Roman Olynyk
Modern infrastructure is built and deployed faster than ever, but increased speed can elevate risk. Developers who work on cloud-native applications often use infrastructure as code (IaC) to define cloud resources in configuration files, which are then shared across teams and deployed automatically. Although this approach is efficient, undetected misconfigurations in IaC can quickly introduce security risks into production environments.
Datadog IaC Security, now generally available, helps your teams shift security left by scanning cloud configuration files directly in their Git workflows. IaC Security detects misconfigurations, policy violations, and insecure defaults before they impact your environment, giving you the visibility and context to fix issues at their source.
In this post, we’ll show how IaC Security helps you:
- Identify cloud configuration risks before they’re deployed
- Empower developers to build and remediate without slowing delivery
- Track IaC security posture over time with Datadog reporting
Identify cloud configuration risks before they’re deployed
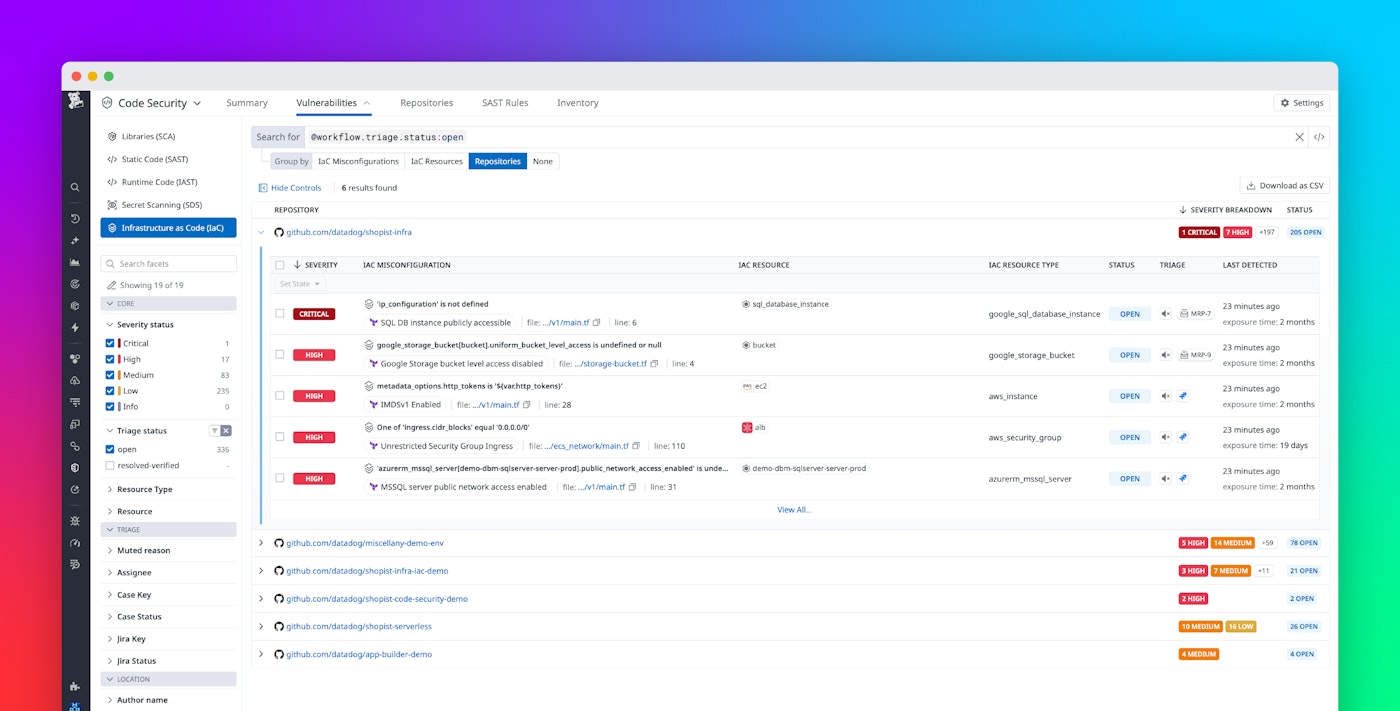
Datadog IaC Security scans every commit across all branches in your GitHub and GitLab repositories, surfacing risks where they’re introduced. Findings appear directly in the Datadog UI, so your engineering and security teams can track configuration issues alongside infrastructure, metrics, logs, and traces without switching tools.

With real-time scanning, you can catch critical misconfigurations such as publicly exposed storage buckets, unencrypted resources, and overly permissive IAM roles before they make it to production. Datadog also supports local Terraform module scanning, helping you identify violations in custom reusable components.
To prevent risky changes from being merged, Datadog supports Quality Gates. You can use this feature to create rules to block pull requests (PRs) that violate thresholds of your choosing. For example, you can block deployment of code that has vulnerabilities of critical or high severity.
IaC Security also does a daily full scan of your configured repositories, allowing you to identify and remediate misconfigurations that already exist in your code.
Empower developers to build and remediate without slowing delivery
Datadog IaC Security integrates directly with your Git-based workflows, enabling your developers to address security concerns and prevent configuration drift without having to learn new tools.
When a violation is detected, IaC Security automatically adds a comment to the PR and provides details about the issue, including the affected code block, severity level, and, in some cases, a recommended fix. (Note: We are continually increasing the number of rules that include recommended fixes.) PR comments can be customized based on rule, severity, or repository, helping your teams fine-tune their policies while avoiding noise.

You can exclude or mute specific findings by using exclusions or by creating mute rules to enable context-aware filtering (for example, by service or by environment). This flexibility helps your teams enforce or relax security standards to suit different environments, workflows, and compliance requirements.
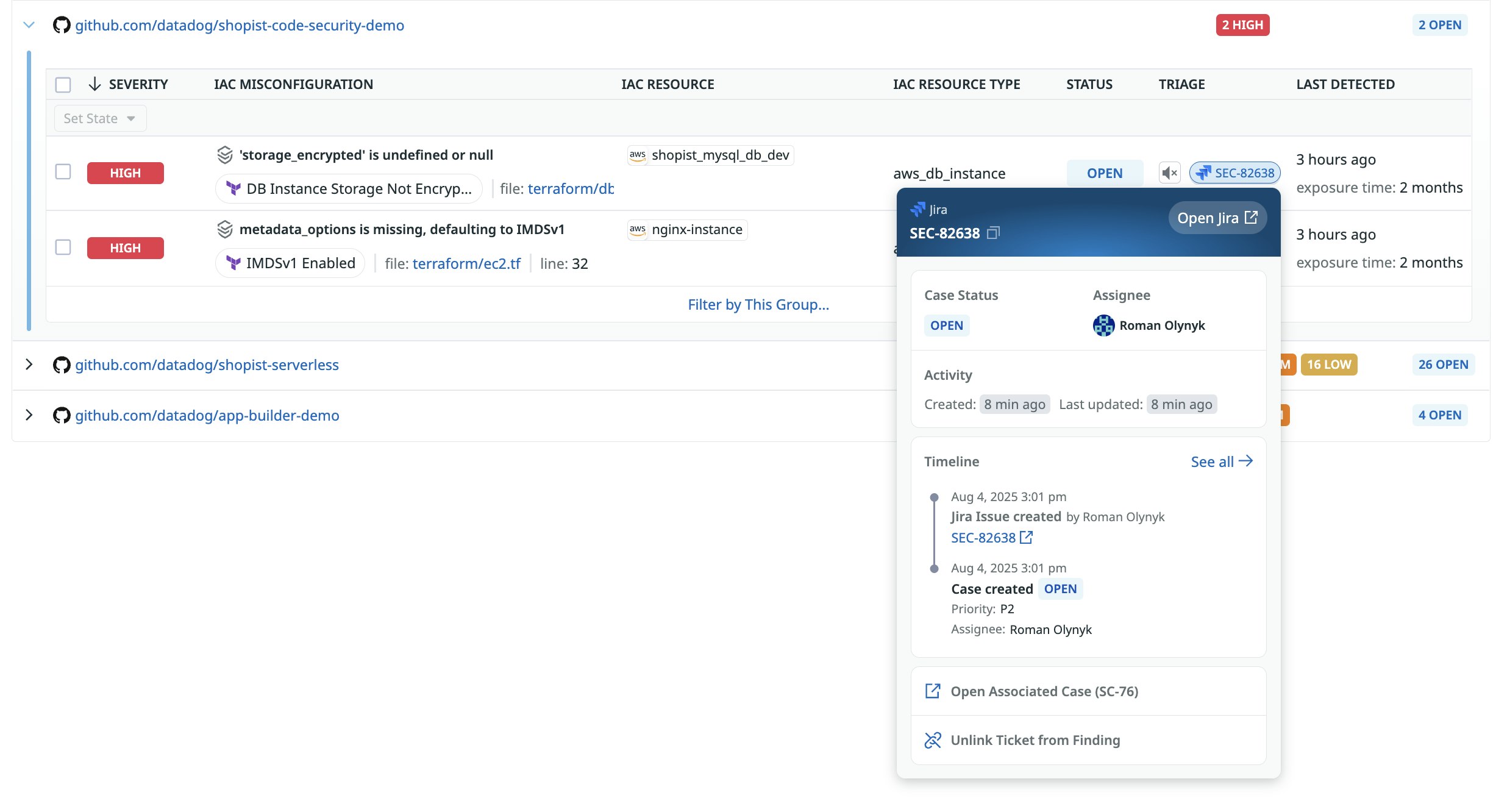
To streamline remediation, IaC Security integrates bidirectionally with Jira. Your teams can create prefilled Jira tickets from Datadog findings in one click, with key context like rule details, severity, and file path. Changes that are made in Jira automatically update the corresponding Datadog finding, and updates in Datadog are reflected in the linked Jira ticket. As a result, both systems remain in sync without manual effort.
IaC Security also supports notification rules, which you can use to automatically forward individual or aggregated findings with the severity and tags of your choosing directly to your teams. You can send these findings to Slack, Microsoft Teams, PagerDuty, ServiceNow, email, and more.
Track IaC security posture over time with Datadog reporting
Beyond detecting misconfigurations, Datadog IaC Security provides a built-in dashboard to help you monitor your organization’s IaC security posture across time, repositories, and teams. You can use familiar Datadog filters (such as repository, team, and environment) to analyze trends, identify recurring issues, and prioritize remediation efforts.
With this visibility, your security and platform teams can track progress, demonstrate compliance, and align security goals with engineering velocity.
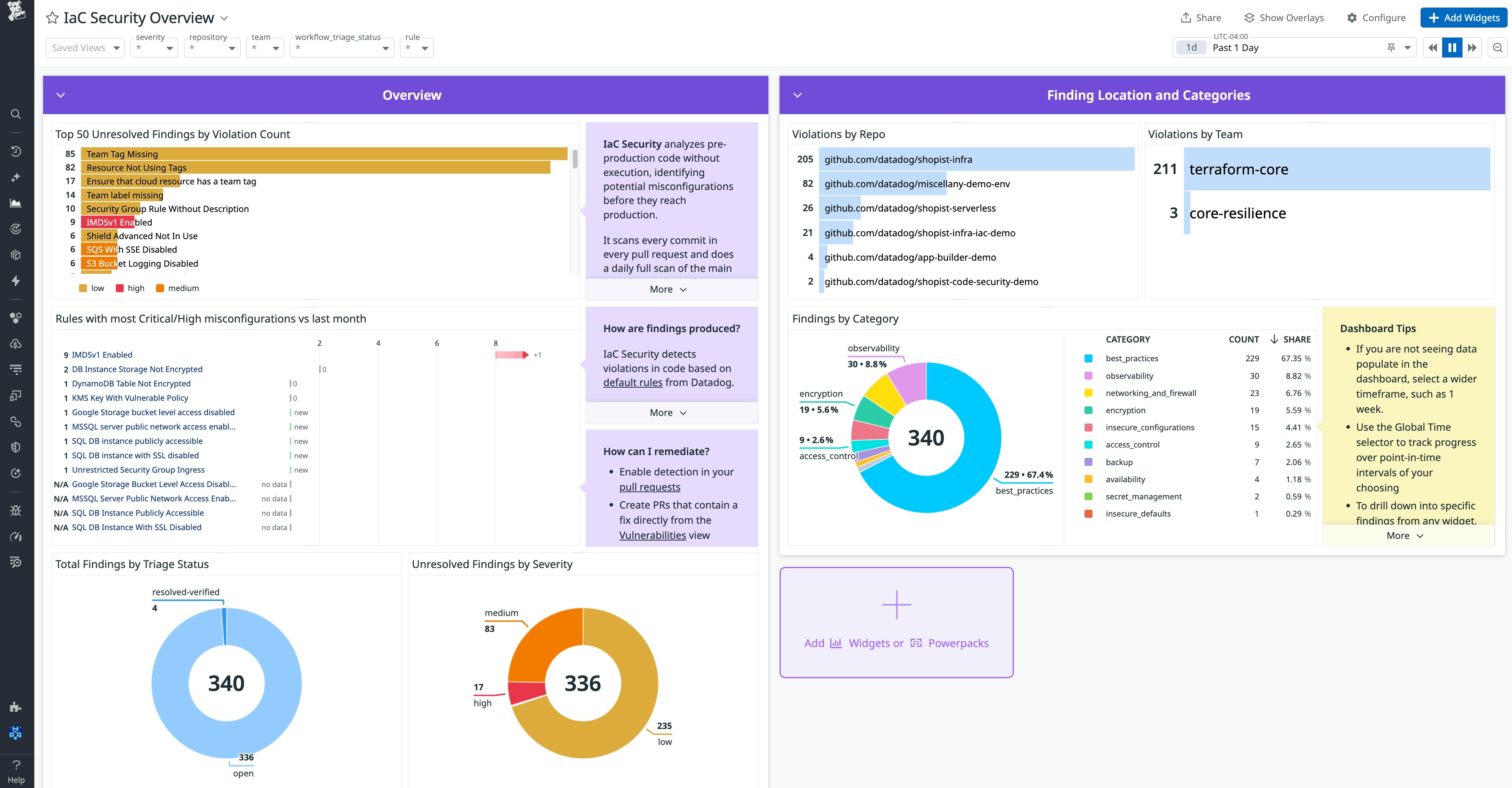
You can also configure the automatic creation of due dates to assign deadlines for remediation of specific findings. Due dates keep your teams informed about the timing of required remediations and help you track compliance with your service level agreements (SLAs).

Shift security left with Datadog IaC Security
Datadog IaC Security helps you reduce risk by detecting misconfigurations early and preventing the deployment of potentially harmful code. By integrating with your Git workflows and the Datadog platform, IaC Security empowers your developers to remediate issues effectively without slowing delivery.
To learn more, check out our IaC Security documentation. If you’re new to Datadog, you can sign up for a 14-day free trial.