Jordan Obey

Nathaniel Beckstead
The Domain Name System (DNS) is responsible for mapping client-facing domain names to their corresponding IP addresses, making it a fundamental element of the internet. DNS-level events provide valuable information about network traffic that can be used to identify malicious activity. For instance, monitoring DNS lookups can help you see whether a host on your network attempted to connect to a site known to contain malware. That’s why we’re pleased to announce that Datadog’s eBPF-powered Workload Protection now analyzes DNS activity—in addition to file and process activity— to detect security threats in real time.
In this post, we’ll look at how DNS-based threat detection can further improve your security posture by uncovering malicious activity, such as cryptojacking attempts and data exfiltration, and correlating it with other health signals in your environment.
Spot security threats with DNS-based detection rules
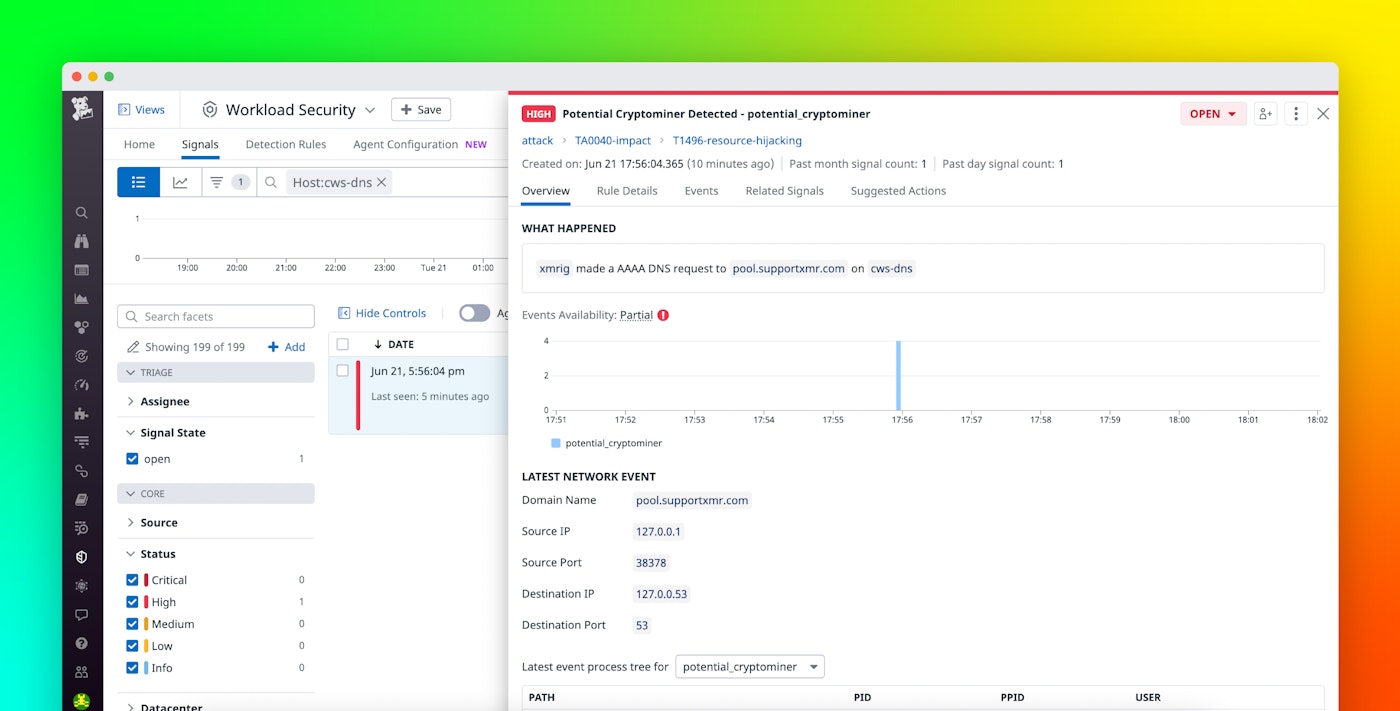
Workload Protection includes out-of-the-box workload threat detection rules that flag suspicious activity, such as unexpected password changes, web shell creations, and nmap executions. Our newest rules expand your coverage by providing visibility into DNS lookups so you can spot attacks at the network level. For example, Workload Protection includes a default rule that alerts you if there’s been a DNS lookup to a domain associated with a cryptomining pool. Cryptomining pools aggregate the compute resources of several hosts over a network to distribute the work of mining cryptocurrencies. If a host on your network unexpectedly performs DNS lookups to a cryptomining pool, it could be a sign of a compromised application. In this type of attack, bad actors infiltrate your infrastructure and use your resources to mine cryptocurrencies without your knowledge, severely degrading the performance of your service. If you suspect a host is being used for cryptomining, you can remediate the issue by disconnecting and reimaging the host in question.

Datadog Workload Protection also includes out-of-the-box rules to help you detect “command and control” attacks, in which bad actors commandeer a segment of your system. For instance, you can set a rule that detects DNS lookups made to “paste sites”, which are used to share plain text over the internet. Paste sites are commonly used by developers to share code segments and configurations, but they can also be used to store malicious scripts that can be downloaded and executed within your environment. For instance, a bad actor might upload a malicious script to a paste site in order to exfiltrate sensitive information, such as customer payment data.
If developers in your organization rely on a few trusted paste sites, it’s important to ensure that this routine activity will not trigger false positives. Datadog enables you to add specific domains and applications to a suppression list, which will ensure the rule only triggers in response to unexpected activity.
Correlate security signals for additional context
Detection rules generate security signals when they are triggered, which provide additional details about the suspicious activity you’re investigating. For instance, they include the threat’s severity level, as well as the host or container where the threat was detected.

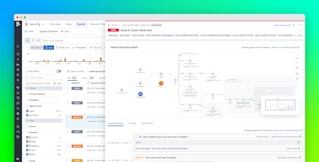
Datadog Workload Protection automatically correlates related security signals, giving you contextual information that can help you determine whether suspicious behavior is malicious. In the screenshot below, you can see that a security signal for cryptomining is related to a security signal for a Java process that has generated a shell. If you see these two signals in tandem, it’s highly likely that a web shell attack has occurred and that your resources are being used to mine cryptocurrencies.

Add a new layer of protection for your environment
Datadog Workload Protection monitors file and process activity in your environment so that you can identify threats to your infrastructure in real time. Now, the new DNS-based threat detection rules provide another layer of protection by analyzing and detecting suspicious activity at the network level. To get started with Datadog Workload Protection and DNS-based threat detection, make sure you are running the latest version of the Datadog Agent—see our documentation for further instructions. You will also need to set up and configure Datadog Security, which can be done through the Datadog app.
If you’re not already a Datadog customer, sign up for a 14-day free trial.