Vera Chan

Eitan Moriano

Nicole Parisi

Amber Tunnell
As cloud environments become more complex, security teams are inundated with alerts, many of which require repetitive, manual triage across tools and teams. Without automation, analysts are forced to manage disconnected signals, jump between platforms, and rely on improvised processes to respond. This slows response times and strains limited resources, contributing to burnout and making it harder to contain threats before they escalate.
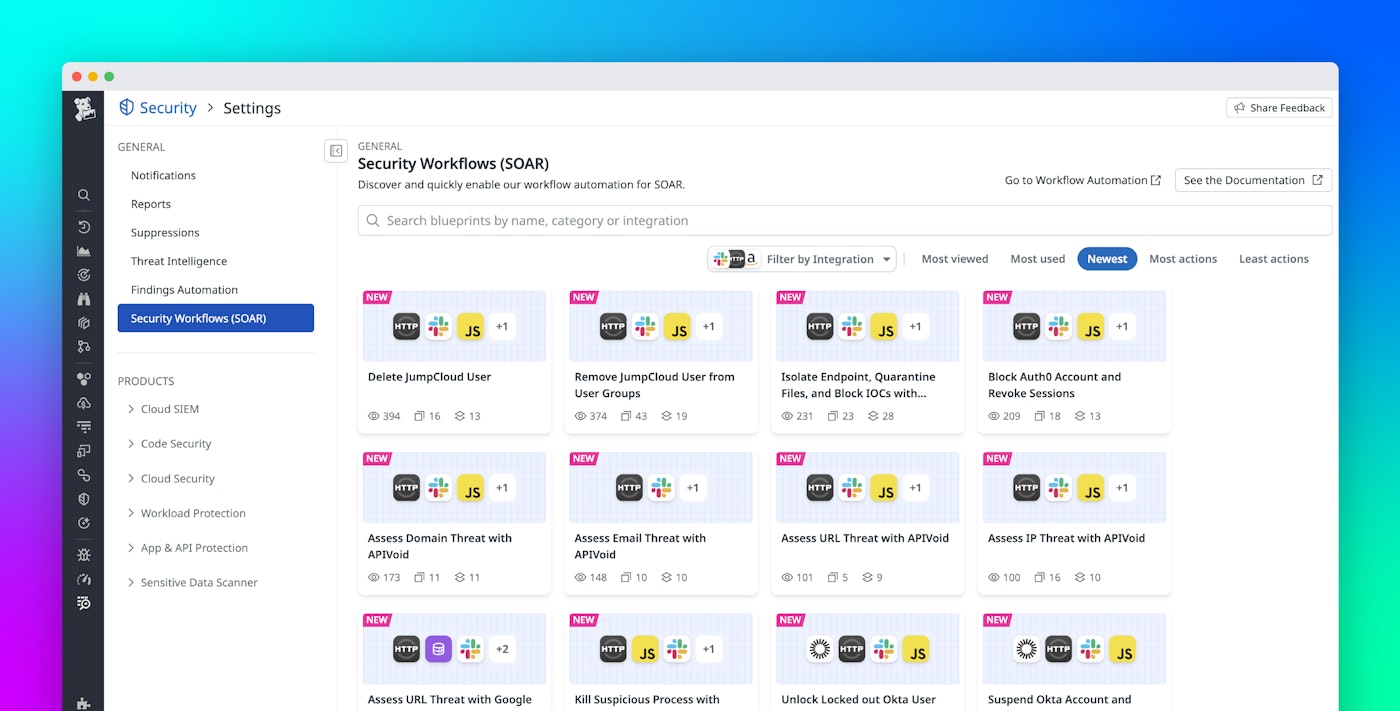
To address these problems, we’ve expanded Datadog Security Orchestration, Automation, and Response (SOAR) to bring security automation directly into Datadog Cloud SIEM. Prebuilt, customizable blueprints enable teams to automate key security workflows that can enrich, triage, escalate, and respond to threats without manual effort. Integrated case management streamlines collaboration, while out-of-the-box blueprints help standardize responses to common threats like unauthorized access or malware detection. By unifying detection, investigation, and response, Datadog SOAR workflows help security teams respond faster and more confidently.
In this post, we will highlight several of our newest SOAR workflows, including:
- An Identity and Access Management (IAM) workflow that automates responses to suspicious logins and account compromises
- An Endpoint Detection and Response (EDR) workflow that speeds up the investigation and containment of endpoint threats
- A Threat Intelligence Enrichment workflow that enriches alerts with external data so you can prioritize and respond more effectively
Automate identity protection with IAM workflows
Identity and Access Management (IAM) workflows help automate detection and response to suspicious user activity, playing a key role in containing active threats. With tools like Microsoft Entra ID, Google Workspace, Okta, Auth0, and JumpCloud, organizations can quickly respond to potential account compromise by triggering actions like disabling accounts, killing sessions, enforcing multi-factor authentication (MFA), and prompting an immediate password reset. Automating these responses ensures fast containment, reduces the risk of human error, and improves consistency across incidents.
Automate removing an Okta user from assigned groups and apps
When an employee leaves the company or changes roles, there’s a risk that their access to sensitive applications and systems remain active. If these accounts are not properly deactivated, they could become targets for malicious actors looking to use valid but outdated access permissions to infiltrate the network. The Datadog SOAR Remove Okta user from assigned groups and apps workflow ensures outdated permissions are removed quickly, reducing the risk of insider threats or unauthorized access.
Here’s how this workflow checks and removes a user’s access to assigned groups and applications in Okta:
- Verify user: First, the workflow checks if the user (via email or ID) exists in Okta.
- Retrieve assigned apps and groups: If the user is found, the workflow pulls a list of all apps and groups assigned to that user.
- Admin approval: The details of the assigned apps and groups are sent to the admin for approval, ensuring the decision is authorized.
- Revoke access: If the admin approves, the workflow automatically revokes the user’s access to the assigned apps and groups.
- Stop workflow: If the admin does not approve, the workflow halts, leaving the user’s access unchanged.
The following screenshot shows the blueprint for this workflow:
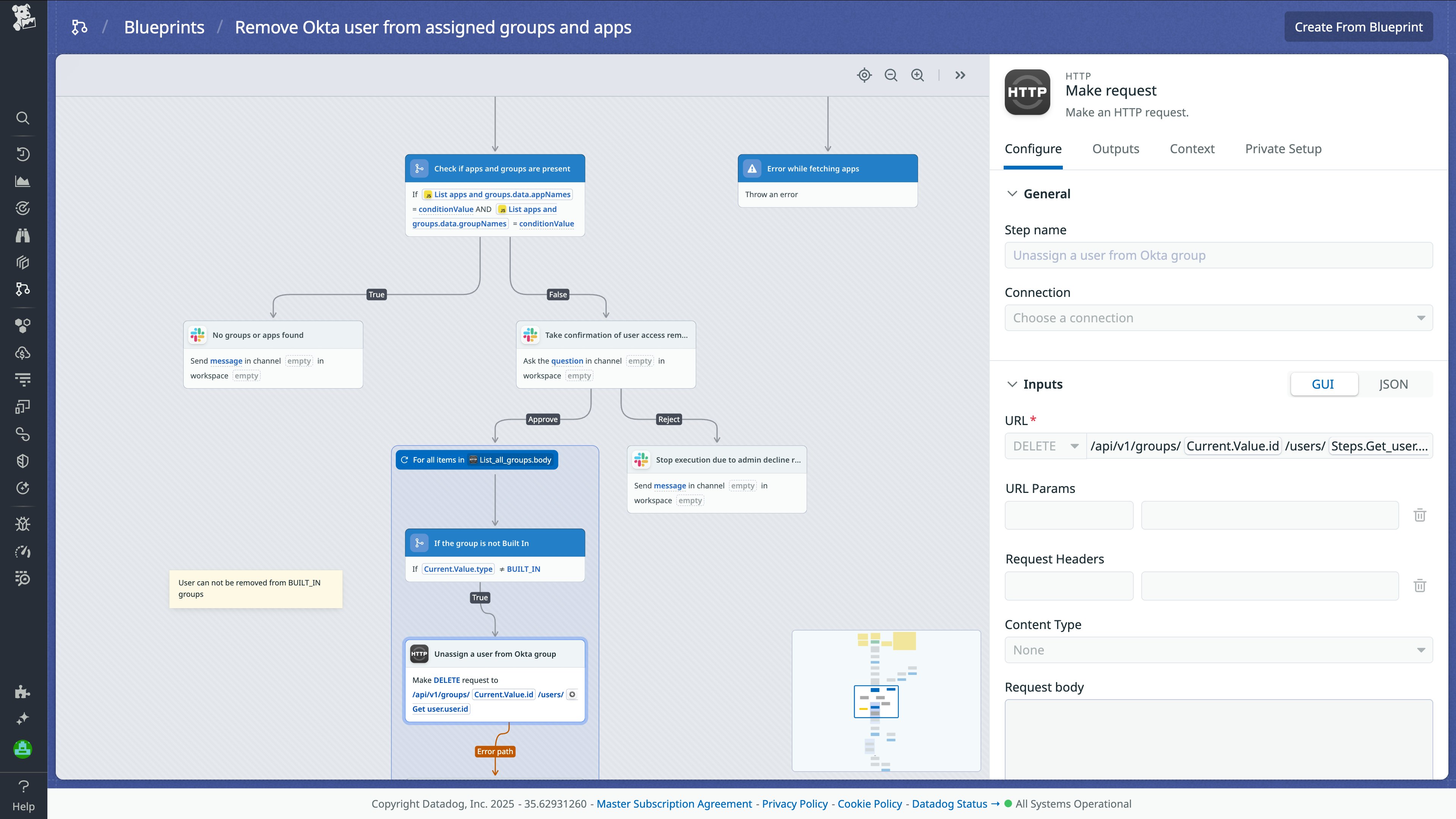
This streamlined process helps security analysts manage user access securely and efficiently, ensuring that permissions are only revoked with proper authorization. For example, let’s say a SOC analyst is investigating a signal in Cloud SIEM and notices that activity is still being logged for an entity named Calvin.Jones even though the associated employee recently left the company. From within the signal view, the analyst can quickly take action by launching a SOAR workflow from the Next Steps widget on the right.
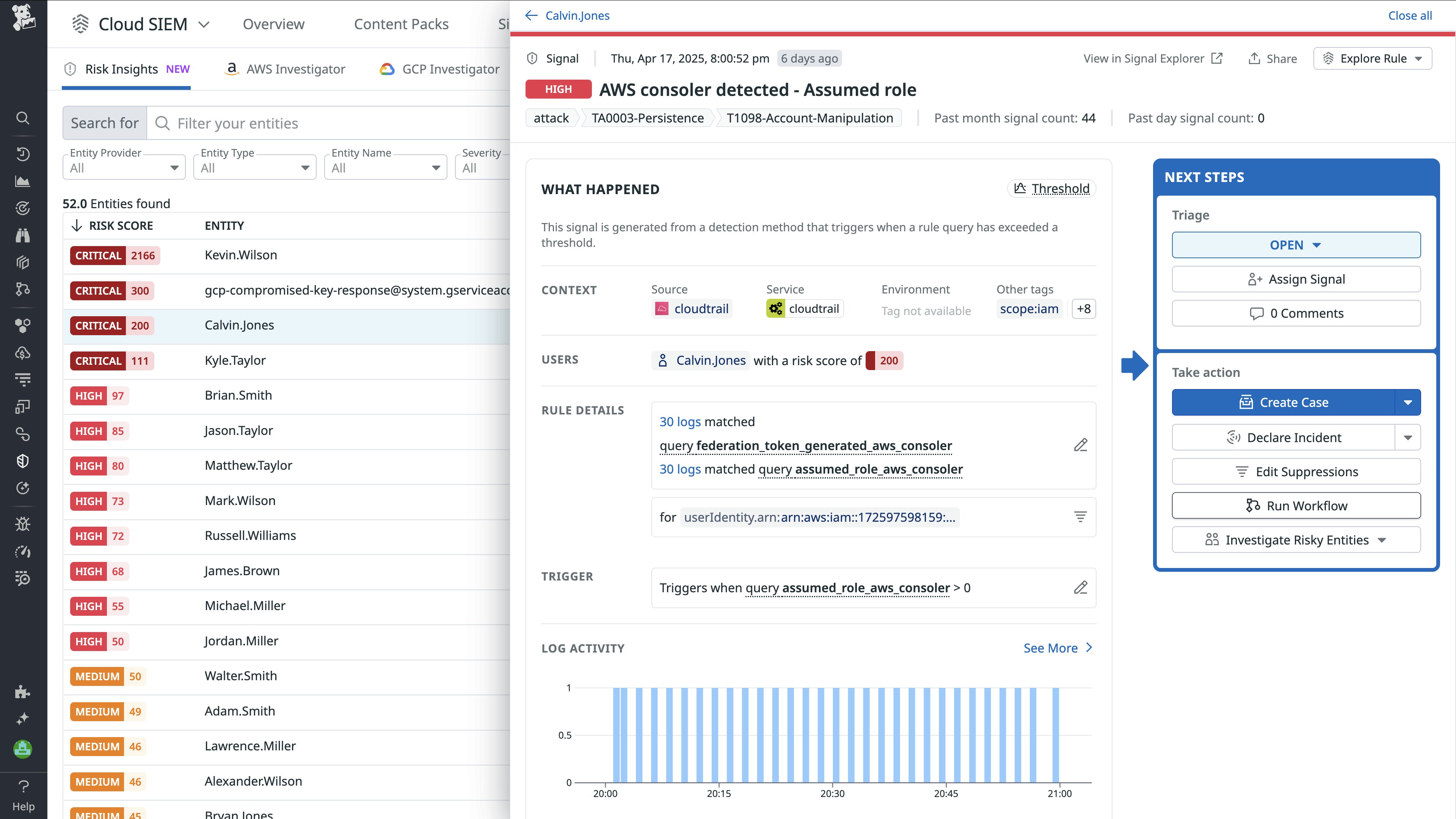
In this case, they might choose to initiate the Okta workflow to remove the user from all assigned groups and applications, helping to reduce potential access risks while the investigation continues. Depending on your needs, workflows like this can be executed automatically or manually, enabling both proactive and reactive response strategies.
Automate threat containment with endpoint detection and response workflows
Endpoint Detection and Response (EDR) workflows automate the investigation and containment of threats across endpoints. Integrations with leading EDR tools like CrowdStrike, Microsoft Defender for Endpoint, and SentinelOne provide real-time visibility into endpoint activity, enabling security teams to isolate compromised machines, perform deep forensic analysis, and trigger remediation steps automatically. By automating key actions like host isolation and artifact retrieval, these workflows help teams respond more efficiently to endpoint incidents, minimizing the impact of attacks and improving overall security resilience.
Automatically kill suspicious processes with CrowdStrike
Imagine that you are a security analyst who is handling a malware or ransomware attack. When an endpoint is compromised, malicious processes may continue running in the background, causing further harm by encrypting files, exfiltrating data, or spreading to other systems. To prevent further damage, it’s crucial to immediately stop these malicious processes by running the SOAR workflow to kill a suspicious process with CrowdStrike.
Let’s break down how the workflow would help contain this threat:
- Retrieve alert details: The workflow starts by pulling the alert details using the Composite ID (Alert ID) from CrowdStrike.
- Identify associated processes: The workflow identifies all processes linked to the alert, determining which ones are potentially malicious.
- Check for active processes: The workflow checks if any of the identified malicious processes are still running on the endpoint.
- Terminate active processes: If active malicious processes are found, the workflow automatically attempts to terminate them to prevent further damage or spread of the attack.
- Stop workflow: If no active malicious processes are found, the workflow halts, ensuring that no unnecessary actions are taken.
The following screenshot shows the blueprint for this workflow:
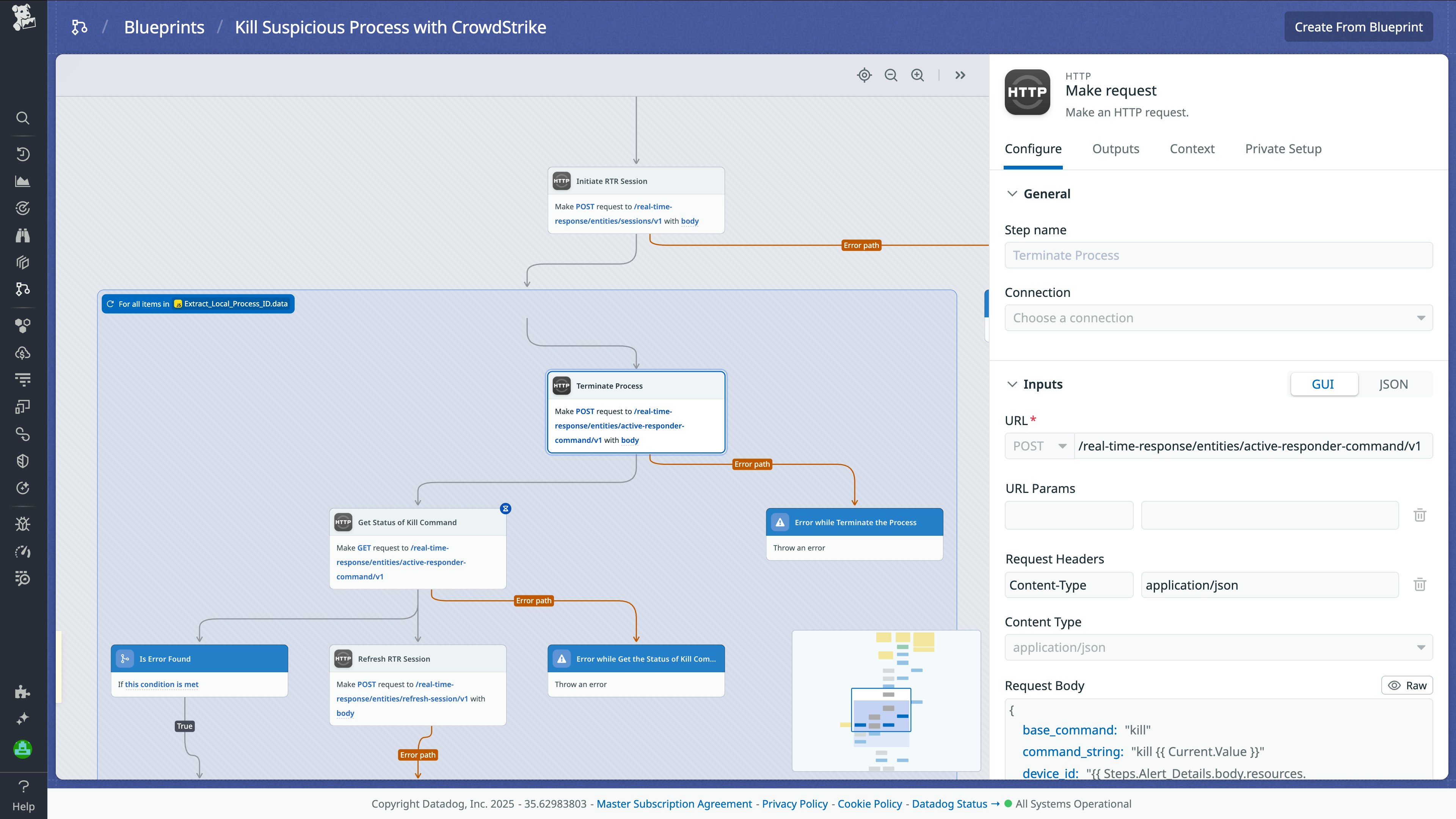
By automating the termination of malicious processes, this workflow enables security teams to quickly contain and neutralize threats, minimizing the impact and reducing the time to response.
Prioritize high-risk incidents with threat intelligence enrichment workflows
Threat intelligence enrichment workflows automate the process of enriching alerts with external threat intelligence. Integrations with services like Google Safe Browsing, Abuse IPDB, Censys, Phishtank, APIVoid, and Malshare enable teams to cross-reference indicators of compromise (IOCs)—such as suspicious URLs or IP addresses—against up-to-date, global threat intelligence databases. By automatically flagging malicious URLs, phishing attempts or known unsafe IPs, domains, and file hashes, security teams can prioritize high-risk incidents and respond more effectively.
Automatically assess URL threats with Google Safe Browsing
Security teams frequently receive alerts or tickets for potentially suspicious URLs from sources like phishing emails, suspicious user activity, or threat intel feeds. Manually checking each URL for threats can be time-consuming and error-prone. More critically, if a malicious URL isn’t discovered quickly, users might click through and unknowingly expose the organization to malware, credential theft, or other attacks. Automating this process by using a SOAR workflow to assess a URL threat with Google Safe Browsing helps teams act fast, stay consistent, and reduce the risk of web-based threats slipping through the cracks.
Here’s how this workflow quickly asseses URLs for possible threats:
- Validate the URL: The workflow starts by checking that the input URL is properly formatted and valid.
- Query Google Safe Browsing: It then sends the URL to the Google Safe Browsing Lookup API, which checks for threats such as malware, phishing, or deceptive content.
- Store malicious URLs: If the URL is flagged as unsafe, the workflow logs and securely stores it in a centralized datastore for future reference or correlation.
- Notify the team: A concise Slack notification is sent to the security team, including the threat status of the URL and any relevant context, enabling faster decision-making or escalation.
- Stop workflow: If the URL is clean, the workflow stops, avoiding unnecessary follow-up while maintaining a consistent audit trail.
The following screenshot shows the blueprint for this workflow:
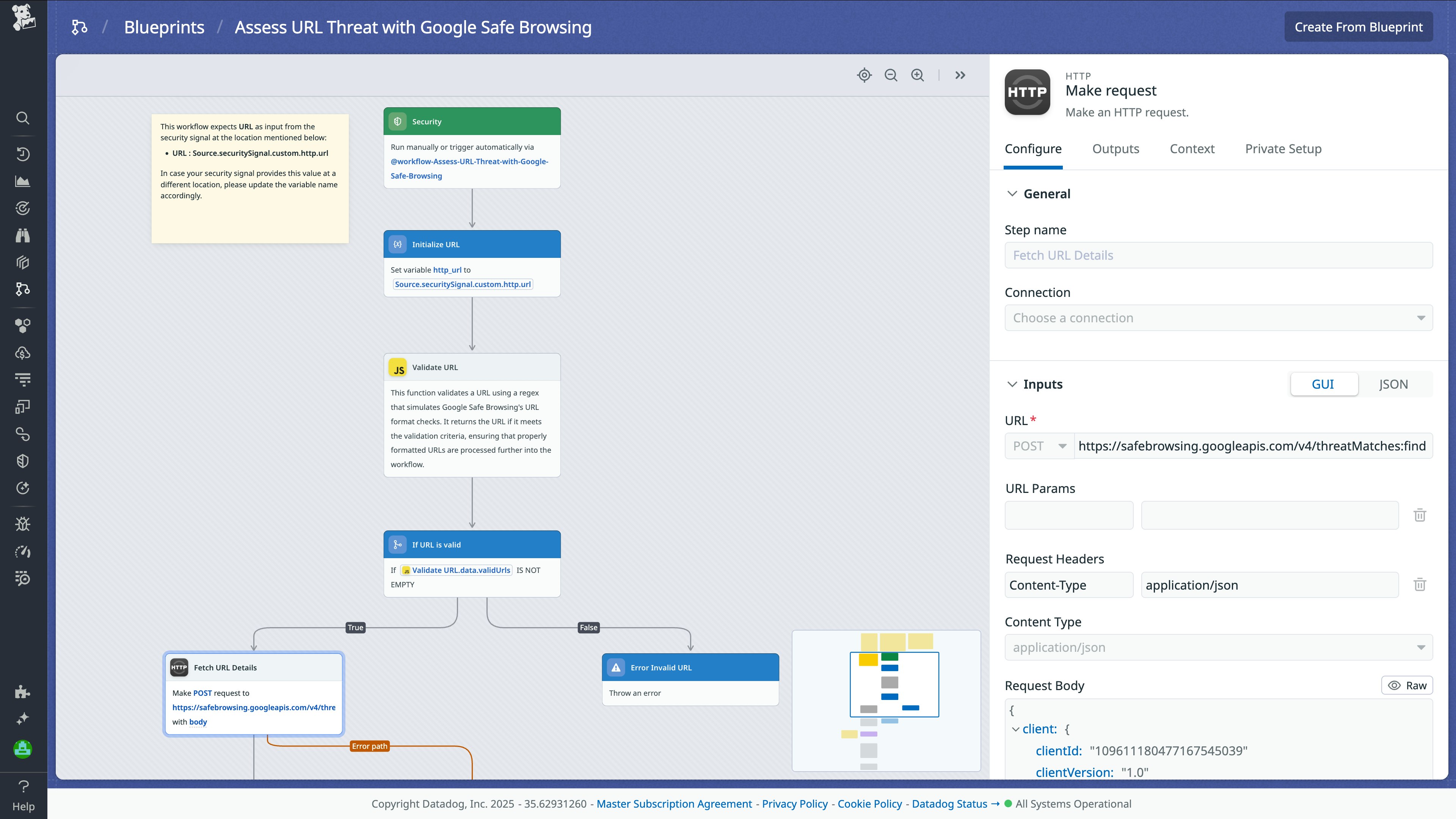
This workflow helps security analysts quickly and confidently assess URL threats, cutting down manual effort and enabling faster, more consistent responses to web-based risks.
Tailor automation to your environment by customizing workflows
Each SOAR blueprint is fully customizable. You can start with prebuilt templates as a foundation, then modify steps or conditions to match your team’s processes. You can also stitch together components from multiple blueprints to create complex, end-to-end workflows, all within the same intuitive interface.
Transform your security operations with automated workflows
As you’ve seen in this post, our newest Datadog SOAR workflows automate critical security tasks, enabling faster and more efficient threat responses. IAM workflows streamline user access management, EDR workflows automate endpoint threat containment, and Threat Intelligence Enrichment workflows enhance triage by integrating external threat data. Automation reduces response times, improves incident handling, and enables teams to focus on stopping real attacks.
We are also developing behavioral and agentic AI, a new approach to detection and automation. Agentic AI uses complex reasoning to link data, context, and teams, helping you get from alert to resolution within minutes. Together, agentic automation and SOAR offer a flexible toolkit to help your team move faster, cut through alert noise, and stay focused on high-impact threats, all within a single platform.
You can check out the SOAR solutions page and Workflow Automation documentation for more information or start building workflows today. If you don’t already have a Datadog account, you can sign up for a 14-day free trial.