Jordan Obey
Amazon Security Lake allows customers to build security data lakes from integrated cloud and on-premises data sources as well as from their private applications. Directing your security telemetry into a unified data lake makes it easier to manage, analyze, and route security-log and event data to third-party SIEM solutions that leverage that telemetry.
We are pleased to announce that security logs and events stored in Amazon Security Lake can be easily forwarded to Datadog and analyzed by Datadog Cloud SIEM, providing you with a simplified way to analyze security logs from various sources for real-time threat detection.
Setting up the Amazon Security Lake integration is quick and easy, so you can start using Datadog to analyze your security logs within minutes. Simply install Datadog’s AWS integration, add Datadog as a subscriber in the Amazon Security Lake console, and update your IAM role permissions to enable Datadog to fetch security-log files. See our documentation for more details.
In this post, we’ll look at how this integration helps improve your security posture by enabling you to identify and investigate threats from across your environment with out-of-the-box security detection rules, dashboards, and Datadog Log Management tools.
Analyze security logs from Security Lake with OOTB detection rules and dashboards
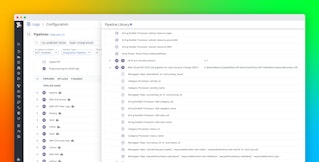
Datadog Cloud SIEM provides out-of-the-box (OOTB) detection rules and threat intelligence that map security-related logs and events against suspicious IP addresses and attack patterns that bad actors have previously leveraged. Once you set up our integration and Datadog begins ingesting Security Lake logs and events, you will automatically receive signals associated with suspicious activity. This way, instead of needing to forward logs and events separately, you can forward all security-related telemetry data from your Security Lake directly to Datadog for quick and easy analysis.
Logs from Security Lake will also be collected and visualized in Datadog’s OOTB IP Investigation dashboard. This dashboard can help you execute IP-based security investigations by providing you with a centralized view of key IP security data such as security signals, unusual HTTP requests, and traffic from malicious IPs.

Use saved views to quickly highlight logs surfacing security-related issues
Since Security Lake aggregates a large volume of security telemetry, it’s particularly important for you to have an efficient way to explore the resultant data. With Datadog Log Management and our Log Explorer, you can search for and view security-related logs collected from Security Lake. You can then use custom and OOTB saved views—which enable you to isolate specific subsets of logs—to focus the Log Explorer on a specific contextual scope. For example, you can create a saved view that narrows your view down to VPC flow logs and CloudTrail logs that indicate security-related issues such as rejected VPC traffic and AccessDenied errors. Narrowing your view down to a specific subset of logs enables you to quickly identify security-related issues for faster troubleshooting.

Let Datadog fetch your Security Lake logs today
Amazon Security Lake helps customers improve their security posture by aggregating security telemetry into a centralized pool that can then be sent to Datadog. To learn more about how you can ingest Security Lake telemetry to detect threats and explore issues with Datadog Cloud SIEM and Log Management, please check out our documentation here.
If you aren’t already using Datadog, sign up today for a 14-day free trial.