Martin Tournier
Organizations rely on best-in-class solutions for observability and security, and various teams within an organization often have preferences for different platforms. For example, your security team may use a SIEM platform like Microsoft Sentinel and Google Security Operations (SecOps) to detect and investigate threats, while your DevOps teams use Datadog Log Management for real-time troubleshooting and monitoring.
At the same time, many companies aim to standardize log processing across all their tools to ensure consistent formatting, tagging, and enrichment. For smaller teams, eliminating infrastructure management overhead is also a priority.
With Datadog Log Management, you can centralize log processing and governance while maintaining the flexibility to adopt the security tools of your choice. In this post, we’ll explore how you can ingest, enrich, and easily forward security logs from Datadog Log Management to Microsoft Sentinel and Google SecOps.
Standardize and enrich your security logs with Datadog log pipelines
Security teams need reliable, structured data to detect threats efficiently, but raw logs often arrive in different formats and contain inconsistent attributes. With Datadog Log Management, you can create log pipelines that enable you to centralize, process, and enrich security logs from across AWS, Azure, and Google Cloud, ensuring consistency before they reach your SIEM.
With Datadog, you can:
- Parse and standardize logs at ingestion by structuring unformatted data, normalizing attributes, and ensuring consistency across all sources.
- Enrich logs with contextual data on stream using built-in processors like geoIP resolution and threat intelligence.
- Generate metrics from logs to optimize storage and track performance in real time, analyze trends, and correlate with other infrastructure and application metrics that you already monitor in Datadog.
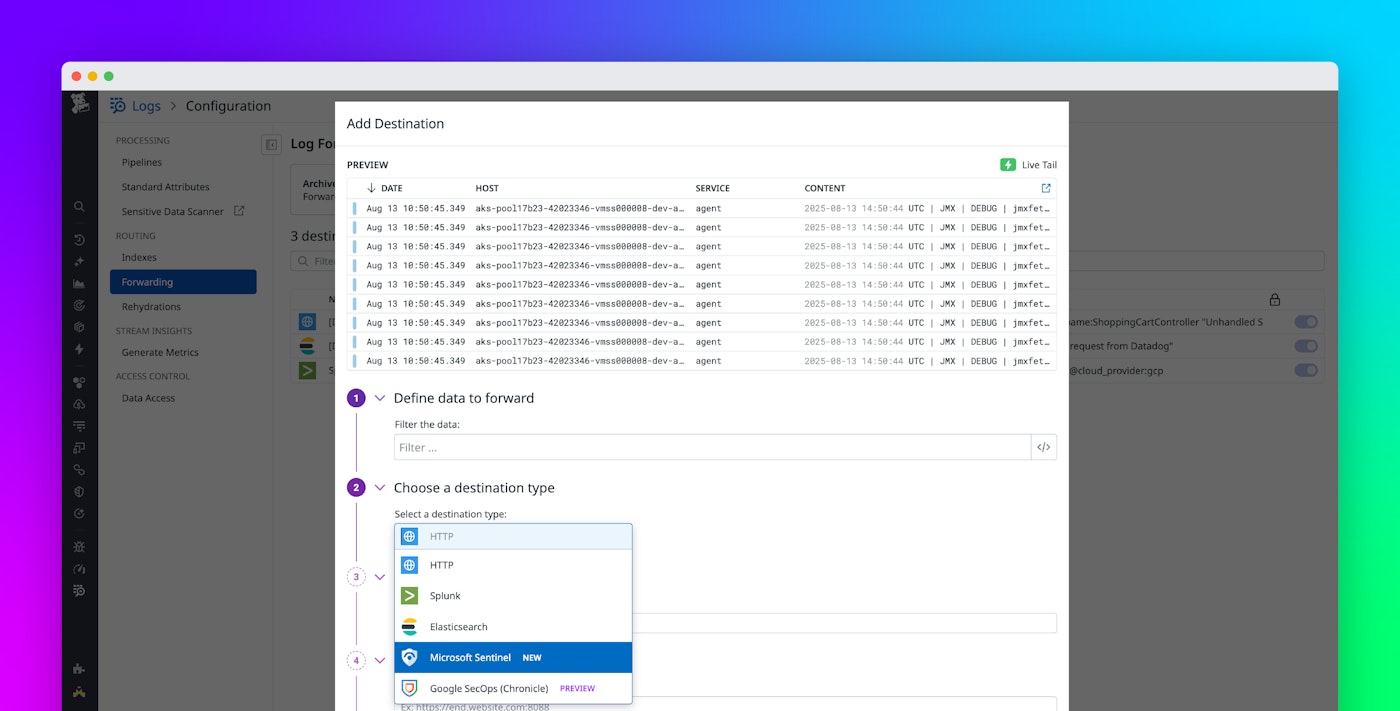
Once logs are structured and enriched, you can route security data to Microsoft Sentinel or Google SecOps without infrastructure overhead or complex integrations.
Forward security logs to Microsoft Sentinel or Google SecOps
To start forwarding security logs, you’ll first need to integrate Datadog with your cloud provider—Azure in the case of Microsoft Sentinel, or Google Cloud in the case of Google SecOps. Once integrated, you can configure log forwarding in Datadog by creating a custom destination, choosing Microsoft Sentinel or Google SecOps as your destination type, and selecting the appropriate cloud provider tenant and client.

Datadog gives you full control over which logs you forward. You can filter logs based on attributes, apply granular tagging, and exclude unnecessary data to optimize costs. Once enabled, security logs automatically stream to your SIEM, where you can analyze them for threat detection and security investigations.
Start using Datadog to send logs to your SIEM
By combining Datadog Log Management with your SIEM of choice, security teams can eliminate management overhead, enforce log consistency, and optimize security analytics, all without disrupting existing workflows.
To get started, check out our documentation to configure Microsoft Sentinel as a custom log destination and start forwarding security logs from Datadog. If you’re a Google SecOps user, you can join our Preview to enable log forwarding to Google SecOps. Alternatively, you can send logs directly to Datadog Cloud SIEM, where you can detect threats and investigate incidents alongside observability data from across the stack. If you’re not yet using Datadog, sign up for a 14-day free trial.