Martin McCloskey
GitHub is a mission-critical software development and version control platform that is used to store proprietary source code and other sensitive data. Monitoring logs generated by activity in your GitHub environment can be useful, as unexpected patterns of behavior could indicate attacker activity or insider threats.
We’ve previously covered how our GitHub integration enables you to collect and monitor GitHub audit logs in Datadog. Now, we’ve expanded this integration so that users can ingest and normalize audit logs streamed from GitHub. In addition, Datadog Cloud SIEM now includes detection rules that enable you to quickly detect suspicious GitHub activities that might signal an attack, such as anomalous cloning of repositories or the addition of new enterprise administrators.
In this post, we’ll show you how to uncover suspicious activity in your GitHub audit logs using Datadog Cloud SIEM.
Uncover suspicious GitHub activity
Datadog collects and monitors the audit logs generated by GitHub to identify suspicious activities that may occur within your GitHub organization or enterprise account. If it detects an issue, Datadog generates Security Signals to alert you so you can investigate. Once you’ve configured audit log streaming, Datadog Cloud SIEM will automatically analyze all of your GitHub audit logs in real time and evaluate them against multiple out-of-the-box detection rules. These rules identify various activities that could signal attacker behavior, a few examples of which we’ll look at below:
- A GitHub enterprise owner was added
- An anomalous number of repositories was cloned
- SSH keys were added by a suspicious IP address
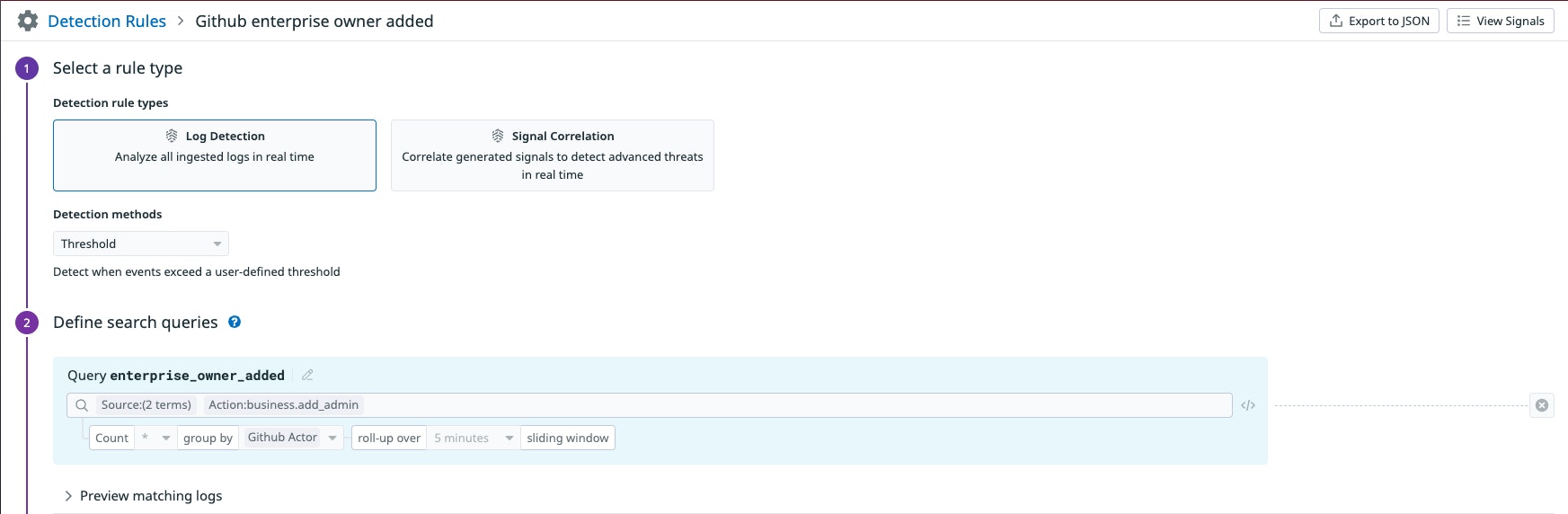
GitHub enterprise owner added
A GitHub enterprise owner has complete control over the enterprise and can take every action, including:
- Managing administrators
- Adding and removing organizations to and from the enterprise
- Removing enterprise members from all organizations owned by the enterprise
- Managing enterprise settings
- Enforcing policy across organizations
- Managing billing settings
An attacker with unauthorized access could seek to persist in the GitHub environment by adding additional roles or targeting members with this level of privilege. The “GitHub enterprise owner added” rule in Datadog Cloud SIEM helps you investigate this behavior by generating a Security Signal whenever the business.add_admin action takes place.
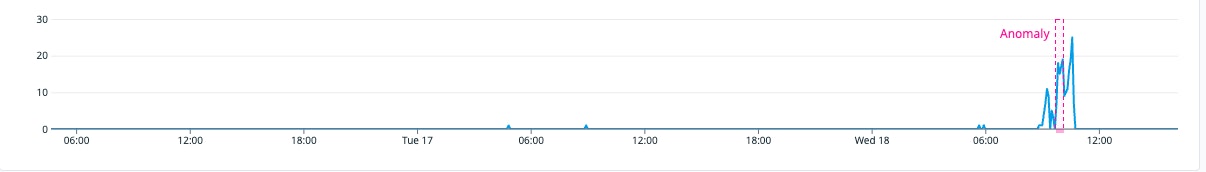
Anomalous number of repositories cloned by user
The theft of sensitive data, such as intellectual property or customer information, is a major threat. An attacker with unauthorized access or insider threat may try to clone your GitHub repositories in an effort to collect data for exfiltration or to gain contextual awareness of your environment.
Datadog Cloud SIEM now includes a rule that utilizes the anomaly detection method to identify any unusual spikes in repository cloning activity, which could indicate an attack attempt and may require further investigation.
GitHub SSH key added by suspicious IP
A phishing campaign reported by GitHub’s security team indicated that attackers may try to add an SSH key once they have gained unauthorized access to an account, in order to maintain that access. The “GitHub SSH key added by suspicious IP” detection rule alerts you to the creation of an SSH key from IP addresses deemed to be suspicious based on Datadog threat intelligence.
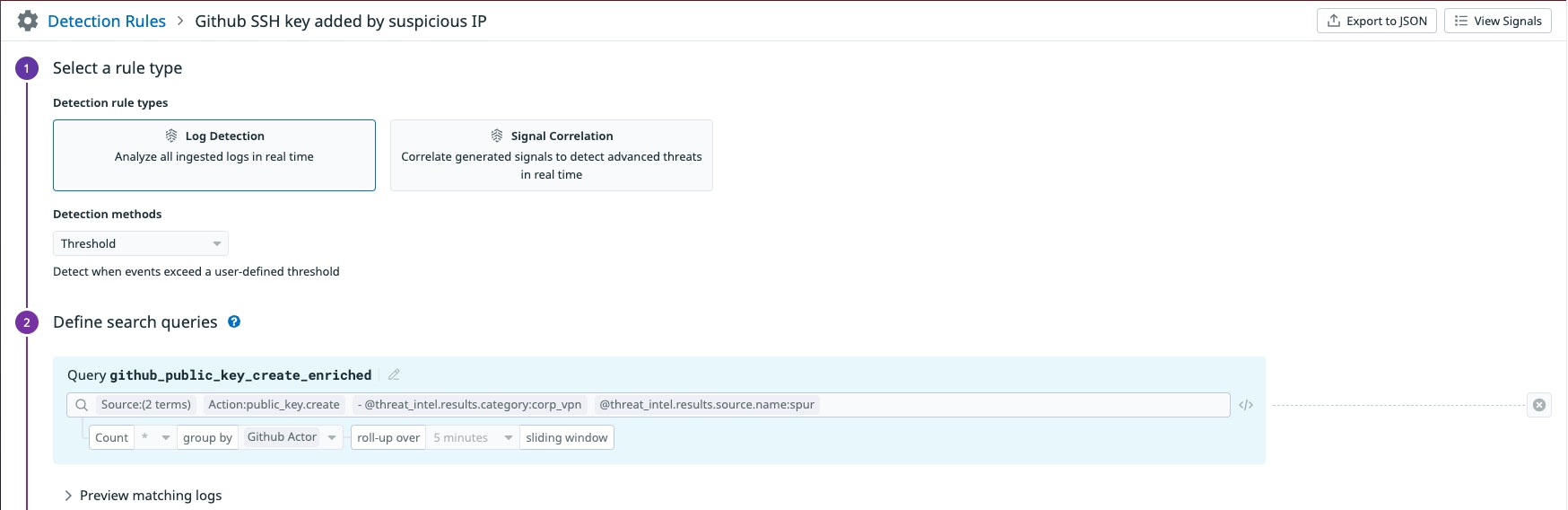
Note that by default, GitHub does not display the source IP address for events in your organization’s audit log. We recommend enabling IP addresses to provide as much context as possible when responding to Security Signals.
Get started
Datadog’s GitHub integration enables you to monitor GitHub activity in real time. Now, you can use Datadog Cloud SIEM to detect signals that could indicate suspicious activity, so you can secure your GitHub organization against threats.
If you’re already a Datadog customer, you can start exploring our GitHub integration and Cloud SIEM documentation. If you’re new to Datadog, get started today with a 14-day free trial.