Thomas Sobolik

Geoffrey Carlisle
As of August 2023, only 3 out of 23 US government agencies were compliant with Office of Management and Budget (OMB) requirements for log management and security observability. These requirements are outlined in M-21-31, a 2021 memorandum that was issued following Executive Order 14028 on improving national cybersecurity. Until all of these agencies implement the new requirements, the federal government’s ability to fully detect, investigate, and remediate cybersecurity threats will be constrained.
Datadog offers Log Management, Workload Protection, and Cloud SIEM in its US1-FED region on AWS GovCloud, aligning with our FedRAMP® Moderate Authorization. This enables seamless compliance for public sector organizations using Datadog. Our solution brief explains how Datadog helps organizations address the challenges associated with M-21-31 compliance.
In this post, we’ll explain how Log Management, Workload Protection, and Cloud SIEM can be used with GovCloud workloads to meet M-21-31 requirements for:
- Log retention and storage
- Log management and access
- Security threat management
Investigate threats with historical context
M-21-31 dictates that agencies and organizations must retain logs for 30 months: 12 months in “active” or “hot” storage—which can be accessed instantly—and another 18 months in “cold” data storage that can be retrieved upon request. Datadog Log Management handily meets these requirements, with 15 months of hot storage and the ability to rehydrate older logs from cold storage. This enables your team members to query historical data related to ongoing security incidents and form a full picture of emergent behavior by threat actors.
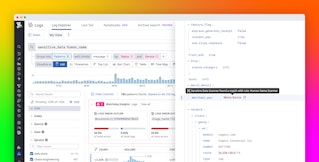
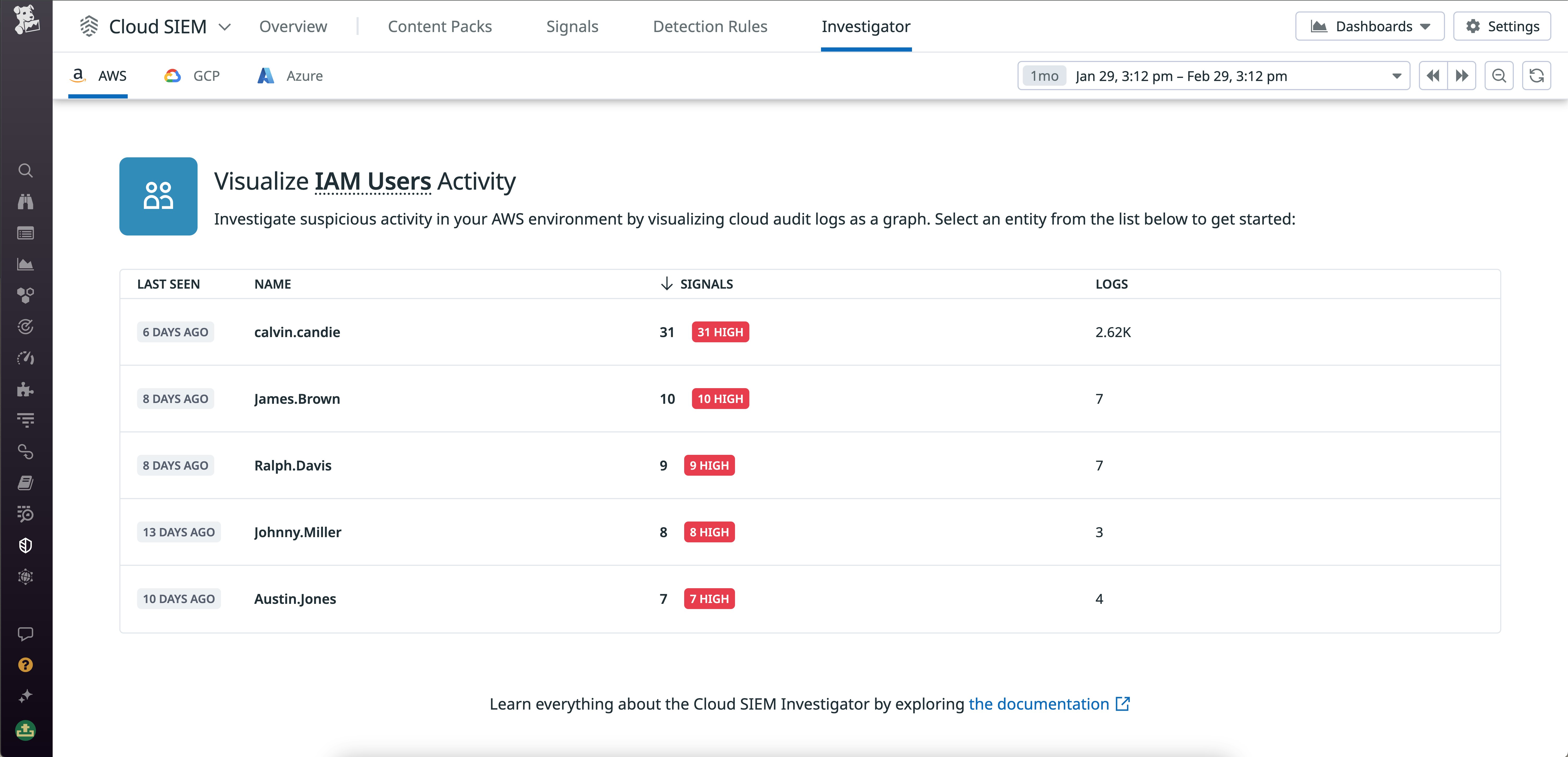
Datadog Cloud SIEM is integrated seamlessly with Log Management, so you can easily uncover and investigate security threats and attackers using your retained logs. In Datadog Cloud SIEM, you can view an overview of ongoing threats, including triggered security signals and related context such as suspicious actors and impacted resources. For example, the following screenshot shows IAM users whose activity recently triggered high-severity security signals in Cloud SIEM. After highlighting a triggered signal, you can then use Log Management to query logs within this context and investigate the attackers’ activity within your system.
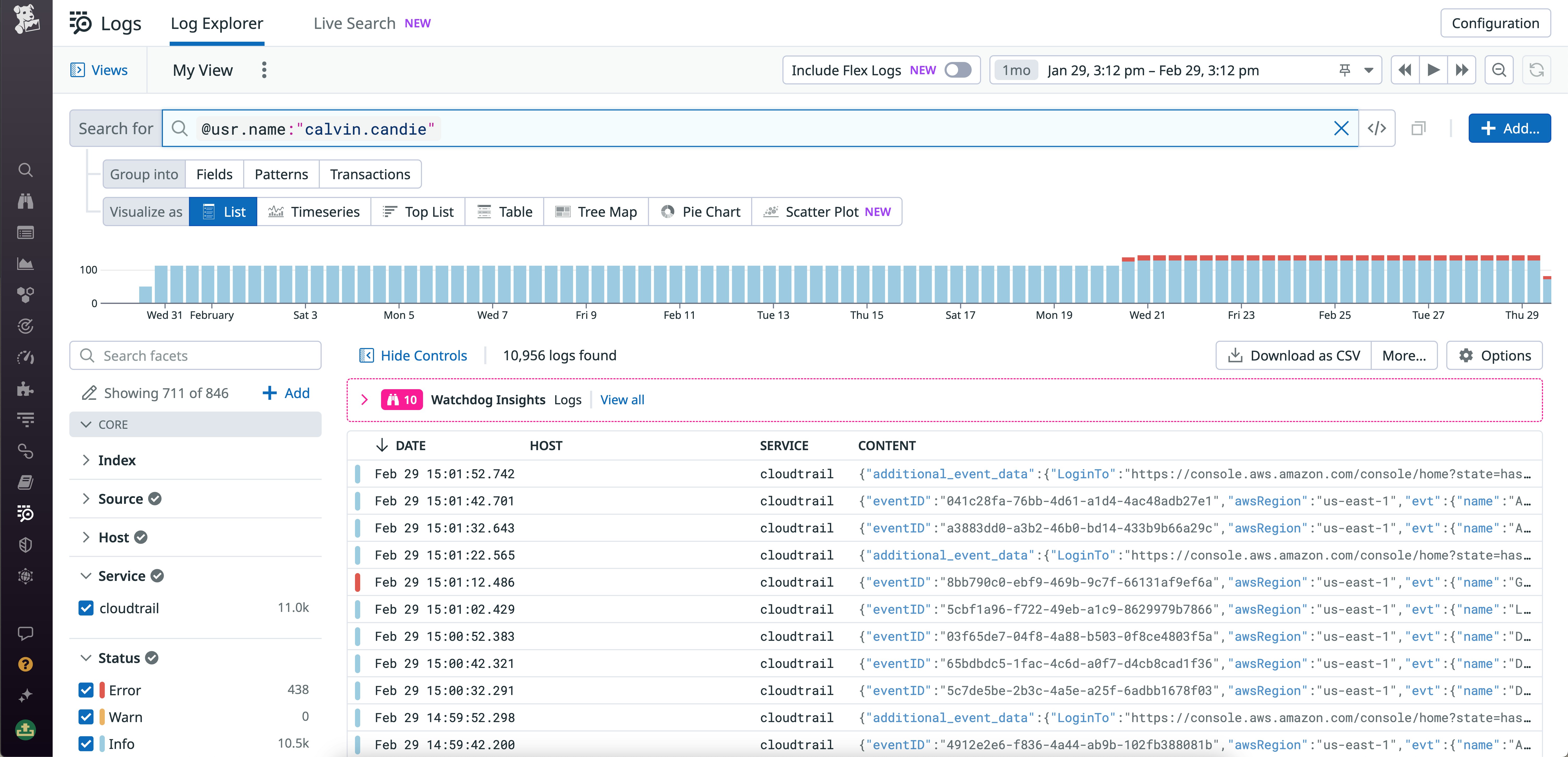
M-21-31 also contains several provisions focused on aggregating logs to ensure centralized access and visibility across teams. By letting you process, enrich, and route logs from every component of your system within a centralized view, Datadog Log Management follows these requirements and helps simplify security incident investigations. For example, let’s say one of your application teams has detected an attack where a privileged account—calvin.candie—was taken over to enable a threat actor to take unauthorized action that compromises the application’s cloud resources. The following query shows how an investigator can use Log Management to quickly surface logs for this account’s activity.
Detect emergent threats in real time
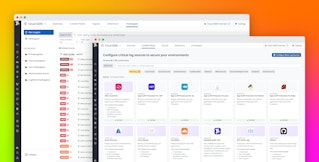
M-21-31 requires organizations to implement threat management practices to remediate threats quickly and limit exposures. Datadog Cloud Security delivers real-time threat detection and continuous configuration audits, enabling teams to trace the full attack flow and identify the targeted resource’s owner as soon as a threat emerges. With Workload Protection, users can set detection rules that catch known attack methods.
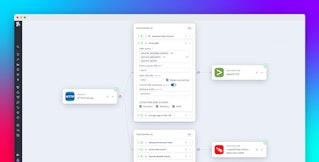
Workload Protection performs kernel-level analysis of workload activity to uncover threats and other malicious activity on your infrastructure and workloads. This is critical for mitigating attacks that can’t be easily caught using application logs alone, such as web shell exploitation. For example, the following signal shows the execution of the “Password utility” command, which is used to change user account passwords and is often an indicator of an attacker’s attempt to compromise a host and gain persistence.
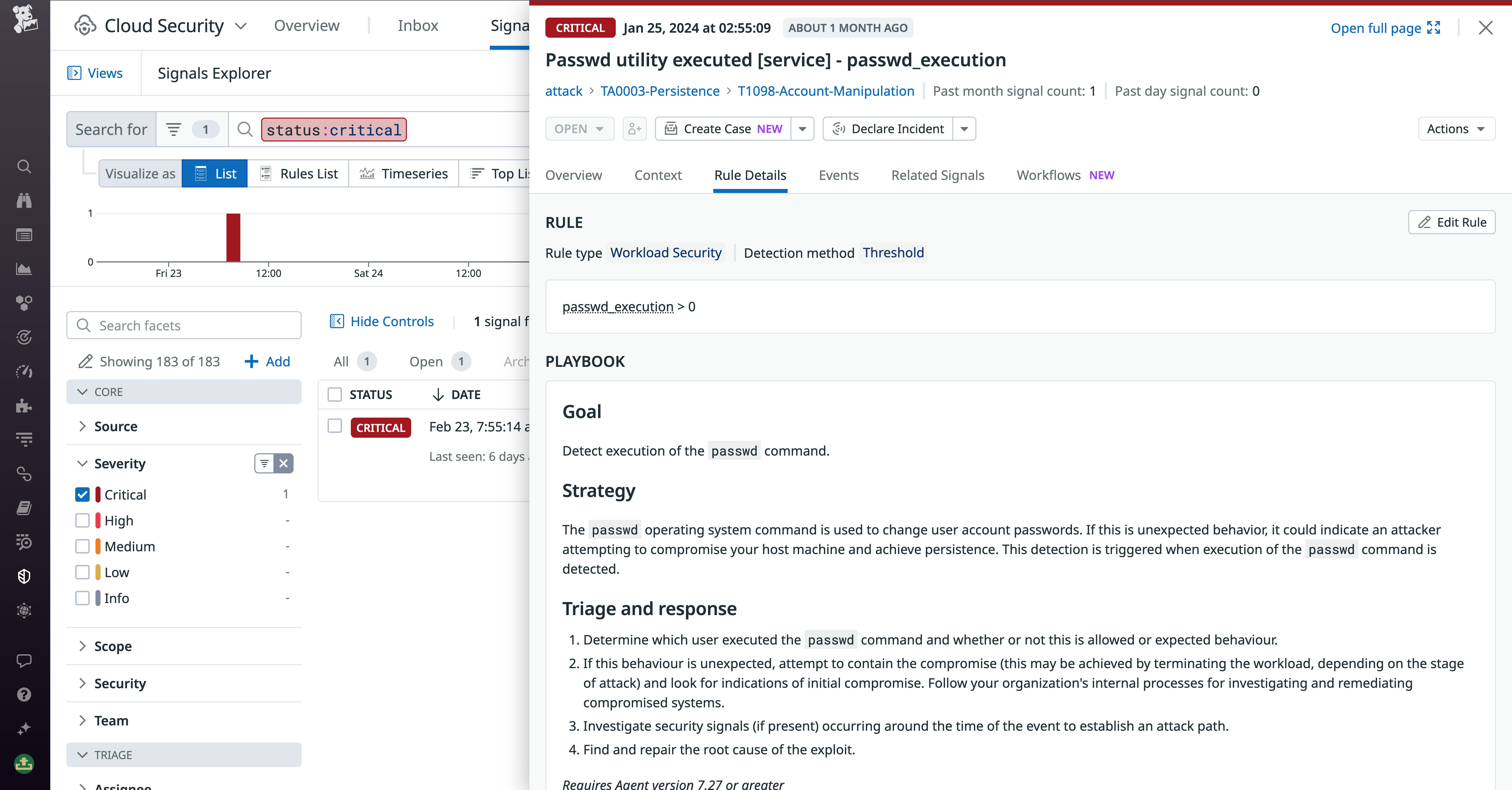
The signal contains useful context to help facilitate investigations, including information on the impacted host—the environment, impacted services, and ownership—and the full path of the event.
Secure your public sector applications
By enabling teams to access broad historical context related to security exposures and auto-detect new threats in real time, Datadog provides a comprehensive, compliant cloud security solution to help public sector organizations comply with federal requirements that will improve the nation’s cybersecurity. To learn more about how you can use Datadog Log Management to meet the requirements of M-21-31 and EO 14028, read our solution brief.
Datadog also offers free courses on log management and processing. You can sign up for Introduction to Log Management and Going Deeper with Logs: Processing to dive deeper into these topics. Or, if you’re brand new to Datadog, sign up for a free trial.