Roman Olynyk
Infrastructure as code (IaC) is the practice of managing and provisioning infrastructure through machine-readable definition files. Instead of relying on manual setup via cloud provider UIs or command lines (a practice also known as ClickOps), teams can use IaC tools like Terraform, AWS CloudFormation, and Azure Resource Manager to define, provision, and manage cloud resources using code. Advantages of this approach include:
- Scalability: IaC enables rapid scaling of infrastructure resources, allowing organizations to efficiently handle increased workloads and deploy new environments.
- Enforceability: IaC ensures consistent configurations across environments, reducing the risk of human error and configuration drift.
- Testability: Teams can validate and scan resources before they are live, ensuring infrastructure meets security, performance, or cost-efficiency standards prior to spinning up actual cloud environments.
- Version control: Storing infrastructure definitions in version control systems allows teams to track changes, collaborate effectively, and roll back to previous configurations if necessary.
While IaC has increasingly become the norm because of these benefits, undetected misconfigurations in IaC can quickly spread across environments, leading to potential security risks that can become amplified and difficult to root out. In this post, we’ll walk through:
- Several common security risks associated with IaC
- Popular open source IaC scanning tools that help organizations find misconfigurations
- How you can use Datadog to gain deeper insight into IaC risks
Common IaC security risks
Cloud misconfigurations are among the most common cybersecurity issues that organizations face. In IaC, common misconfigurations include:
- Overly permissive security groups: IaC enables teams to write security group policies as code that can then be applied across their cloud environment. If these policies are configured too permissively—for example, allowing unrestricted inbound traffic—attackers may be able to attain unauthorized access to infrastructure resources.
- Publicly writable S3 buckets: Misconfigurations in bucket policies, such as setting access control lists (ACLs) to
public-writecan allow attackers to access, add, or change data stored in your S3 buckets. - Overprivileged IAM roles: Assigning roles more permissions than necessary can increase the blast radius of a breach and make it easier for attackers to escalate privileges after compromising a cloud account.
As an example of a risky IaC configuration, the Terraform configuration below creates a publicly writable S3 bucket. This poses a significant security risk, as it allows anyone—including malicious actors—to upload, modify, and delete objects within your bucket.
terraform {...}
provider "aws" { default_tags { tags = { Environment = "production" } }}
resource "aws_s3_bucket" "static" { bucket = "static-bucket" acl = "public-write"}As the increasing complexity and volume of cloud resources grows, so does the number of potential misconfigurations like the one above. This trend makes it increasingly essential—but also more difficult—to continuously monitor IaC files for risky configurations as they are created and modified.
Open source IaC scanning tools
The primary method for monitoring IaC for security risks is static scanning, which involves analyzing IaC files without executing them. This process identifies misconfigurations, vulnerabilities, and compliance issues early in the development life cycle, allowing for timely remediation before the misconfigurations make it to production where they can be exploited.
Open source IaC scanning tools play an important role in identifying and mitigating misconfigurations before they reach production environments. Below, we cover some popular options.
Open Policy Agent (OPA)
OPA is a versatile, open source policy engine that offers a consistent way to enforce context-aware policies across various systems, providing unified governance and control over complex systems. OPA decouples policy decisions from enforcement, which helps promote flexibility and scalability.
OPA integrates with numerous technologies, including CI/CD pipelines for early policy enforcement, Kubernetes for granular control, and microservices architectures for application-level policy enforcement. This interoperability across platforms makes OPA a central policy management tool, enhancing consistency and reducing the complexity of managing different policy engines.
OPA policies are written in Rego, a high-level declarative language with a clear syntax that allows teams to precisely articulate infrastructure configuration controls. Rego’s reasoning features enable OPA (and other policy engines that use Rego) to evaluate policies based on comprehensive contextual data, like system attributes and relationships.
Checkov
Checkov is a static code analysis tool that scans your IaC files for misconfigurations that may lead to security or compliance issues. It supports multiple IaC frameworks, making it useful for organizations with diverse cloud and infrastructure technologies.
Checkov’s built-in policies cover various industry standards and best practices like CIS Benchmarks, PCI DSS, and HIPAA, so that teams have an immediate baseline for security and compliance assessment. Checkov also allows custom policy definitions using Python or YAML, enabling you to tailor checks to your specific security needs and internal standards.
Keeping Infrastructure as Code Secure (KICS)
KICS is an open source solution that analyzes IaC files to identify security vulnerabilities, compliance violations, and general misconfigurations. Supporting various popular IaC frameworks, KICS is valuable for organizations using multi-cloud or hybrid cloud environments.
It features an extensive, regularly updated library of predefined queries that address current threats and compliance requirements, helping teams quickly assess their IaC configurations against known risks. Like OPA, KICS uses Rego as its policy language.
Gain deeper visibility into IaC risks with Datadog
In order to fully secure your IaC deployments, it’s critical not only to identify misconfigurations in IaC files but also to enable engineers to proactively prevent and remediate these issues. Datadog IaC Security builds on the strengths of open source IaC scanners by extending their capabilities with an integrated observability and security platform that provides teams the context they need to take action.
Comprehensive scanning and reporting
Datadog continuously scans every commit across every branch in your GitHub repositories, giving you immediate visibility into misconfigurations exactly where and when changes are introduced. The Datadog platform surfaces IaC scan results in a centralized interface, so you can explore vulnerabilities in the same UI where you already monitor infrastructure, metrics, logs, and traces.
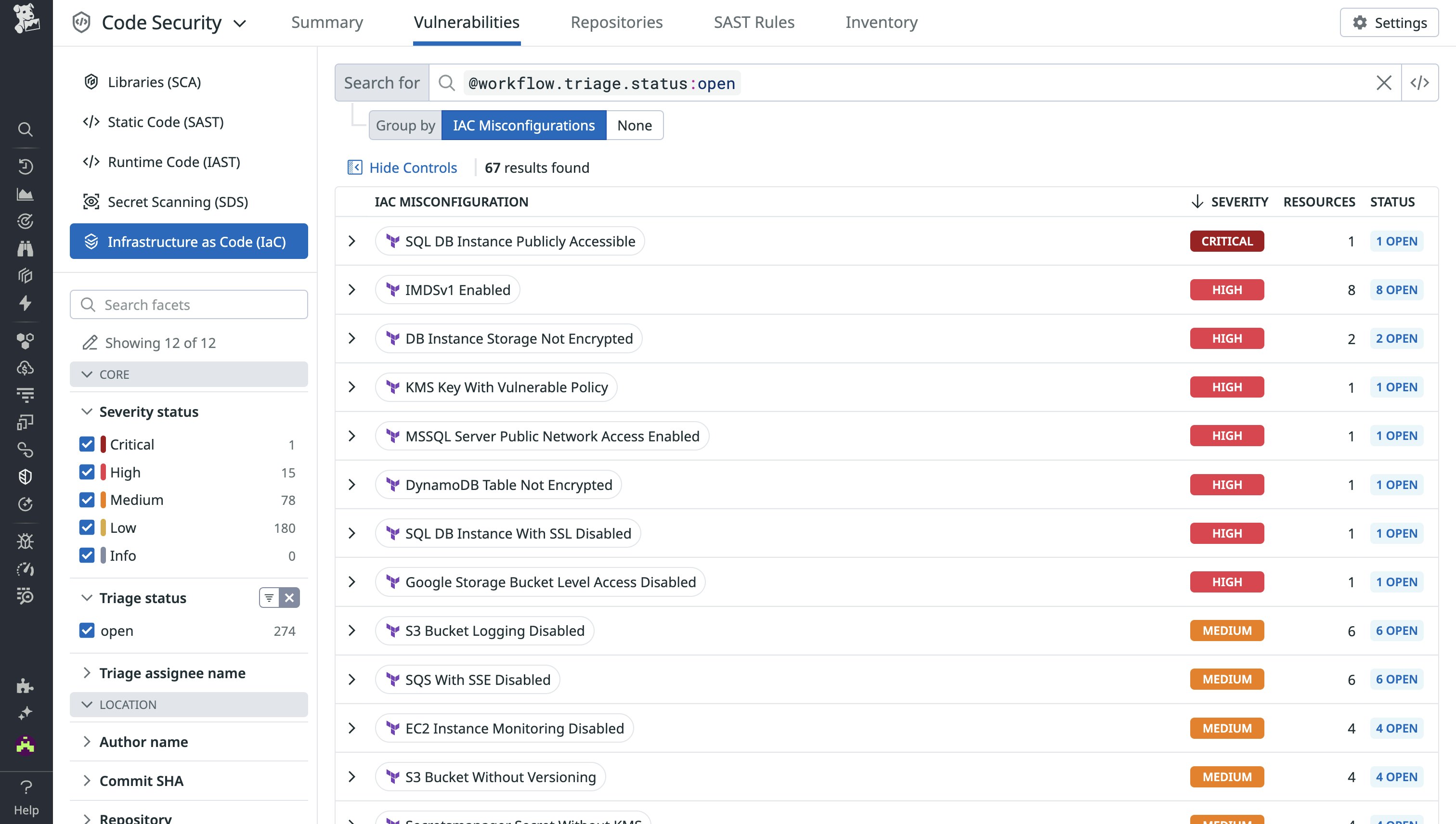
Actionable insights and fixes where your teams work
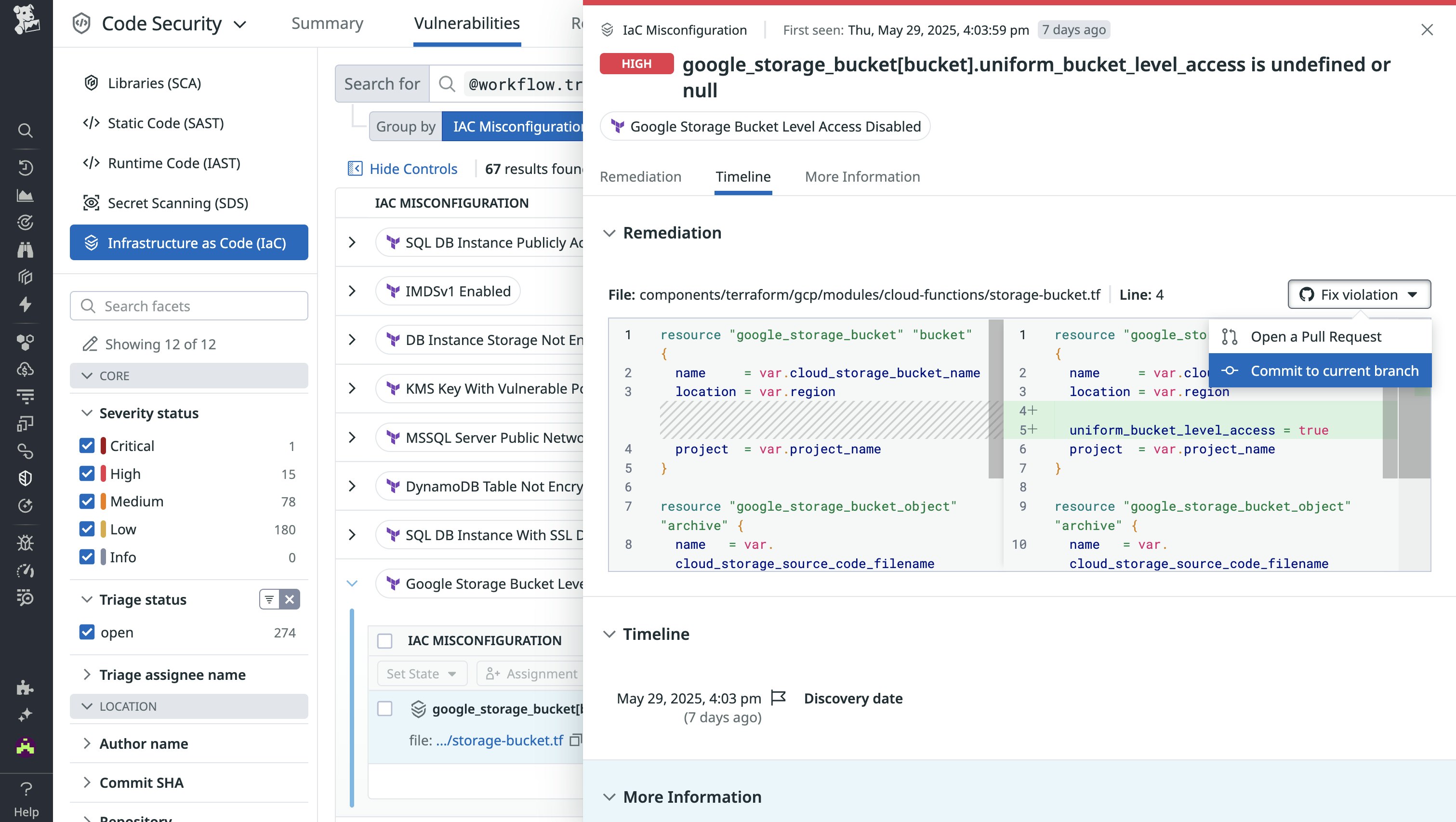
Where many open source tools stop at identifying an issue, Datadog helps you immediately act on IaC misconfigurations with detailed explanations of the risk, why it matters, and ways to potentially fix it.
For many common misconfigurations, Datadog also suggests automated fixes right inside both GitHub pull requests and the Datadog UI. These capabilities help teams close the loop without extra tooling or overhead, making security enforcement feel less like policing and more like assistance.
Connecting static and runtime context
Datadog builds on open source static IaC scanning by using over 800 Rego-based rules from KICS to find security and compliance issues in Terraform deployments across AWS, Azure, and GCP. Datadog also uses the same Rego engine for pre-deployment scanning and continuous monitoring, enabling a “write once, enforce everywhere” approach for consistent policy enforcement and a holistic view of security and compliance.
However, most static scanners analyze code in isolation, even though not all misconfigurations cause problems until infrastructure is live. With Datadog Cloud Security, teams can correlate static issues with runtime context. For example, a permission like iam:CreatePolicyVersion might seem safe in a code scan—but if that permission is actively used in production, the risk changes. Datadog surfaces this context, enabling teams to prioritize issues that actually matter based on real-world usage.
Get started with Datadog IaC Security
Datadog IaC Security provides end-to-end coverage of your cloud environment, helping you detect issues before they make it to production. IaC Security also integrates seamlessly into your developer workflows to provide a unified view of findings across code and cloud. Because you can use IaC Security alongside Cloud Security and other Datadog products, you can manage all of your detection rules in a single platform.
To learn more, check out our IaC Security documentation. If you’re not already using Datadog, get started today with a 14-day free trial.