Blake Connell

Kassen Qian
For many organizations, merely detecting vulnerabilities isn’t sufficient anymore for securing their codebase. The real challenge is knowing which vulnerabilities matter the most, who owns them, and how to fix them efficiently. Modern application security tools can quickly overwhelm teams with noisy or false-positive findings, resulting in alert fatigue, longer remediation cycles, and eroding developer trust when security teams flag non-issues. At the same time, security is treated as a separate process from day-to-day development. This means that developers—who often bear the ultimate responsibility for remediation—frequently lack the necessary tools and context for mitigating an issue.
Datadog Code Security bridges these gaps by continuously scanning code and libraries across development, CI/CD, and runtime environments. By integrating with Datadog’s end-to-end observability data, Code Security helps you effectively prioritize the most pressing risks and provides actionable fix recommendations. These capabilities enable teams to ship secure code without slowing down delivery.
In this post, we’ll look at how Code Security prioritizes vulnerabilities, continuously detects them from development to production, and accelerates remediation.
Prioritize the risks that matter most
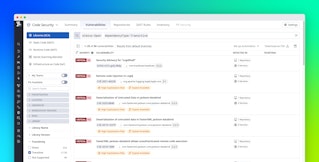
Not every vulnerability is equally important—only a fraction of critical vulnerabilities are worth prioritizing. Code Security prioritizes vulnerabilities by assessing runtime context and service impact, such as which vulnerabilities are actively running in production services, for both first-party code and third-party libraries. You can review findings for your code and libraries on the Summary page and quickly see your security posture, vulnerabilities that need remediation, and top security risks.
For example, you can filter unresolved library vulnerabilities based on a specific level of risk defined by the Datadog Severity Score. You can also see vulnerabilities grouped by application services, affected libraries, and the teams responsible for resolving them. This range of data and display options gives you a multilayered approach to identifying and prioritizing critical vulnerabilities.
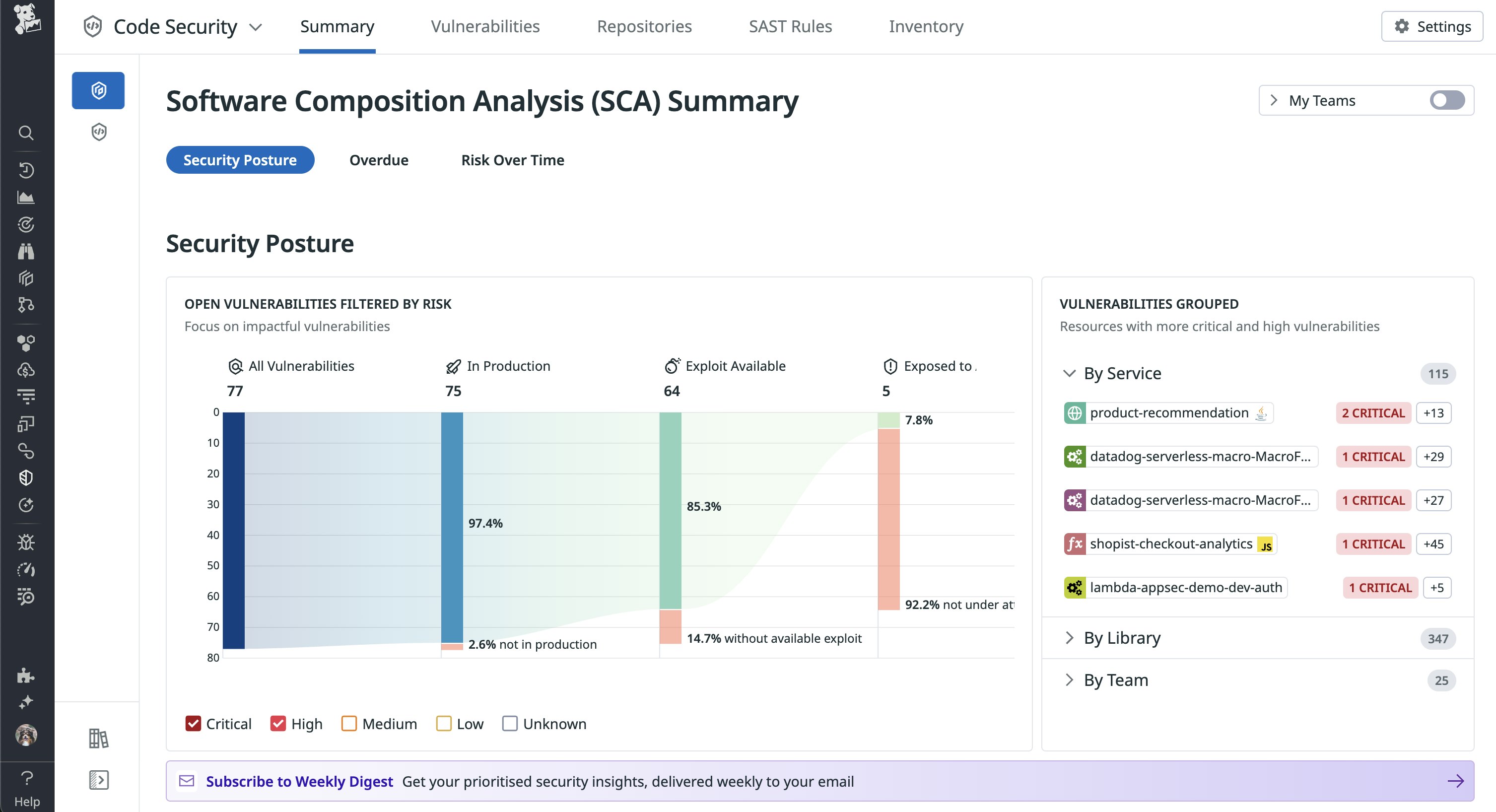
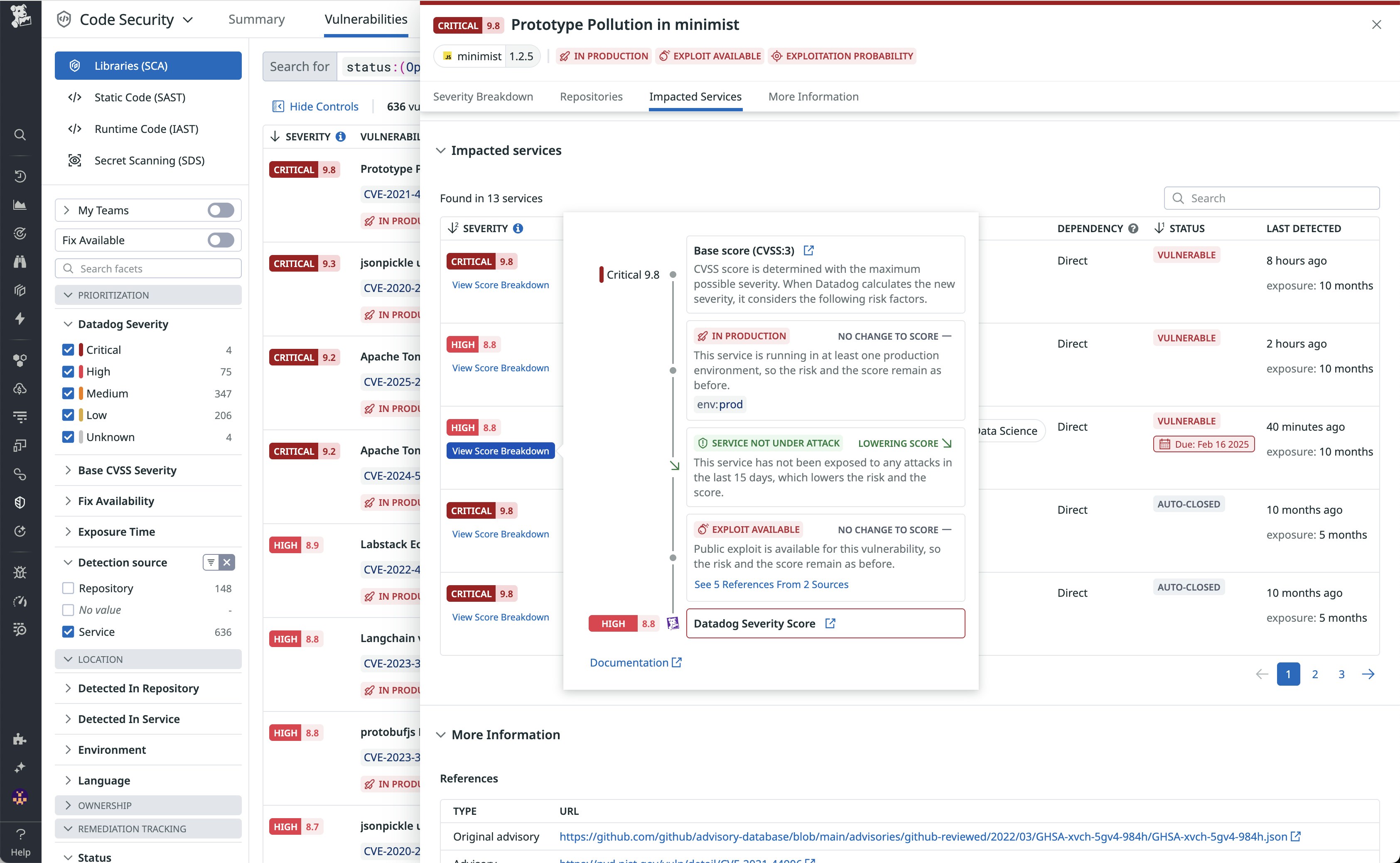
Drilling into a specific library vulnerability, you can see exactly where in your source code a vulnerable dependency is introduced, as well as which services are running it. For each service, Datadog produces a service-specific severity score to help you prioritize remediation.
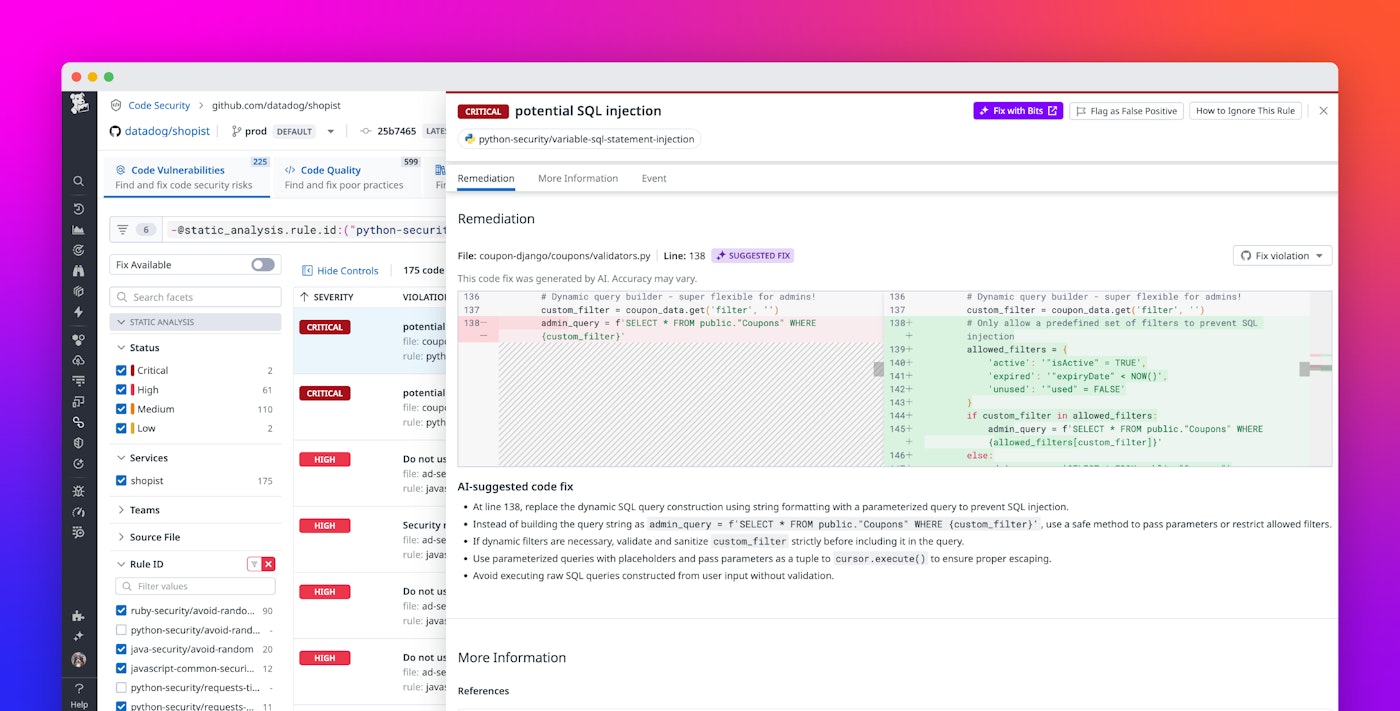
To review all of Code Security’s findings from your production codebase, you can navigate to the Vulnerabilities Explorer. Here, you can select a particular finding and drill down into specific issues, such as a SQL injection vulnerability in production code.
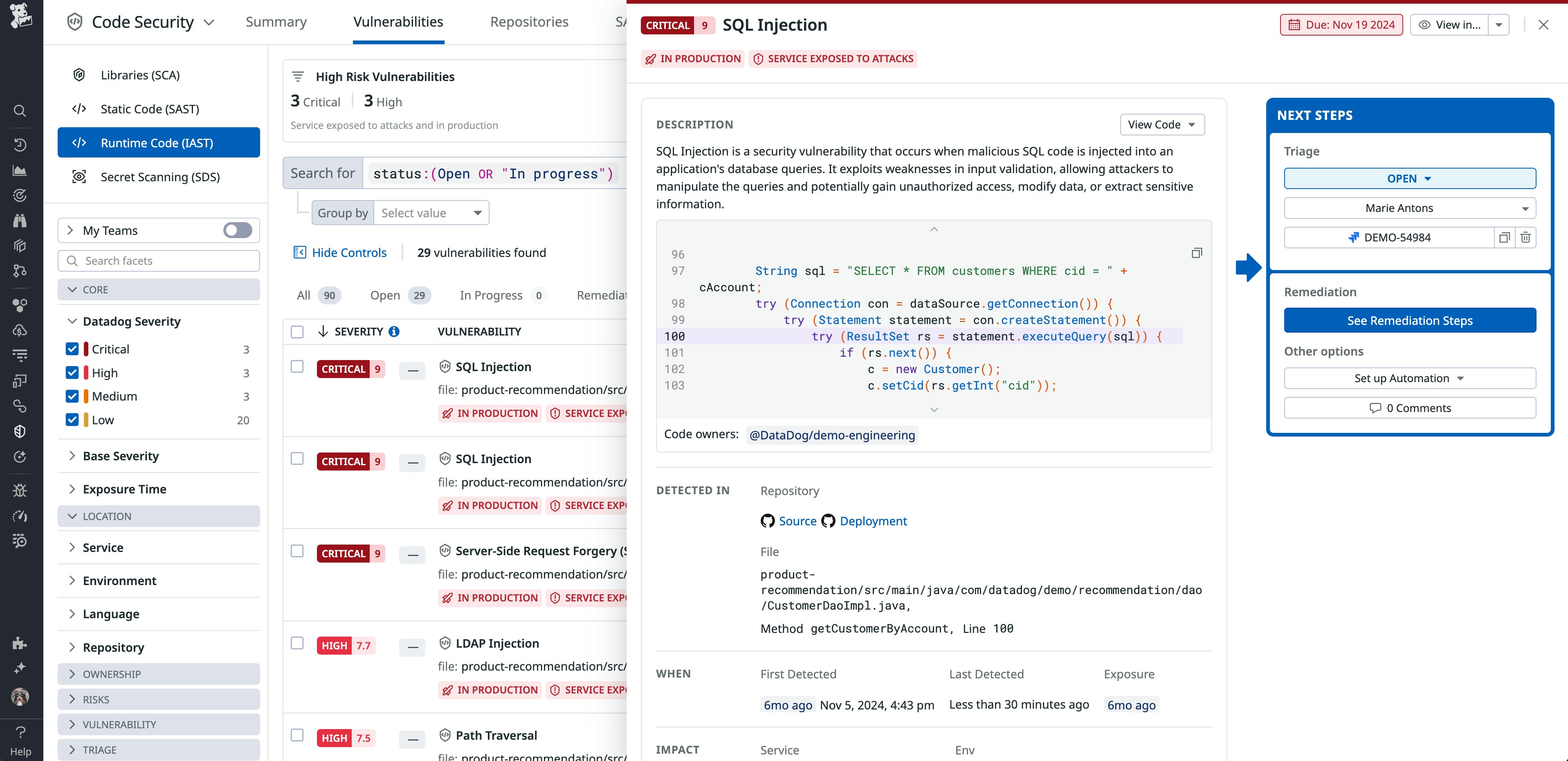
In this detailed view, Datadog also provides clear guidance on where the vulnerability was found in your code and how to fix it. This context enables you to proactively remediate issues and ship fixes faster.
Integrate security into every step of the SDLC
Early detection makes it easier for developers to fix issues quickly and helps reduce overall remediation costs for the organization. Code Security supports developers where they work by continuously scanning code and libraries at each stage of the software development life cycle (SDLC). Whether you’re writing new code, reviewing pull requests (PRs), or monitoring services in production, Code Security helps ensure that critical vulnerabilities don’t slip through the cracks.
Catch issues early in the IDE
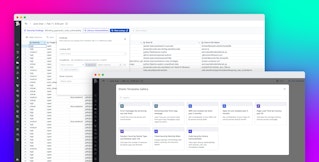
Starting with development, Code Security can flag vulnerabilities directly in your IDE, such as VS Code, and provide actionable context and deterministic, suggested fixes. You can also scan your entire local repository directly within your IDE, with Datadog immediately reporting actionable findings. This enables you to systematically work through each issue before they are even committed to your repositories.
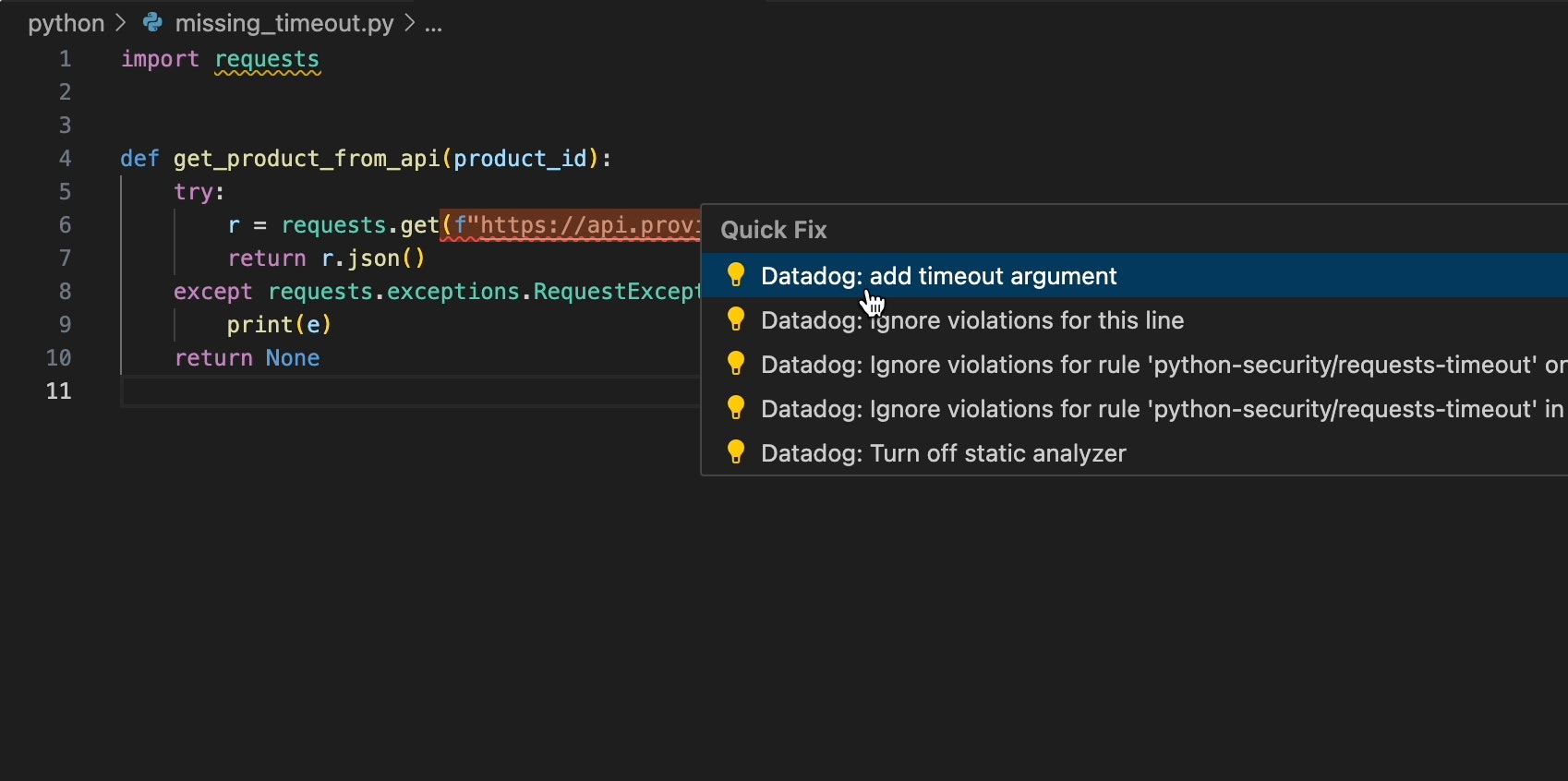
Automate secure code delivery in CI/CD workflows
In addition to the insights you receive in your IDE, you can integrate Code Security with version control systems like GitHub to act as a code reviewer in your PR workflow. When PRs are opened, Code Security leaves inline comments that flag vulnerabilities, providing detailed context and suggested fixes. You can see exactly where the issue occurs and commit the fix directly from the PR without switching tools. These comments mirror the same remediation guidance available in the IDE and in Datadog, providing a consistent experience across the SDLC.
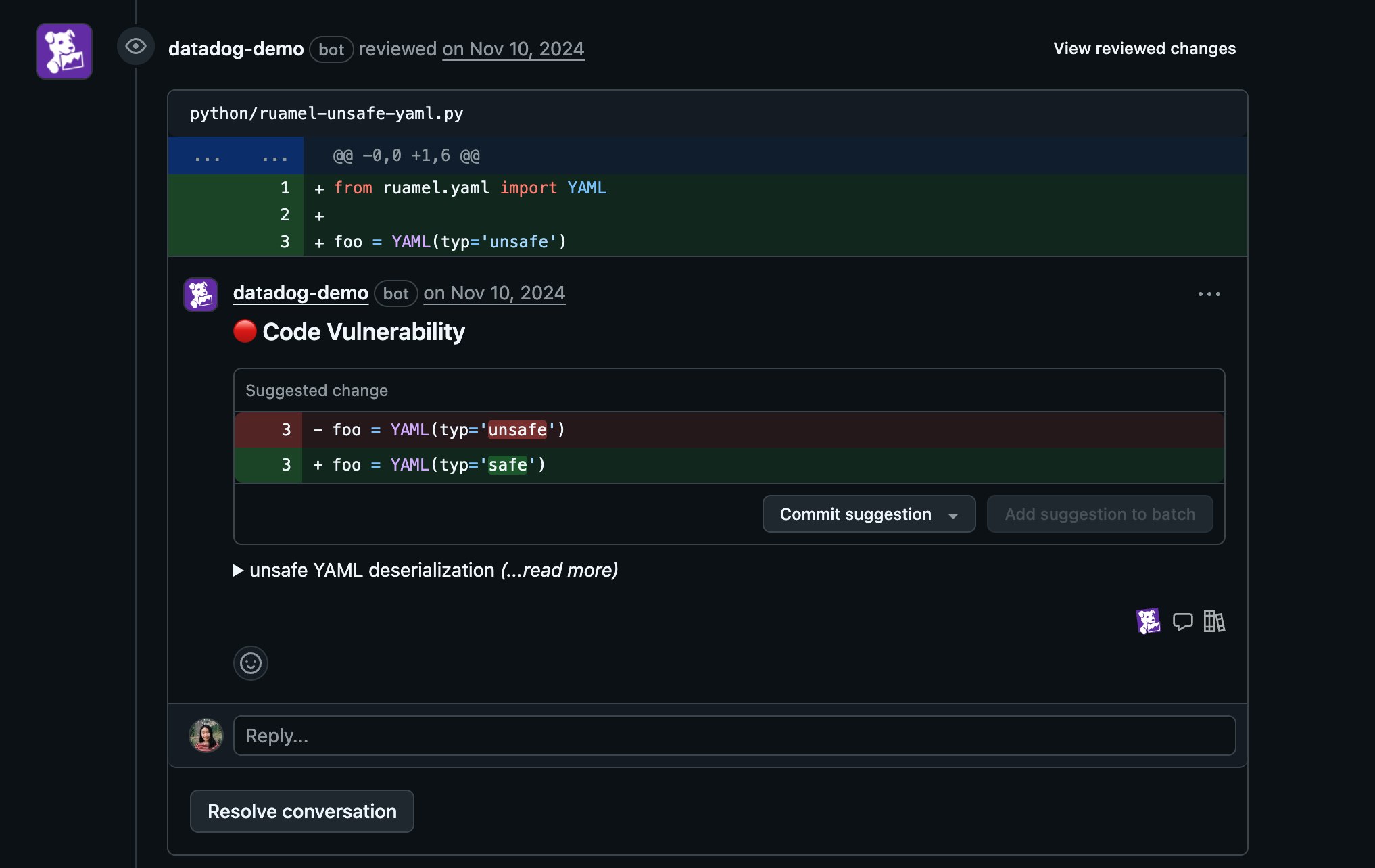
To further enforce security standards, Code Security also supports Quality Gates for your CI/CD pipeline. Gates enable you to automatically block merges to your default branches based on whether new code or library vulnerabilities are introduced in the pull request.
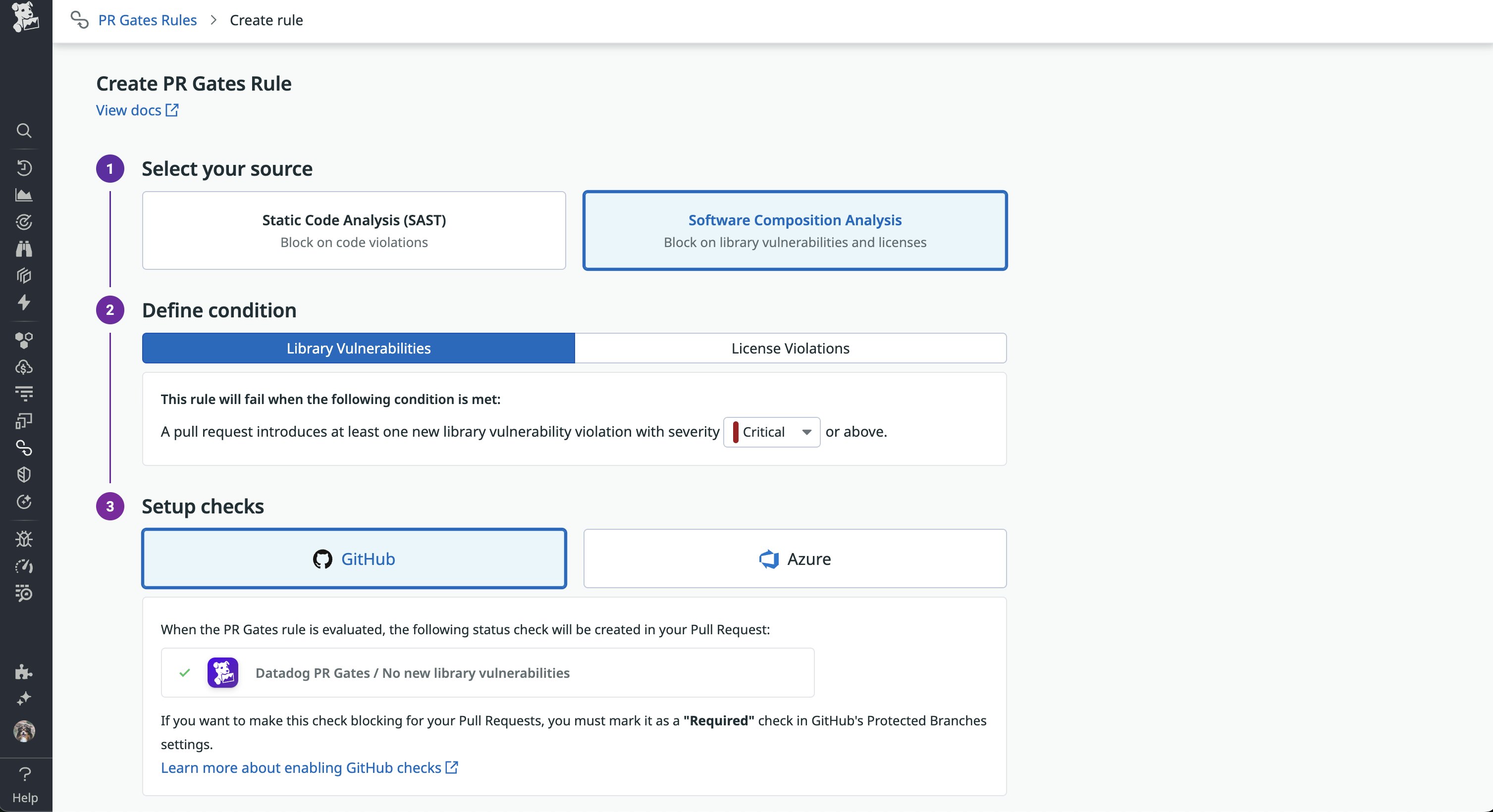
Get real-time, continuous visibility into active vulnerabilities in production
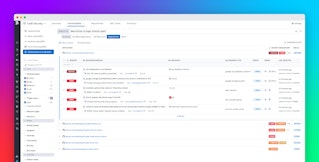
Extending beyond development and deployment, Datadog Code Security continuously monitors application security in production, providing real-time visibility into active vulnerabilities affecting specific services. Your Security and Operations teams gain a unified view of application health and risk in a single platform—no need to wait for scheduled scans. This allows teams to identify and respond to active threats faster and prioritize the issues that are actually exploitable and impactful in production.
Proactively accelerate remediation
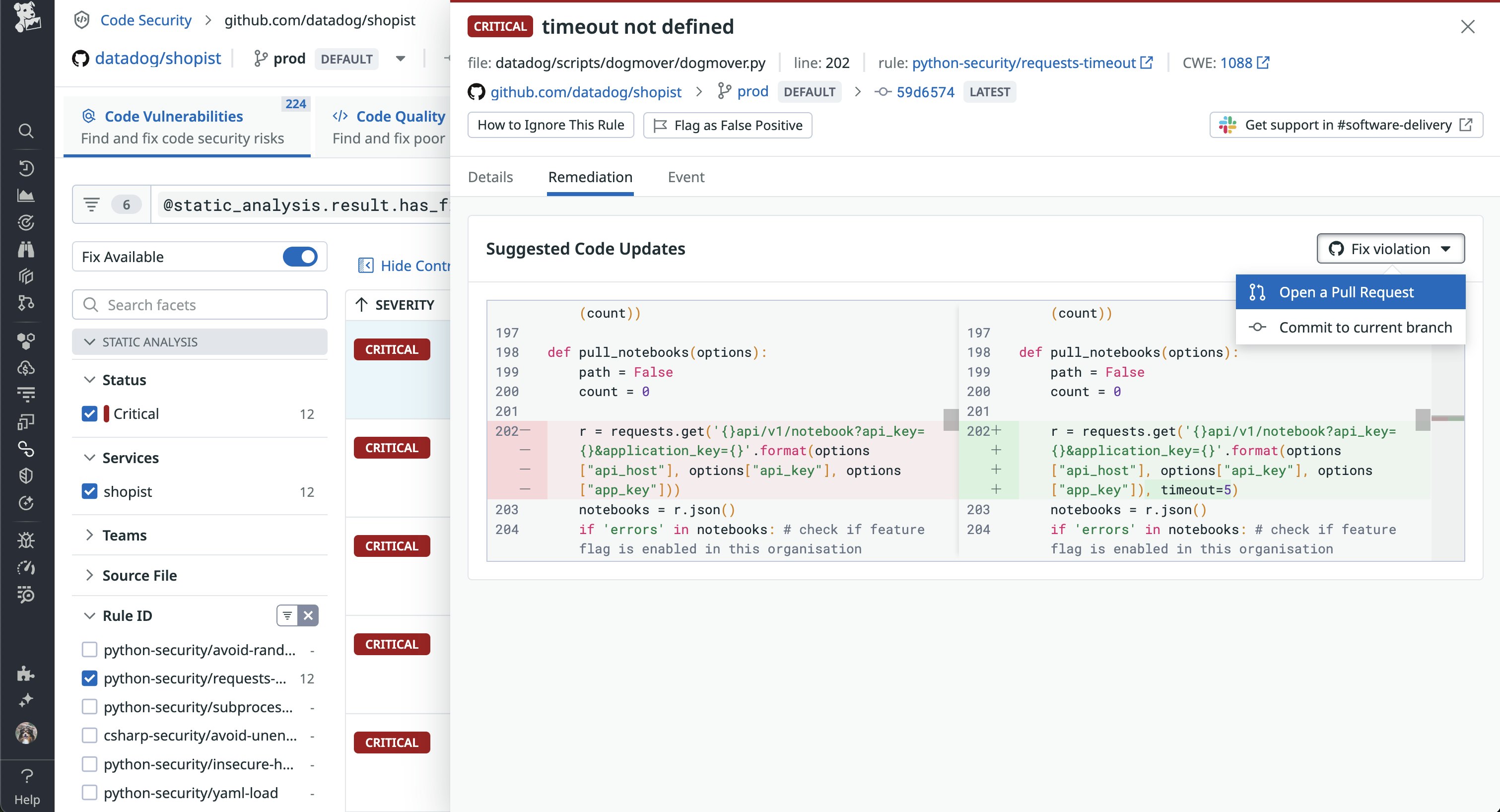
Remediating vulnerabilities quickly is critical but often delayed by manual handoffs and unclear ownership. Datadog Code Security eliminates these bottlenecks by automatically associating vulnerable services with their code owners, repositories, and responsible teams within Datadog. Flagged vulnerabilities also include auto-generated code fixes, which can be either deterministic or powered by Bits AI. With this context, you can notify the right teams, who can then quickly apply and push critical fixes using Code Security’s one-click PR creation.
And for a high-level view of the vulnerabilities that your team is working on, Datadog’s custom dashboards let you easily share real-time vulnerability insights with stakeholders or generate regular security posture reports.
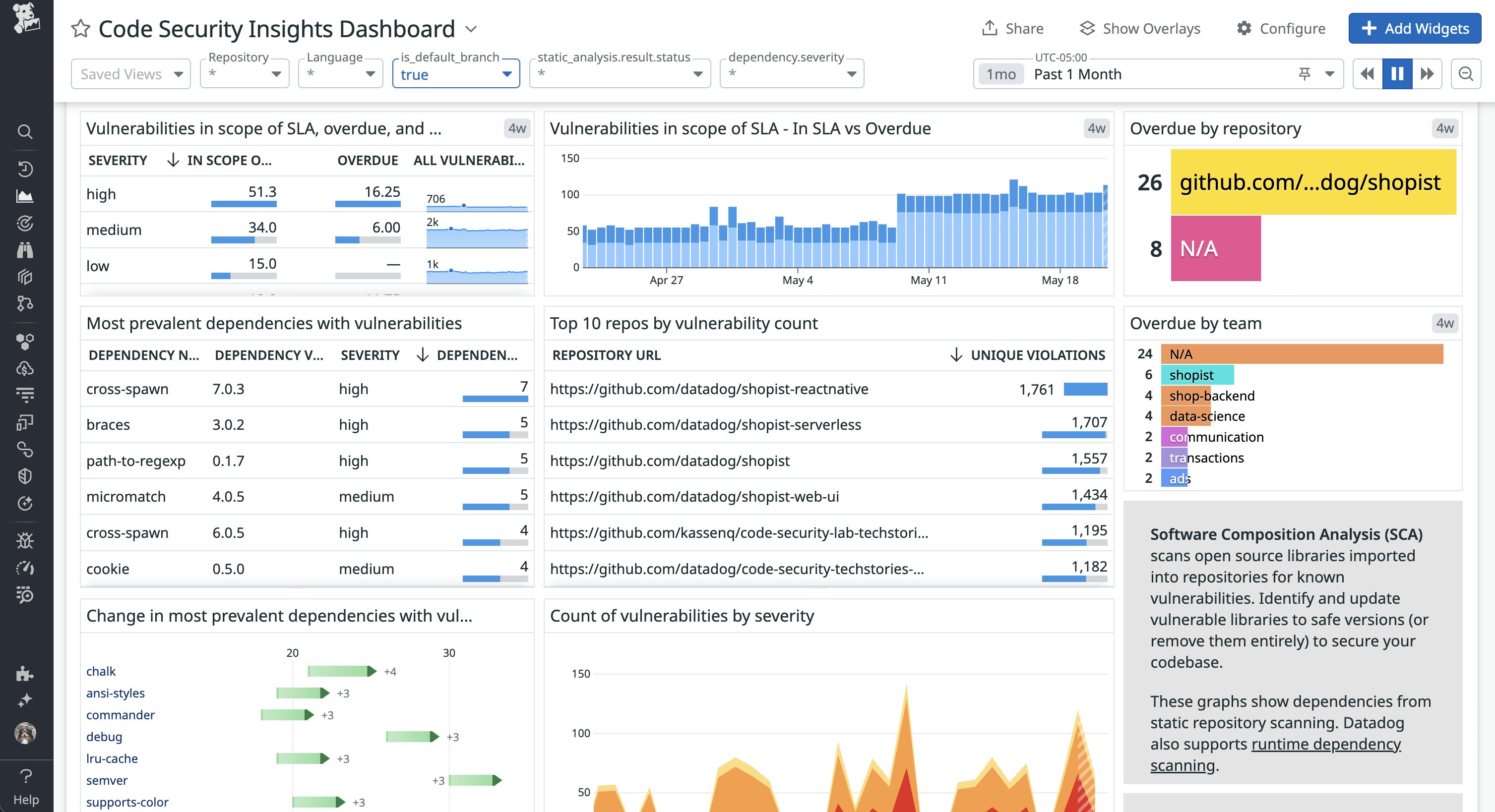
Together, these capabilities allow you to improve collaboration, unify incident management, and efficiently resolve urgent security risks before they significantly affect your applications and customers.
Secure your source code with Datadog
By integrating vulnerability detection with remediation from development to production, Datadog Code Security uniquely enables teams to deliver secure applications at scale. Check out our documentation to learn more about Code Security. If you don’t already have a Datadog account, you can sign up for a free 14-day trial.