Margherita Donnici

Prachi Chouksey
APIs now sit at the center of almost every digital product, from mobile apps and SaaS platforms to embedded services. As organizations scale, the number of endpoints grows quickly, as does the attack surface. Unmonitored or misconfigured APIs have already led to major incidents across industries, including data exposure, broken authentication, and large-scale account takeover. These cases highlight how unknown or unmanaged APIs can leak sensitive data, introduce compliance risks, and give attackers a way in. Many of these problems start with something relatively simple: You cannot protect what you cannot see.
Datadog App and API Protection (AAP) helps you move from API visibility to concrete security outcomes. With API Inventory, API Findings, and a posture overview, AAP discovers your endpoints across environments, detects misconfigurations and sensitive data exposure, and gives teams the context they need to prioritize and remediate risk, all in the same platform they already use to monitor applications and infrastructure.
In this post, we’ll show how you can use AAP to:
- Gain full visibility into your API landscape with API Inventory
- Detect hidden risks and suspicious activity across endpoints
- Investigate and remediate issues with API Findings
- Understand and improve your overall API security posture
- Turn API visibility into continuous, automated protection
Gain full visibility with API Inventory
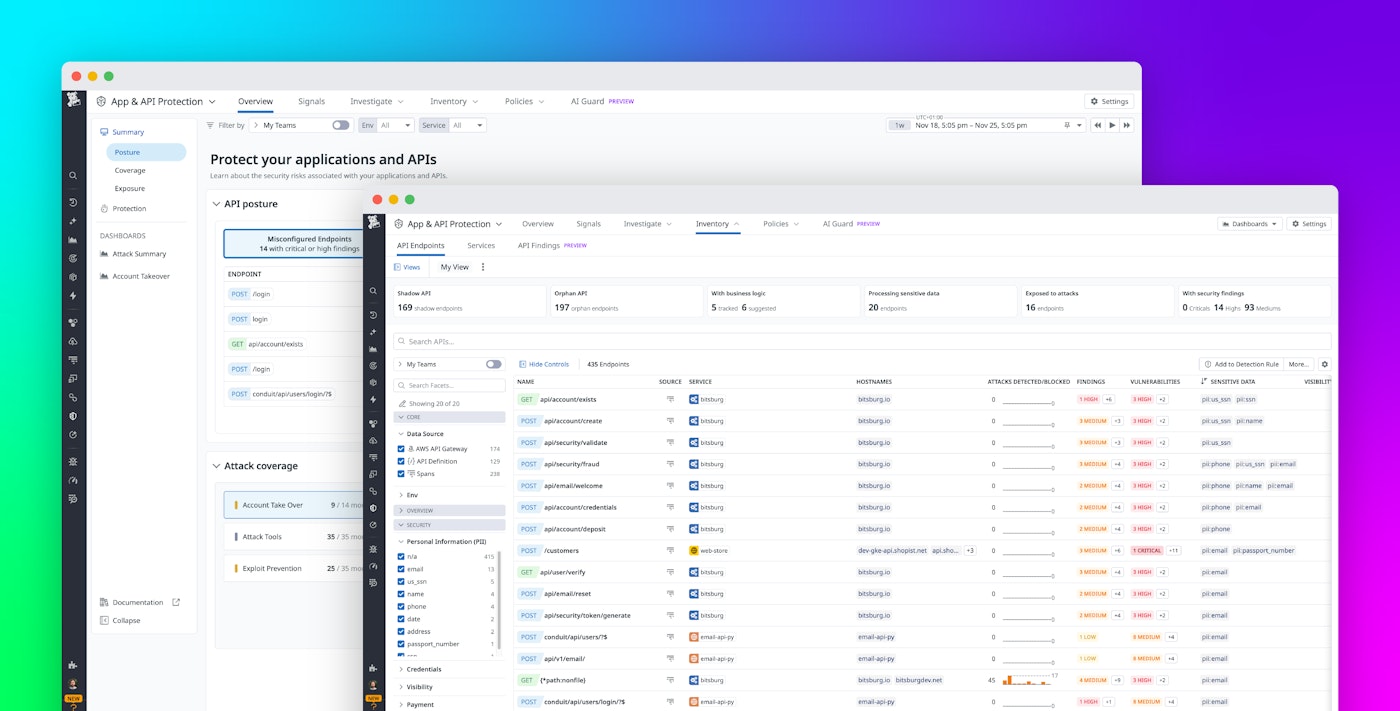
Effective API security starts with a complete, accurate inventory of your endpoints. In most environments, that inventory is scattered across OpenAPI specs, gateway configs, source code, and whatever your HTTP logs happen to reveal. AAP’s API Inventory brings all of this together into a single, continuously updated view.
AAP automatically discovers endpoints from multiple sources, including:
- Live traffic, to show which routes are actually in use in real time
- Uploaded API definitions, such as OpenAPI specifications
- Inferred routes, detected from non-instrumented traffic
- Integrations with AWS API Gateway, to surface managed APIs across cloud environments
- Source code analysis, which detects endpoints directly from your repositories
- Tracer-less and edge integrations with NGINX, Envoy, HAProxy, and Google Cloud Load Balancing, so you can get instant visibility even before teams instrument code
The following diagram shows how Datadog AAP collects API metadata from multiple discovery sources and unifies them into a centralized API Inventory:
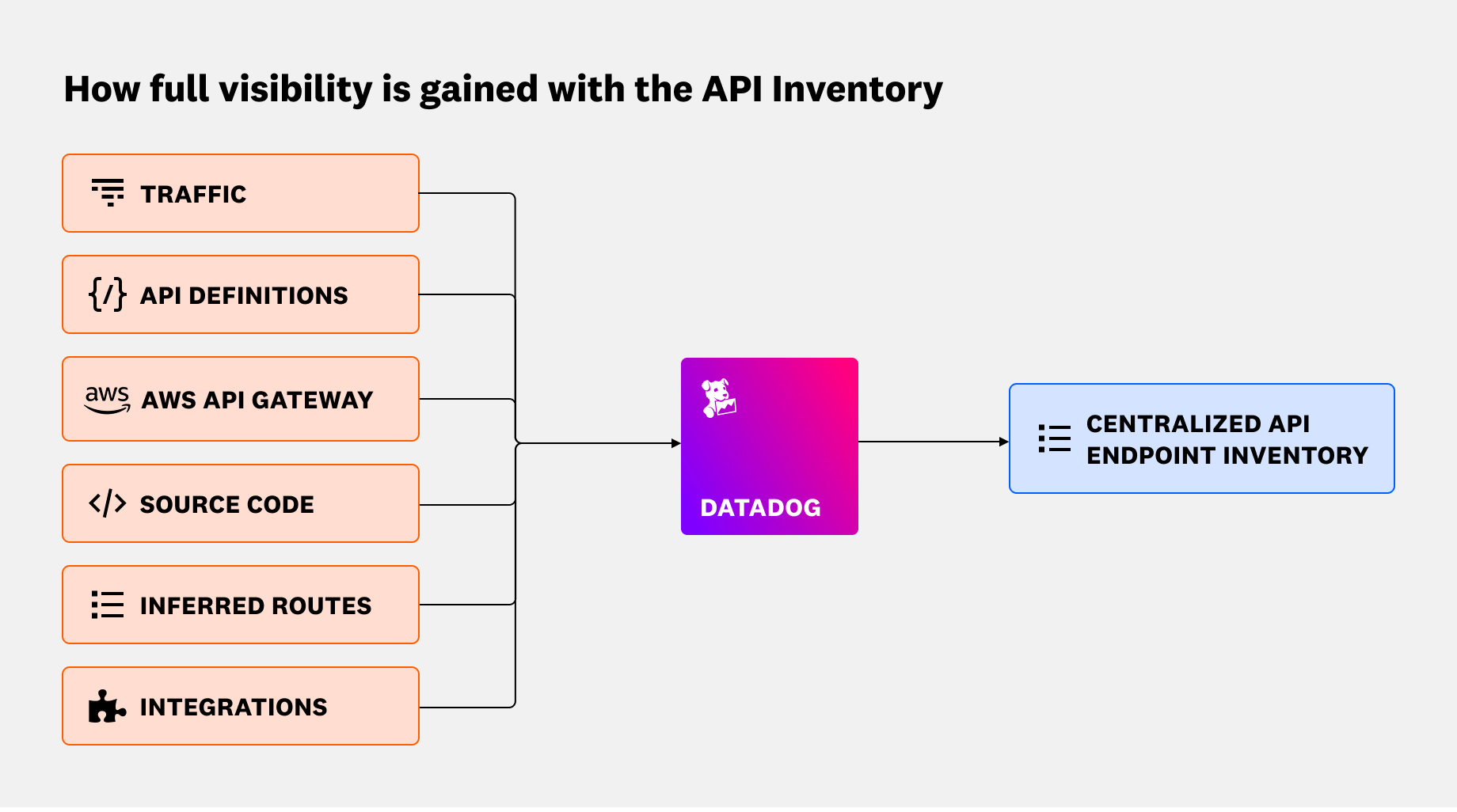
By consolidating these inputs, API Inventory gives you a unified view of your API landscape, whether or not those endpoints are documented. Each entry in the inventory is enriched with critical security context, such as:
- Authentication methods and whether an endpoint is public-facing
- Security findings, including potential misconfigurations, weak authentication, or sensitive data exposure
- Usage data, including when an endpoint was last seen in traffic
This makes it straightforward to answer questions that usually require custom scripts or one-off audits, such as:
- Which endpoints are undocumented or exposed to the internet?
- Which APIs handle sensitive data?
- Which endpoints have the riskiest combinations of sensitivity, exposure, and traffic?
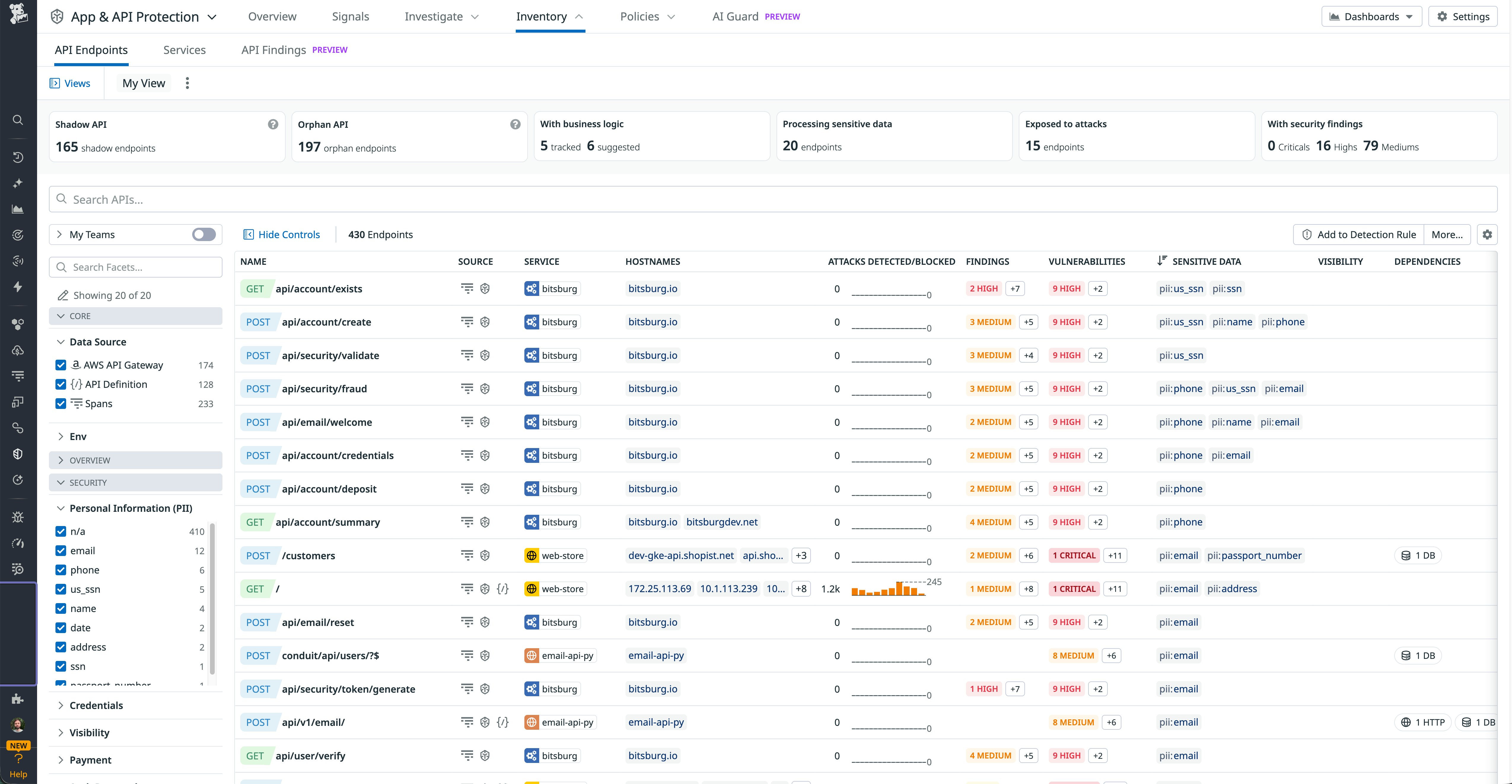
The following screenshot of API Inventory shows how this context in a single place enables security and platform teams to align on a single source of truth for APIs instead of juggling spreadsheets, gateway configs, and code searches.
Detect hidden risks in your API landscape
Once your endpoints are discovered, the next step is understanding which ones are risky, unused, or under active attack. API Inventory includes flexible search and filtering so you can explore the surface area in detail and build workflows around the patterns that matter most to your organization.
You can, for example, quickly surface:
- Undocumented APIs by filtering for endpoints seen in traffic or other data sources but missing from definitions (for example, by using the query
api:n/a). These are shadow APIs that may be handling production traffic without governance or review. - Unused documented APIs by finding endpoints defined in specs but with no recent activity (for example, by using the query
api:* last_seen_traffic<=(timestamp)). These often point to legacy or abandoned routes that you can deprecate or monitor for unexpected calls. - Endpoints handling sensitive data by filtering on personally identifiable information (PII) tags (such as by using
pii:*) and combining them with authentication or ownership filters to check that high-sensitivity APIs are properly secured. - Endpoints under attack by querying for security activity, such as by using
security_activity:*or, for more specific patterns,security_activity:attack_attempt.sql_injection.
These searches give teams a powerful way to investigate anomalies, validate assumptions about “low-risk” endpoints, and build continuous hygiene checks into their operational routines. Even more importantly, any search or filter combination can be saved as a custom finding query. AAP will then continuously evaluate your endpoints against that query and create findings when the conditions are met, turning ad hoc investigations into ongoing monitoring.
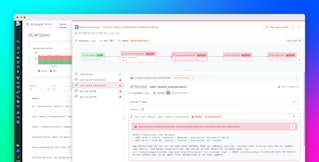
Detect and respond to risks with API Findings
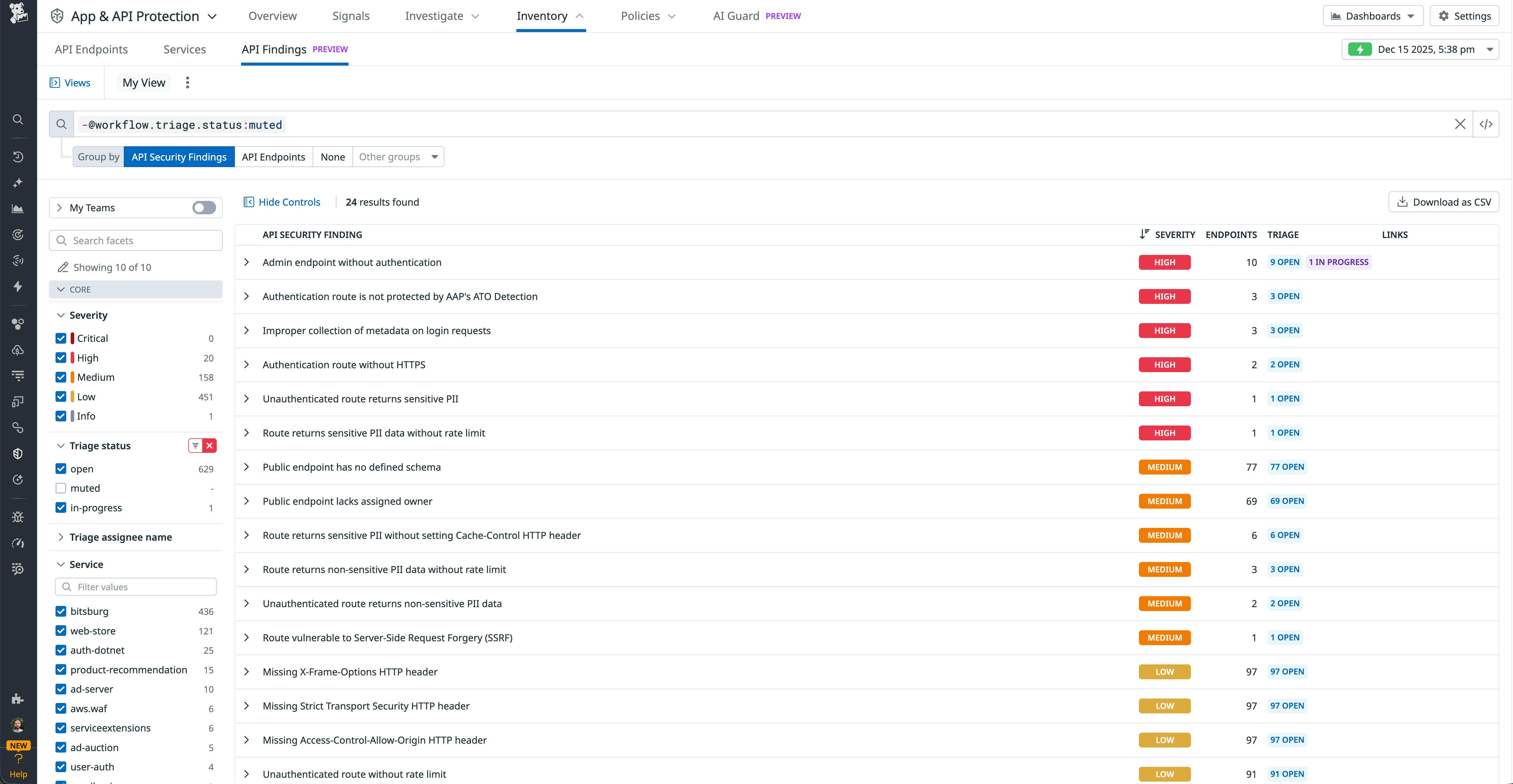
Discovery and exploration are useful on their own, but most security teams also need a prioritized list of issues to work through. API Findings aggregates potential vulnerabilities and misconfigurations across your endpoints. Datadog provides built-in detection rules authored by security experts, and you can also define your own logic to match your environment’s patterns and policies.
Findings can flag issues such as:
- Insecure authentication and authorization, such as endpoints that lack authentication or use weaker methods than expected
- Sensitive data exposure, including PII in parameters or responses
- API misconfigurations, such as missing rate limiting or overly permissive access
- Deprecated or high-risk endpoints that are still receiving traffic
Each finding includes key context: severity, the affected endpoint and service, the relevant detection rule, and any related activity. This makes it easier for DevSecOps teams to triage and decide whether to tackle an issue immediately, add it to a remediation backlog, or adjust the underlying rule.
Because API Findings is deeply integrated with the rest of the Datadog platform, you can configure notifications for new findings and create monitors that alert the right on-call teams when high-severity issues appear. You can also add findings to dashboards alongside your application and infrastructure metrics, and trigger Datadog Workflow Automation to open tickets and notify owners. This helps close the loop between detection and remediation so issues discovered in APIs do not linger as static reports.
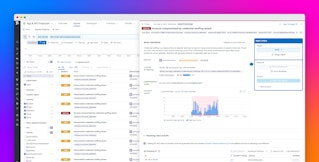
Understand your security posture at a glance
As the number of APIs grows, it becomes harder to answer simple questions about overall risk. AAP’s API posture overview gives you an organization-wide view of API security health so you can quickly see where to focus.
From the posture view, you can immediately see how many endpoints are documented versus undocumented, which endpoints have security findings broken down by severity, and which APIs are most frequently attacked or at elevated risk of account takeover.
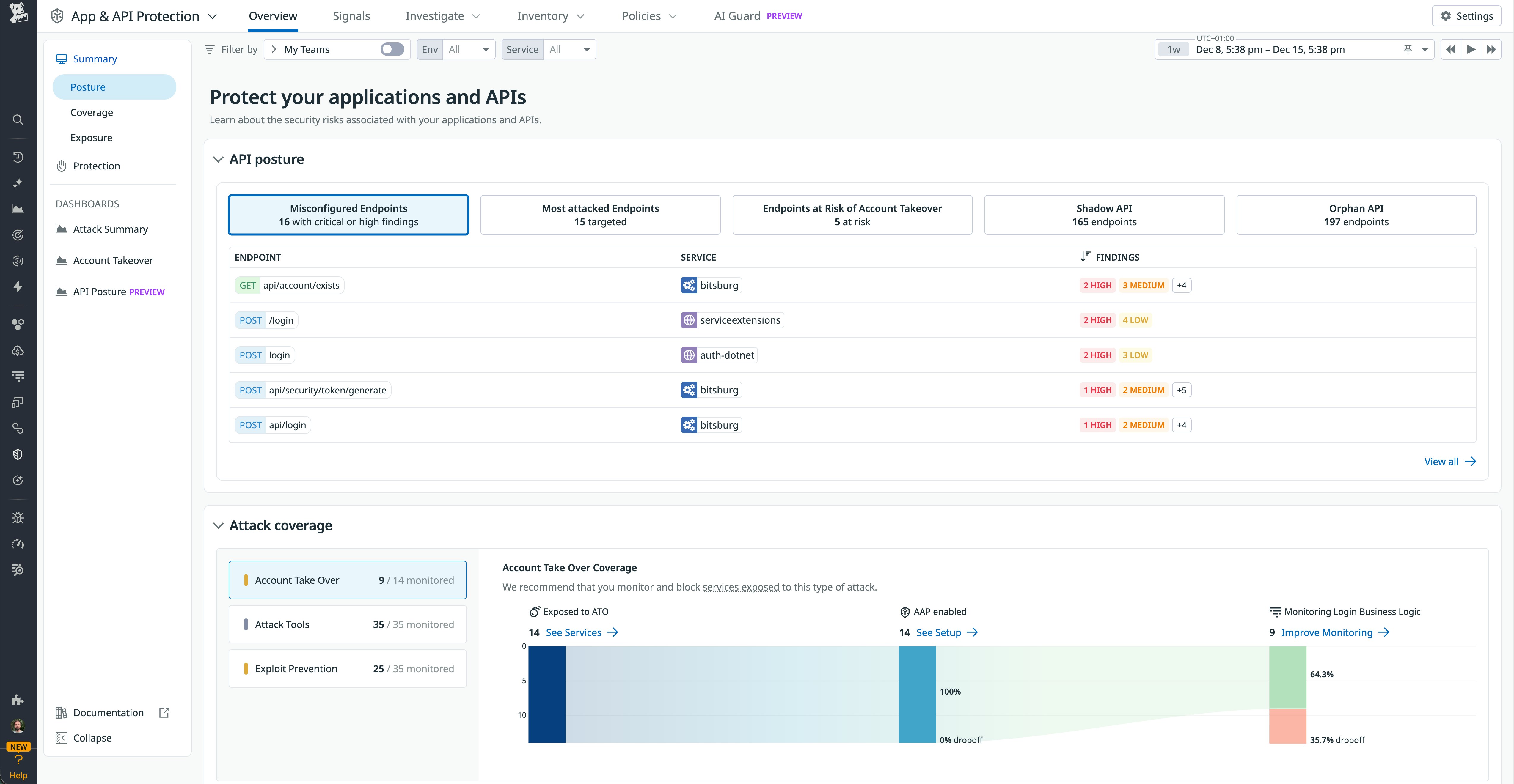
This view helps teams quickly prioritize work. For example, you might first focus on undocumented endpoints with high-severity findings. You could also disable unused legacy APIs that still receive attack traffic. Finally, you can coordinate with service owners to fix medium-severity misconfigurations in heavily used endpoints.
Because the posture overview is built on the same live data as API Inventory and Findings, it updates as you document APIs, deploy fixes, and tune detection rules. This gives you a feedback loop between engineering work and measurable improvements to API security.
Turn API visibility into continuous protection
Visibility is only useful if it changes how teams work. Datadog App and API Protection is designed to take you from one-time discovery to continuous protection by bringing observability data and security context into a single workflow.
With AAP, teams can:
- Discover all APIs across environments, whether or not they are documented
- Detect misconfigurations and vulnerabilities early, while changes are still fresh
- Monitor usage trends and identify dormant or legacy APIs that can be retired
- Automate notifications, escalation, and remediation tracking by using Datadog monitors and workflows
AAP is also evolving alongside modern API practices. New data sources will expand discovery coverage even further, and upcoming configurable scanners will let you define how sensitive data is detected and classified, as well as how authentication and rate-limiting configurations are evaluated. This gives organizations flexibility to adapt detections to their own policies and risk models. Early adopters are already using these capabilities to turn scattered API data into a clear, actionable map of their environment that encompasses who owns which APIs, what data they handle, and how well they are protected.
Start securing your APIs with Datadog
APIs are critical to your business, but they also represent one of its largest and fastest-changing attack surfaces. Datadog App and API Protection helps you bring that surface into focus, and detect and act on risky patterns without leaving the monitoring platform you already use to operate your services. To learn more, see the App and API Protection documentation. If you’re new to Datadog, sign up for a 14-day free trial.