When it comes to securing your production environment, it’s essential that your security teams are able to detect any suspicious activity before it becomes a more serious threat. While detecting clear-cut attacker techniques is essential, being able to spot unknowns is vital for full security coverage. But given the huge volume of logs modern cloud infrastructures generate, understanding baseline user activity that occurs within those infrastructures and spotting anomalies can be like finding a needle in a haystack. And with microservice-based environments constantly changing their behavior, keeping track of what’s “normal” becomes a challenge.
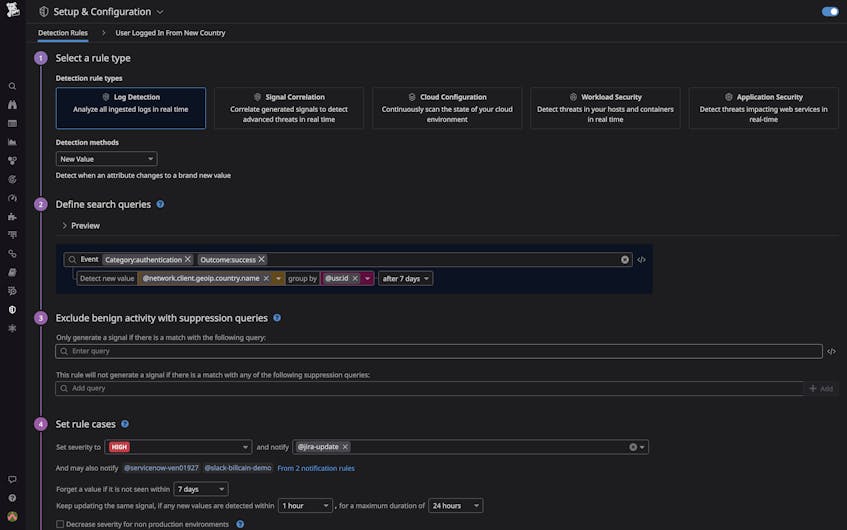
Datadog Cloud SIEM’s Security Rules let you define patterns that match specific activity from an attacker as dangerous, and then alert you when these patterns occur. To give you even more options for alerting on anomalous activity, you can now create rules that use the new value detection method, so that Datadog will learn the historical behavior of specified entities within your environment and then notify you when unfamiliar values appear in the attribute fields of their associated logs. This means that Datadog can now monitor behavioral patterns in your logs and automatically notify you whenever a deviation from the baseline occurs.
Security on your terms
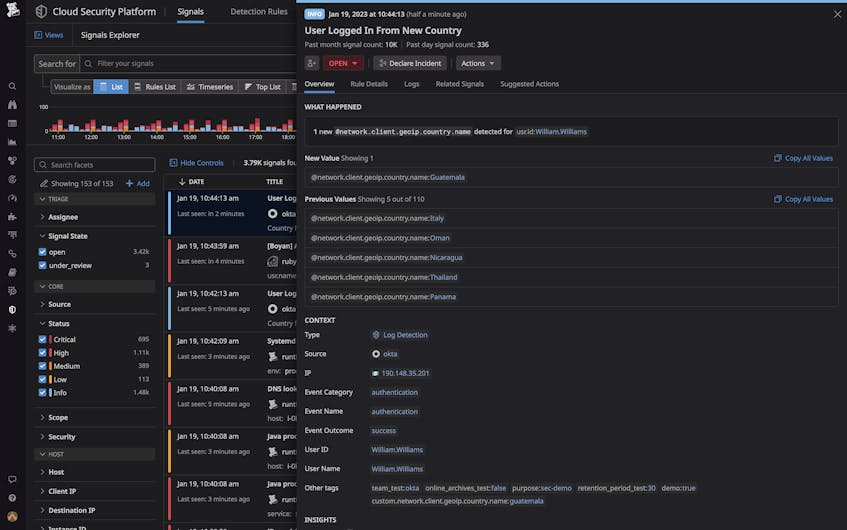
In order to detect deviations from normal behavior, new value–based rules analyze users and entities within your log data over a chosen period of time. If Datadog ingests a log that contains an attribute value for a given user or entity that is different than what has appeared over that time window, it generates a record of the anomaly, or a Security Signal. Values to monitor might include requests coming from new countries, IP addresses, or cloud regions; unusual compute types for newly provisioned resources; and so on.
As an example, you may want to detect the first time a user authenticates from a country they have never authenticated from before. You can do this by enriching your authentication logs with geo-ip and monitoring for newly seen countries for each user. In this instance, it would make sense to configure the training window to “after first seen value,” as this would generate a Security Signal for any new country a user logs in from after their first authentication occurs.
Another example is to detect when an attacker launches infrastructure resources in a cloud region which is not used in your environment. Attackers use this strategy after they have compromised a user account and they want to maintain persistence or mine cryptocurrency with your compute infrastructure. To catch such instances, you can set up a Detection Rule that groups logs by AWS account, GCP project, or Azure subscription and notifies you whenever your account performs a write action in a new region. This would allow you to investigate the anomaly when the attacker gains persistence and before they can begin to spend a large amount of your money on compute resources. In order to give the rule an accurate representation of usual activity, it would make sense to set this rule’s training window to one week.
Expand your cloud SIEM with new value Detection Rules
With the addition of new value–based Security Rules, Datadog Cloud SIEM can now automatically look for and alert you to anomalous activity in your logs, giving you more alerting reach than ever before. If you’re already a Datadog customer, see our documentation to get started creating Detection Rules using the new-value detection method. Otherwise, get started today with a 14-day free trial.