Jonathan Epstein
Microsoft 365 is a suite of cloud-based productivity and communication services that includes Microsoft Office applications (including OneNote and OneDrive) as well as other popular Microsoft tools like Skype and Teams. Microsoft 365 tools and services are at the core of many organizations’ data management and day-to-day workflows, so monitoring activity across your environment is key to making sure that these services remain secure and meet compliance standards.
To gain a deeper level of insight into the security of your Microsoft services and monitor usage across your organization, you can ingest all of your Microsoft 365 audit logs directly into Datadog. Audit logs contain rich information about actions that occur within your Microsoft 365 environment, and are invaluable when discerning the compliance status of your services, applications, and files. With Datadog, you can analyze and alert on these logs in real time for security threats, centralize your monitoring and eliminate friction across your teams.
Monitor activity across all of your Microsoft 365 services
Microsoft 365 audit logs tell you the who, what, and when of the actions performed across your Microsoft 365 cloud services, like logins, file edits, and more. Audit logs record key data that includes the name of the operation that was performed, the user that performed the action, the type of user calling the action, and the status of the operation, as well as other useful identifying parameters.

Datadog automatically processes your logs and enriches them with tags and metadata, which lets you easily filter, sort, and group your logs to surface and visualize key information and patterns within your audit logs, such as which users generate spikes in failed requests, or which services are experiencing the most activity.

Once you enable the integration, you can use Datadog to monitor important activity across your Microsoft 365 audit logs, including:
- Service activity and file access
- User activity
- Authentication and authorization actions
- Security threats
Monitor service activity and file access
Microsoft 365 audit logs can help you track the types of operations performed within and by your Office services and give you a better picture of the most common activities across your environment. Datadog tracks your most active Microsoft 365 services, as well as the most common actions performed within or by those services. If you notice unusual activity on a service, you can quickly pivot to relevant logs to dive deep into the specifics of its usage.

Similarly, you can easily track anonymous user activities across your Microsoft 365 services to check for security threats. Datadog tracks anonymous user operations across your environment; you can also use the following query in the Log Explorer to inspect each anonymous user log individually.
source:microsoft-365 usr.id:urn\:spo\:anon*Microsoft 365 audit logs can also help you track file activity across OneDrive and SharePoint, including content edits and sharing settings changes; this is especially useful for determining which users have accessed or altered sensitive information. The following query will filter the Log Explorer's Live Tail to all OneNote file edit events.
source:microsoft-365 service:OneNote evt.name:FileModifiedLogs for file activity describe the name and type of the user who interacted with the file, the type of action performed, the IP address from which the user accessed the file, and more. You can use this information to visualize trends across your file activity; for instance, you can use Log Analytics to quickly create a visualization of the most frequently accessed files in your OneDrive system.

Monitor user activity
Each Microsoft 365 audit log records information on the user or service that performed the action, including their IP address and geographic location. You can use this data to track users across your environment and spot usage patterns that could indicate a compromised or malicious user. You can use Datadog to visualize and track the most active users and user types in your environment, giving you immediate access to your Microsoft 365 user information.

Once you spot an inconsistency in user activity, you can quickly pivot to the related logs in the Log Explorer for a closer look. For example, if your organization is entirely based in the United States and you spot logs originating in Ireland, you can zoom in on the anomalous logs using the following query.
source:microsoft-365 @network.client.geoip.country.name:IrelandUsing those logs, you can determine what those users have already done, and take the necessary actions to lock them out. Similarly, in order to track individual login attempts, you might want to filter your logs based on authentication request type. The following query returns all logs for user logins.
source:microsoft-365 @evt.name:UserLoggedInMonitor authentication and authorization actions
Microsoft 365 audit logs record every instance of login activity across your suite of services, including failed login attempts. Each log details the circumstances of the attempt, including the IP address that made the attempt, the time it occurred, the service the user attempted to use, the outcome of the attempt, and more.
You can query on these attributes in Datadog to discover how many login failures have occurred over a given time window, and use Log Analytics to build data visualizations and spot failure patterns.

To monitor and alert on trends in login activity over time, you can generate metrics based on any log attribute. Then, use Datadog's anomaly detection monitor to detect unusual trends. For example, you might spot an abnormal spike in login attempts coming from a certain geographic area: using key attributes from the related logs, you can correlate the failed login attempts with other API activity coming from that region.
And using Datadog's integrations with popular collaboration tools like Slack and Jira, you can set up automated alerts for any sort of user or system behavior and detect threats before they can cause serious harm.
Monitor and alert on changes to user credentials
Microsoft Entra ID manages the identity and access credentials of every user in your Microsoft 365 environment. It's important to be aware of any changes to Entra ID user authentication or authorization protocols, which could represent an attacker attempting to gain admin persistence. You can use your Microsoft 365 audit logs to track and notify on user account modifications. For example, you might want to see all instances of password changes across your user base with the following query:
source:microsoft-365 service:AzureActiveDirectory evt.name: Change user passwordYou could then inspect the returned logs to determine which credential changes are expected and which are potentially malicious.
Security monitoring and auditing
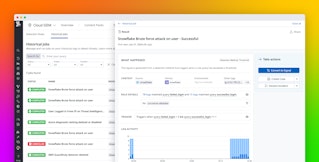
In order to determine if any actions in your Microsoft 365 environment pose a security threat, you can create custom Threat Detection Rules to look for potentially malicious activity. You can export any of the previously mentioned Log Explorer queries into a Threat Detection Rule, making it easy to get notified immediately when issues occur. For example, in the screenshot below we're creating a rule that gets triggered if there are more than five failed login attempts from a single user, possibly indicating a brute-force attack.

When Datadog ingests an audit log that matches the circumstances defined by a rule, it creates a Security Signal, a record of the infraction that, depending on the rule broken, might contain incident metadata (e.g., the geographic location from which the call was made, the type of agent, if any, attached to the calling instance, etc.) and determine the relative severity of the threat. You can inspect all of the Security Signals generated in your account in Datadog's Security Signals Explorer, where you can triage signals and correlate them with logs taken from across your stack to determine their potential causes.
Datadog's Microsoft 365 integration includes an out-of-the-box dashboard that gives you a full-picture perspective of the security and performance of your 365 services and infrastructure. The dashboard includes widgets that track the most common user activities (by username and IP address) in your environment, your most accessed files, anonymous user actions, and more. You can also customize the dashboard to include widgets based on the most relevant Microsoft 365 metrics for your monitoring scope.

24/7 monitoring for Microsoft 365
Datadog offers integration with numerous Microsoft 365 log sources for comprehensive monitoring of your environment. Some supported sources include:
- Exchange: Mailbox audit logs, Admin activity logs
- SharePoint: Site collection activity logs, Admin activity logs
- Microsoft Entra ID: Sign-in logs, Audit logs
- OneDrive: User activity logs, Admin activity logs
- Microsoft Teams: User activity logs, Call records, Meeting records
This is only a partial list. For the full list and further details on each log source, please see our documentation.
Datadog's Microsoft 365 integration gives you deep visibility into the security and compliance status of your Microsoft cloud applications. If you're already a Datadog user, you can start using the new integration now. If not, get started today with a 14-day free trial.