On January 13, 2026, Node.js released information about a denial-of-service (DoS) vulnerability that affects applications that use async_hooks or AsyncLocalStorage. This vulnerability is tracked as CVE-2025-59466 and can cause Node.js processes to exit unexpectedly when certain stack overflow conditions occur while async_hooks are enabled.
Because Datadog APM’s Node.js dd-trace-js tracer uses AsyncLocalStorage to trace requests, this issue is relevant to APM customers who use affected Node.js versions (8.x through 23.x). This vulnerability is not specific to Datadog APM’s Node.js dd-trace-js tracer, and we have validated the tracer against patched Node.js versions.
This post will walk you through:
- A summary of the vulnerability
- How to use Datadog Cloud Security to identify vulnerable Node.js packages in your environment
- How to remediate the vulnerability
Summary of the vulnerability
In affected Node.js versions, if a stack overflow occurs in user code while async_hooks are active, Node.js may immediately terminate the process instead of throwing a catchable RangeError. This behavior bypasses standard error handlers, making the failure unrecoverable and enabling DoS attacks.
Because AsyncLocalStorage is built on top of async_hooks, this issue can surface in applications and frameworks that rely on request context, including React Server Components (React 18 or later), Next.js, and application performance monitoring tooling. For customers running vulnerable Node.js versions, applications may be susceptible to process crashes if unsanitized user input can trigger excessive recursion.
Detect vulnerable Node.js packages with Datadog Cloud Security
Datadog Cloud Security helps you understand and manage vulnerability exposure by continuously scanning your workloads. Using the following search query, you can review detected Node.js packages across your environment, including versions within the affected 8.x through 23.x range:
(cve:CVE-2025-59466 OR package_name:nodejs)Because this vulnerability depends on runtime behavior, only workloads actively executing an affected Node.js version are susceptible. Datadog Cloud Security enables you to prioritize running workloads while maintaining visibility into unused Node.js versions that may require future upgrades. Each finding includes additional information about the vulnerability and the recommended Node.js version to upgrade to.
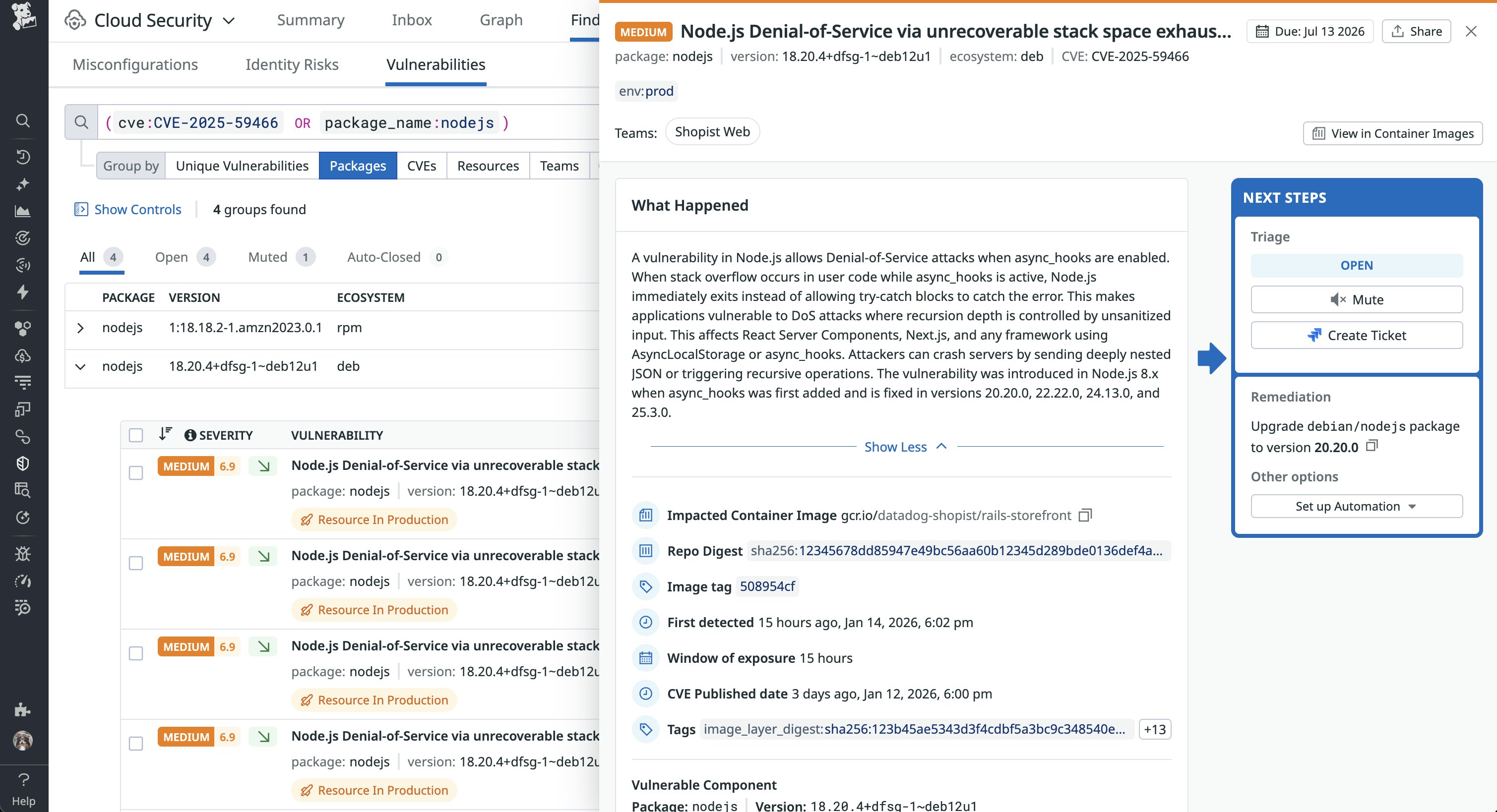
Remediation and next steps
We recommend upgrading to one of the following patched Node.js versions released on January 13, 2026:
- Node.js 25.3.0 (Current)
- Node.js 24.13.0 (LTS)
- Node.js 22.22.0 (LTS)
- Node.js 20.20.0 (LTS)
For details about the vulnerability and remediation steps, see Datadog’s Security Research Feed.
Closing
We will continue to monitor advisories closely and validate Datadog’s tracer compatibility with patched releases. Customers who have questions about their specific configuration or upgrade path are encouraged to contact Datadog Support.
Acknowledgments
Thank you to Kennedy Toomey, Ryan Simon, and Eslam Salem, all of whom contributed to this post.