Tom Sobolik
Organizations running containerized environments face complex security challenges as they scale Kubernetes and adopt dynamic, ephemeral infrastructure. Traditional security tools often miss activity inside containers, making it difficult to detect policy violations or threats at runtime.
Falco is a runtime security monitoring tool for containerized infrastructure. Falco uses eBPF probes and a custom Linux kernel module to detect malicious behavior in hosts and containers by detecting system calls in real time.
Datadog now integrates with Falco, enabling you to forward Falco alerts into Datadog to visualize and analyze container security events alongside relevant infrastructure metrics, traces, and logs from across your environment. In this post, we’ll show how you can use the Falco integration to accelerate your investigations with the power of Datadog dashboards, alerts, and Cloud SIEM.
Correlate Falco health and performance metrics with infrastructure telemetry
Once you’ve configured the integration to send telemetry from your Falco instance to Datadog, you can track key task execution metrics and spot performance bottlenecks by using the included dashboard. For instance, it can be helpful to correlate Falco’s CPU usage with the running processes count to hypothesize whether elevated resource utilization is caused by increased load or a single bottleneck process.
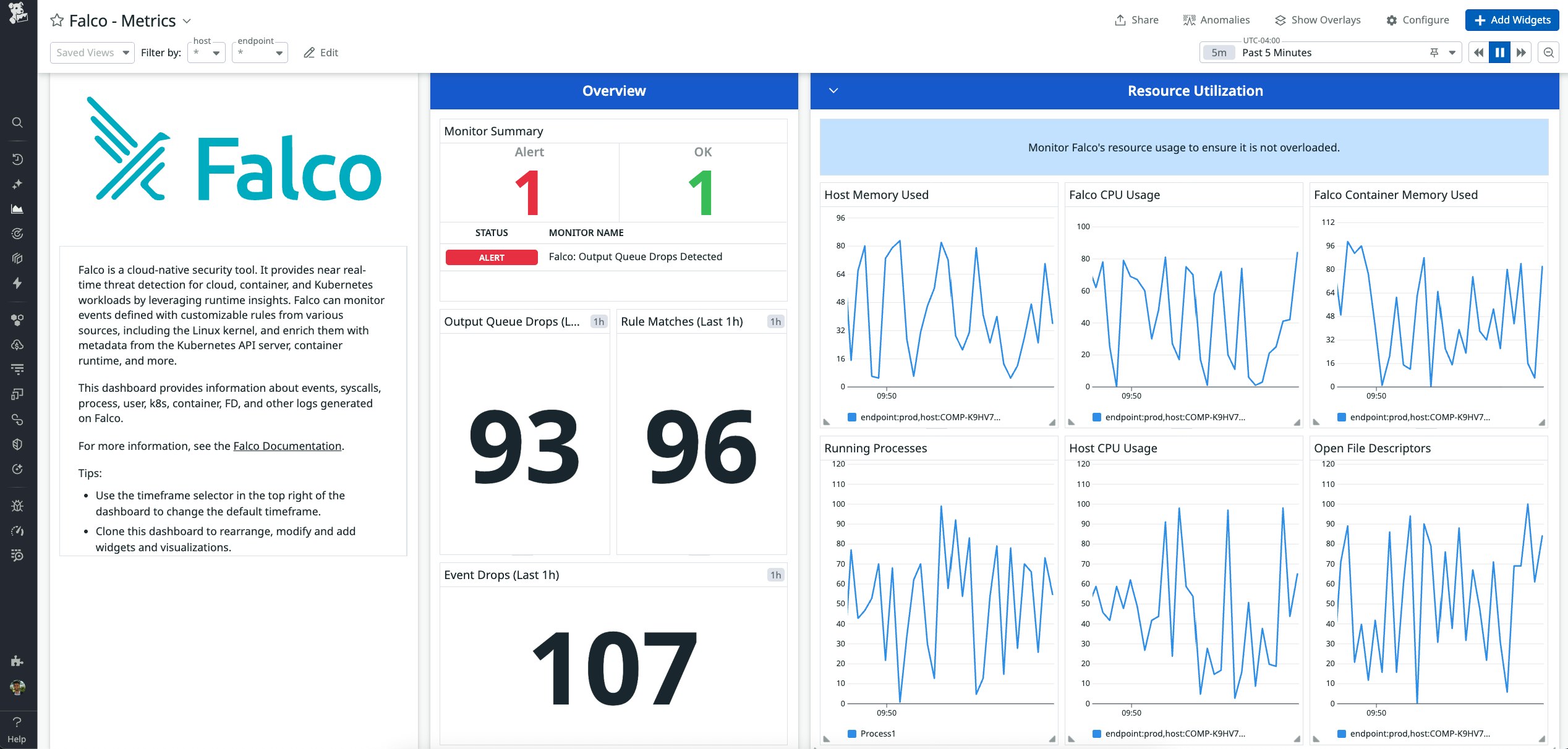
It’s also paramount to track and alert on output queue drops, as this is the strongest indicator that your Falco instance is missing critical threats. The health and performance of your Falco instance is a key component of the broader observability you need into your containerized workloads.
You can easily customize dashboards to help correlate Falco telemetry with health and performance signals from the rest of your Kubernetes environment. For instance, let’s say Falco detects an unexpected shell process in your application and submits an alert. By forwarding this alert to Datadog, you can correlate it with Kubernetes and application telemetry to understand the broader impact. For example, elevated CPU or memory usage on the affected pod or node might indicate that the attacker is running resource-intensive processes, such as crypto mining. Or, increased outbound network connections from the compromised container could signal data exfiltration or a command-and-control attack.
Speed up investigations with Falco and Datadog Cloud SIEM
By seeing security alerts within a broader application observability context, teams can more efficiently analyze the root cause and scope of a threat. The Falco integration can send security alerts from Falco directly into Datadog via API forwarding or the Datadog Agent. This allows your team to view, analyze, and act on runtime alerts while armed with logs and metrics from across your environment.
In addition to tracking Falco alerts within Datadog Monitors, adding alerts to dashboards, and pinning alerts to incident responses within Incident Management, you can send your Falco alerts to Datadog Cloud SIEM to help accelerate investigations and automate remediation workflows.
For instance, suppose Falco detects that a container in your Kubernetes cluster attempted to escalate privileges by writing to a sensitive system file such as /etc/passwd. This kind of unusual behavior could indicate a privilege escalation attack.
The Falco alert logs for this attack can be integrated into Cloud SIEM, which automatically scans all your security logs to flag malicious activity via built-in detection rules. By using Cloud SIEM’s historical engine, you can surface correlated threats hidden deep within your environment, such as abnormal user behavior, account takeovers, lateral movement, privilege escalations from authenticated insiders, and more.
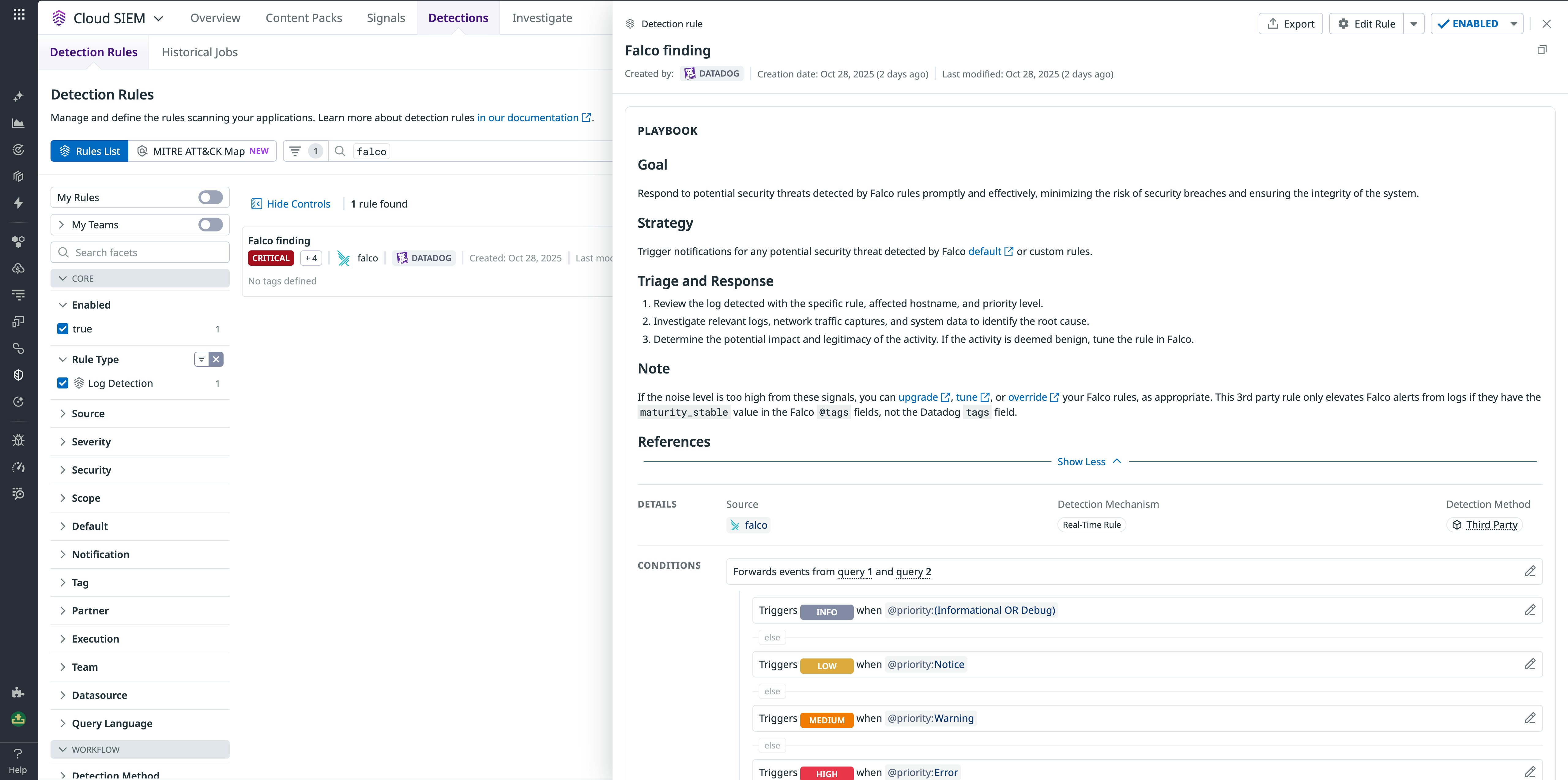
By correlating the Falco alert and other security logs using Cloud SIEM, you can expand your investigation into things like:
- User and authentication logs associated with the same container or service account, to detect if the attacker has accessed other resources with elevated permissions
- Historical activity, including past Falco and Kubernetes audit logs, to reveal if similar attempts occurred on other nodes or pods, suggesting lateral movement
- Correlated security signals to spot related detections (e.g., suspicious outbound SSH attempts or anomalous API calls) that can help you build a full timeline of the attack
Incorporate runtime security insights into your container observability
Falco provides visibility into container and host activity, while Datadog unifies those insights with metrics, logs, and traces across your entire stack. Together, they enable teams to accelerate investigations, reduce MTTR, and strengthen their security posture as they scale Kubernetes and other containerized environments.
With Datadog dashboards, monitors, and Cloud SIEM, your Falco alerts become part of a broader security and observability strategy that gives you real-time protection and actionable insights. Get started setting up the Falco integration by checking out our documentation. For more information about Datadog Cloud SIEM, see the Cloud SIEM docs. Or, if you’re brand new to Datadog, sign up for a free trial to get started.