Pronoy Chaudhuri
Organizations are scaling their environments at a rapid pace, deploying thousands of cloud resources, services, and accounts. Because of their size and complexity, these environments are more susceptible to compliance issues—a misconfiguration in a single cloud resource can lead to costly data breaches. For that reason, organizations are prioritizing governance, risk, and compliance (GRC) management to ensure that their environments are configured appropriately.
Datadog Cloud Security Misconfigurations supports your GRC goals by providing a single place where you can track your compliance posture, surface misconfigurations that leave your organization vulnerable to attacks, and automate evidence collection for audits. We’re excited to announce that, in addition to our existing AWS and Azure support, we’ve expanded our posture management offering within Datadog Cloud Security to Google Cloud. Now, you can leverage Datadog to do the following:
- Get a high-level overview of your Google Cloud security posture with tailored reports
- Detect drift from compliance controls for Google Cloud resources
- Correlate findings and other cloud security issues with Datadog Cloud Security
Regardless of your cloud provider, Datadog Cloud Security offers a complete picture of the state of your resources. And with support for industry-standard frameworks like PCI DSS, SOC 2, GDPR, and HIPAA, you can easily verify that your cloud environments follow best practices promoted by the latest compliance and security standards.
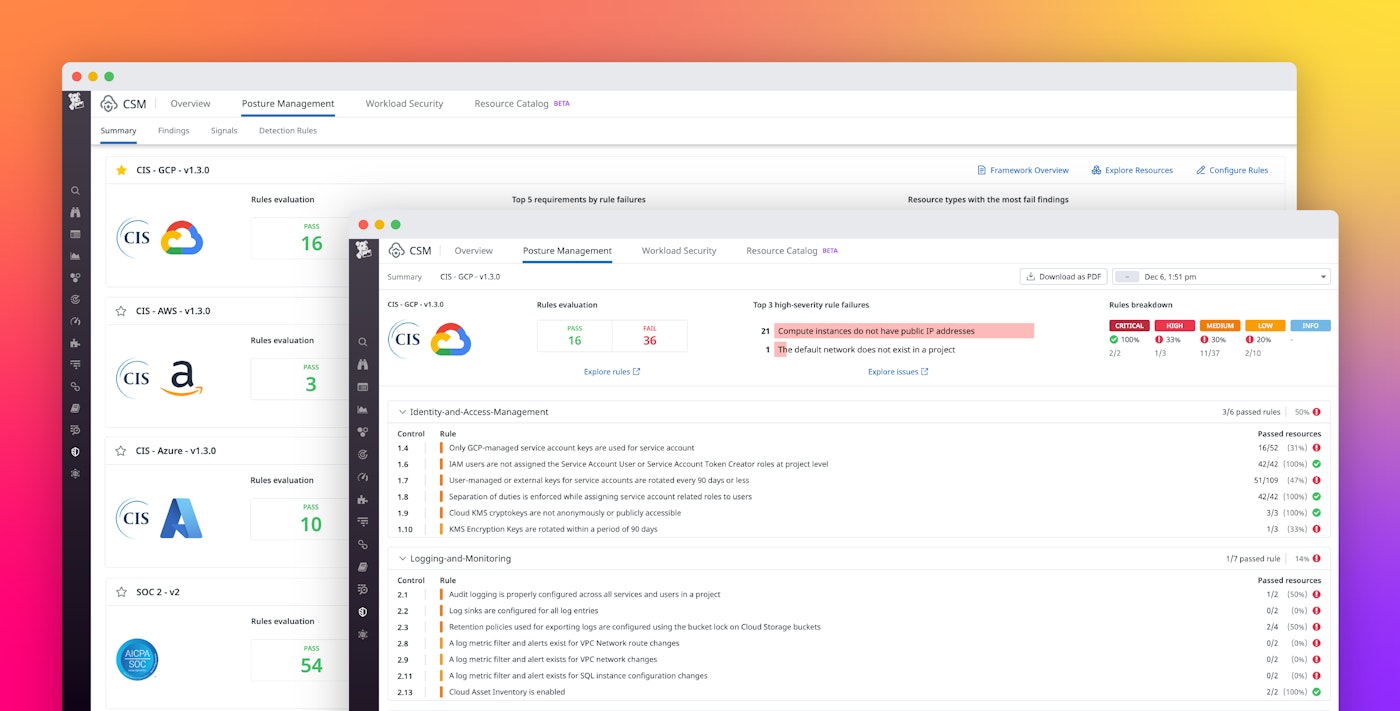
Review the security posture of Google Cloud resources with curated reports
Datadog’s expert-built reports offer a snapshot of all of your cloud environments, including Google Cloud. These reports are available within minutes of integrating your Google Cloud account with Datadog. For example, the following CIS for GCP report gives you insight into which CIS controls are failing in your environment, along with more details about the misconfigured resources:
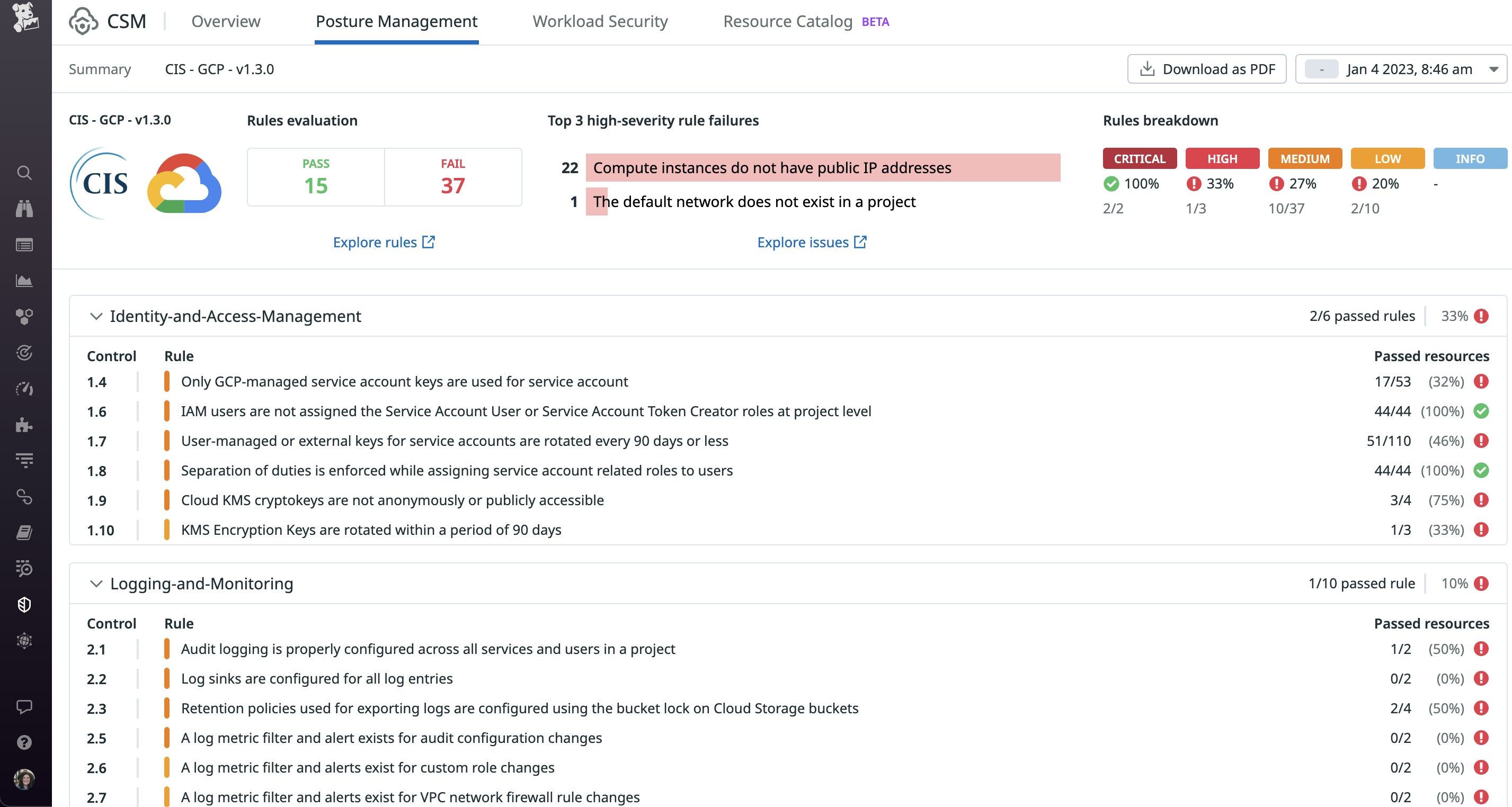
At the top of the report, you can see a summary of which of these violations require your immediate attention. This data helps you save time on searching for resources that are not compliant, such as those that grant anonymous or public access. Restricting access to these resources can protect them—and their data—from the risk of exposure.
Detect drift from compliance controls for Google Cloud resources
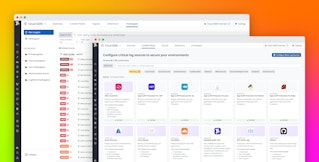
Datadog Cloud Security runs more than 400 security and compliance rules against your Google Cloud and multi-cloud resources, which enables you to accelerate detection when an asset’s configuration deviates from standard compliance controls. For example, you can use Datadog Cloud Security to spot the following issues:
- Google Cloud storage buckets without uniform bucket-level access enabled
- SQL Database instances that do not use SSL for all incoming connections
- Unencrypted BigQuery tables
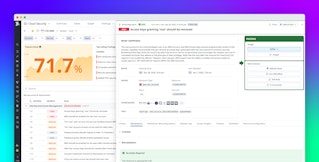
When Datadog identifies a resource that does not comply with a compliance control, it will generate a finding with more information about the associated control, all affected resources, and detailed remediation steps to resolve the issue. Cloud Security findings also incorporate the infrastructure data that you already collect from Google Cloud via Datadog’s integration, enabling you to contextualize a finding in terms of the affected projects, services, and resource groups. You can review a finding by searching for specific Google Cloud resources and compliance controls in the Findings Explorer or by clicking on a relevant compliance control in any dedicated report.
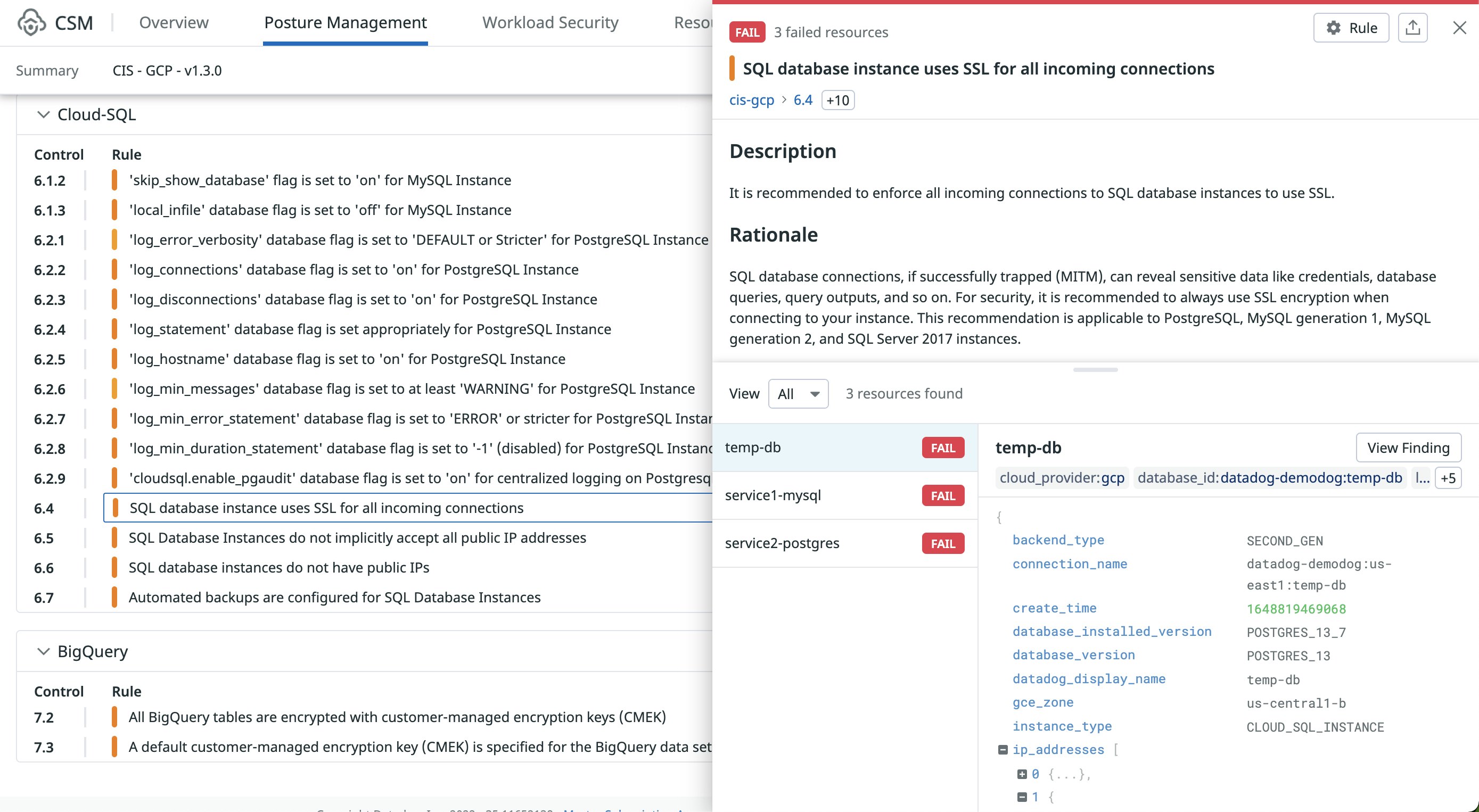
In the preceding example, Datadog Cloud Security identified three Google SQL database instances that do not use SSL for all incoming connections, which can result in an attacker accessing and exposing sensitive data. You can mitigate this issue by updating connection policies to only allow SSL connections.
Correlate findings and other cloud security issues with Datadog Cloud Security
Datadog Cloud Security allows your Security and DevOps teams to act on the shared context of observability data and security risks to determine the impact of a threat quickly. You can review misconfigurations alongside potential threats to understand the full security landscape of your cloud infrastructure—all in a single view. This enables you to efficiently surface and triage the most critical threats to your Google Cloud infrastructure.
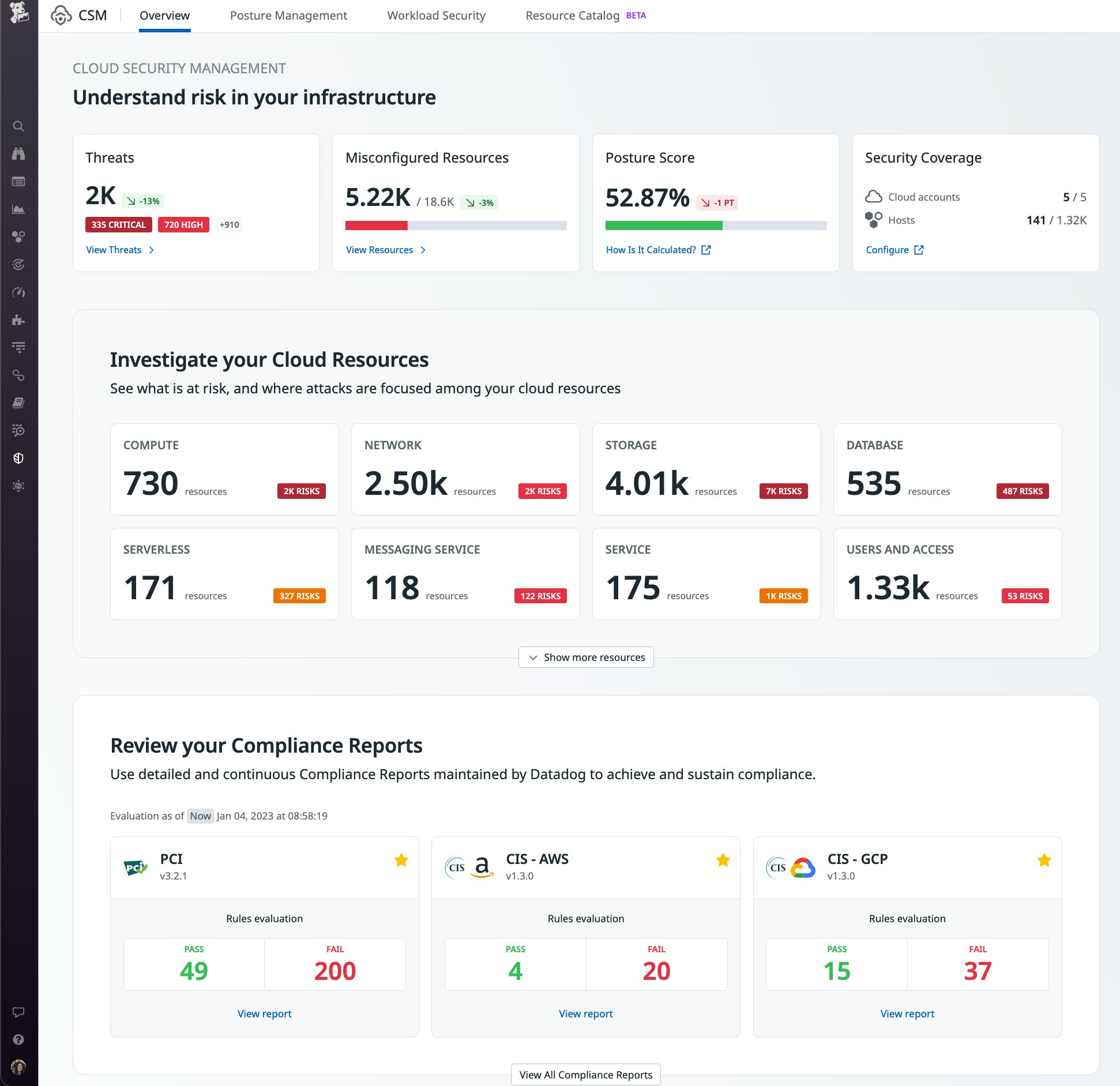
Remediate misconfigurations in your Google Cloud environment
Datadog Cloud Security provides critical insight into the security posture of your Google Cloud environment while leveraging our existing Google Cloud integration to place that data in context with your resources. Cloud Security also provides your Security and DevOps teams with shared context for quickly identifying the impact of threats on your cloud resources. Check out our documentation to learn more, or self-enroll to get started—curated reports are available within minutes of enrolling. If you don’t already have a Datadog account, you can sign up for a free 14-day trial today.