Vera Chan

Eitan Moriano

JC Mackin
Security teams need visibility across every system they defend, including cloud platforms, SaaS applications, security controls, identity providers, and custom services. But those systems all produce logs in different formats, with inconsistent field names and structures. That lack of standardization makes it harder to correlate events, write reusable detections, and investigate incidents quickly.
Datadog Cloud SIEM already helps address this challenge by basing its default common data model on the Open Cybersecurity Schema Framework (OCSF), an open standard for normalizing security telemetry. Recently, we also announced prebuilt OCSF normalization pipelines for common sources like AWS CloudTrail, Okta, and GitHub. Since that announcement, our OCSF coverage has expanded to include more sources, spanning network, endpoint, device, collaboration, and more. These supported OCSF pipelines help analysts see consistent, standardized events in Datadog Cloud SIEM right out of the box.
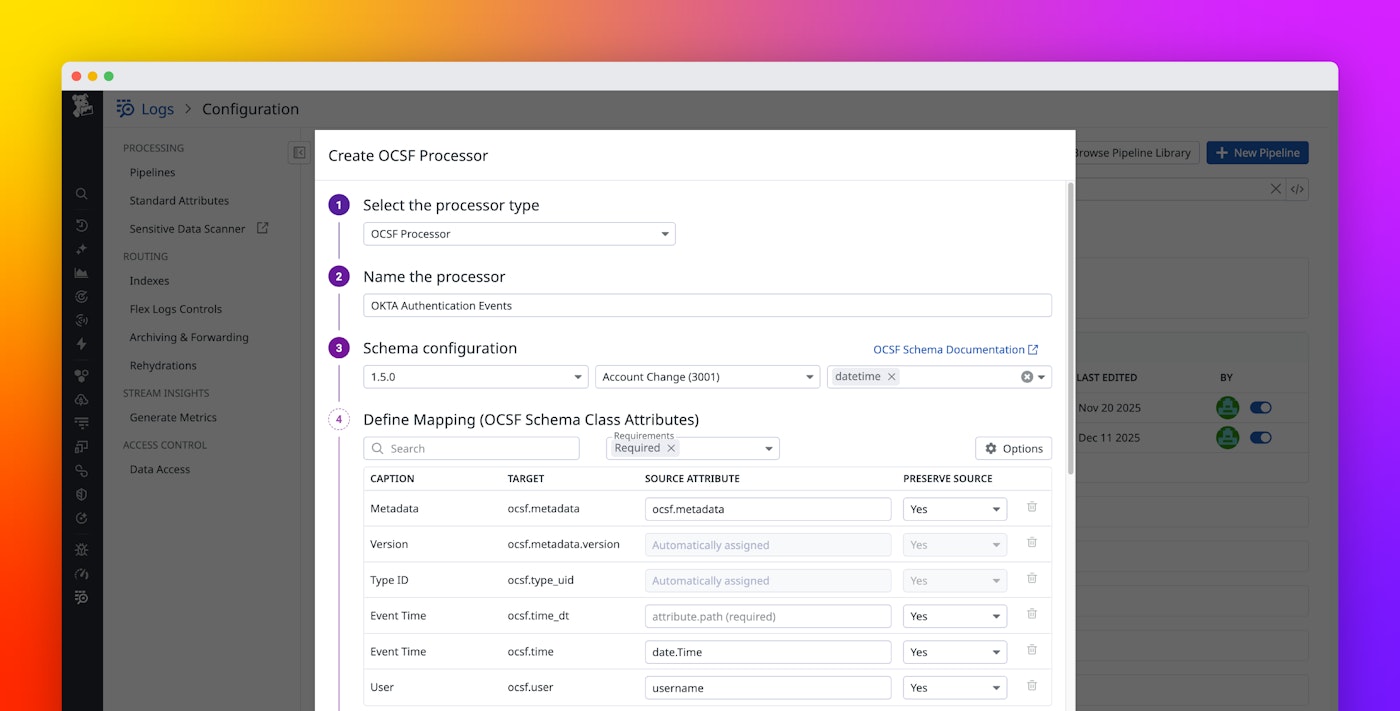
Now, we’re extending OCSF normalization to any log source. Datadog’s new OCSF processor gives you full self-service control over normalization so that you can bring any log data, map it to OCSF, and analyze it in Datadog Cloud SIEM alongside your other security telemetry.
Bring any logs into a common security language
As environments grow more complex, security teams increasingly rely on internal applications, niche SaaS tools, or partner integrations that don’t necessarily come with predefined OCSF mappings. Datadog’s OCSF processor lets teams close those gaps by mapping any log source to OCSF, without requiring any custom engineering work.
Built into Datadog Log Management pipelines, the OCSF processor allows teams to normalize logs into a specific OCSF event class, such as authentication or detection activity. It offers a guided experience to help you normalize logs and ensure that mappings align with the OCSF schema, so normalized events are consistent, accurate, and ready for downstream analysis in Cloud SIEM.
Once processed, custom logs look and behave like native Datadog OCSF events, making them immediately usable for detections, dashboards, and investigations. The post-processor then automatically applies OCSF semantics, enriching events with standard classification fields, and constructing the observables array. As a result, custom data benefits from the same processing, enrichment, and analytics as all other logs and events in the system.
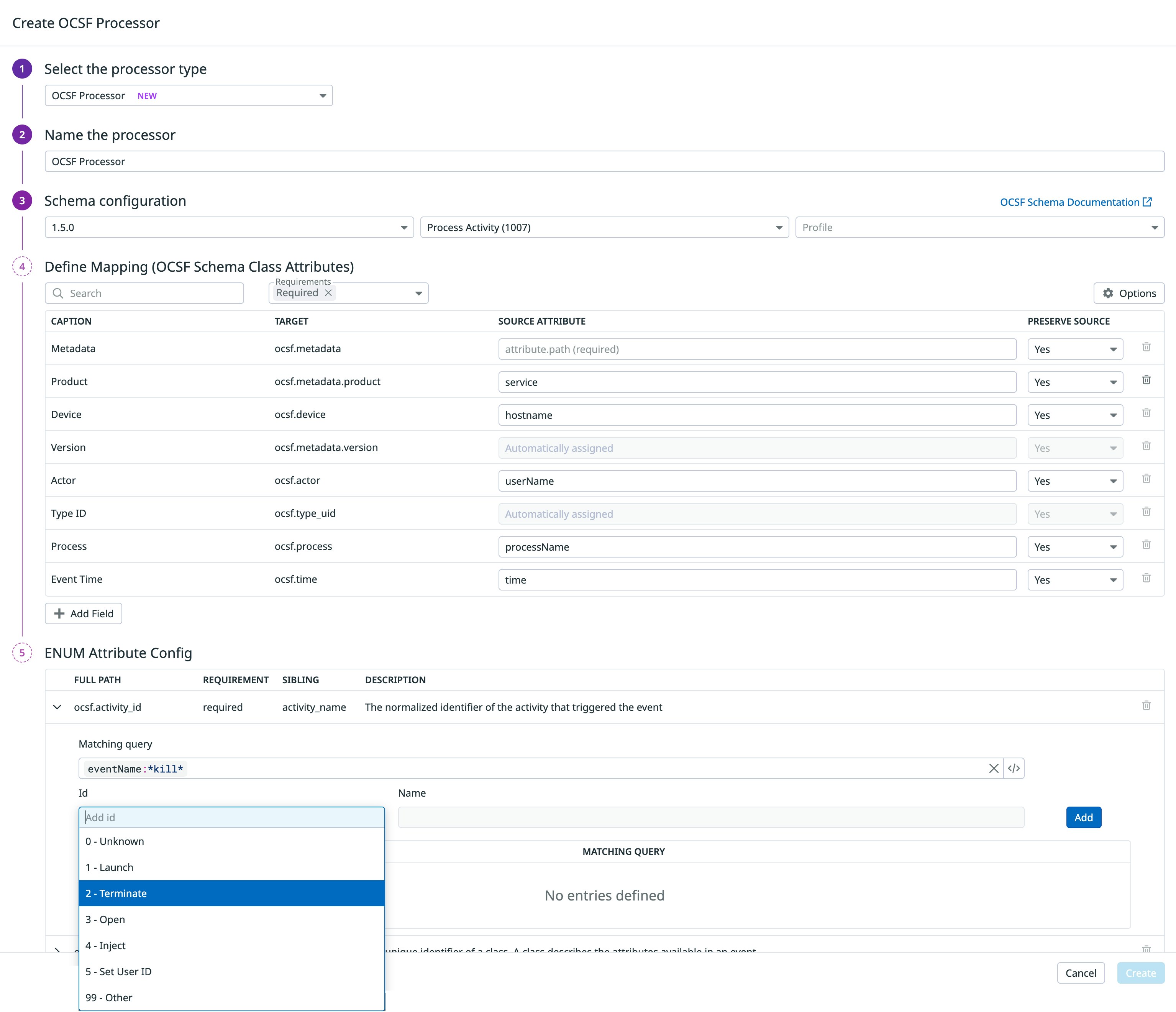
Standardize detections and investigations across multiple data sources
By providing a standard data format for all log sources, OCSF normalization helps teams handle ingestion and analytics at scale. When events share a common schema, security teams can write detection rules once and apply them across multiple sources, reducing the operational overhead and maintenance required for source-specific logic.
For example, with Datadog’s OCSF processor, fields like user.uid, src_endpoint.ip, and activity metadata are consistently populated. This normalization of log data allows analysts to easily correlate related activity across cloud, identity, and custom systems. The result is faster triage, clearer context, and fewer blind spots caused by inconsistent log formats.
Support a flexible, open SIEM operating model
The OCSF processor is part of Datadog’s broader approach to a modern SIEM operating model, one built on flexibility, openness, and customer control. By aligning Cloud SIEM with open standards like OCSF, Datadog helps security teams unify their data around a transparent, extensible schema that works across tools, teams, and environments.
Datadog’s OCSF processor gives teams the flexibility to decide what data to collect, how to normalize it, and where to route it—whether the destination is Cloud SIEM, a long-term archive, or an external data lake. This open approach helps teams reduce schema lock-in, simplify SIEM migrations, and apply analytics and detections consistently as their environments evolve.
Normalize everything without compromise
With its new OCSF processor, Datadog Cloud SIEM extends normalization beyond prebuilt integrations, giving security teams a practical way to bring any log source into a shared security data model without needing to rely on external tools. By making OCSF normalization self-service and consistent, teams can scale as their environments evolve, onboard new data sources with less effort, and reduce operational complexity.
To learn more, view our latest prebuilt OCSF pipelines, or get started with our documentation to create a log pipeline and configure the OCSF processor for your needs. And if you’re not yet a Datadog customer, sign up for a 14-day free trial.