Nimisha Saxena

Dayspring Johnson
1Password is a password manager that helps organizations reduce the use of weak and reused credentials across their teams. Because your organization uses 1Password to store highly sensitive information, including passwords, access keys, and secret tokens, monitoring logs generated by activity in your 1Password environment can be useful, as unexpected patterns of behavior could indicate malicious activity by attackers.
We’re pleased to announce that Datadog now offers an integration with 1Password that collects and processes your 1Password logs so you can monitor them in real time. The integration also provides detection rules in Datadog Cloud SIEM that enable you to quickly detect suspicious activities that might signal an attack, such as credential theft or brute-forcing.
In this post, we’ll cover how to:
- Visualize 1Password activity in real time using Datadog’s out-of-the-box 1Password dashboard
- Uncover suspicious activity in your 1Password logs using Datadog Cloud SIEM
Visualize 1Password activity in real time using Datadog’s out-of-the-box 1Password dashboard
Datadog’s integration with 1Password collects logs using 1Password Events API, which generates three types of logs:
- Sign-in attempts: These logs include the name and IP address of the user who attempted to sign in to the account, when the attempt was made, and—for failed attempts—the cause of the failure, such as an incorrect password, key, or second factor.
- Item usage: This type of log contains actions that describe how an item—e.g., a password or other credential—was used. Possible values for action include
fill,enter-item-edit-mode,export,share,secure-copy,reveal,select-sso-provider,server-create,server-update, andserver-fetch. - Audit events: These logs include actions performed by team members in a 1Password account, such as changes made to the account, vaults, groups, users, and more.
Once you enable the integration, Datadog’s out-of-the-box log processing pipeline will automatically parse and normalize your 1Password logs to structure them for easier analysis and correlation with your other log sources in Datadog.
After parsing your 1Password logs, Datadog will then populate the out-of-the-box 1Password overview dashboard with insights into security-related events from your 1Password values, items, and users. Widgets include toplists showing the most frequent and infrequent events, and a geolocation map that shows you the country of origin of sign-in attempts.
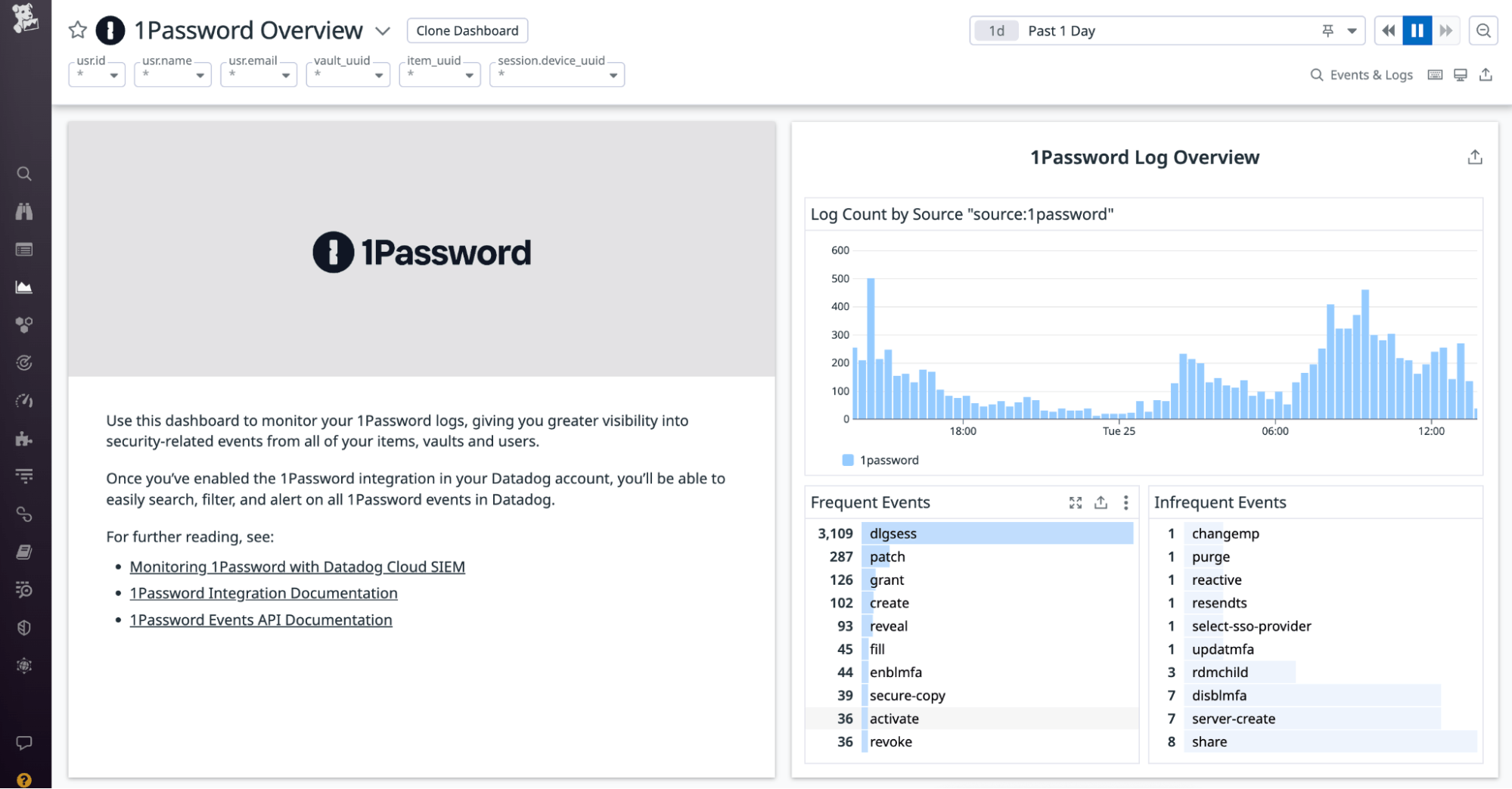
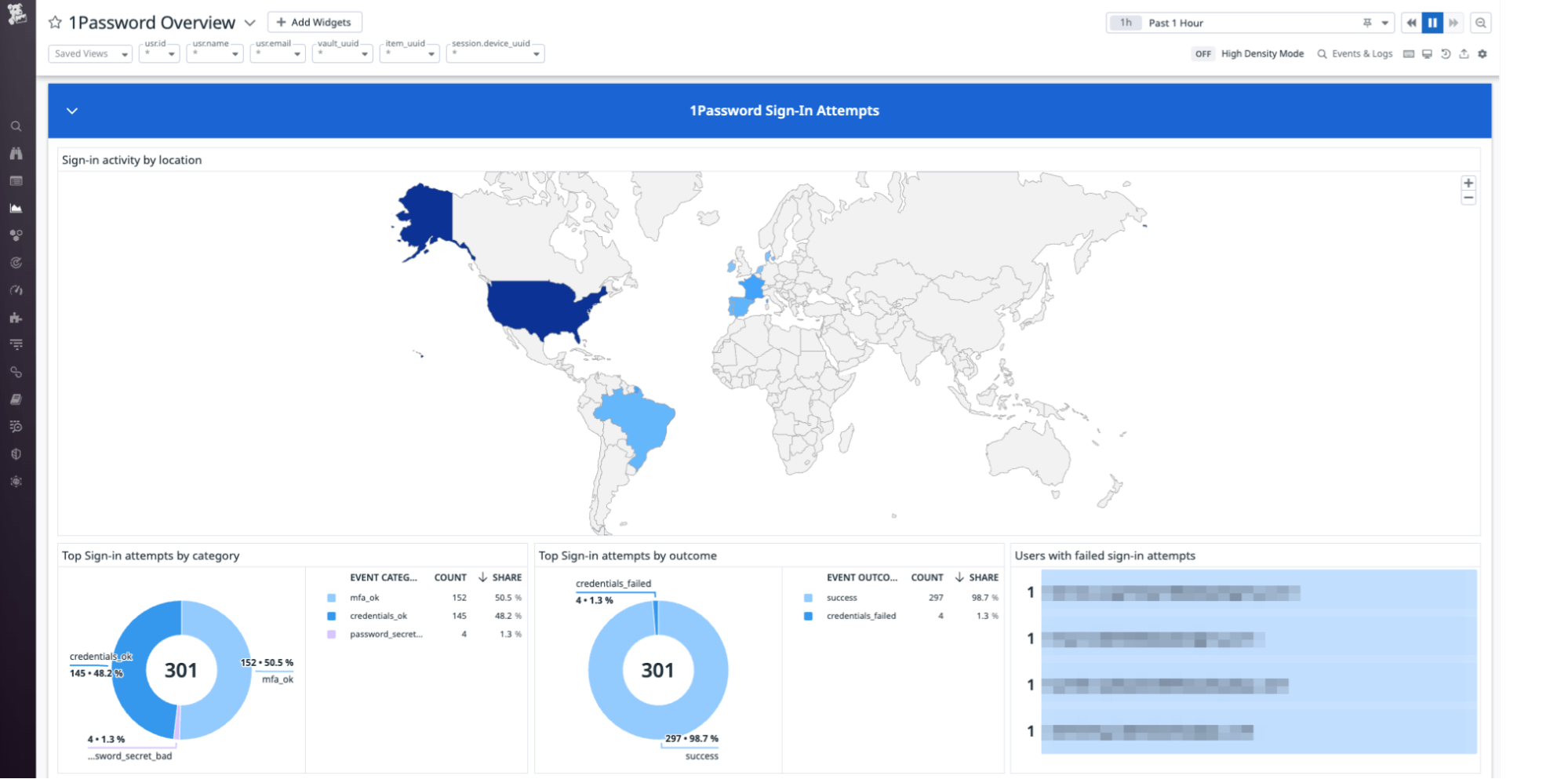
By aggregating critical insights from your 1Password environment into a single pane of glass, this dashboard helps you set a baseline for normal 1Password activity across your organization, so you can more easily identify abnormal patterns that could indicate an attack.
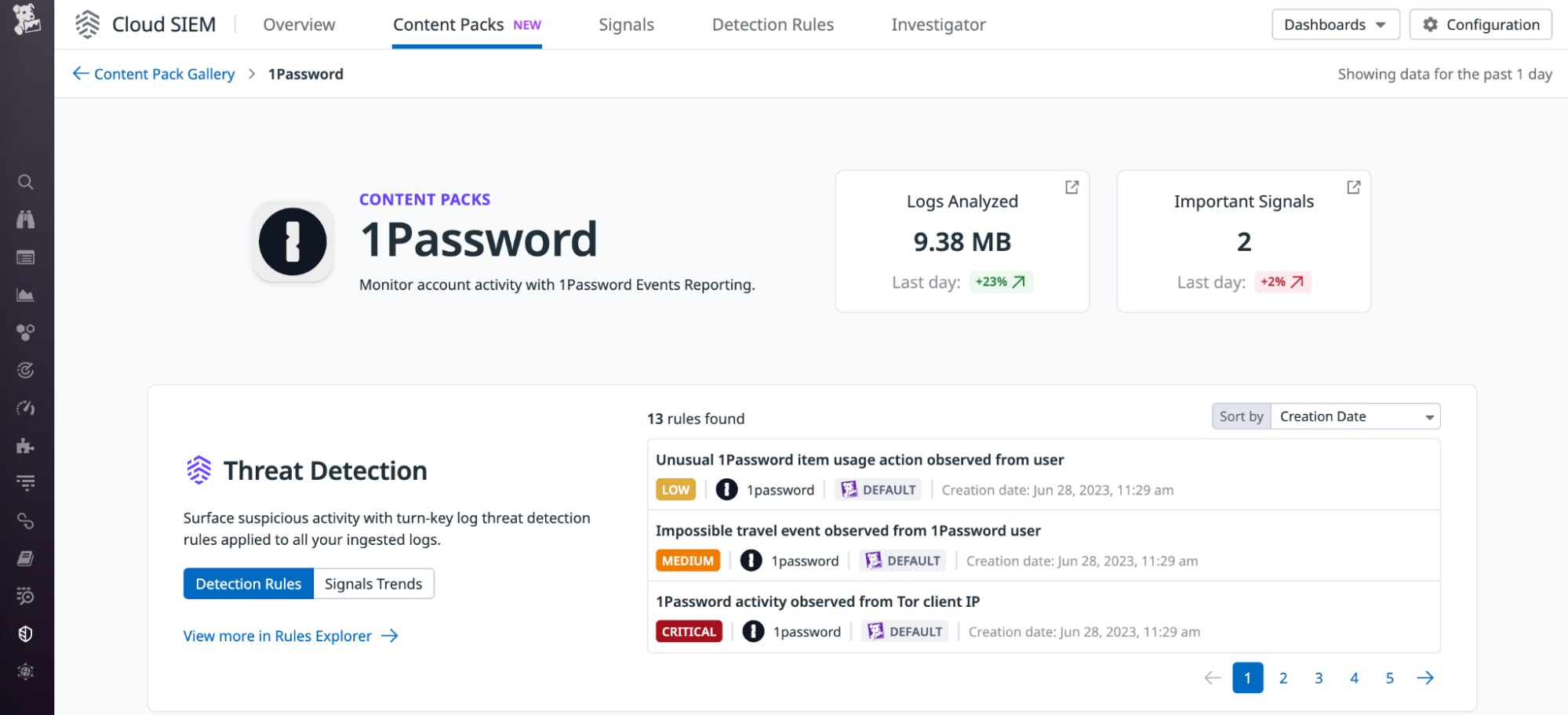
Uncover suspicious activity in your 1Password logs using Datadog Cloud SIEM
Datadog uses the three types of logs generated by the 1Password’s events API to identify suspicious activities that may occur within your 1Password tenant and generates Security Signals to alert you so you can investigate. After you enable the integration, Datadog Cloud SIEM will automatically analyze all of your 1Password logs in real time and evaluate them against multiple out-of-the-box detection rules. These rules identify various malicious activities, such as item exfiltration attempts, impossible travel events, item modification attempts, and more.
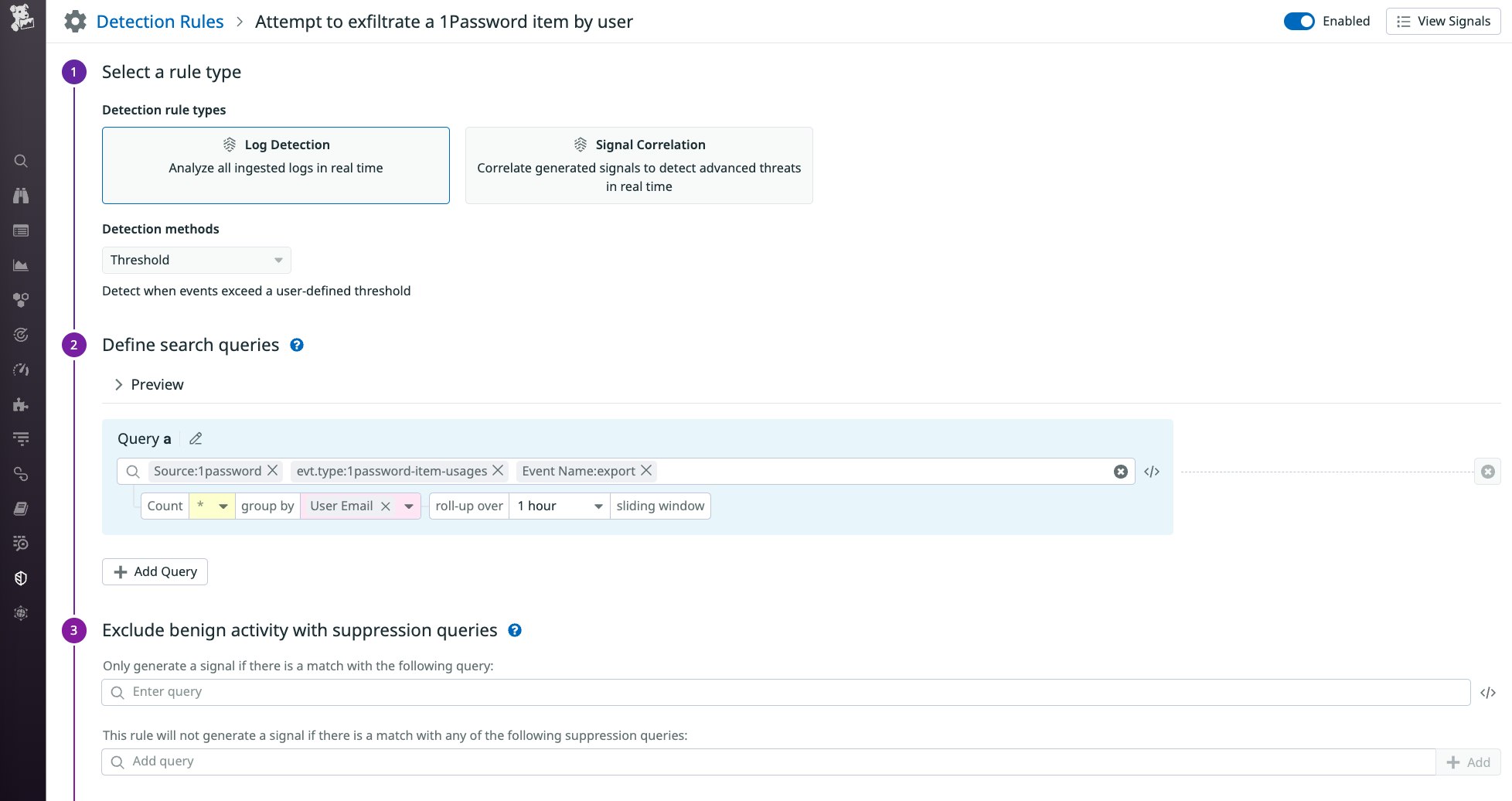
Some of these rules search for 1Password item usage actions that could indicate an attack. For example, the below rule uses the 1password-item-usages event type and the export event name to detect potential password exfiltration attempts.
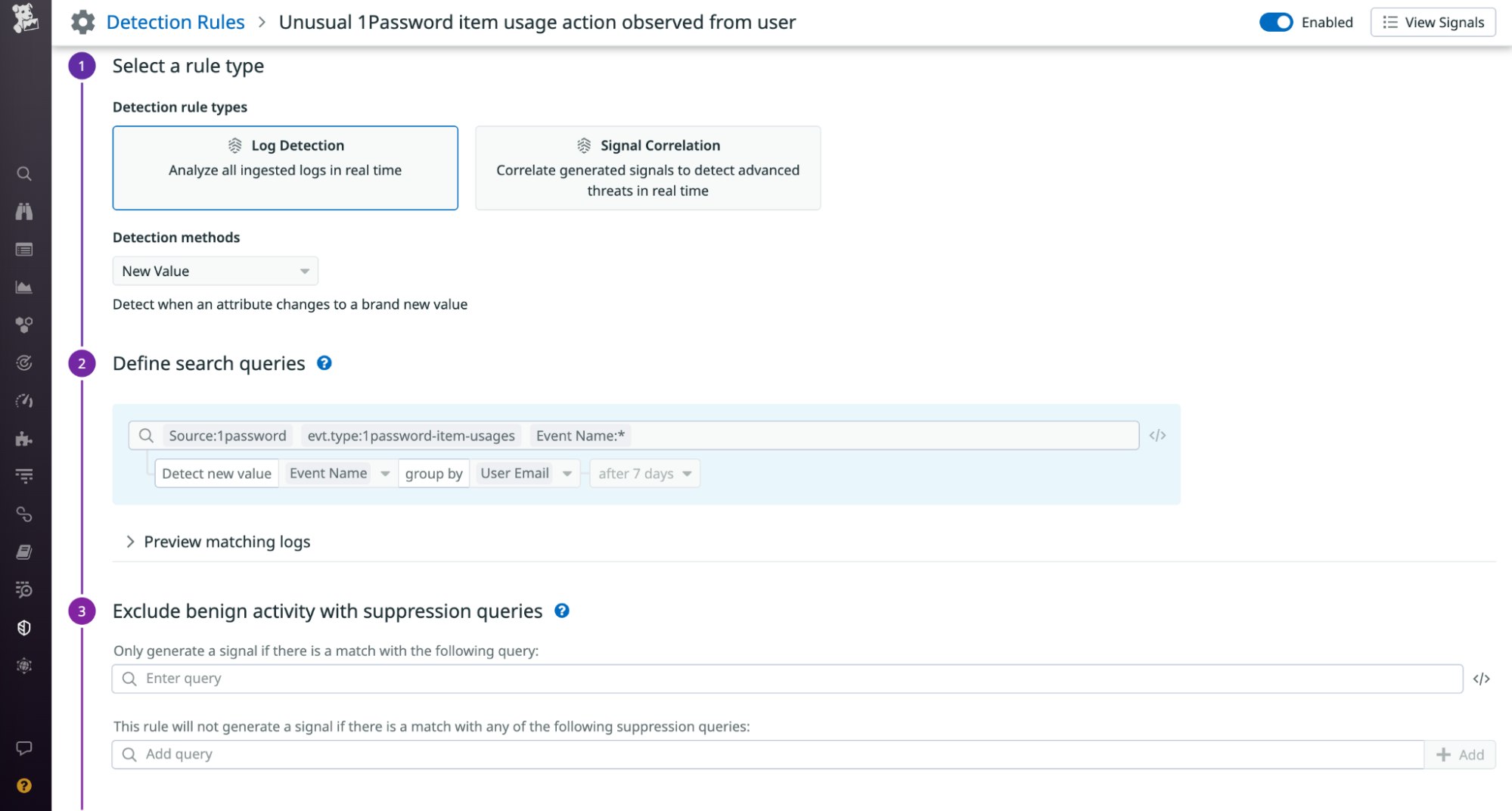
Other rules utilize the new value detection method to identify when an attribute, such as the event name familiar to a user, changes to a new value.
These out-of-the-box detection rules generate Security Signals in Datadog Cloud SIEM to alert you to potential attacks quickly, so you can start mounting a response.
When you’ve identified a Security Signal from 1Password that requires investigation or remediation, you can use Datadog Workflow Automation to orchestrate an automated series of actions in response to the alert, using a customized workflow or one of our out-of-the-box Workflow Blueprints. For example, you can use the Investigate Security Incident and Create Case Workflow Blueprint to compile a Notebook in Datadog, where you can collect relevant information about the incident, then automatically send a Slack message to the appropriate team member so they can take additional remediation actions while you investigate further. The Workflow will then create a case in Datadog Case Management, which allows you to create a centralized, easily accessible workspace for investigating your security signals, so you can streamline the triage process and keep track of your progress in determining whether a Security Signal from 1Password is a true attack attempt.
Get started now
Datadog’s 1Password integration provides you with real-time monitoring to detect and secure your 1Password tenant against threats. If you’re already a Datadog customer, you can start exploring the new 1Password integration now. And if you’re not, get started today with a 14-day free trial.