Amanda Quach
Cloud infrastructures can comprise thousands of interconnected and dynamic resources. This complexity introduces unique challenges to monitoring and securing these architectures. Understanding where user activity originates—and what actions constitute security threats—is a complex task when you’re dealing with the huge volume of logs, metrics, and other telemetry that highly distributed cloud environments generate each day.
We’re excited to announce Datadog Cloud SIEM Investigator for Azure, which provides crucial visibility into Microsoft Azure environments for security teams and DevOps. This release complements the existing availability of Cloud SIEM Investigator for AWS and GCP. Datadog Cloud SIEM investigator uses Azure audit logs to help teams visualize activity across resources, including Azure Storage and Azure Virtual Machines (VMs), and associate this activity with Azure entities such as service principals and end users—making it easy to quickly understand who is doing what in your environment.
In this post, we’ll provide an overview of how the Cloud SIEM Investigator enables you to:
- Visualize Azure activity and drill down into specific entities
- Improve cross-team collaboration on investigations into cloud resources
Visualize Azure activity and drill down into specific entities
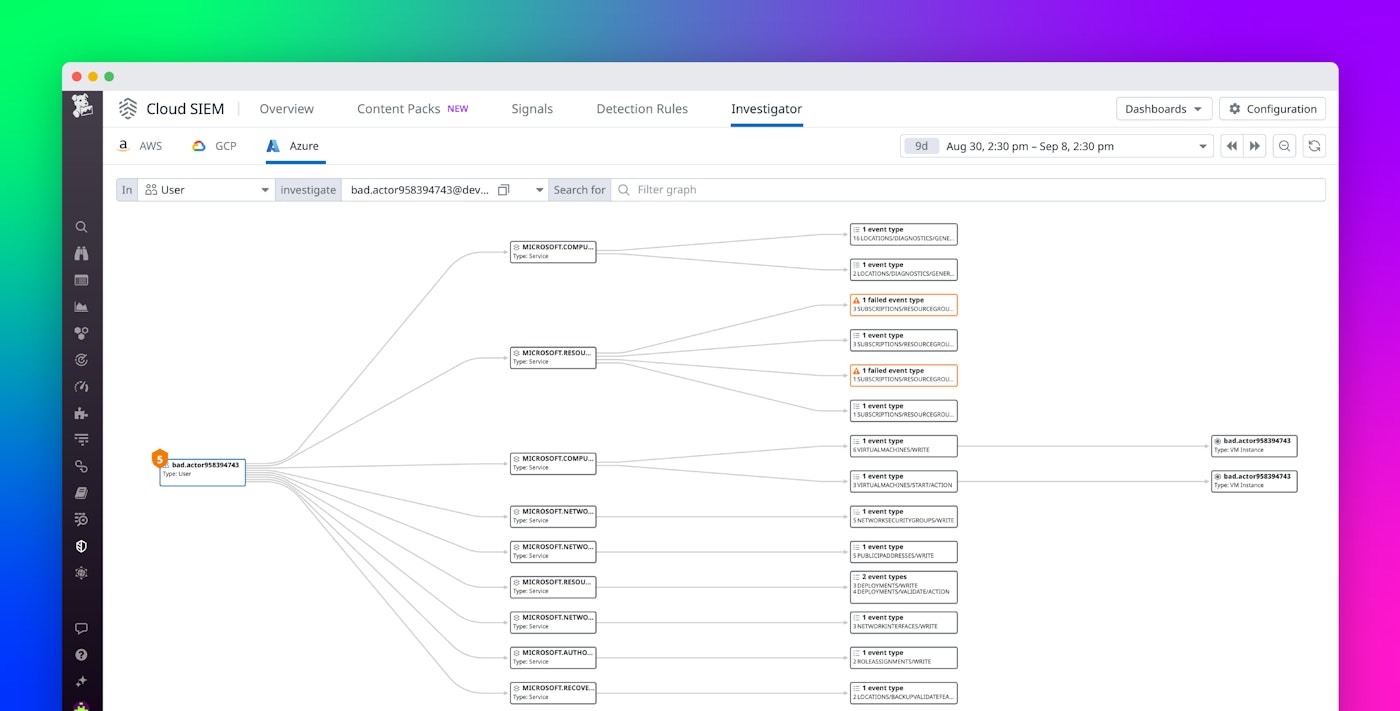
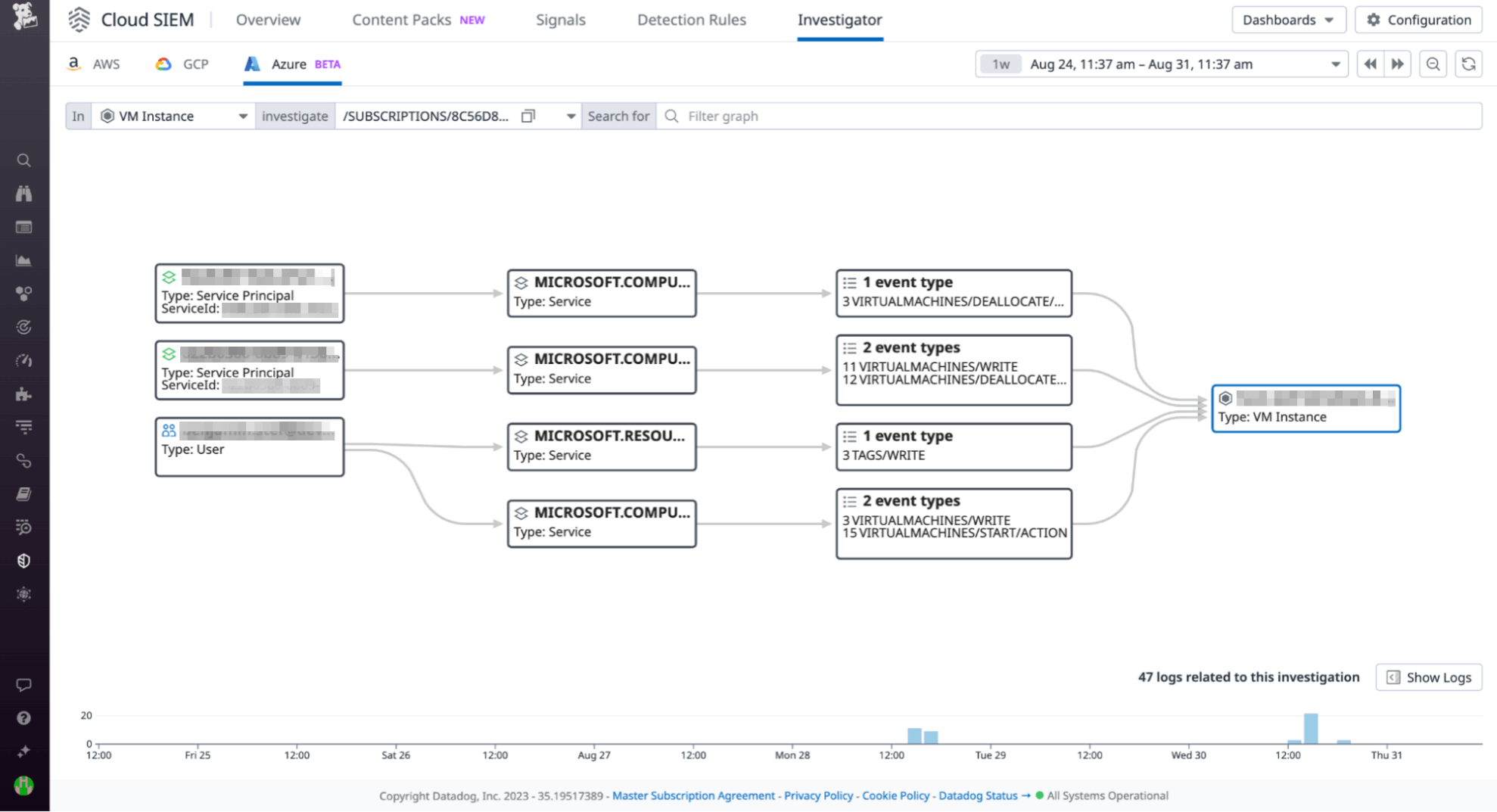
Datadog Cloud SIEM Investigator uses the information contained in your Azure audit logs to build a graphical representation of user and entity behavior. This visualization helps teams investigate potential security incidents by answering key questions about their Azure logs, such as:
- Which users and service principals have interacted with what resources
- What actions have been taken by end users and service principals within a specified time frame and whether errors have occurred along the way
- What specific operations were performed on a resource
For example, security teams and DevOps can explore all actions taken by a specified service principal to determine if they’re interacting with business-critical resources, such as Azure Storage accounts or Azure VMs. The following screenshot shows a Cloud SIEM Investigator breakdown of an instance in which a service principal fails to perform an operation on an Azure storage account.
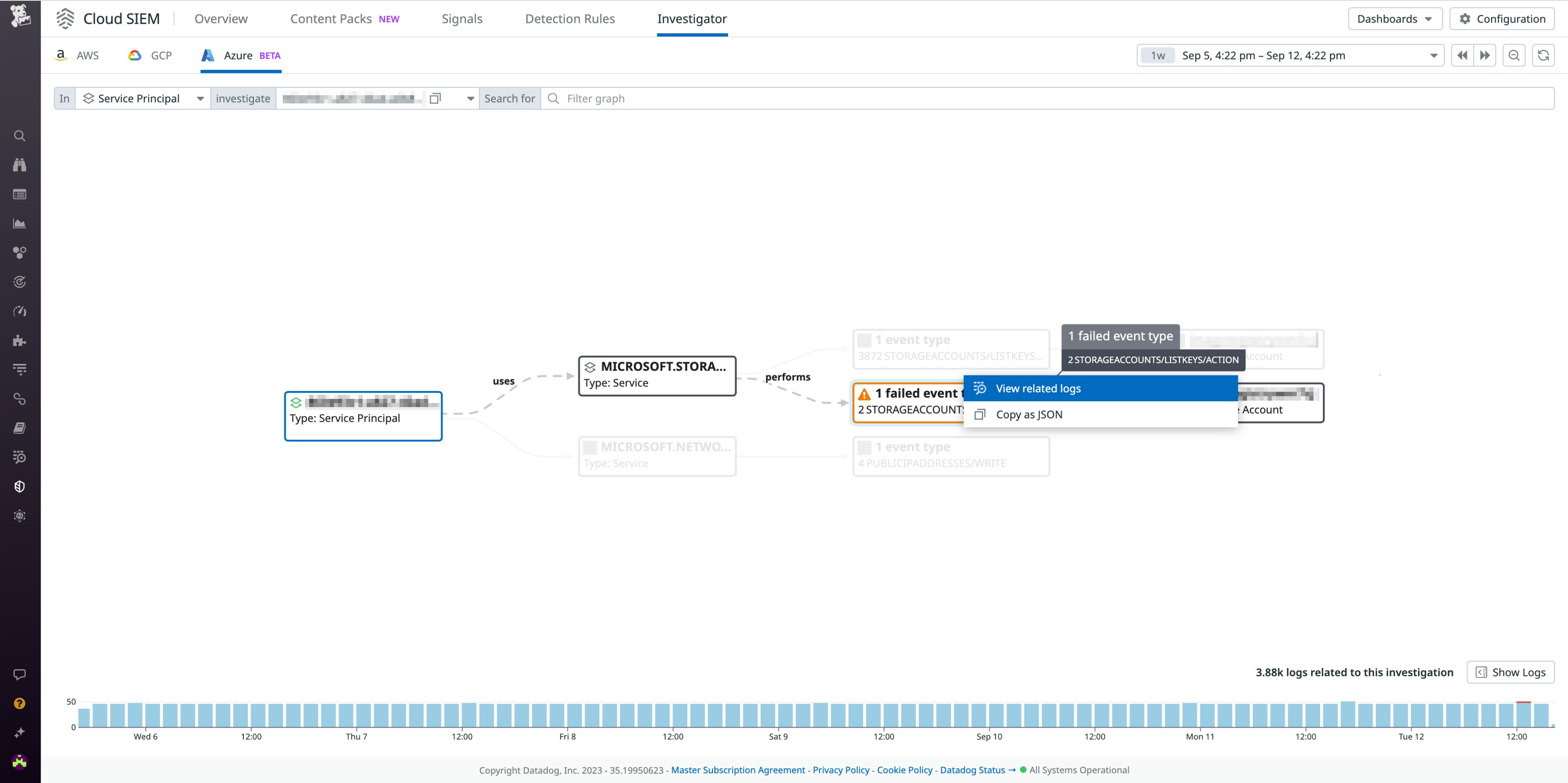
Failed operations could indicate that the account has been compromised, so it’s important to investigate related activity to determine whether the incident represents a security threat. Security teams and DevOps engineers can use the visualizations provided by Cloud SIEM Investigator to drill down into related logs for details that can help them determine if the activity is coming from a legitimate user or an attacker.
Improve cross-team collaboration on investigations into cloud resources
During these kinds of investigations, context is essential—but often, siloed data prevents teams from attaining it. Security engineers may not have complete insight into infrastructure makeup and configuration when assessing the legitimacy of a potential attack and evaluating how it has propagated through the environment. Meanwhile, DevOps engineers may lack the frame of reference needed to identify the security implications of a given set of logs.
Cloud SIEM Investigator integrates with both the Datadog Log Explorer and Security Signals, giving teams a centralized set of resources they can use to collaborate on identifying the source of a flagged event or log. For example, Datadog Cloud SIEM will generate a security signal when your Azure logs indicate that a new owner has been added to a service principal. In the Investigator, you can select the “View related signals” option on a given user, action, or event to pivot to a security signal and gather more information about a potential incident.
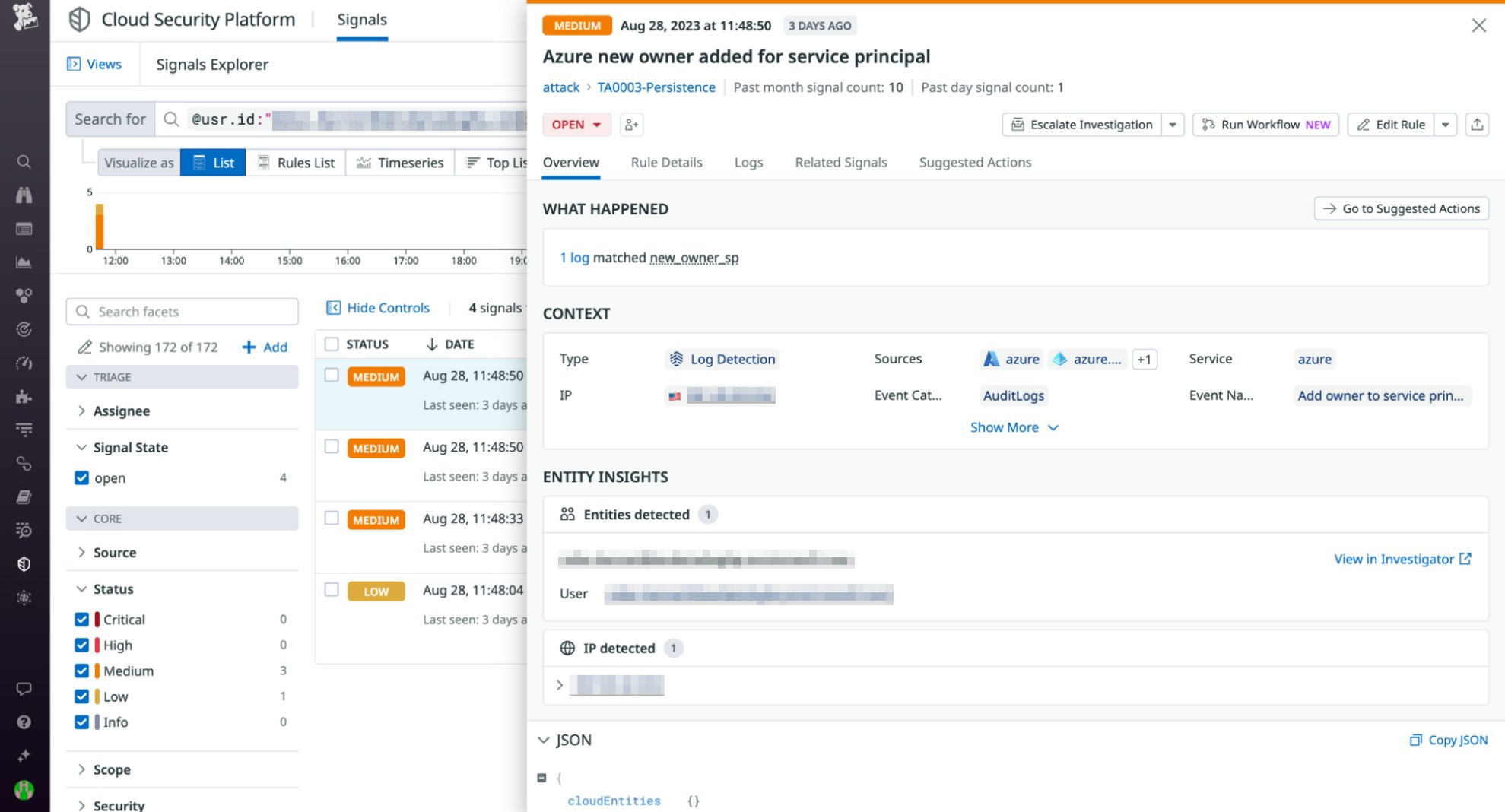
From here, security and DevOps can work together using the contextual information provided in this security signal—such as the user email address, IP address, and more—to determine if the new owner is a legitimate user or an attacker trying to attain persistence in your environment.
Get enhanced visibility into your Azure environment today
With Datadog Cloud SIEM Investigator, organizations can now visualize activity throughout their Azure environments, enabling them to quickly identify details about the end users and service principals that are interacting with key Azure resources. This visibility enables DevOps and security teams to align and dig deeper into root causes more efficiently.
Check out our documentation to learn more. If you’re new to Datadog, sign up for a 14-day free trial today.