Vera Chan

Lance Malacara

Yash Kumar
Security can quickly become overwhelming for large organizations, with teams processing logs that are fragmented across cloud providers and SaaS platforms, staggering alert volumes, and the need to scale operations efficiently as environments grow. Datadog Cloud SIEM is designed to help teams manage this workload by centralizing insights, detecting threats faster, and prioritizing investigations with rich risk context.
With the addition of Bits AI Security Analyst, Datadog helps teams respond faster by automating triage and accelerating investigations. By working closely with customers, we’ve continued to expand our Cloud SIEM platform to enhance visibility, improve detection, and automate response.
As a result, users can easily:
- Gain unified visibility and context across complex cloud environments
- Detect and investigate threats faster
- Leverage AI and automation to accelerate response and scale operations
Gain unified visibility and context across complex cloud environments
As organizations continue to expand across multi-cloud and SaaS ecosystems, security teams face growing complexity in how they collect, normalize, and analyze data. Logs often arrive in inconsistent formats and are scattered across sources, which makes it difficult to access a comprehensive, accurate view of organization-wide security activity. To detect threats and respond quickly, teams need a centralized and consistent view of all security data.
OCSF Common Data Model: Centralize and normalize logs with log pipelines
Datadog allows teams to ingest data from different sources and automatically normalize and map it to the Open Cybersecurity Schema Framework (OCSF) through prebuilt log pipelines. This OCSF Common Data Model creates a consistent structure for analysis, enabling security teams to correlate events across multiple cloud and SaaS platforms. This consistency allows for prebuilt detection rules that are source-agnostic and apply across multiple attack surfaces.
By automatically mapping disparate data to a consistent schema, analysts can correlate events, scale detection, and investigate threats faster without creating custom parsers or managing inconsistent formats. Teams can also access prebuilt detection rules through the out-of-the-box pipelines.

OCSF pipelines supported today include identity sources such as 1Password, Okta, and AWS CloudTrail; network sources such as Cisco Meraki and Palo Alto Networks; and endpoint sources such as CrowdStrike and Microsoft Windows.
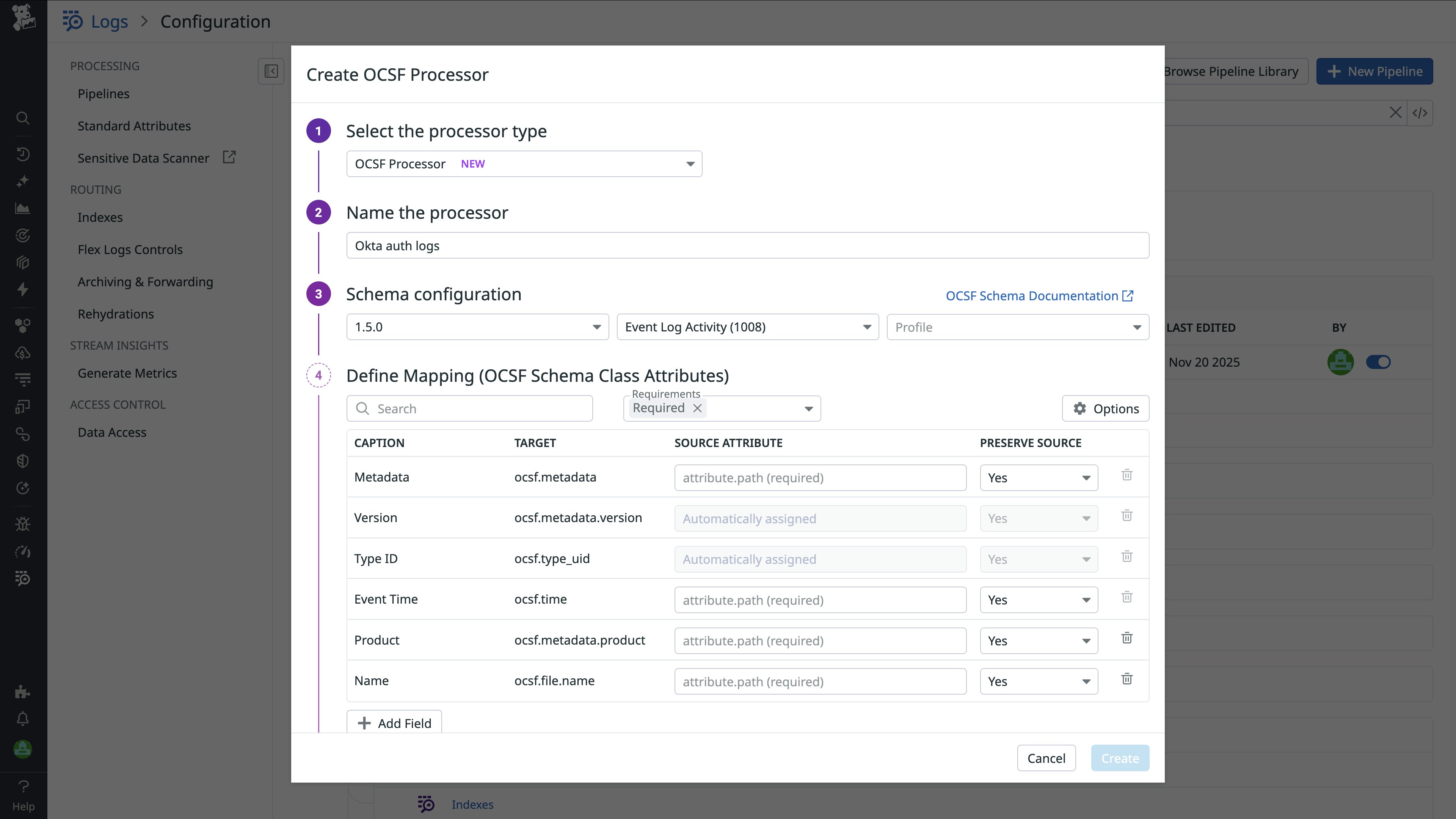
OCSF Processor: Normalize custom data for consistent analysis
For teams with custom logs or specialized tools, the OCSF Processor provides a flexible, guided experience for users unfamiliar with the OCSF framework to normalize events to OCSF. This self-service capability reduces friction when integrating new data sources and helps teams maintain consistent visibility across all environments, even those with unique or legacy systems. Additionally, security teams may need to ingest and analyze new log sources faster than vendors can release new integrations. The OCSF Processor gives teams the flexibility to do so on their own by enabling them to transform and normalize custom logs into the OCSF framework. The processor also supports more complete detection coverage on their own timelines, providing a consistent path for incorporating new or custom data.
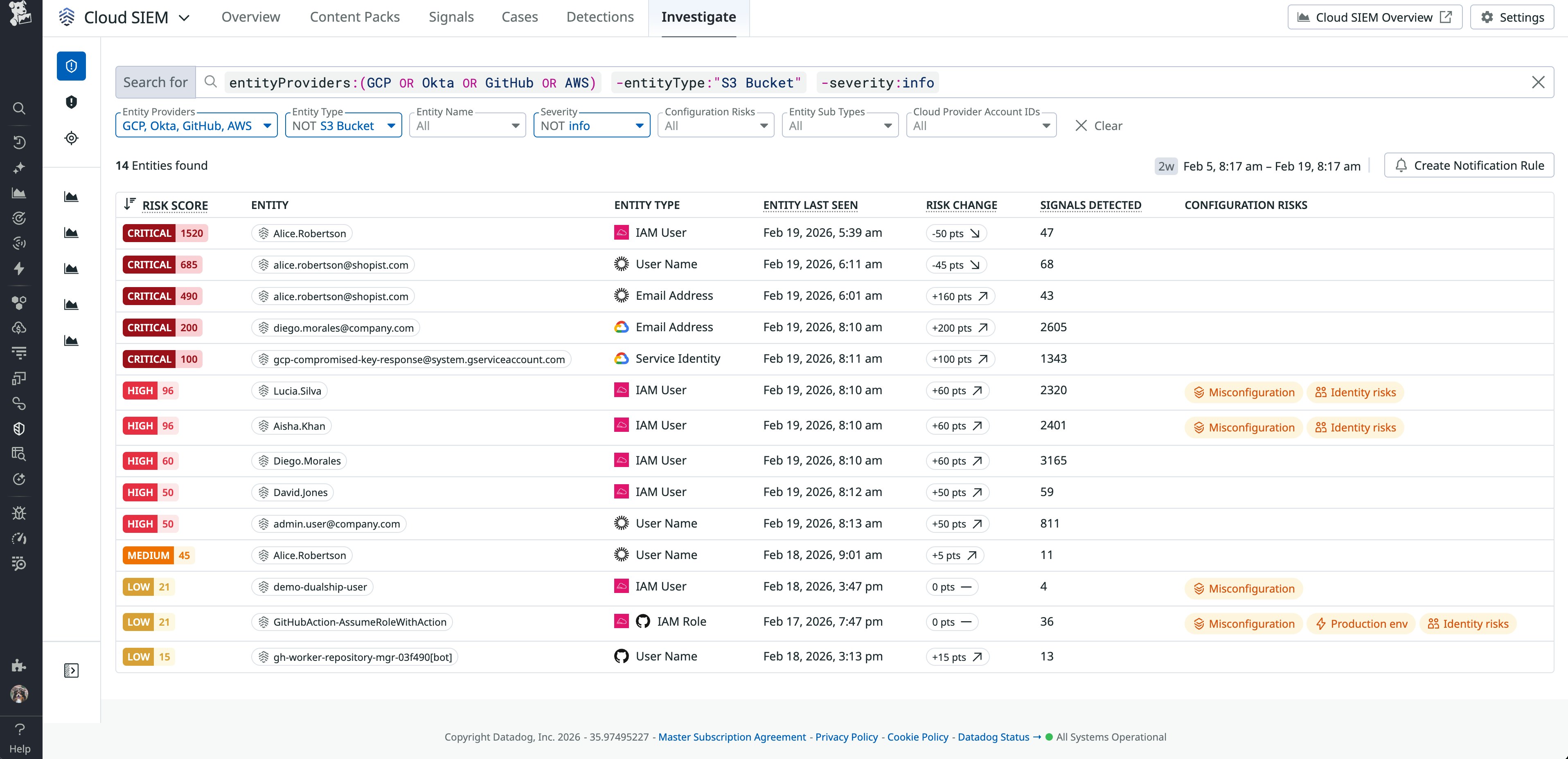
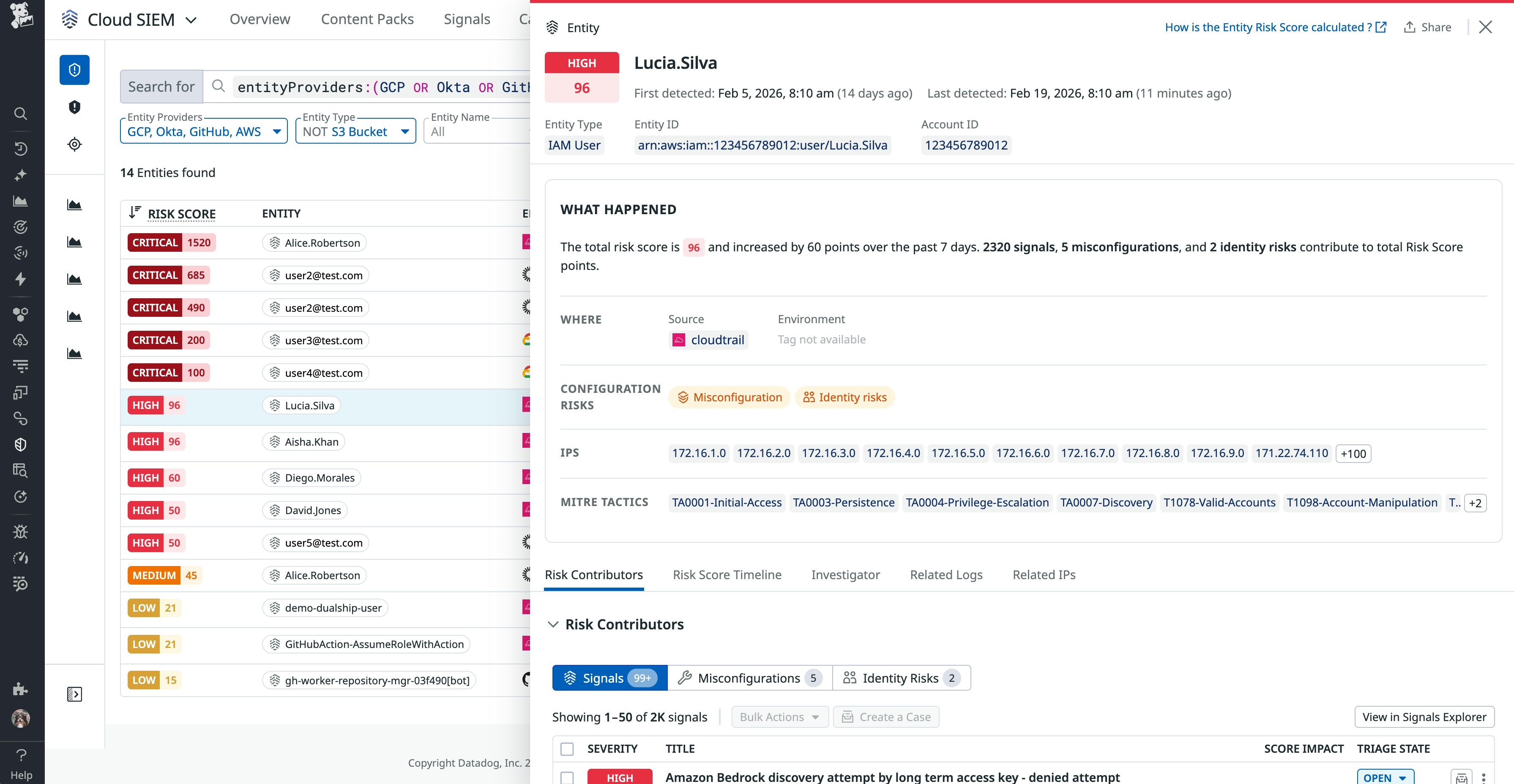
Risk Insights: Prioritize effectively with identity and behavior insights
Risk Insights helps security teams correlate activity and user identity across multiple sources, giving analysts the context they need to investigate threats efficiently and prioritize the most important alerts. These insights draw on a number of variables, such as the severity level and frequency of any signals associated with an entity, to calculate an easy-to-interpret risk score. In addition to AWS, Google Cloud, and Azure entities, Risk Insights now also includes support for identity sources such as Okta and GitHub, with more integrations on the way.
Integrations and Content Packs: Broad coverage with fast onboarding
Integrations and Content Packs give security teams a fast way to build robust monitoring processes with minimal setup. Integrations enable teams to bring telemetry from endpoints, identity providers, email systems, cloud audit platforms, networks and infrastructure, and collaboration tools directly into Cloud SIEM. Content Packs include prebuilt detection rules, dashboards, and Workflow Automation blueprints, all of which help teams start monitoring and investigating critical systems without manual configuration.
Together, these capabilities give security teams a complete and consistent view of their environment, improve detection and investigation speed, and make it easier to scale monitoring across complex and growing infrastructure. Cloud SIEM includes integrations and Content Packs for more than 90 platforms, such as AWS CloudTrail, Google Workspace, Datadog Audit Trail, Microsoft 365, Nginx, 1Password, Auth0, Okta, Azure, Fastly, and Zendesk.

Detect and investigate threats faster
To detect threats quickly, security teams need to ingest and examine signals from their entire stack. However, this often leads to alert fatigue, and critical incidents risk being buried under noise.
Cloud SIEM connects signals across sources and automatically highlights related activity, helping analysts prioritize the most pressing incidents and investigate more efficiently. It also provides a foundation for faster, more targeted threat analysis.
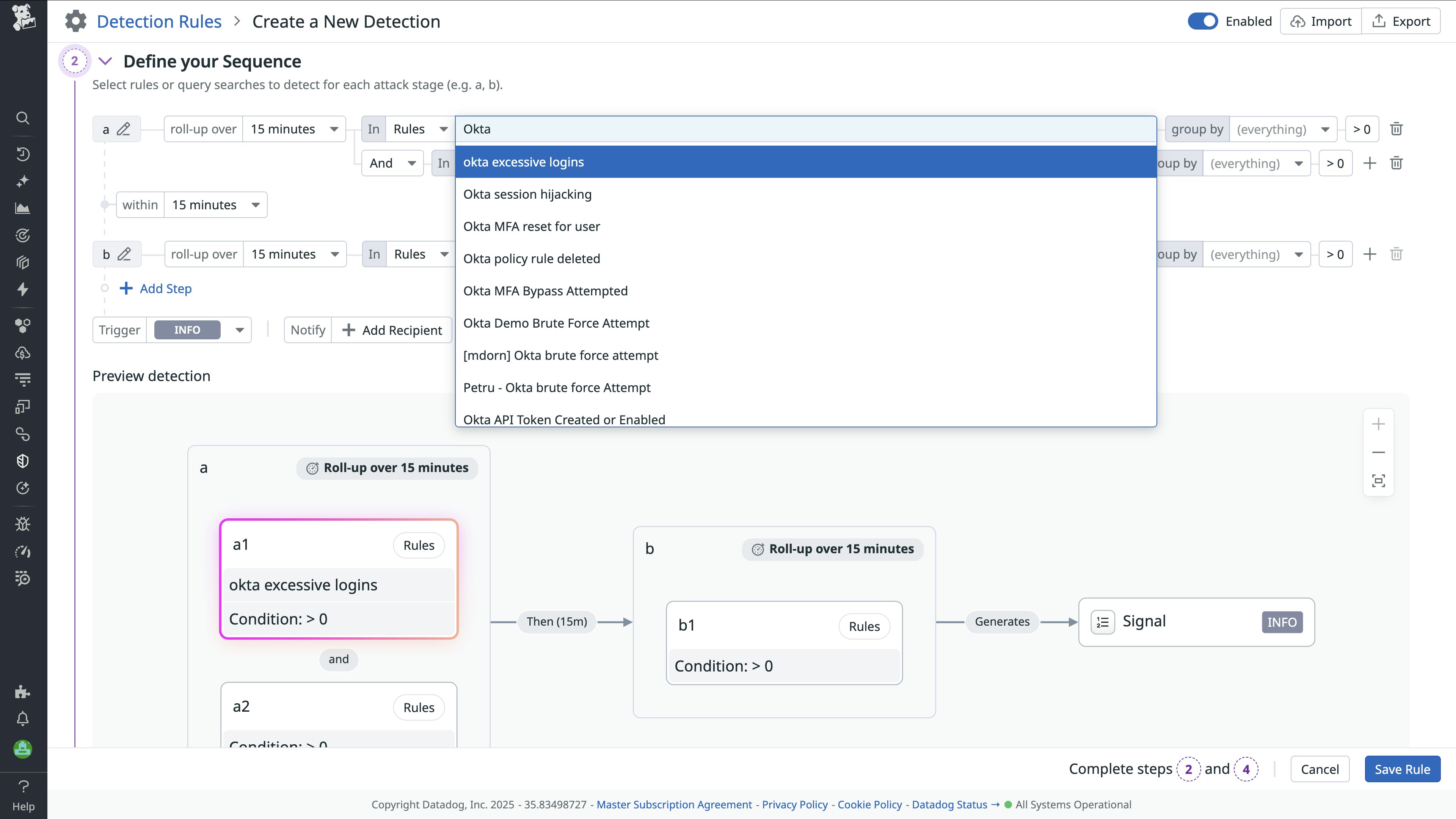
Sequence Detections: Uncover coordinated attack patterns
Security incidents are rarely isolated events. Attackers often move through multiple stages, from initial access to privilege escalation and data exfiltration, leaving behind a series of seemingly unrelated signals.
With Sequence Detections, security teams can now identify and correlate these linked behaviors within Cloud SIEM. This capability allows analysts to define ordered sequences of events and specify combinations of users, actions, and time frames that should trigger a signal. By correlating related activity across sources and time windows, Datadog helps surface coordinated attacks that individual rules might otherwise miss.
As a result, teams gain a more complete picture of incidents and reduce noise from single-event detections, enabling faster, more confident investigation and response.
Threat Intelligence: Enrich alerts with context you control
Effective investigations depend on context. With Threat Intelligence, analysts can enrich alerts with known indicators of compromise (IOCs), such as malicious IPs, domains, or file hashes, to better understand whether activity in their environment is part of a known campaign. By automatically correlating internal signals with relevant external threat data, analysts can prioritize alerts more effectively and respond faster with greater confidence.
Datadog’s built-in feeds provide global threat data, while Bring Your Own Threat Intelligence allows teams to integrate their own internal or third-party feeds into Cloud SIEM. This gives organizations full control over the threat data they rely on, whether it comes from commercial sources, industry sharing groups, or custom intelligence pipelines.
Automate and scale security operations with confidence
As enterprise environments grow, security teams manage more alerts, data sources, and workflows than ever before. Scaling operations efficiently while maintaining speed and accuracy is a constant challenge. Analysts need tools that help them automate repetitive tasks, simplify investigations, and adapt quickly to new threats and data sources—all without adding operational risk. Cloud SIEM helps teams automate and scale with confidence by combining AI-driven investigation, self-service data normalization, low-code automation, and migration tools that make modernization seamless.
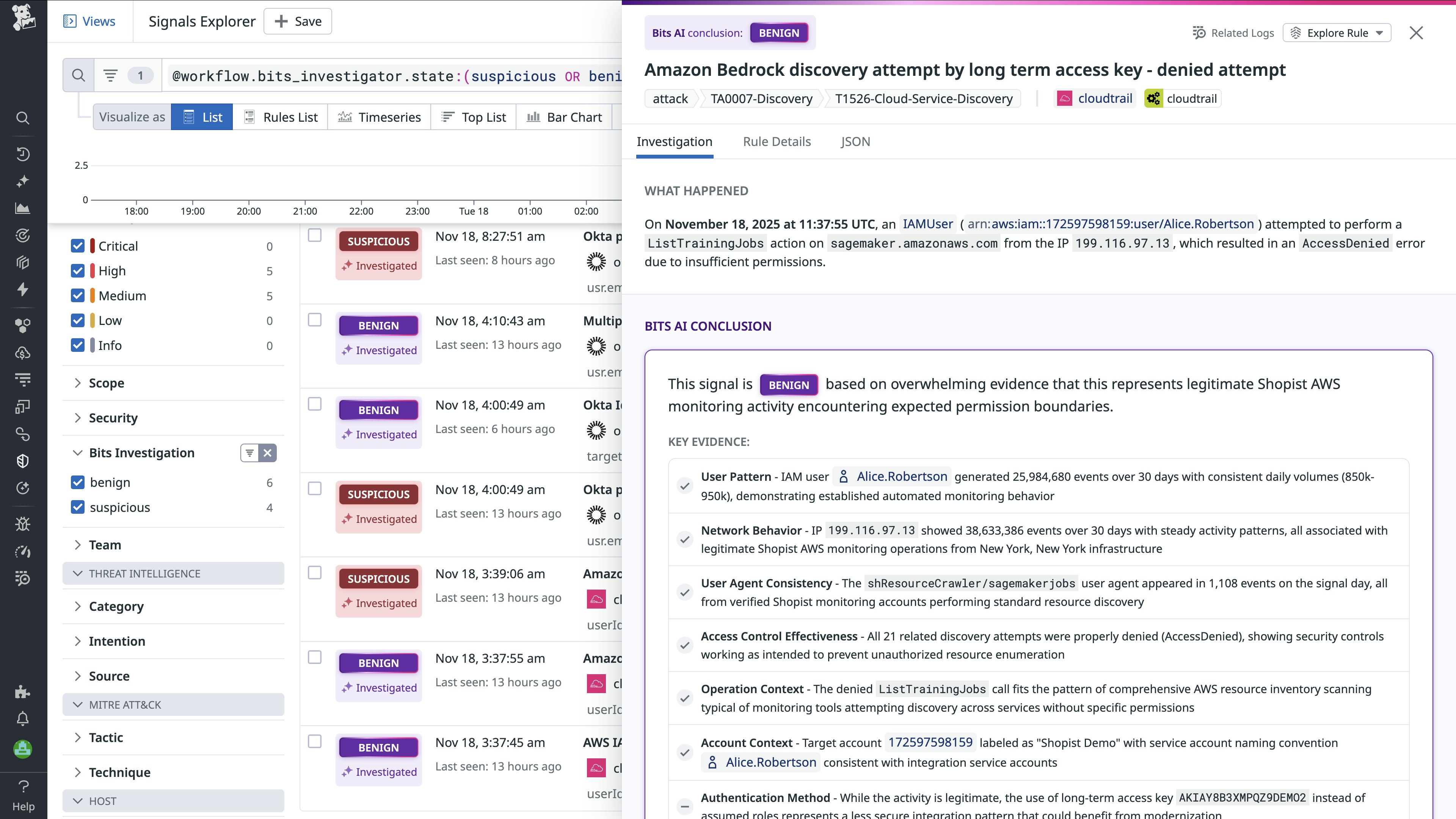
Bits AI Security Analyst: Automate Cloud SIEM investigations
As alert volumes continue to increase, analysts spend significant time analyzing and triaging signals. Bits AI Security Analyst uses generative AI to autonomously investigate SIEM signals. Bits AI assesses whether a signal is benign or suspicious, summarizes key evidence, and shows detailed investigative steps with accompanying queries. This reduces the toil of manual triage and helps teams surface and resolve high-priority incidents faster. To learn more, you can sign up for the Security Analyst Preview.
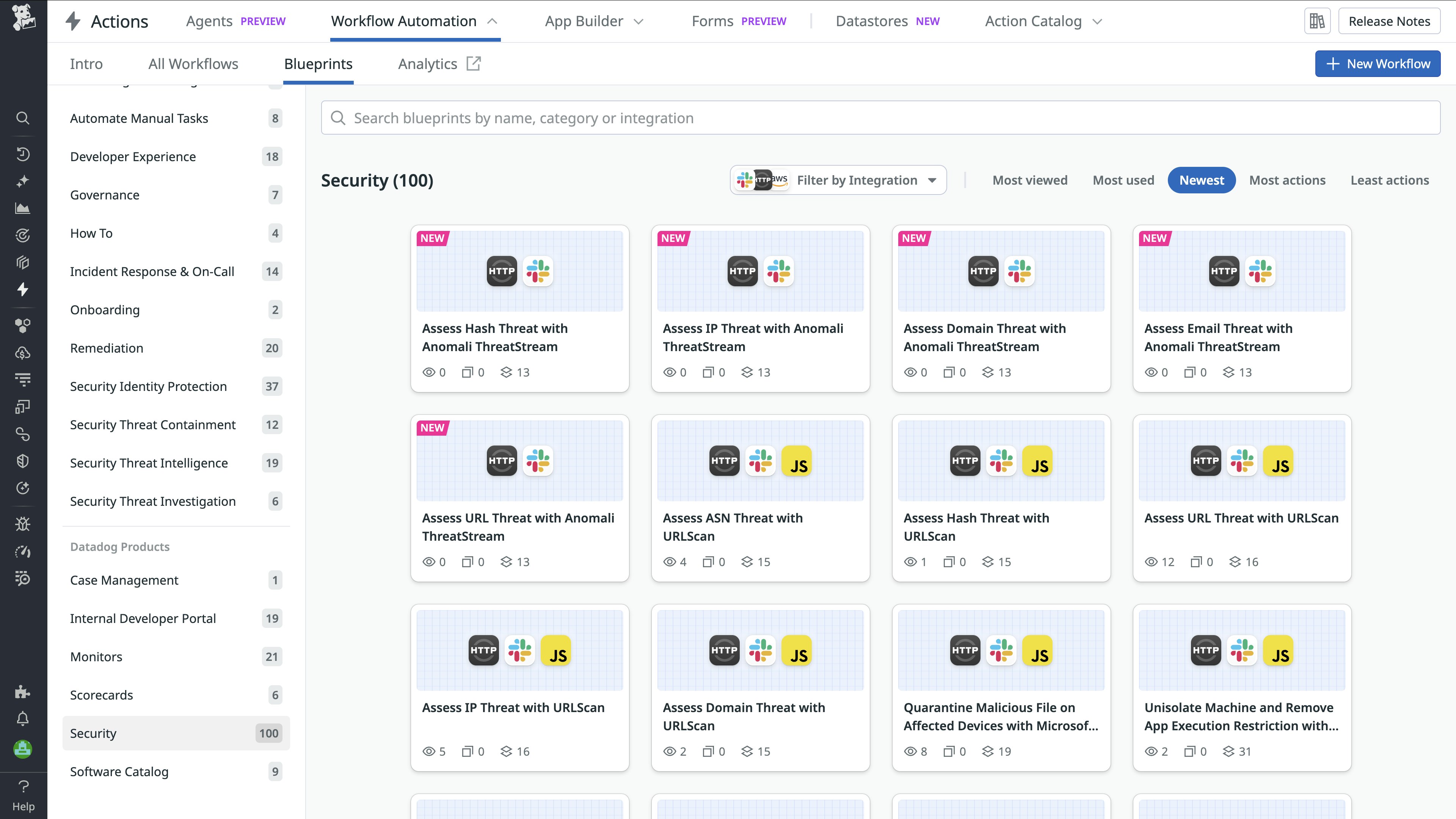
SOAR blueprints: Automate response actions
Many response processes still depend on manual playbooks that vary across tools and teams. Security Orchestration, Automation, and Response (SOAR) Workflow Automation blueprints standardize and automate those common actions—enriching alerts, creating tickets, disabling accounts, or escalating incidents—directly within Datadog. Teams can respond consistently and confidently while maintaining human oversight for higher-risk decisions.
App Builder for security: Customize automation at scale
Every security team has unique processes that evolve as their environment changes. With App Builder, organizations can create custom apps that orchestrate actions across Datadog and third-party tools. This flexibility allows teams to adapt automation to their specific needs and scale their response playbooks as they grow. For example, teams can create apps that automatically block IP addresses and disable user accounts in response to suspicious activity, enabling faster remediation upon detection.

Migration and automated detection rule conversion tools
Modernizing from legacy SIEMs can be time-consuming and risky if teams must rebuild detection logic from scratch. Datadog simplifies the transition by ingesting data from any source through pipelines and by supporting rapid onboarding and operationalization with Content Packs and an intuitive query language designed for fast adoption.
Teams can also work with our trusted partners to automate dashboard, alert, and detection rule conversion, which helps accelerate migration efforts. This support enables organizations to carry existing detections and workflows into Cloud SIEM with minimal disruption, reducing operational risk and accelerating the time to value. As Rishi Divate, Director of Business Development at Crest Data, a Datadog partner, notes, “Our partnership with Datadog accelerates observability and SIEM migrations by up to 60% and reduces cost, risk, and complexity.”
Migrating to a new SIEM is more than a technical shift. It’s an opportunity to reduce operational overhead and give security teams more time for higher-value work. In one recent migration, a security team consolidated platforms, eliminated 20 hours of weekly administrative work, and saw search performance increase by a factor of five compared to their previous system. They achieved 30% license cost savings, reduced AWS egress costs by $120,000, and gained 365 days of instantly searchable logs via Flex Logs—eliminating cold-storage delays and expensive rehydration cycles. As a result, the team now spends less time on maintenance and more time advancing their security program with greater speed and confidence.
Start safely scaling your security operations
Across industries, customers are using Datadog Cloud SIEM to modernize how they detect, investigate, and respond to threats in the cloud. By unifying visibility across complex environments, accelerating threat detection, and automating investigation and response, Cloud SIEM enables security teams to keep pace with the scale and speed of modern infrastructure.
See our documentation for more information and to get started. If you’re new to Datadog, you can sign up for a 14-day free trial to get started.