Aaron Kaplan

Arjun Katragadda

Christophe Tafani-Dereeper
Cloud environments, in all their dynamic complexity, demand careful monitoring by DevOps and security teams. But the sheer abundance of telemetry data associated with the thousands of resources, users, and roles that comprise these environments can make monitoring a formidable task, causing security risks and other issues to be all too easily overlooked.
We’re excited to announce Datadog Cloud SIEM Investigator for Google Cloud, which provides crucial visibility into Google Cloud environments for DevOps and security teams. This release complements the existing availability of Cloud SIEM Investigator for AWS, with support for Microsoft Azure coming soon. Cloud SIEM Investigator now leverages Google Cloud Audit Logs to help teams visualize activity in resources such as Google Cloud Storage (GCS) buckets and Google Compute Engine (GCE) instances, and correlate this information with entities such as service accounts and end user identities.
In this post, we’ll provide an overview of how the Cloud SIEM Investigator enables you to:
- Visualize Google Cloud activity and drill down into specific entities
- Improve cross-team collaboration on investigations into cloud resources
Visualize Google Cloud activity and drill down into specific entities
Datadog Cloud SIEM Investigator enables DevOps and security teams to answer key questions when investigating changes or incidents in their Google Cloud environments. It helps them quickly determine:
- Which end users and service accounts have interacted with a resource
- The actions taken by end users and service accounts within a given time frame, and whether or not they resulted in errors
- The specific operations performed on specific resources
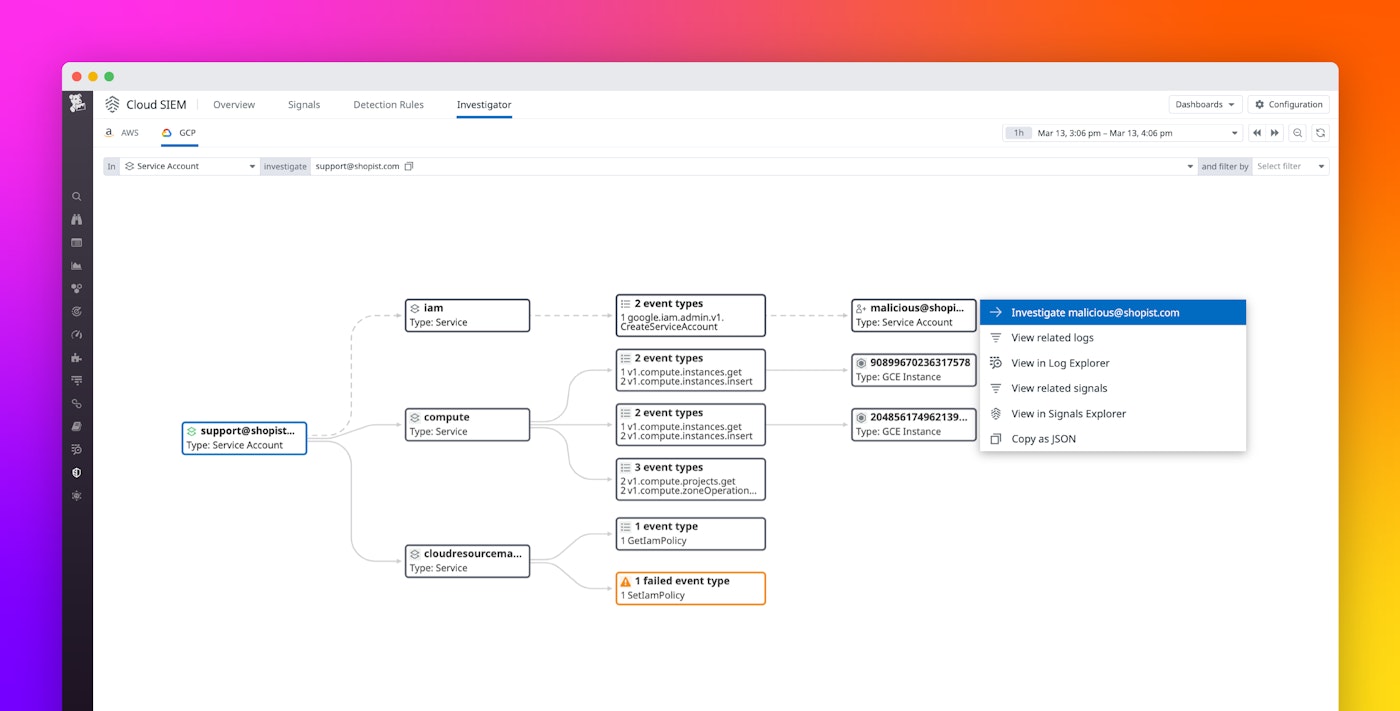
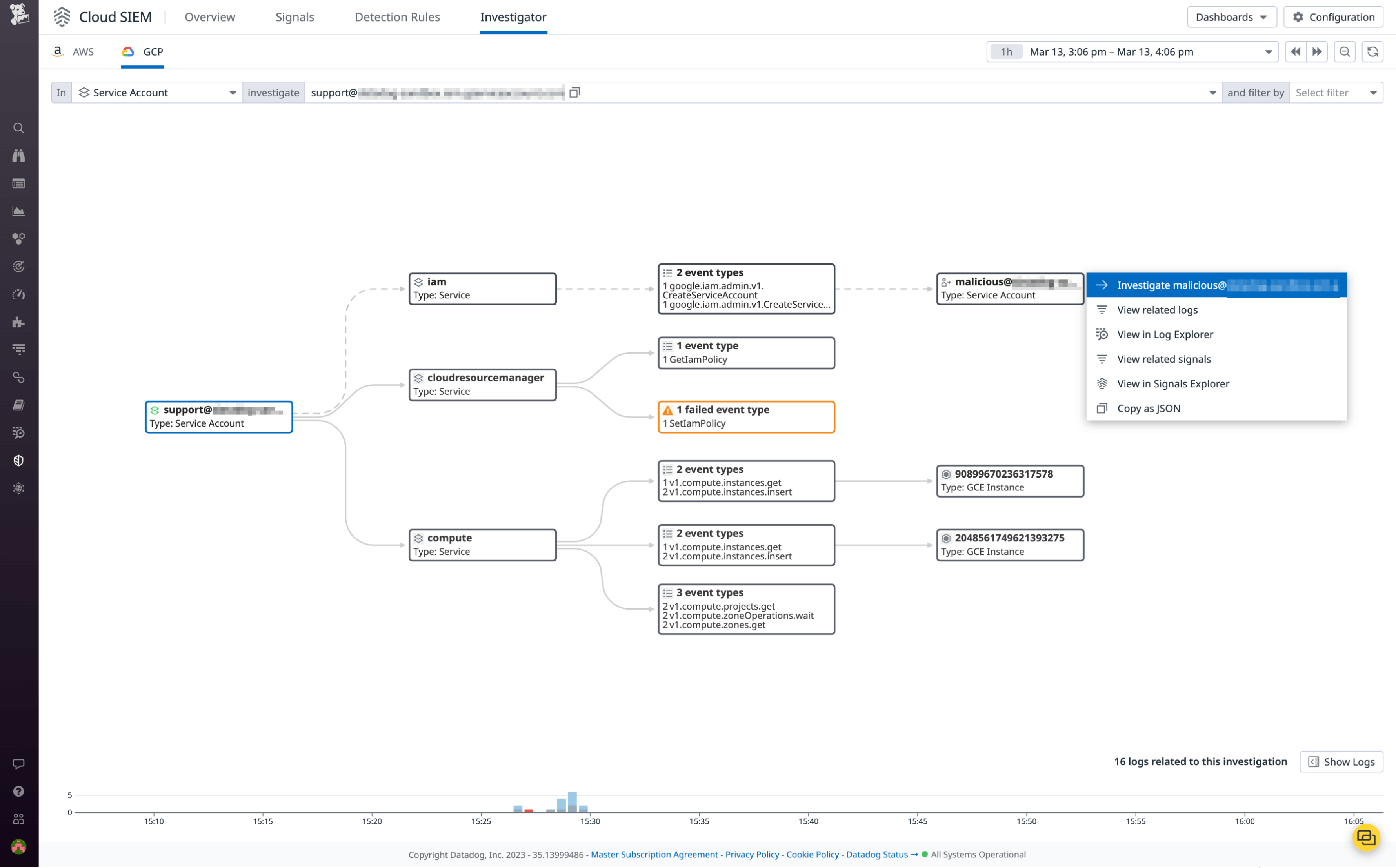
For example, security and DevOps teams can analyze all activity of a specific service account to determine if that account has interacted with business-critical resources, such as GCS buckets or GCE instances. The following screenshot shows a Cloud SIEM Investigator breakdown of an instance in which a service account attempts to create another service account, grant it editor permissions on a project, and launch multiple compute instances. This type of activity may be symptomatic of a compromised account, so it’s important to utilize the insights provided by Cloud SIEM Investigator to ensure legitimacy. By reviewing associated security signals, security teams can refine their investigations to determine whether accounts have been compromised.
Improve cross-team collaboration on investigations into cloud resources
When investigating potential threats in large-scale cloud environments, context is key. In these situations, DevOps may lack the frame of reference to properly assess activity logs. Meanwhile, security teams may lack critical visibility into infrastructure. Discrepancies like these can hinder overall investigations, making it hard to pick out stealthy attacks from business as usual.
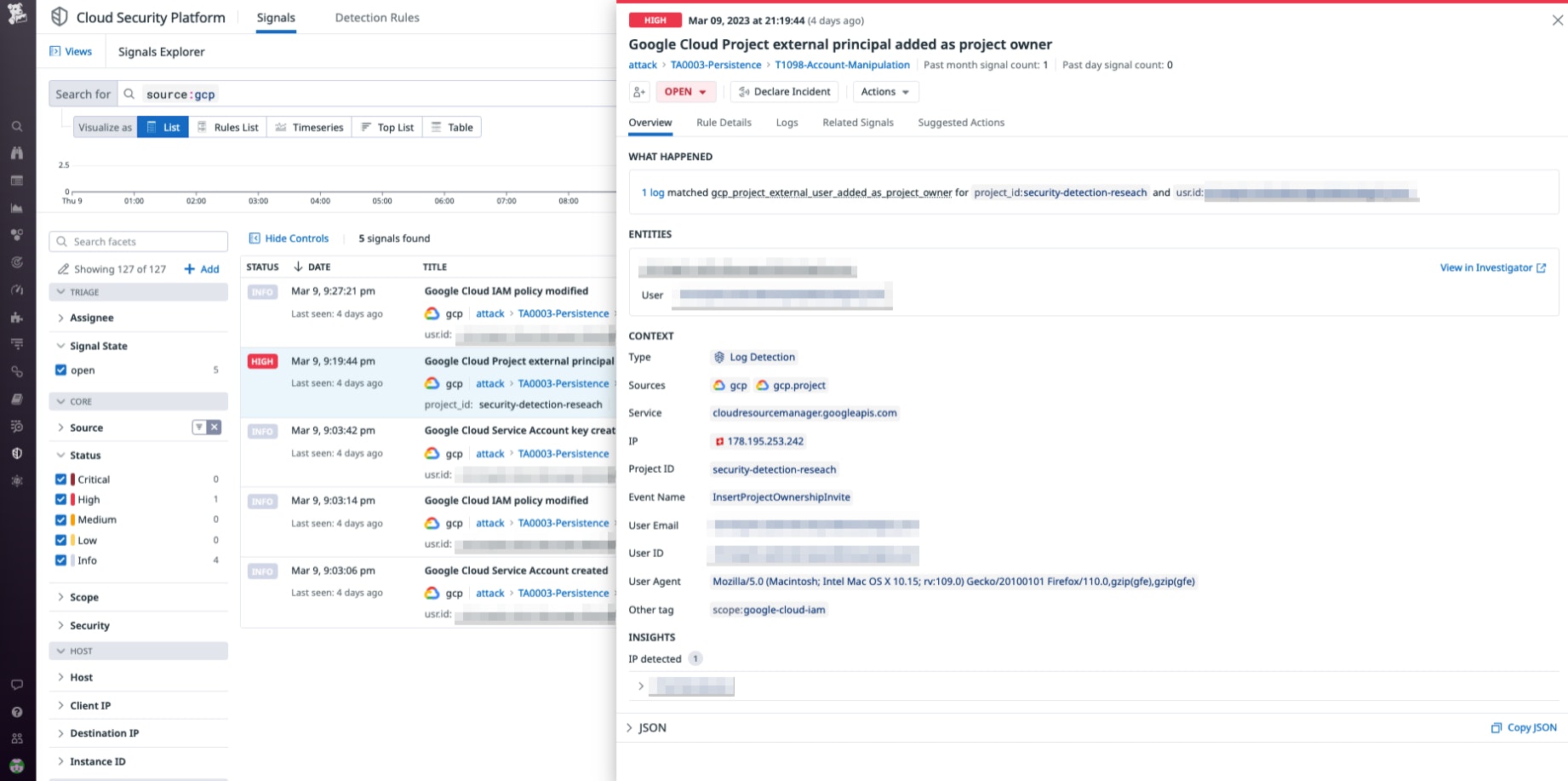
Datadog Cloud SIEM Investigator is tightly integrated with both the Log Explorer and Security Signals, allowing disparate teams to work together on identifying the sources of flagged events or logs, regardless of their entry point. For example, Datadog Cloud SIEM generates a security signal when an external user is granted owner permissions on a project, or when a new service account is created. The following screenshot shows a security signal that is triggered when a user modifies permissions and creates a new service account.
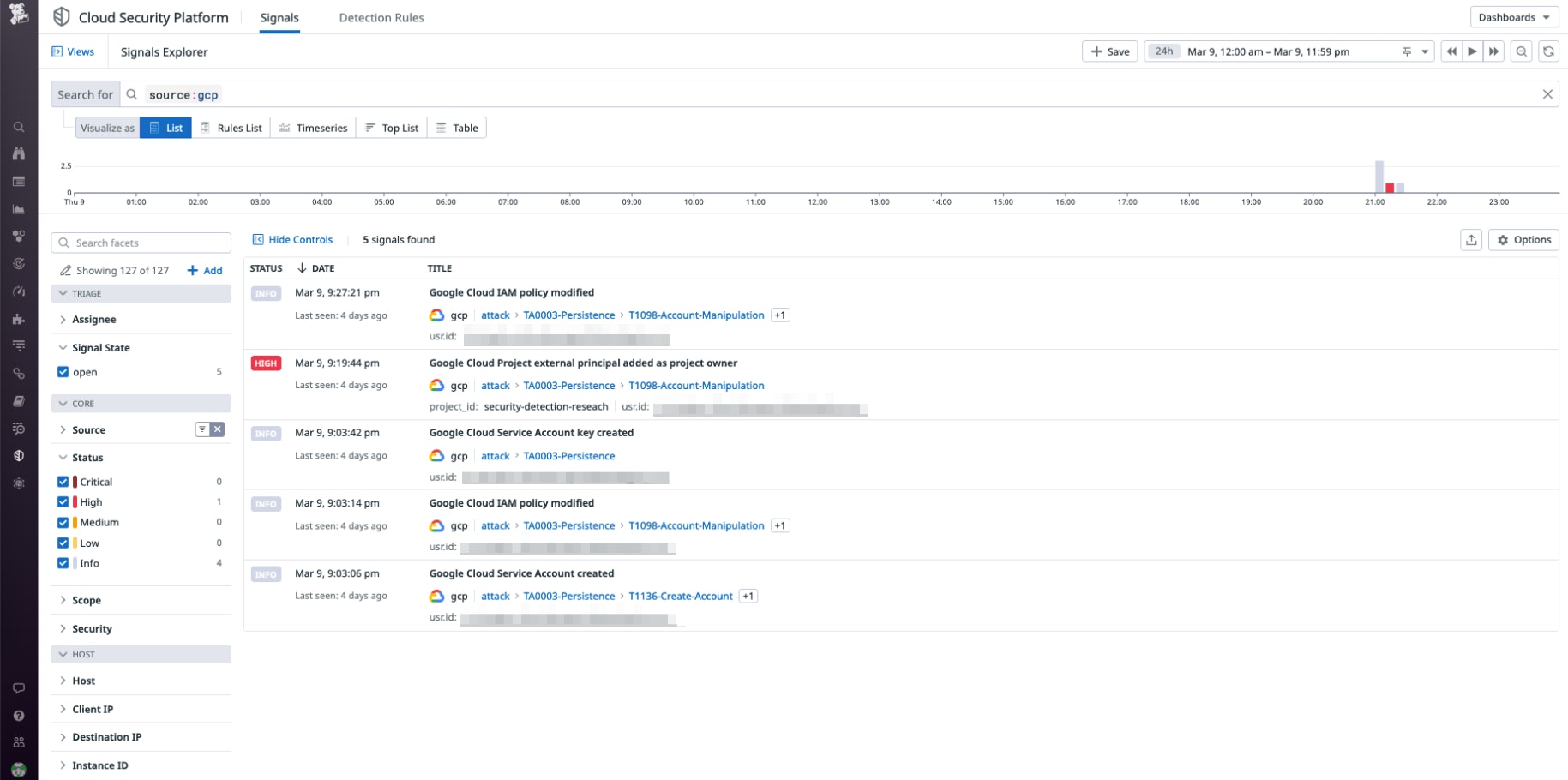
Below, we can see some of the data security signals provide on end users and their specific actions.
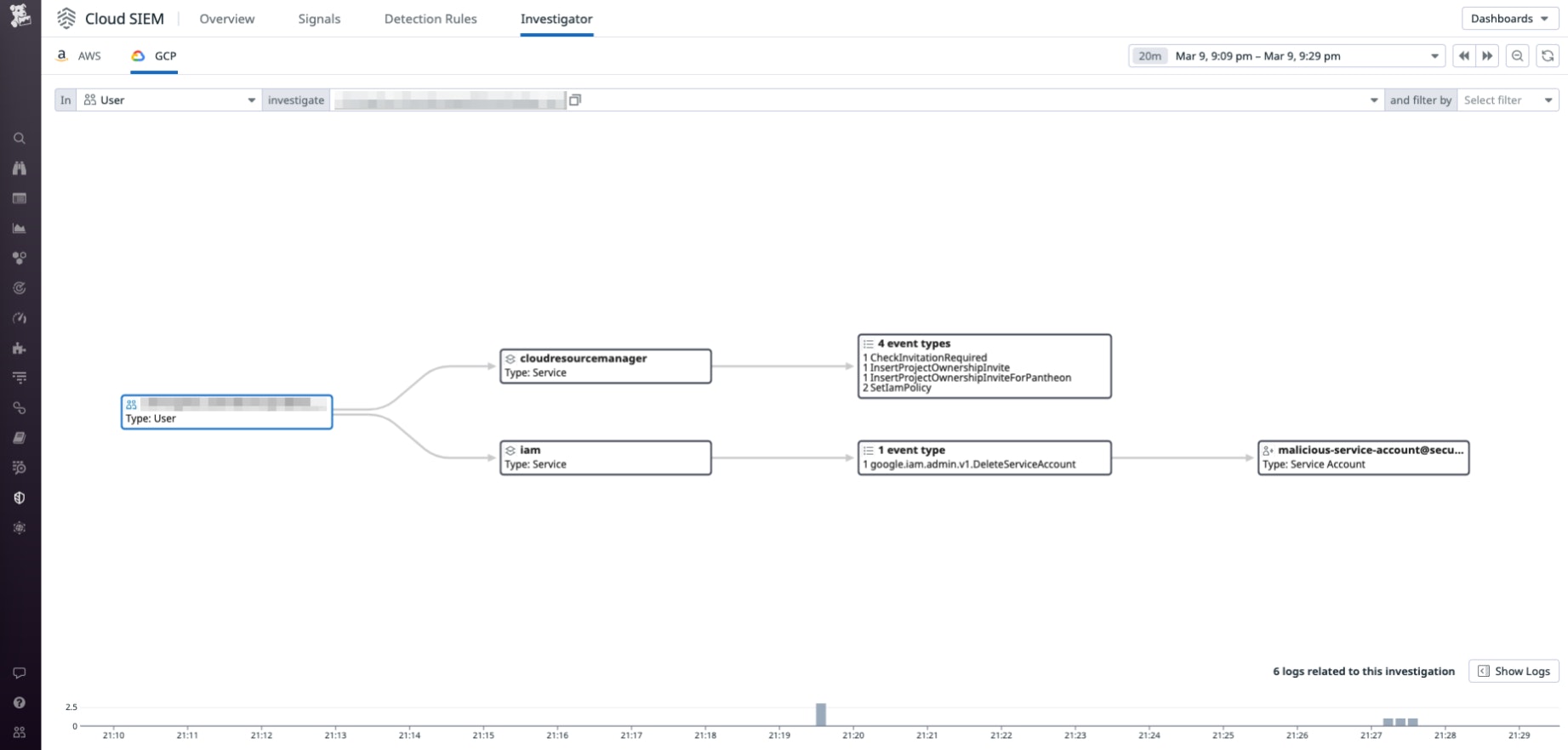
Finally, we can see how the Investigator maps out this activity in a clear, schematic fashion.
Get enhanced visibility into your Google Cloud environment today
With Datadog Cloud SIEM Investigator, organizations can now visualize activity throughout their Google Cloud environments, enabling them to quickly determine the interactions of end users and service accounts with resources such as GCS buckets and GCE instances. This visibility enables DevOps and security teams to align in their investigations of incidents and events and quickly get to the bottom of issues. Check out our documentation to learn more. If you’re new to Datadog, sign up for a 14-day free trial today.