Christina DePinto
Security organizations are expected to keep pace with a growing set of regulatory and industry requirements as their cloud environments grow. Yet maintaining compliance in modern, fast-moving infrastructure is increasingly difficult. Cloud resources change by the minute, teams adopt new services without centralized oversight, and evidence needed for audits is often scattered across tools and providers. Security teams are left spending valuable time reconciling inconsistent data, tracking configuration drift, and validating controls long after changes have been deployed.
These challenges make it hard to maintain an accurate, up-to-date view of posture and even harder to scale compliance programs as the business grows. Traditional point-in-time assessments no longer keep up with dynamic cloud environments, creating gaps that increase risk and slow down both security and development teams.
To keep up with changing infrastructure, teams need a unified, continuous approach to compliance. Datadog Cloud Security provides global framework coverage and deep visibility into posture risks, giving teams a single place to identify gaps, validate controls, and simplify audit preparation. With up-to-date context for their environments, DevOps and security teams can quickly understand the compliance posture of their resources and take action without slowing down development.
In this post, we’ll show how Datadog Cloud Security helps you:
- Improve your security posture and audit readiness
- Understand your compliance posture at a glance
- Track requirements across global and industry-specific compliance frameworks
Improve your security posture and audit readiness
Datadog Cloud Security provides more than 1,500 out-of-the-box detection rules mapped to key industry, regulatory, and regional frameworks. It also supports both agentless and agent-based scanning, which run at automated or on-demand intervals to deliver near real-time visibility into your environment. A 15-month history of misconfigurations helps you keep supporting evidence on hand for investigations or audits so teams can efficiently track progress and measure program effectiveness over time.
Detection rules are routinely updated by the Datadog Security Research team to reflect emerging threats and evolving standards. When you need to tailor controls to your environment, you can modify existing rules or create custom policies using Rego. New or updated rules automatically run in your environment as soon as they’re saved.
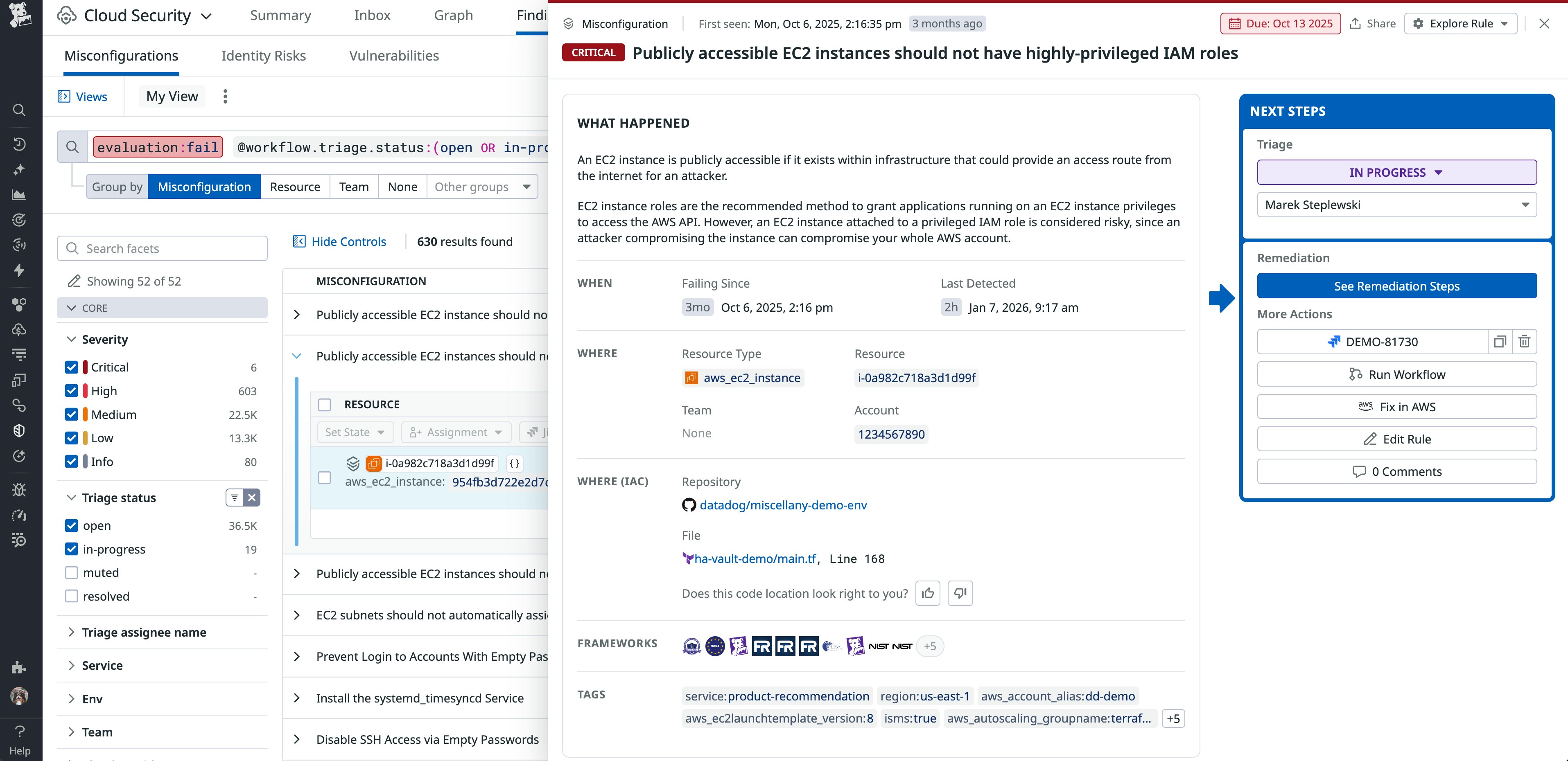
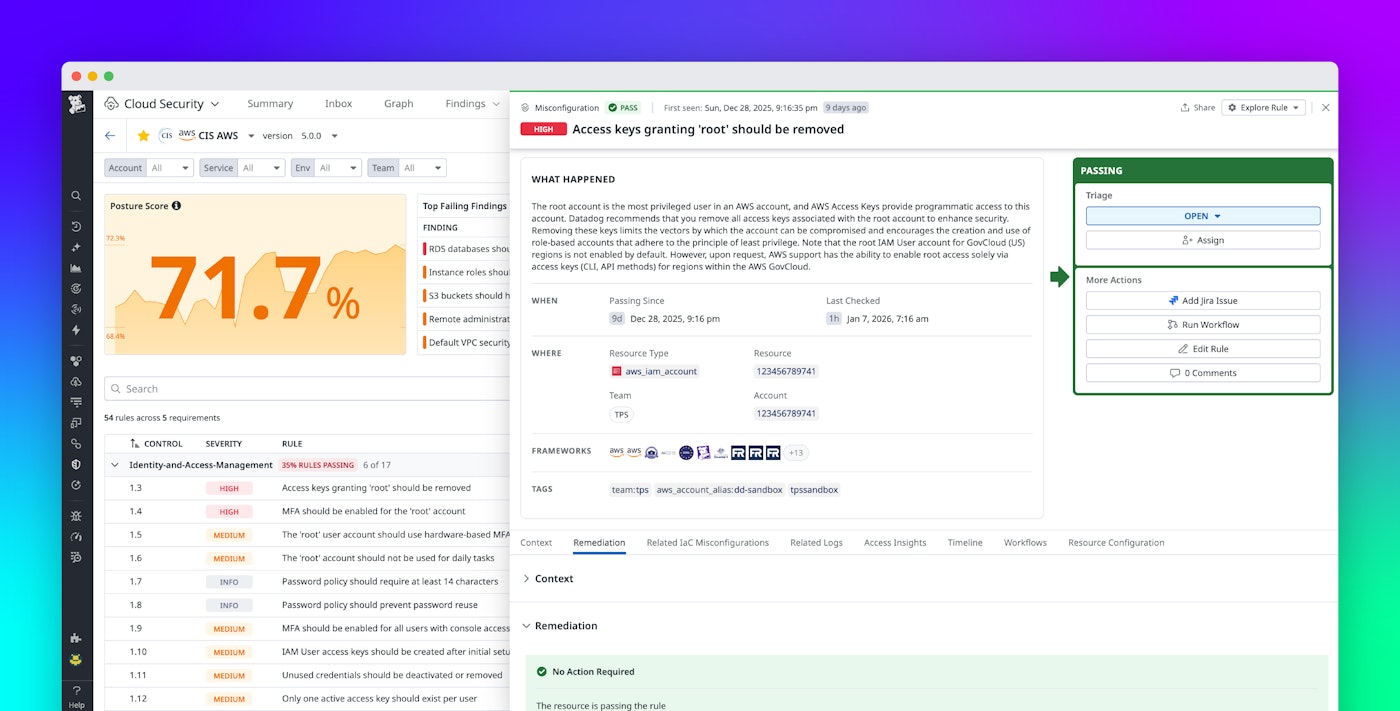
Misconfiguration findings are automatically tagged with the compliance frameworks they relate to, along with clear explanations of why each misconfiguration introduces risk. This makes it easy for any user, even those without a security background, to understand the impact and urgency of the issue.
Each finding includes where and when Datadog detected the misconfiguration, which team owns the affected resource, exposure paths between connected resources, and concrete remediation guidance. With this context in one place, you can focus on the findings that create the most risk. Findings also include integrated orchestration tooling, which enables you to resolve critical issues faster by minimizing repetitive, manual tasks.
Understand your compliance posture at a glance
Each compliance framework includes a posture score that updates hourly and reflects how well your environment adheres to active controls. Scores use a weighted formula based on severity and the number of failing resources, helping teams prioritize what matters most. You can also customize your scores by excluding accepted risks or controls that aren’t relevant to your environment. All of this information is surfaced in the Compliance homepage within Datadog Cloud Security.
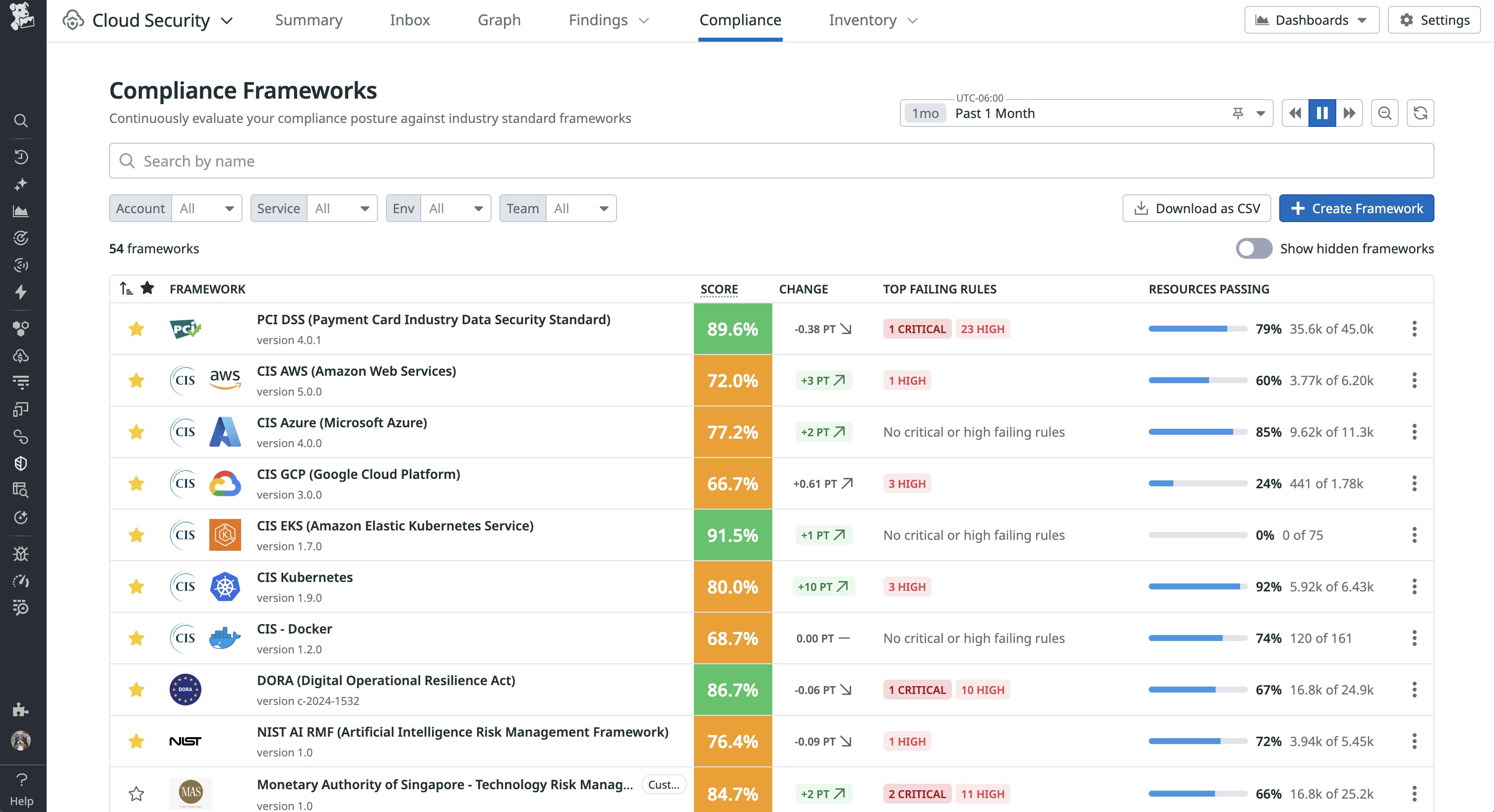
From the Compliance homepage, you can select a framework and see its posture score at a glance, how that score has changed over time, and the top failing findings, including their triage status and impact. This view helps you quickly understand your compliance gaps and provides the data you need to drill into specific framework sections or sort findings by team to route remediations to the right owners.
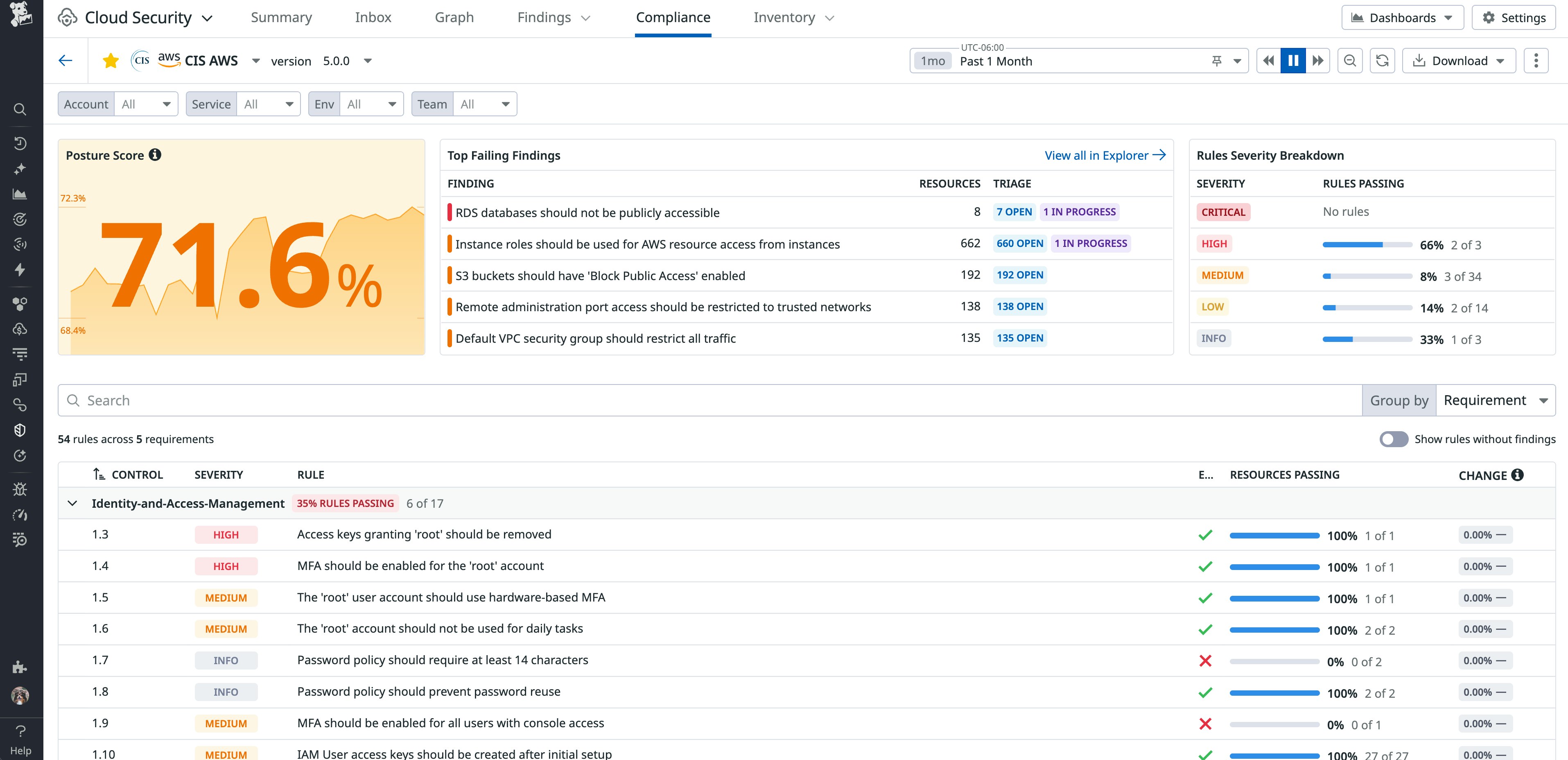
Track requirements across global and industry-specific compliance frameworks
Datadog now supports an even wider set of compliance frameworks to help global, multi-cloud organizations meet regulatory, industry, and regional security requirements. This expanded coverage includes frameworks such as Australian Prudential Regulation Authority (APRA) CPS 234 and Monetary Authority of Singapore (MAS) Technology Risk Management (TRM) guidelines. Support for these frameworks help strengthen continuous compliance efforts and boost audit readiness for distributed environments.
Key frameworks include:
- NIST AI Risk Management Framework (AI RMF): The NIST AI RMF provides organizations with guidelines for managing risk in AI deployments. Datadog Cloud Security includes out-of-the-box support for this framework and Amazon Bedrock so teams can adopt an AI security posture management (AI-SPM) approach and continuously identify configuration risks that could expose data or models to unauthorized access.
- ISO 27001:2022: ISO 27001 remains one of the most widely adopted security standards worldwide. Datadog maps misconfigurations directly to updated Annex A controls, helping organizations maintain their Information Security Management System (ISMS) with continuous evidence collection, automated posture monitoring, and clear traceability. This supports certification efforts and ongoing internal assessments.
- SOC 2: For SaaS and service providers, SOC 2 compliance is essential for demonstrating strong security, availability, and confidentiality practices. Datadog aligns findings to the Trust Services Criteria (TSC), giving teams a continuous view of gaps that would traditionally surface only during audits. This allows organizations to maintain audit readiness year round and simplify evidence gathering.
- PCI DSS 4.0: PCI DSS 4.0 introduces significant new requirements around authentication, segmentation, and ongoing monitoring. Datadog helps teams continuously validate controls that reduce cardholder data risk, helping compliance teams stay ahead of evolving payment security obligations and avoid costly assessment delays.
- CIS Benchmarks for AWS, Azure, GCP, and Kubernetes (including EKS, AKS, and GKE): CIS Benchmarks provide a starting point for many cloud security programs. Datadog supports the latest benchmarks, including CIS AWS 5.0.0, AWS Foundational Security Best Practices, and CIS Kubernetes 1.9.0, which gives organizations an automated way to measure cloud configuration health, reduce drift, and ensure environments conform to industry-accepted hardening guidelines.
- APRA CPS 234: Highly regulated industries such as banking and insurance must ensure control effectiveness and operational security. Datadog’s coverage of APRA CPS 234 helps organizations validate their security capabilities, monitor for control failures, and maintain compliance across cloud infrastructure in real time.
- UK Cyber Essentials, GDPR, EU Cyber Resilience Act, Australia Essential Eight, MAS TRM, and DORA: Datadog continues to add support for region-specific frameworks as regulatory expectations expand globally. These frameworks help organizations quickly understand how local mandates impact their cloud environments, especially those operating in the EU, APAC, and UK. Datadog’s continuous monitoring and control mapping simplify multi-region compliance without requiring multiple tools or manual processes.
Sensitive Data Scanner complements this coverage by discovering, classifying, and redacting sensitive data in logs, traces, real user monitoring (RUM), and events. This helps organizations meet key data protection requirements, including redacting credit card numbers and personally identifiable information (PII) from logs.
Strengthen cloud compliance posture with Datadog Cloud Security
Maintaining continuous compliance in cloud environments will continue to be a challenging but necessary goal for security organizations. Datadog’s expanded framework coverage, continuous misconfiguration detection, and automated evidence collection give organizations a unified way to understand posture and respond to risk at scale. With Datadog, you can continuously validate controls, reduce the time and effort for audit preparation, and significantly improve your security posture.
To get started, read the Datadog Cloud Security documentation. If you’re new to Datadog, sign up for a 14-day free trial.