Colten Woo

Jace Harker
As cloud infrastructure becomes more dynamic and distributed, DevOps and security teams need to quickly detect risks and understand their context: where those risks live, how critical they are, and how to respond effectively. By surfacing misconfigurations, vulnerabilities, sensitive data risks, and identity threats directly on a real-time diagram of your infrastructure, Cloudcraft helps teams identify, prioritize, and remediate security issues at scale. This visual context allows teams to reduce risk across cloud environments, using a shared and trusted view of your architecture.
In this post, we’ll show you how you can use Cloudcraft to:
- Identify misconfigured cloud resources
- Uncover the most impactful vulnerabilities in your environment
- Visualize identity risks and secure your infrastructure from IAM-based attacks
- Spot and secure sensitive data stored in cloud resources
Identify misconfigured cloud resources
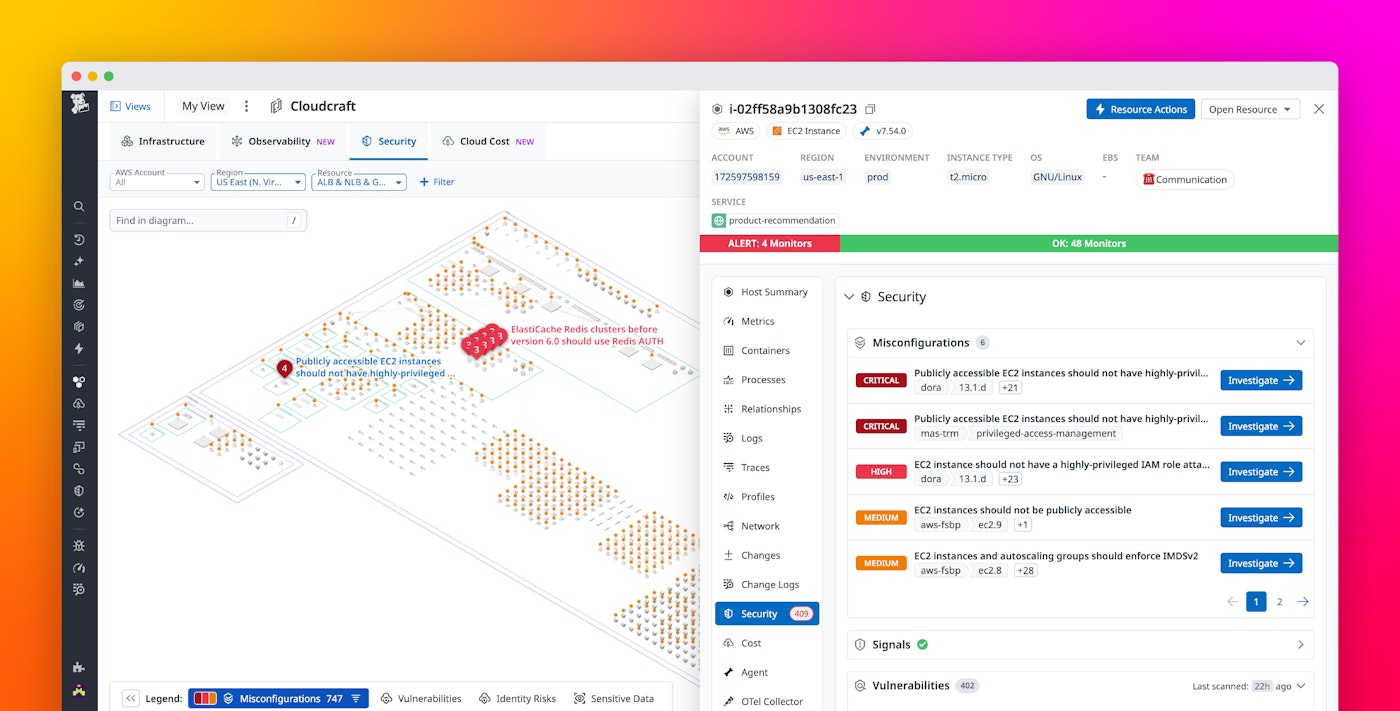
Misconfigurations in cloud resources can leave your organization vulnerable to attacks and lead to costly data breaches. To surface these misconfigurations, Datadog Cloud Security runs continuous configuration checks on your cloud resources using more than 1,000 out-of-the-box detection rules mapped to compliance standards and industry benchmarks. Using Cloudcraft, you can view all misconfigurations across your infrastructure on a diagram and dig deeper into each finding to investigate the issue.
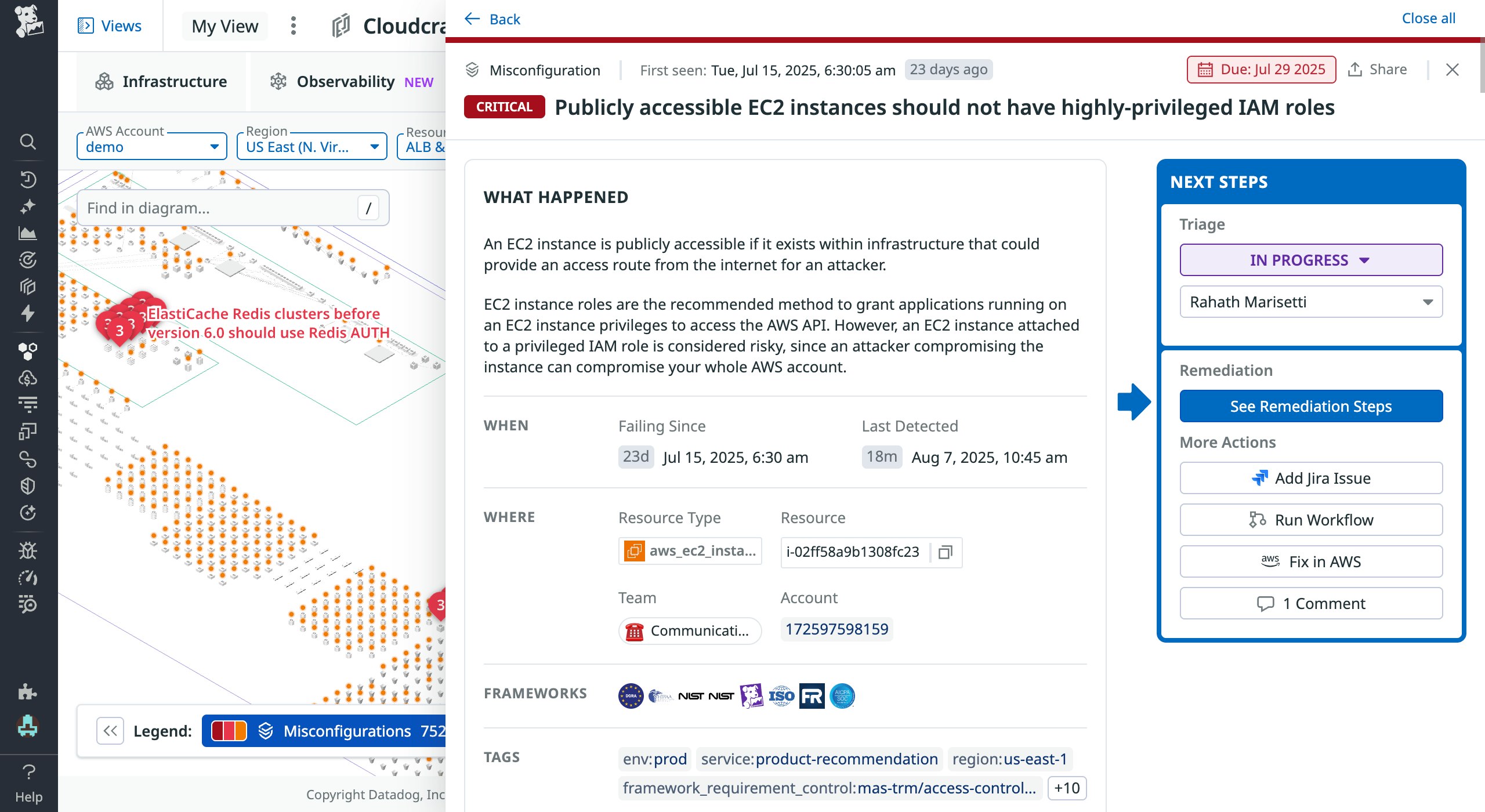
Cloudcraft color-codes misconfigurations by their severity score and shows you relationships between resources, helping you prioritize which issues to focus on. In the example above, Cloudcraft has surfaced a critical misconfiguration: a publicly accessible EC2 instance has highly privileged IAM roles. After clicking into this finding, you can see other misconfigurations affecting the impacted resource before investigating further. For each misconfiguration, Datadog provides a detailed description of what happened, suggested remediation steps, and quick actions so you can open a Jira ticket, run a workflow, or otherwise act to remediate the issue.
Uncover the most impactful vulnerabilities in your environment
With ephemeral resources running on different packages and versions, tracking existing and new vulnerabilities can be challenging. To identify and remediate these issues, Cloud Security continuously scans your containers, hosts, and serverless functions for known vulnerabilities, from your pipelines to your production environment. The ability to see these findings in Cloudcraft enables you to quickly assess the number of vulnerabilities in your environment and their severity, so you can begin triaging them.
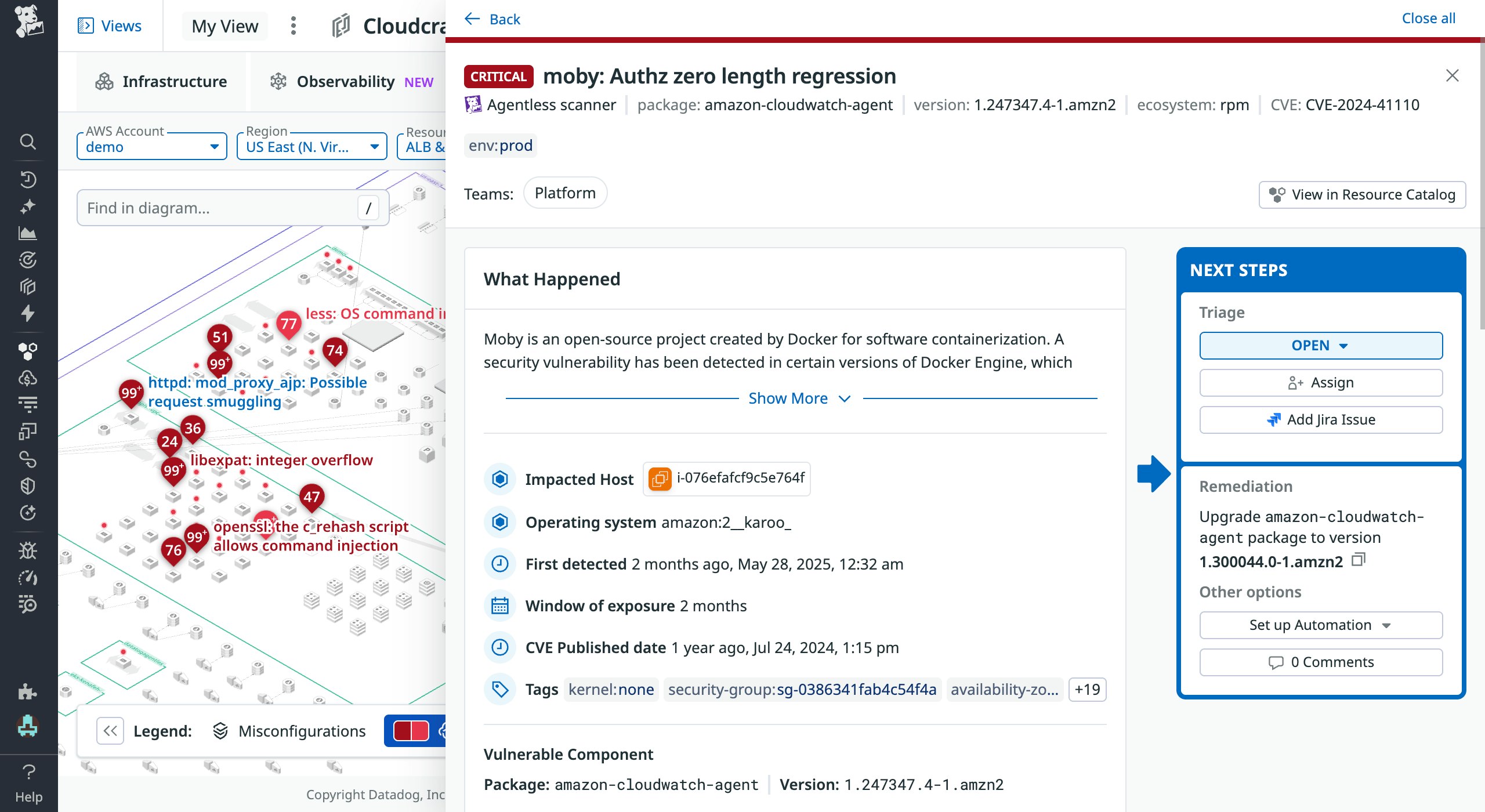
In the screenshot above, Cloudcraft has surfaced a vulnerability that carries a critical severity score, has an available exploit, and impacts a resource running in production. These three factors indicate that this is a high-priority vulnerability that should be addressed immediately. Once you click into the finding, you can see details about the vulnerable component, a description of the issue, and recommended remediation steps, along with actions you can take to begin triage.
Visualize identity risks and secure your infrastructure from IAM-based attacks
Mismanagement of identity and access management (IAM) systems is one of the leading causes of security breaches and insider threats. To mitigate entitlement and identity risks, Datadog Cloud Security Identity Risks scans your cloud environment for known IAM issues such as lingering administrative privileges, privilege escalations, permission gaps, and cross-account access. Cloudcraft enables you to visualize these findings in your infrastructure diagrams, so you can see which resources are impacted and which others are connected or downstream, helping you better assess identity risks, access paths, and blast radius.
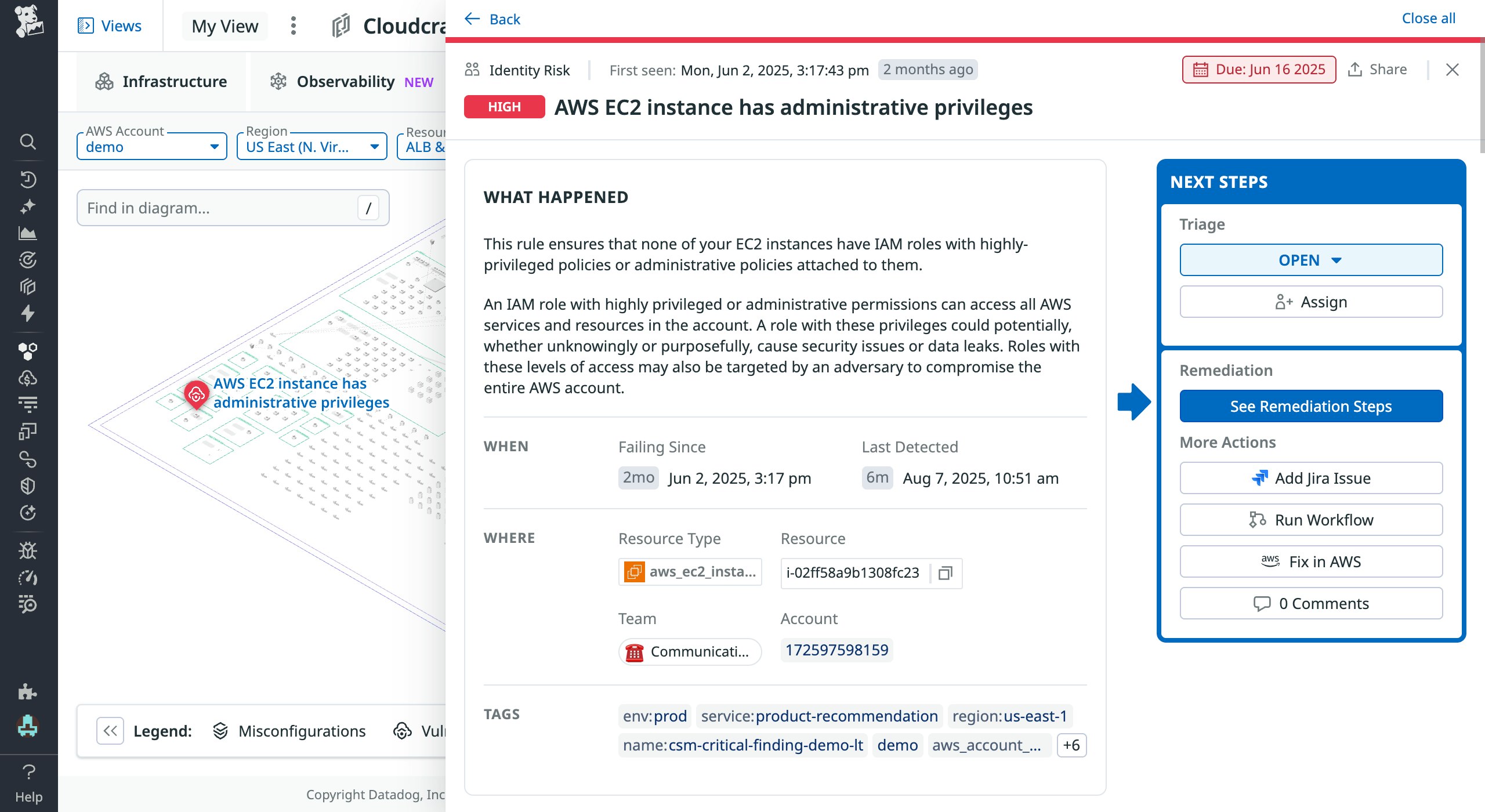
In the screenshot above, Cloudcraft shows us that an AWS EC2 instance has administrative privileges, which could cause security issues or data leaks. The detailed side panel for this finding displays a summary of what happened, what entities the resource can access, who can access the resource, and other key information. For quick remediation, you can run a workflow in Workflow Automation, view suggested downsized policies before making the change in your cloud console, or create a Jira issue.
Spot and secure sensitive data stored in cloud resources
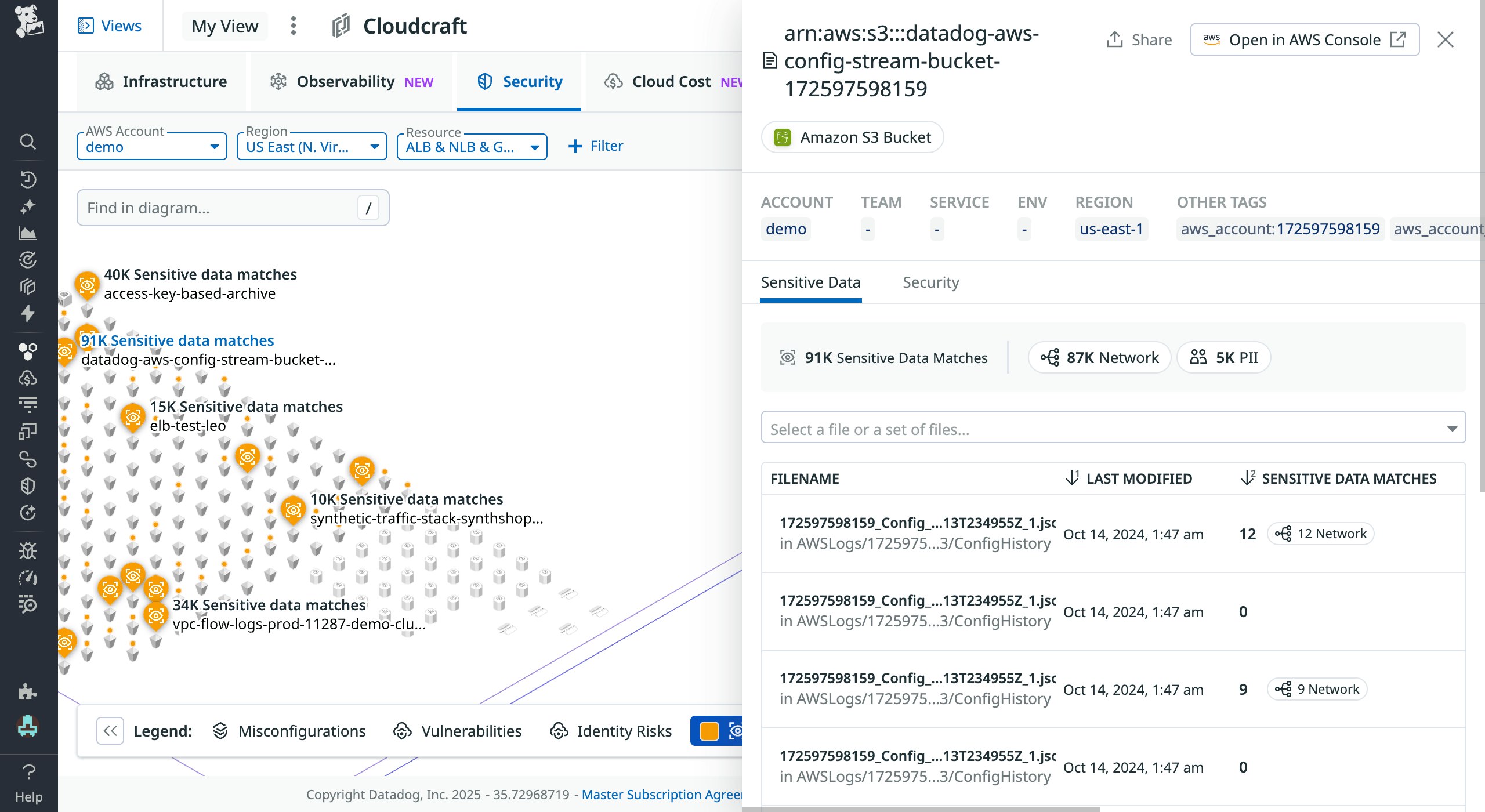
Securing sensitive data is critical for avoiding costly data breaches and meeting compliance standards. To catalog where this data is stored, Sensitive Data Scanner (SDS) scans text files (such as CSVs and JSONs) and tables in Amazon S3 buckets, using its rule library to determine if sensitive data is stored there. If SDS finds matches in any of your resources, Cloudcraft will mark them with an orange dot and label them with the number of matches found, so you can quickly focus on the most problematic resources that need your attention.
To continue your investigation, you can click a resource to open a side panel that shows you the number of matches, the types of sensitive data found, and the location of the first match.
Assess and strengthen your security posture using Cloudcraft
Cloudcraft brings together multiple security issues, so you can fully analyze possible risks and attack paths. By bringing security insights into architecture diagrams, Cloudcraft transforms how DevOps and security teams understand and manage cloud risk. To learn more about how to get started using the Security Overlay in Cloudcraft, see our documentation. And if you’re not yet a Datadog customer, sign up for a 14-day free trial to get started.