Sourabh Katti

Addie Beach
Azure App Service is a platform-as-a-service (PaaS) commonly used to deploy applications and APIs, as well as functions, mobile apps, and more. It provides flexibility and reliability when deploying new applications and infrastructure, but it also introduces new security risks to your system. In particular, reduced visibility into the infrastructure and deployment of your application leads to a greater chance of application vulnerabilities being exploited by an attacker.
Datadog App and API Protection (AAP) now supports Azure App Service, enabling you to manage application security risk across even more of your system with continuous, real-time monitoring of vulnerabilities in and threats against your web applications and APIs. Additionally, AAP integrates with distributed traces and code-level context, empowering your development, operations, and security teams to build and run secure applications in production.
In this post, we’ll explore how monitoring Azure App Service with AAP enables you to:
- Detect attackers targeting your Azure App Service-deployed applications
- Prioritize fixing the most impactful vulnerabilities
- Correlate security and performance data
Detect attackers targeting your Azure App Service-deployed applications
While cloud-based deployments enable you to scale dynamically, they can present unique security challenges for your system. Risks like insecure code and misconfigured API endpoints can expose your application to malicious actors. And while Azure provides a variety of built-in security capabilities, there often isn’t enough visibility at the application layer to detect every attack attempt.
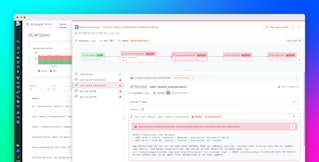
Datadog AAP provides comprehensive attack coverage for over 140 types of attacks out of the box—including the OWASP Top 10 rules, which cover threats such as SQL injection, cross-site scripting, and Log4Shell. Additionally, AAP enables you to create custom rules for business logic exploits and tailor detection rules to specific applications. For example, let’s say you want to monitor your web apps for unauthenticated user access on sensitive endpoints, a common risk when using cloud-based hosting services like Azure App Service. You can instrument the user monitoring SDK for AAP, then build a business logic rule that alerts for unusual activity on these endpoints.

AAP also provides actionable next steps for remediating these threats and securing your system. By viewing security signals in AAP, you can see which services have been targeted as well as any malicious input from the attacker. This enables you to quickly determine whether this signal corresponds to a legitimate attack and block the attacker’s IP address using Datadog’s native blocking capabilities. You can then investigate further alongside your organization’s SRE and development teams to find a permanent remediation for the attack.

Prioritize fixing the most impactful vulnerabilities
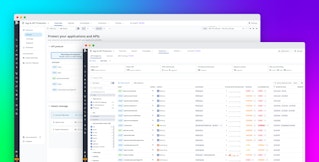
Modern apps are a mix of custom code and third-party libraries, the latter of which introduce additional risk to your applications by increasing the number of dependencies. When combined with deployment platforms like Azure App Service, it’s difficult to detect these vulnerabilities and determine which ones actually pose risks to your system. For example, vulnerabilities in an API running in a staging environment are less likely to be exploited compared to vulnerabilities in an API that’s exposed to public traffic.
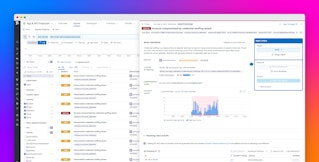
Datadog AAP detects vulnerabilities in applications hosted on Azure App Service across both your third-party libraries and custom code. By using runtime detection, AAP is able to report on an application’s attack surface and prioritize the most critical vulnerabilities. For each vulnerability, you can view attributes such as the package name, impacted services, and remediation details. Additionally, vulnerability severities are adjusted based on the runtime behavior of the application, enabling you to focus on fixing the most pressing risks. For example, the vulnerability severity will increase if the application is running in production or if attack attempts have been detected.

Correlate security and performance data
Security insights for applications hosted on Azure App Service fully integrate with the health and performance metrics provided by other Datadog products. For example, suspicious requests are highlighted in APM and stack trace errors are included in AAP, enabling teams to investigate issues more quickly. Additionally, the Service Catalog provides complete visibility into security, performance, and reliability metrics for all of your services.

Start securing your apps hosted on Azure App Service today
With AAP, you can view security signals and vulnerabilities from all your Azure App Service web deployments directly within Datadog. AAP enables you to quickly detect risks to your cloud-hosted services, view suggested remediation actions for quick troubleshooting, and pivot to APM for more information about the affected services.
You can use our documentation to enable AAP on your applications deployed on Azure App Service. Or, if you’re not yet a Datadog customer, you can sign up for a 14-day free trial.