Unify Monitoring Across Your Stack
Visualize metrics, trace, logs and more in a single platform.
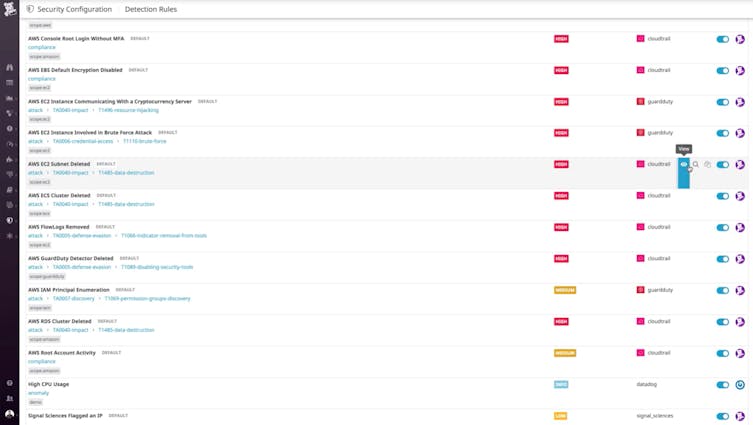
Next-Generation Security Monitoring Tools
Monitor for and proactively remediate potential security threats.
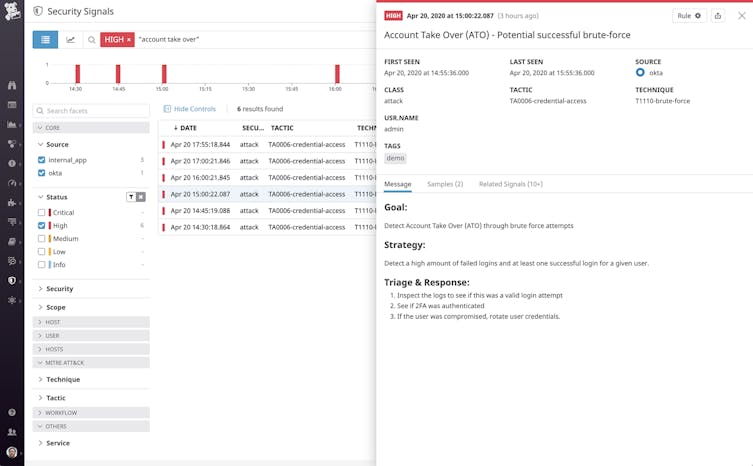
Security Investigation Dashboards
Simplify your investigations with drag-and-drop, customizable dashboards.
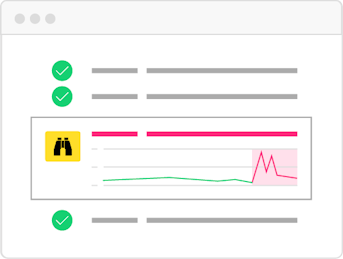
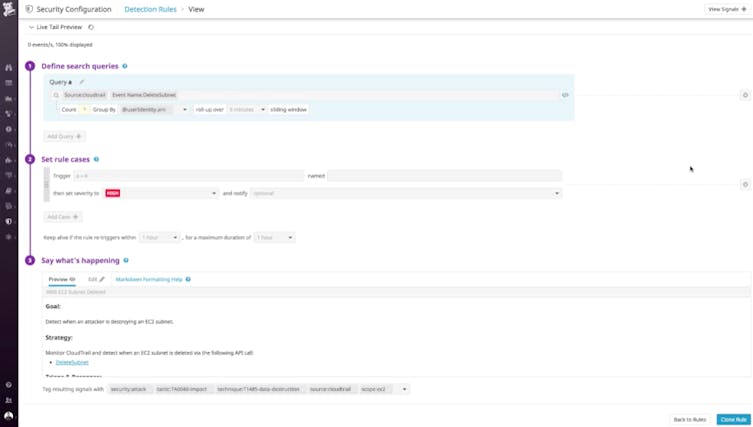
Watchdog
Detect threats and issues using machine learning.
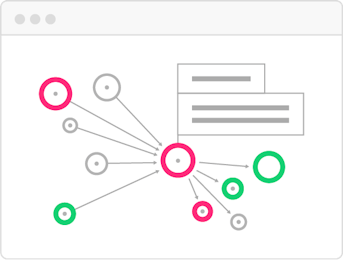
Root cause analysis
Visualize your observability and security data together, seamlessly pivoting between related metrics, traces, and logs.
Security Monitoring Resources
Learn about using Datadog security monitoring tools.