Jean-Claude Kuo
For developers and security engineers alike, one of the most persistent challenges in cloud security is making sense of how compute, storage, identity, and networking components interact. Traditional security tools often lack the ability to surface multi-hop access paths, making it difficult to answer questions like: “Which EC2 instances can access sensitive S3 buckets, and are any of them exposed to the internet?” Datadog Security Graph addresses this problem by modeling your cloud environment as a dynamic, relationship-aware graph. Built on data from Datadog Cloud Security, it enables you to visualize and query the real-world connections between cloud resources, helping you surface indirect access paths, assess identity risk, and respond more effectively to emerging threats.
In this post, we’ll show you how to use Datadog Security Graph to:
- Identify potential attack paths within your cloud resources
- Analyze identity policies with Access Insights
Identify potential attack paths within your cloud resources
Security Graph reimagines your cloud environment as a graph of nodes and relationships. Resources such as EC2 instances, IAM roles, S3 buckets, and security groups are represented as nodes, while access relationships, trust relationships, and network exposure are modeled as edges. This approach has several advantages:
- It captures both direct and transitive relationships, such as a role assuming another role that has access to a resource.
- It enables you to spot indirect access paths and risk exposure that would otherwise remain hidden in IAM policies or configuration files.
- It reflects how attackers think, identifying possible pivot points between resources.
- It gives security teams a complete, contextual view of risk across their cloud environments.
While piecing together relationships across your cloud resources manually would be time-consuming and error-prone with traditional inventory tools, Security Graph combines data from Agentless and Agent-based cloud scanning to offer a detailed view of these relationships. It includes several features that help teams investigate and respond to risk:
- Prebuilt queries for common security questions, such as, “Which publicly accessible EC2 instances have administrative IAM roles?”
- A no-code query builder to help you dive deeper and find potentially risky relationships among your cloud resources
- Interactive visualizations that let you explore cloud resource graphs and view metadata, tags, and linked security findings
- A tabular view for analyzing and exporting results at scale
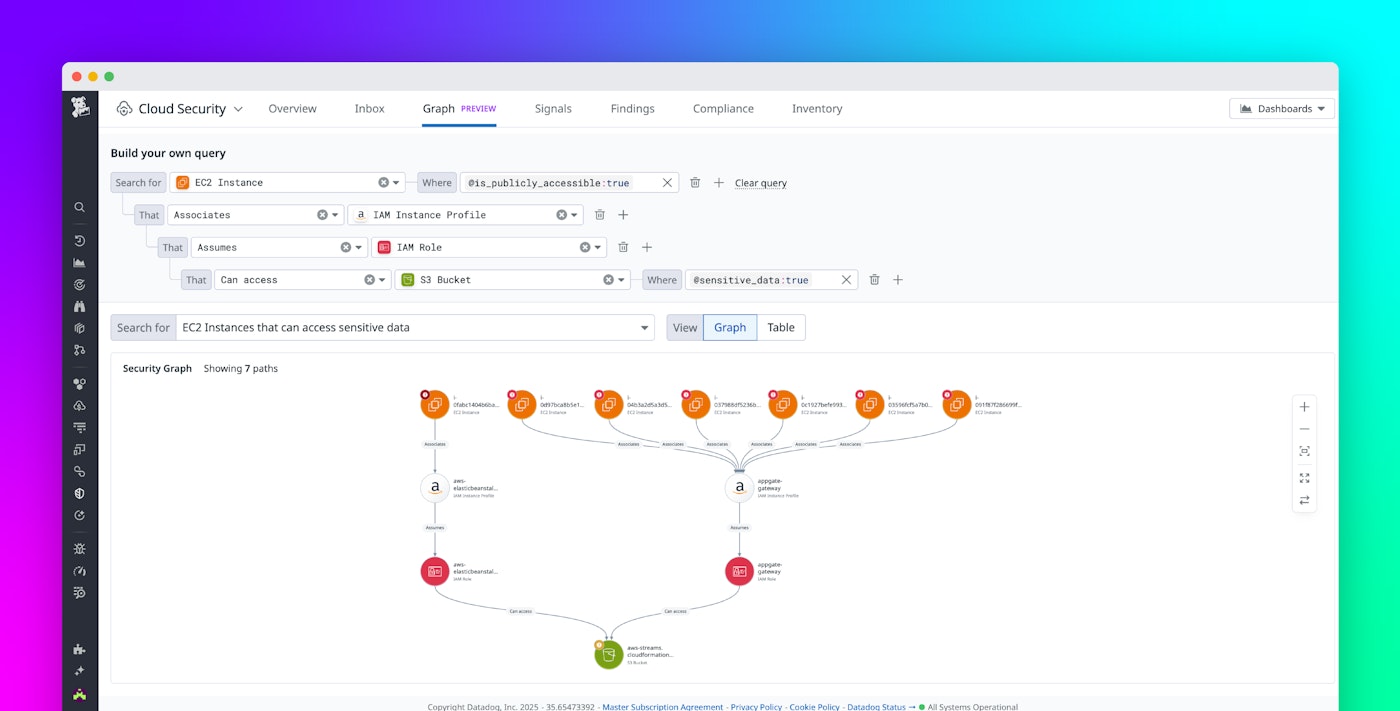
For example, let’s say you’re trying to find any publicly accessible EC2 instances that can access S3 buckets containing sensitive data. This type of investigation requires analyzing a multi-hop path that might look like this:
- A public EC2 instance is associated with an instance profile.
- That instance profile is bound to IAM Role A.
- IAM Role A has a policy that allows it to assume IAM Role B using
sts:AssumeRole. - IAM Role B has a permission policy that grants access to specific S3 buckets (e.g.,
s3:GetObject,s3:ListBucket).
Security Graph makes this entire access chain visible and queryable, enabling you to visualize the exact kinds of resources and paths you’re looking for.
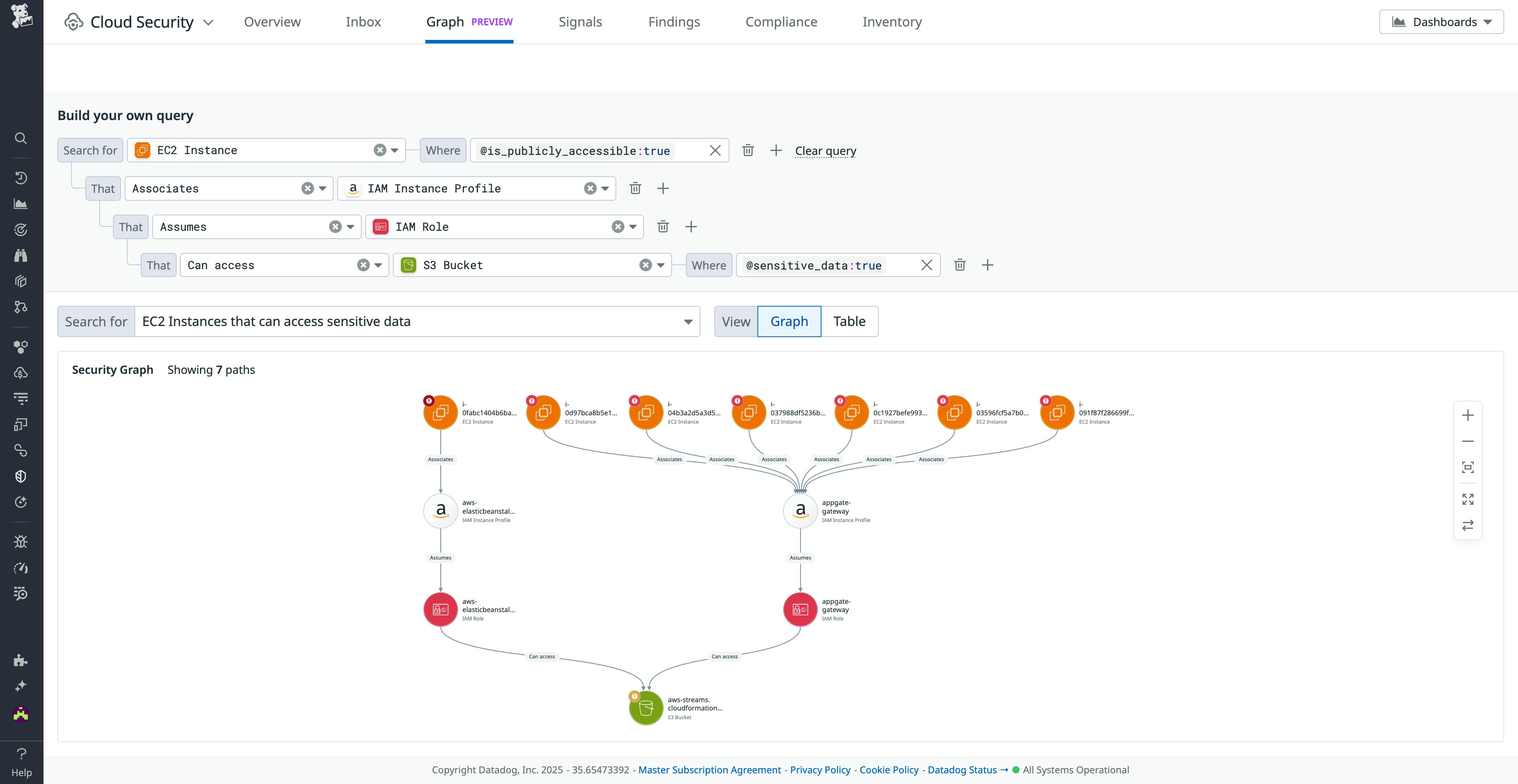
This visualization reveals not just whether access exists, but how it’s granted, enabling teams to assess whether those paths are expected, misconfigured, or overly permissive. With this information in hand, you can remediate any resources where these configurations are unwanted or excessive, limiting your infrastructure’s risk exposure.
Analyze identity policies with Access Insights
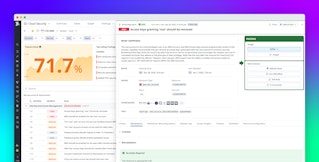
Security Graph also powers Access Insights, which calculates effective permissions for any identity or resource by analyzing:
- Direct policies (inline, AWS-managed, customer-managed)
- Indirect policies (assumed roles, group memberships)
- Resource-based permissions (service control policies, permission boundaries)
When you select a resource in the Security Graph, you’ll bring up a detailed side panel that includes these insights. This data helps you answer questions such as:
- What can this EC2 instance access?
- Which roles or users can read from this S3 bucket?
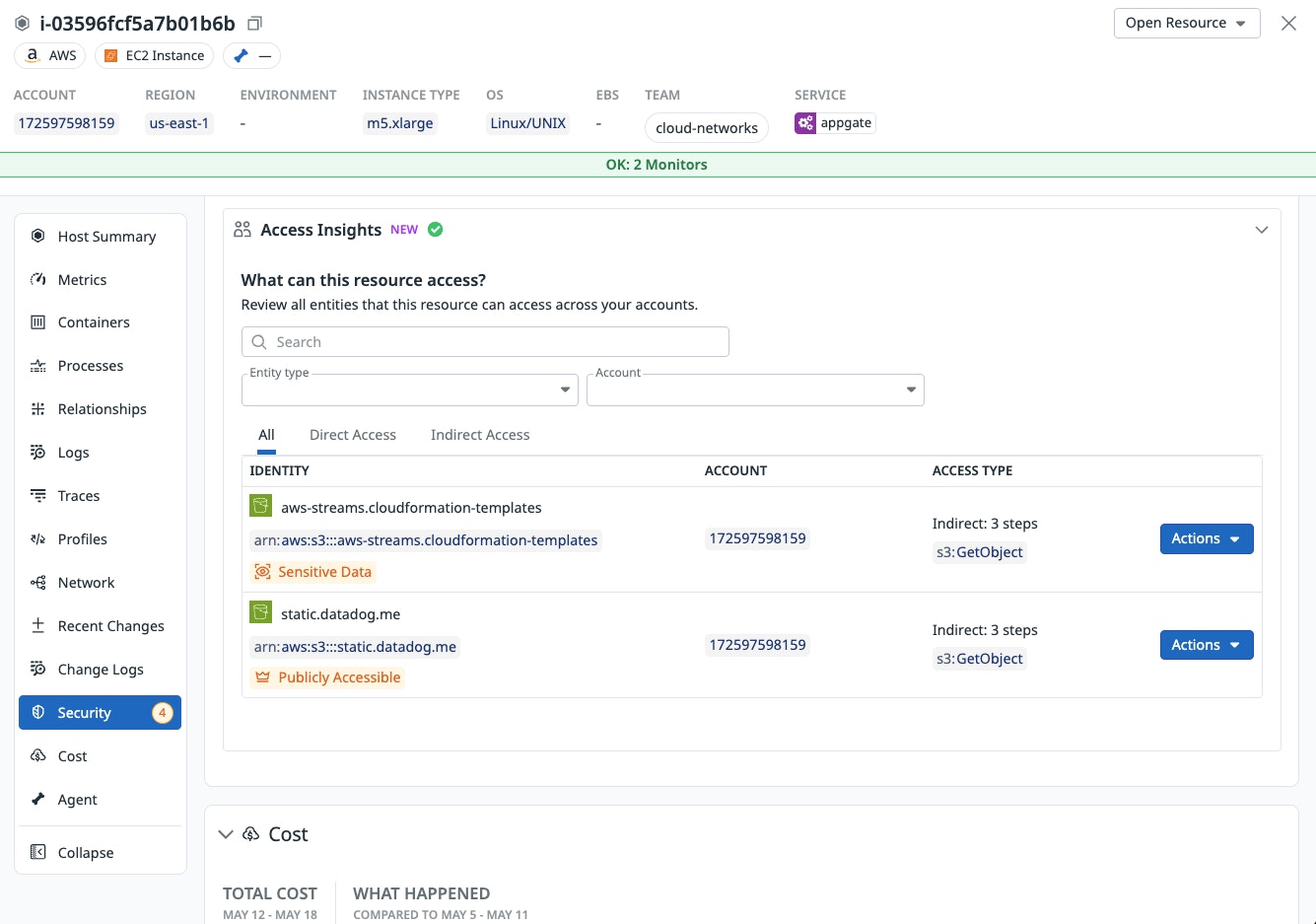
By surfacing both explicit and transitive access paths, Access Insights helps you right-size IAM policies and reduce the potential for lateral movement.
Understand cloud risks holistically with Security Graph
Datadog Security Graph provides security and DevOps teams a real-time, relationship-based view of risks across their infrastructure, so they can:
- Accelerate investigations: Visually trace access paths in seconds instead of reviewing IAM policies line-by-line.
- Analyze blast radius: Understand the downstream effects of a compromised identity or misconfigured policy.
- Perform proactive security reviews: Identify and remediate risky access paths before they reach production.
By modeling access the way attackers do—through connected paths rather than isolated nodes—Security Graph helps everyone make more informed decisions about infrastructure risk.
Datadog Security Graph is currently in preview and available to customers who use Datadog Cloud Security. Sign up for the preview and check out our documentation to get started. If you’re not yet using Datadog, you can sign up for a 14-day free trial.