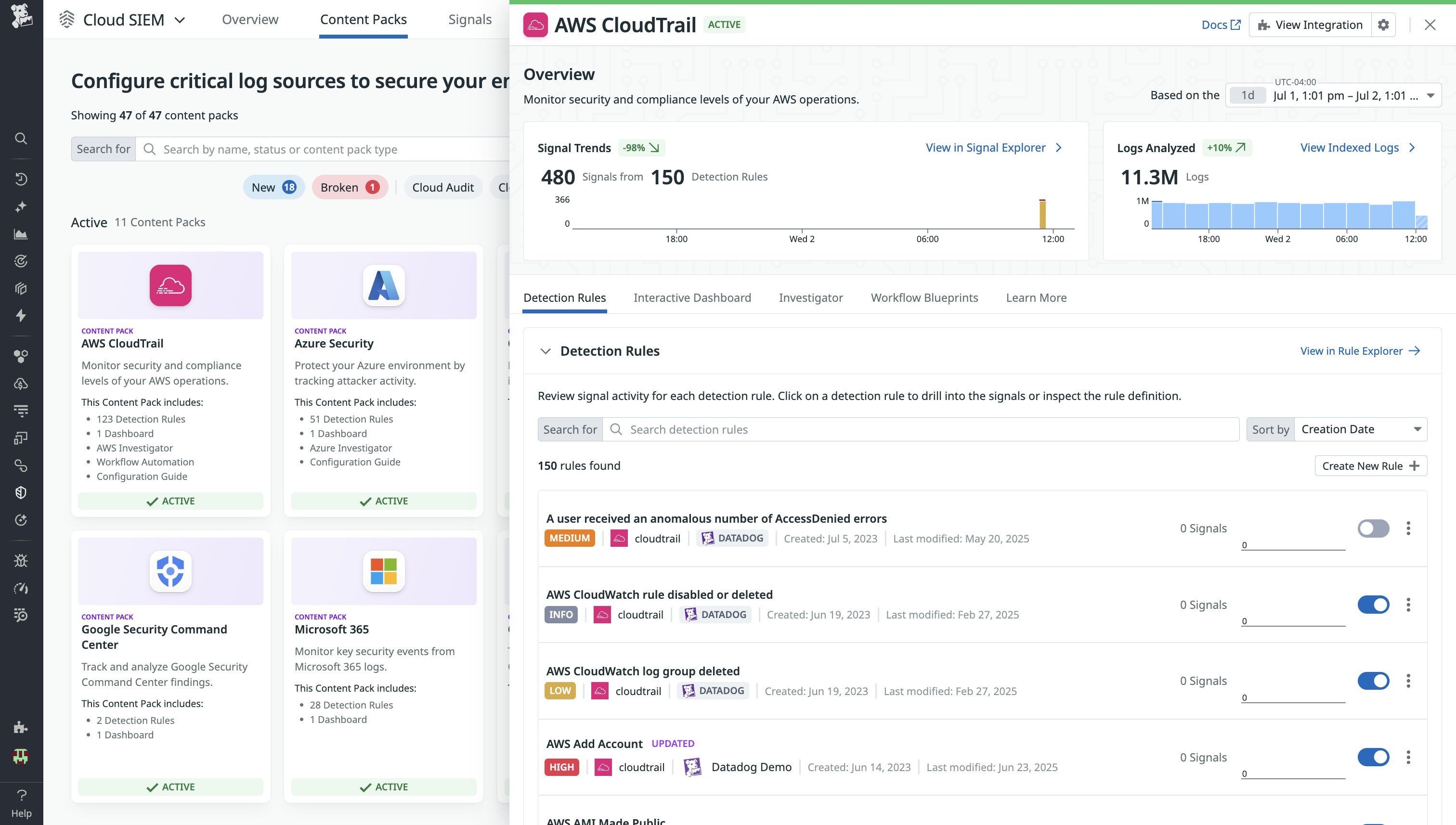
From the Cloud SIEM page, a security analyst can activate the AWS CloudTrail Content Pack in just a few clicks and unlock all its bundled content for centralized access in the overview side panel. This includes 100+ prebuilt AWS CloudTrail detection rules (aligned with the MITRE ATT&CK® Framework), out-of-the-box dashboards, and workflow blueprints to accelerate threat detection and response.
One rule from the AWS CloudTrail Content Pack detects suspicious activity associated with xlarge EC2 instances and cryptomining, a growing threat in cloud environments.
This detection rule that catches an attempt to create xlarge EC2 instances in multiple AWS Regions was created by one of Datadog’s threat detection engineers and is tagged with the TA0005-defense-evasion tactic and the T1535-unused-or-unsupported-cloud-regions technique. This helps visualize and identify gaps to strengthen detection coverage.
From the side panel, the analyst can also interact with a prebuilt AWS Cloudtrail dashboard to visualize anomalous activity, or they can scroll to the Cloud SIEM AWS Investigator to explore security logs using an interactive graphical interface. Within the AWS CloudTrail Content Pack, security teams can access a collection of 10+ prebuilt SOAR Workflow Automation blueprints designed to automate incident response and remediation. For example, the Investigate and Block Malicious IPs in AWS WAF SOAR blueprint automatically creates a notebook to help security responders quickly kick-start their investigation. The blueprint also launches a Slack prompt for responders, allowing them to block the IP or create an incident directly from Slack.
Migrate with confidence and onboard with Datadog Cloud SIEM today
By addressing the challenges of log ingestion and retention complexity, integration gaps, and limited customization, Datadog Cloud SIEM empowers organizations to modernize their approach to log management and quickly onboard their security teams.
Check out our documentation on Cloud SIEM and our detailed guide on getting started to learn more. And if you’re new to Datadog, try it out with a 14-day free trial.