Mallory Mooney

Justin Massey
Protecting your applications from abuse of functionality requires understanding which application features and workflows may be misused as well as the ability to quickly identify potential threats to your services. This visibility is particularly critical in cases where an adversary finds and exploits a vulnerability—such as inadequate authentication controls—to commit fraud. Monitoring your applications for abuse can help you surface critical security gaps in your services and provides a complete and accurate record of events. This enables you to conduct investigations and mitigate threats before they negatively affect your company’s bottom line.
In this post, we’ll cover:
- the stages of application abuse and some common attacks used at each stage
- detecting and mitigating signs of application abuse and fraud
- how to use Datadog to help you proactively monitor your applications
We’ll also look at some specific questions you can ask about your applications and services to help you get a better understanding of how they may be vulnerable to abuse and fraud.
A primer on application abuse and fraud
Abuse of functionality, or application abuse and fraud, is any instance where an adversary misuses your application’s functionality for personal gain or uses an application feature as part of an attack chain to gain access to a business-critical system. According to the MITRE ATT&CK® framework, these types of attacks can differ in levels of severity and often leverage a combination of tactics over a period of time. Which tactics an adversary uses depends on what they are trying to achieve and how much access they may already have to your systems. The key tactics that we will cover in this post include:
- Reconnaissance: actively or passively gathering information about your application in order to find vulnerabilities
- Resource development: using various techniques to create or steal resources that can be leveraged in an attack
- Credential access: attempting to steal account credentials and gain access to your application or other application services
- Persistence: maintaining a permanent foothold in your application
- Impact: disrupting application availability or manipulating business processes
The MITRE ATT&CK framework can help you map tactics to specific techniques an adversary may use to target application components and abuse existing functionality. Next, we’ll look at a few common techniques for each of these tactics.
Reconnaissance
With the reconnaissance tactic, an adversary may leverage techniques such as initiating a password reset for a list of email addresses in order to find valid users for your application. They may also deploy bots to scrape (or harvest) data from your application resources, such as API endpoints and databases, to gather information about your inventory or product prices. All of this data could be used at a later stage in an attack. Additionally, other companies may attempt to find and harvest data that is not publicly available (e.g., behind a paywall) in order to analyze your customers’ activity or purchasing trends, gain a competitive edge, and decrease your market share.
Resource development
As part of the resource development tactic, an adversary will establish the capabilities, tools, and data (i.e., resources) they need to carry out an attack. These might be creating malware, compromising email or social media accounts, or gathering valid credit cards. As part of this process, an attacker may misuse your application’s functionality to test resources before they use them on another third-party service or application. For example, they may test a list of stolen credit cards by signing up for several free trials on your application in order to find valid ones. This enables them not only to take advantage of your application’s features but also hide their activity trail when they make larger purchases elsewhere—a transaction using a valid credit card is more likely to go unnoticed than several declined transactions.
Credential access
In order to gain access to your applications, adversaries will first find ways to exploit insufficient security controls in authentication flows using various techniques such as password guessing or credential stuffing. With these types of attacks, adversaries iterate through lists of stolen usernames and password pairs—typically obtained from publicly available data dumps or purchased on the dark web—in order to find and take over a valid account.
Persistence
Once an adversary has access to your application, they may create new accounts or modify existing ones in order to maintain a foothold in case of an interruption that blocks their access, such as updates to account credentials or a patched vulnerability. Account creation can also be a sign of an insider threat misusing their level of access in order to maintain persistence within a critical system. For example, an employee may create a backdoor administrative account for one of your (or one of your customer’s) services in order to steal data after they leave your company. Or, they may create a new API key that they can still use after their account is revoked since API keys in applications are sometimes not tied to a user account. These instances of application abuse can be more difficult to identify, so it’s important to monitor all types of activity, regardless of the source, in order to detect threats before they disrupt service availability or manipulate business processes.
Impact
With the impact tactic, adversaries leverage attacks to manipulate, disrupt, or sabotage application resources. E-commerce applications are particularly susceptible to these types of attacks on their inventory and payment services. For example, an adversary may attempt to find valid discount codes through token dictionaries or other brute-force methods in order to take advantage of service benefits like reduced prices, limited offers, or credits. In online booking applications, an adversary may create bots to obtain (i.e., scalp) products that have limited availability, such as concert tickets, and sell them on third-party marketplaces for a profit.
An adversary may also use “denial of inventory” attacks to deplete your inventory, or “denial of service” (DoS) attacks to overload your servers with large amounts of traffic. Both of these attacks prevent your users from purchasing or reserving goods or services, which negatively affects your company’s bottom line.
Impact tactics can also be used to take advantage of functionality in banking applications as part of an attack chain. For example, an adversary may use a compromised banking account to transfer funds to another external account that they control. This kind of activity is difficult to identify because it leverages a legitimate feature, so it’s important to have end-to-end visibility into your application in order to find signs of application abuse and fraud.
Now that we’ve seen some examples of how an adversary may misuse an application or application resources, we’ll look at how to detect these types of attacks when they occur.
Identify signs of application abuse and fraud
Your application and infrastructure logs capture activity from across your environment that can help surface key patterns that are invaluable for identifying and mitigating abuse techniques, such as a series of failed credit card authorizations from a single user or IP address. But sifting through all of your logs in order to detect legitimate threats can be challenging, so it’s important to understand how to filter out any noise and identify the right logs for detecting malicious activity.
There are some questions you can ask about your applications to better understand the types of activity you should monitor in order to identify the tactics an adversary may be using to target you. These questions include:
- Is my application exposing information that someone would want to harvest?
- Can an adversary exploit my authentication, registration, or password reset flows?
- Can an adversary target my inventory?
- Can an adversary misuse services to steal from my company’s bottom line?
- How can a user abuse their level of permissions?
Next, we’ll look at these questions in more detail. We’ll also show how to use Datadog to detect activity associated with each one.
Is my application exposing information that someone would want to harvest?
In order to gather more information about your applications, an adversary will deploy bots to scan your applications for common vulnerabilities that they can easily identify, such as open ports or outdated service libraries or dependencies. They may also scrape your applications to find information which may be publicly or privately accessible.
This kind of activity looks like normal user activity (e.g., requests all return 200 OK response status codes), which makes it difficult to detect. But there are some identifiers that you can look for in your logs. In cases where someone is scanning your application, you may see a higher than usual number of unique HTTP paths requested by an IP address or a specific user. If this activity is coming from an authenticated user, then it could mean that the user’s account is compromised or that the user is violating your terms of service.
You can use Datadog’s custom Threat Detection Rules to automatically detect this kind of activity so that you can quickly determine if it is legitimate or needs further investigation. If you discover that it is a part of a targeted attack, you can use a web application firewall to block the malicious IPs or implement rate limiting or reCAPTCHA to slow an adversary down. Otherwise, if the user is authenticated, you may want to review their account activity in order to determine whether it is illegitimate.
Can an adversary exploit my authentication, registration, or password reset flows?
Your authentication, registration, and password reset flows are some of the first components that adversaries target since they grant access to your application services and data. As such, it’s important to determine if they are vulnerable to attacks such as credential stuffing or information exposure. These are common techniques used as part of the reconnaissance and credential access tactics.
In cases where your authentication flows are being targeted, you may see hundreds or thousands of unique usernames failing to login from the same IP address, possibly intermixed with successful attempts. This sequence of events means that an adversary has successfully found a valid account. You can investigate this kind of activity by searching for and reviewing all of the usernames a suspicious IP address has successfully logged in as in order to find the compromised account. On the other hand, you may not initially notice activity like password resets and new account registrations because there is no indicator of compromise, such as a successful login. You can review your logs to determine if there is an unusual increase in password reset attempts for the same accounts or new account registrations within a short period of time.
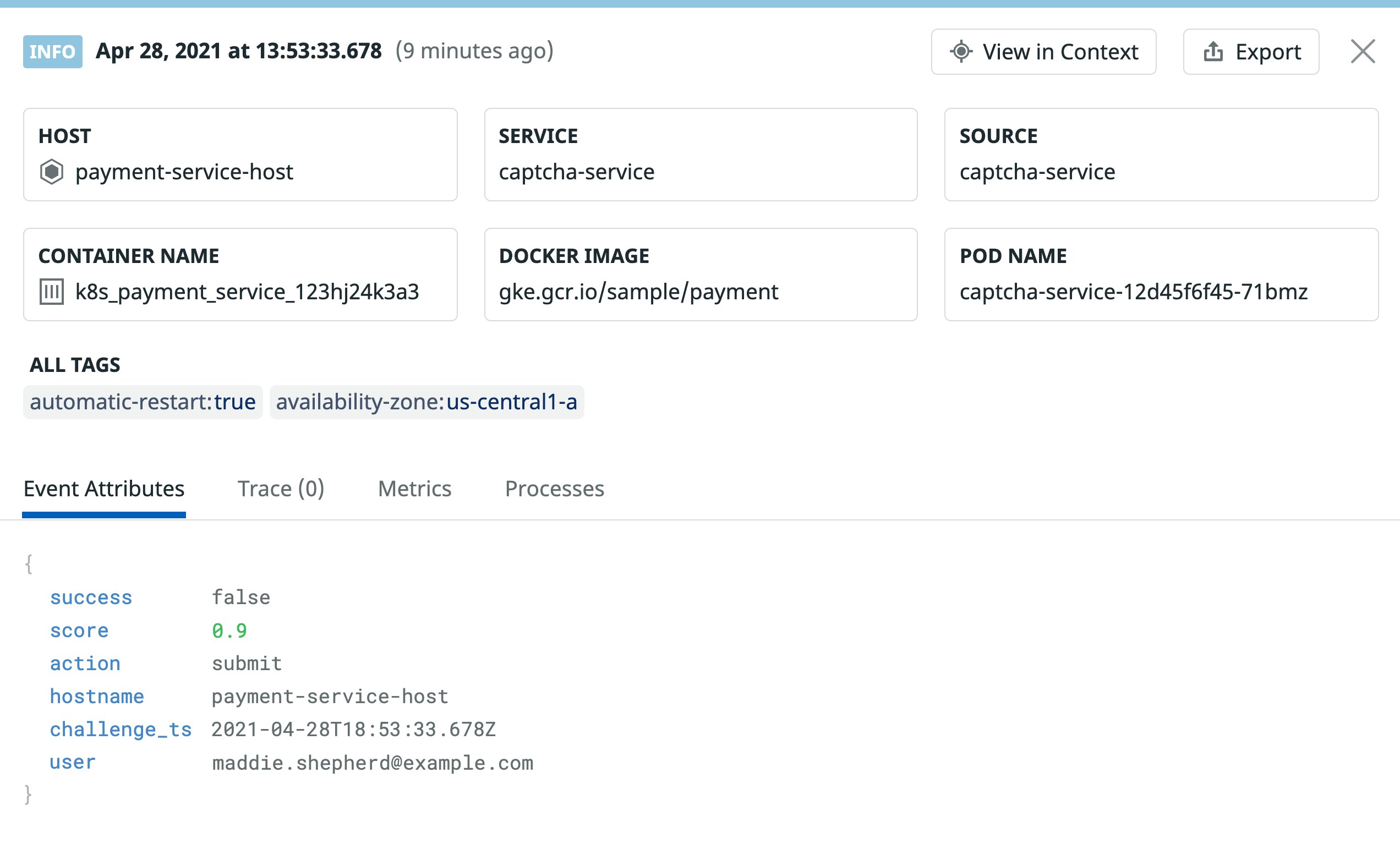
There are a few steps you can take to enhance the security of your authorization and authentication flows and prevent these types of attacks. For example, you can enable two-factor authentication or add limits to the number of failed login attempts you allow. You can also enable reCAPTCHA v3 for all login prompts and use Datadog to log and monitor the score it returns from a login attempt—a score of 0.0 is likely indicative of a bot.
Can an adversary target my inventory?
Once an adversary has access to your application, they may find ways to exploit services for personal gain or to bring them offline. This kind of activity is critical to mitigate as soon as possible, especially in e-commerce applications that provide services for booking venue tickets, hotel rooms, or flights, as it prevents legitimate customers from using them.
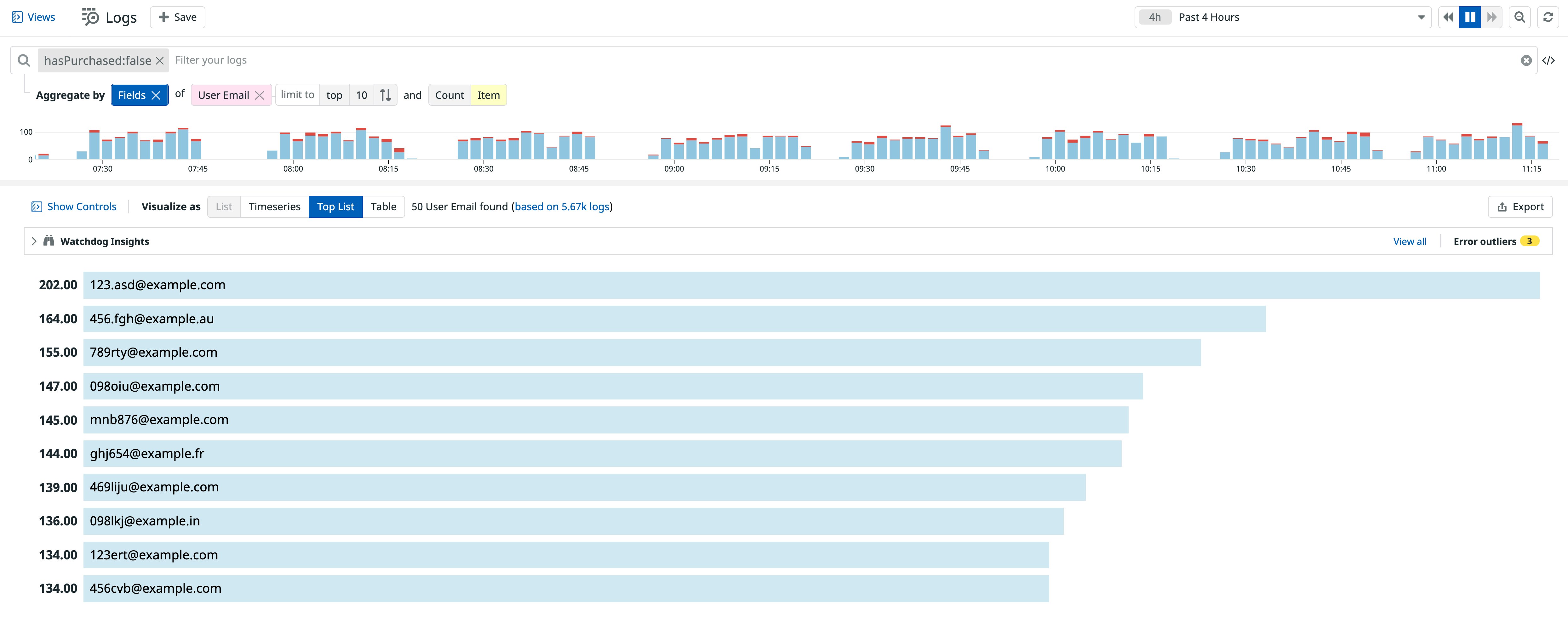
As previously mentioned, there are a few different ways an adversary can target your inventory, such as launching a denial of inventory attack to prevent legitimate customers from purchasing goods or services. In these cases, you may see an influx of application logs in Datadog for newly created accounts, which are often used to bypass purchase limits. You can also log whether a customer makes a purchase in order to help you isolate any unusual accounts from legitimate traffic.
To mitigate these types of threats, you can set a limit on how long an item or reservation can remain in a user’s cart and throttle transactions to prevent someone from purchasing several items within a short period of time. You can also leverage threat intelligence feeds, such as those managed by Datadog, to surface activity from flagged IP addresses.
Can an adversary misuse services to steal from my company’s bottom line?
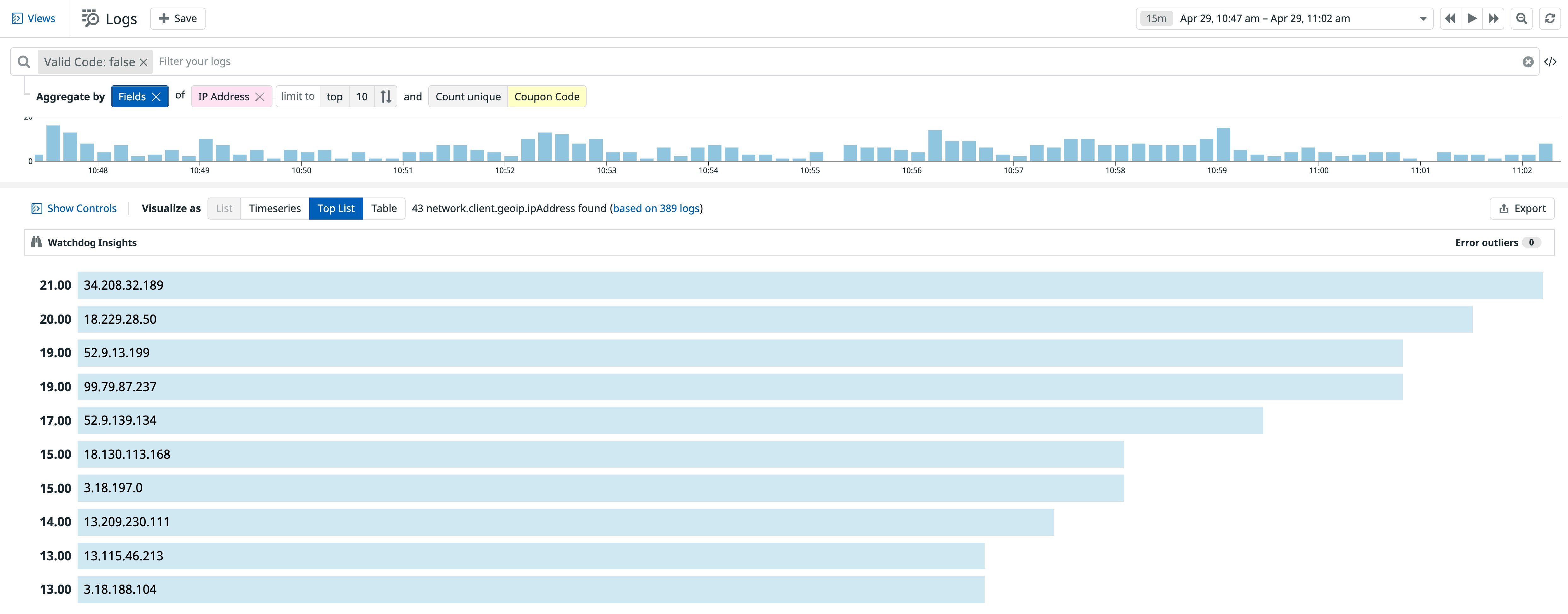
In addition to targeting your application’s inventory, an adversary may attempt to disrupt or take advantage of other services critical to your business, such as a payment service or a customer rewards program. For instance, you may see a sudden increase in failed attempts to use a discount code from the same IP address within a short period of time. This could mean that someone is enumerating through a list of codes in order to find a valid one for your application. Once they find a valid code, they may create new accounts in order to reuse it.
By logging whenever a user applies a coupon code along with its status, you can search for requests that include invalid coupon codes and drill down to the specific IP addresses making the requests.
Limiting account creation and code submission attempts per IP address can help prevent adversaries from misusing services. Once you identify the malicious IP address, you can use a web application firewall to block it from accessing your application.
Can a user abuse their level of permissions?
Some instances of application abuse and fraud are not caused by external parties but by insider threats that take advantage of gaps in your company’s security controls. For example, an employee may misuse their level of access to create a backdoor administrative login in a customer’s account, which is a technique used as part of the persistence tactic. This would enable the employee to access and potentially misuse customer data even after they leave your organization.
The following examples are a few other ways a user, such as a support administrator, may abuse their permissions:
- Create an API key in a customer’s account
- Issue a monetary credit to a customer
- Reset a customer’s free-trial subscription
- Modify a customer’s database
- Initiate a database dump on a customer’s account
- Invite a new user to a customer’s account
Many of these examples may be normal support operations, so you will need to determine which activity you want to focus on. But, even if you choose to accept the risk by not actively monitoring certain activity, it’s important to capture all of it through your application and authentication logs to ensure you have all of the information you need to fully diagnose a threat and create suitable detection rules. This enables you to review any activity when needed, so you can always be aware of potential risks—even if you decide to not address them at the time.
In order to decrease the risk to your application and ensure customer data is safe you can enable “least privilege” policies for internal services and periodically audit existing account permissions.
Proactively monitor abuse of functionality with Datadog
Datadog gives you full control over which logs to ingest, archive, and query, so you can decide how to best capture evidence for detection and investigation, conducting security audits, and further mitigation. Datadog collects all of your application, infrastructure, and cloud provider audit logs and uses them to provide deeper insights into application activity and security. For example, Datadog can generate a Security Signal to automatically alert you when a support administrator creates a new API or application key for one of your (or one of your customer’s) services.
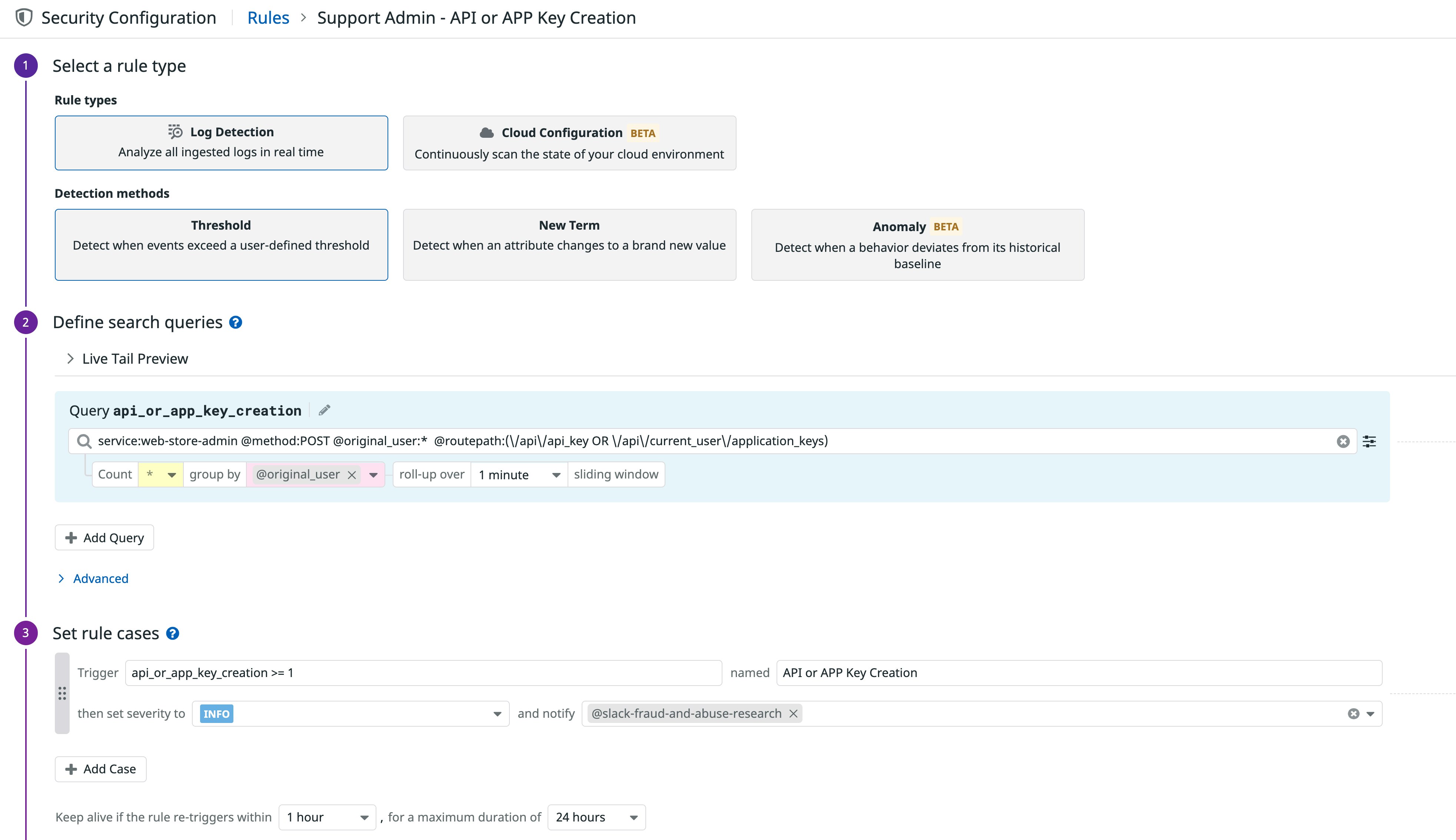
With Datadog’s curated threat intelligence, you can immediately see if suspicious activity has been flagged as a known threat without having to manage your own intelligence feeds. This gives you greater confidence in identifying risks to your applications. For example, the Security Signal below shows a user logging into a service from an IP address that has been marked as malicious by GreyNoise, a Datadog threat intelligence partner.
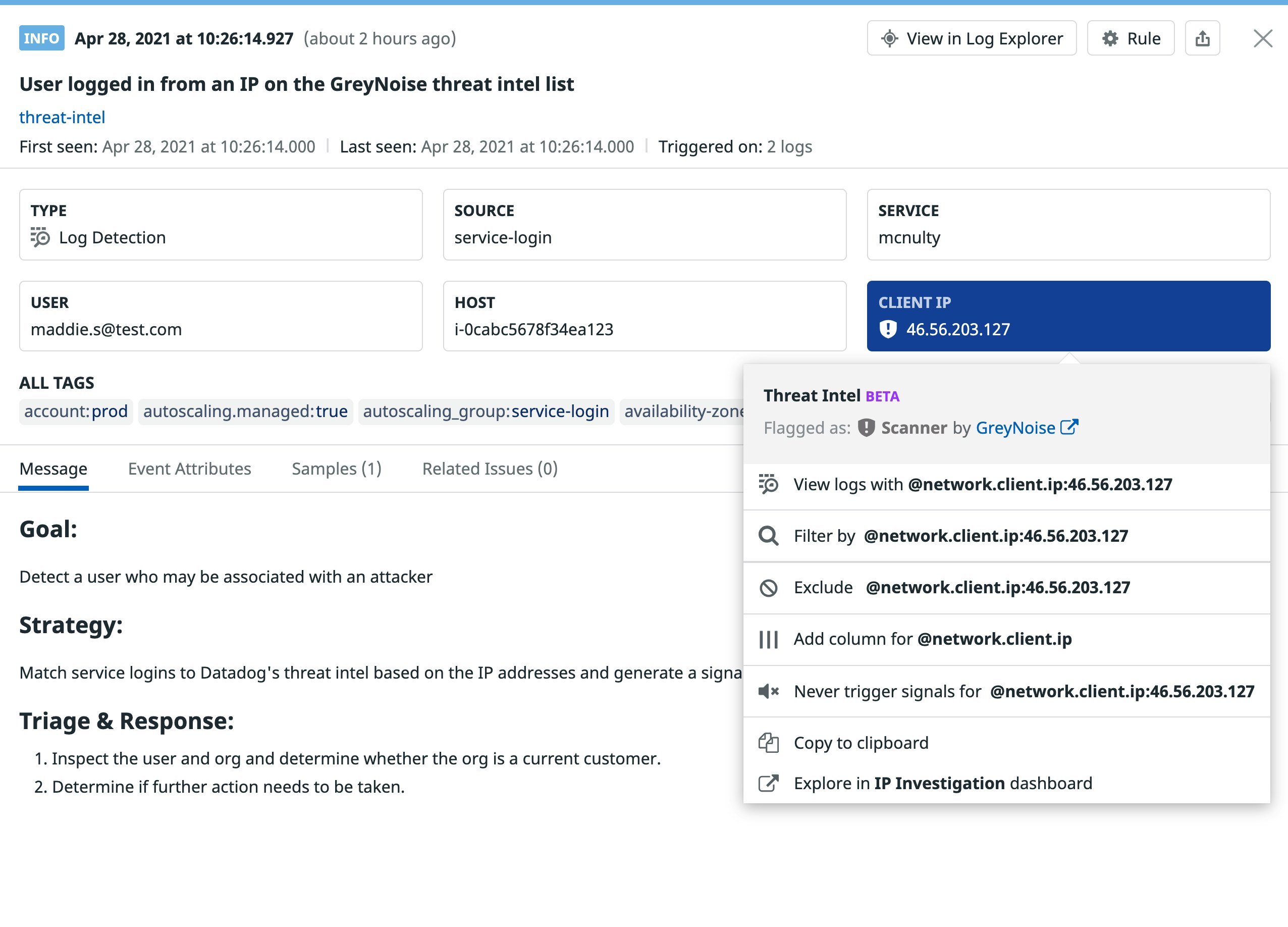
Full visibility into application activity
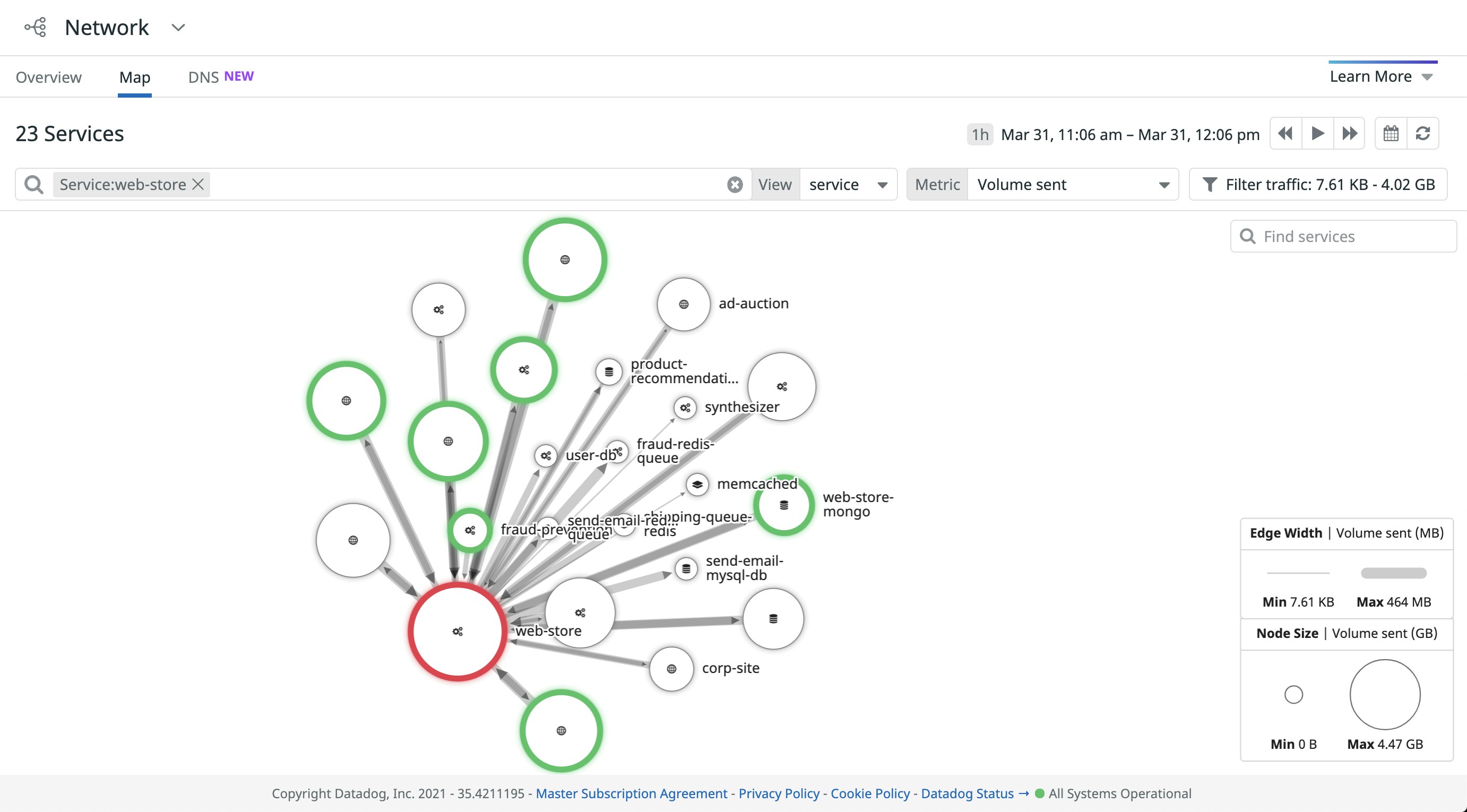
In addition to detecting malicious activity through your logs, Datadog gives you full visibility into how that activity affects your application resources. Datadog’s Service and Network Maps enable you to visualize which parts of your application an adversary is targeting. For example, you can use the Network Map to easily identify large amounts of traffic to a specific application service that might bring it offline. These maps can be useful in gathering data about how your services interact with one another for more effective threat modeling, which helps you identify weak points or missing security controls in your applications that an adversary might abuse.
You can also use Datadog Notebooks to create security runbooks that include more comprehensive detection and mitigation steps. For example, the runbook below provides a response to a possible malicious scanner.
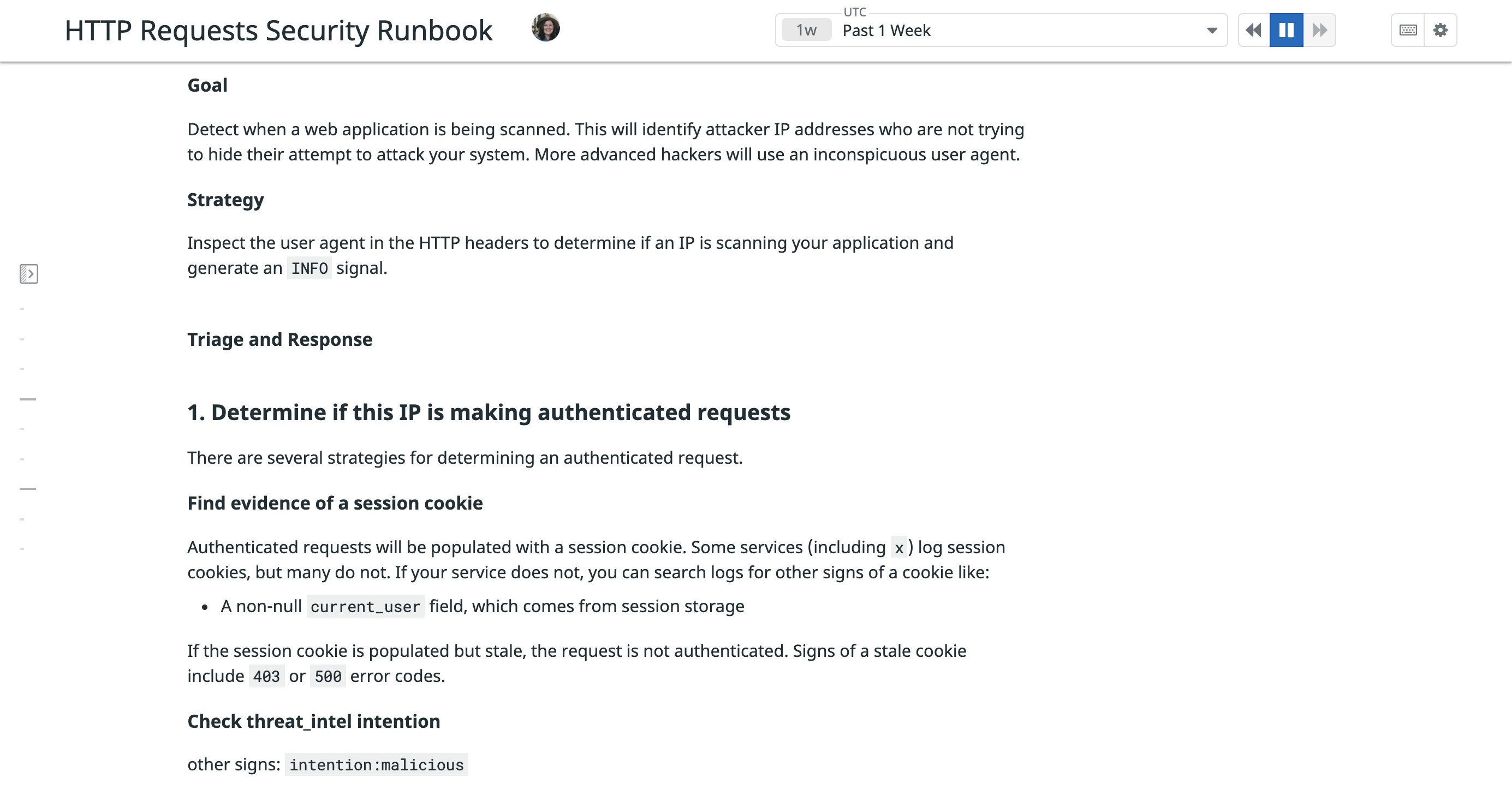
This enables you to investigate specific instances of application abuse and fraud and share your findings with teammates, so they can fully understand which application components were targeted by an attack and how to stop it.
Use Datadog to mitigate abuse of functionality
In this post, we’ve discussed some of the common ways an adversary can find and exploit vulnerabilities in your application services. Datadog can help you monitor this and other types of potentially malicious activity, so you can take the necessary steps to secure your applications before an attack negatively affects your services or customers. Check out our documentation to learn more about Datadog’s security offerings. If you don’t already have a Datadog account, you can sign up for a free 14-day trial today.