Threat modeling is a critical part of building high-performing, secure systems. It is responsible for “analyzing representations of a system to highlight concerns about security and privacy characteristics.”1 Creating an effective threat model involves two main steps: system modeling to map out all existing system components and the relationships between them, and threat elicitation to identify areas in the system that could be vulnerable to a security issue.
Threat models should provide an organization with visibility into its systems, and actionable findings to use as a basis for securing them. Developing threat models that fulfill these expectations can be difficult, as teams can quickly run into one or more of the following pain points:
- Lack of visibility into the active development of new system components
- Blind spots in data flows between systems and resources, especially in legacy and third-party systems and integrations
- Discrepancies between a system’s initial design and its actual implementation
- Lack of documentation for system functionality and ownership
After clearing these hurdles, organizations must then methodically sift through each modeling session’s findings and suggest mitigation strategies that strengthen security for their systems as needed. This is a cyclic process, because an organization’s threat models must adapt as their systems evolve. If threat models do not keep up with system changes, organizations will end up with an incomplete picture of their infrastructure’s attack surface.
Datadog Application Security Management (ASM) addresses these gaps by helping organizations map their entire system, which can surface design flaws in application and business logic that static threat models may miss. This critical visibility enables organizations to quickly identify threats in their existing application topology and anticipate the flow of potential attacks. By leveraging distributed traces through its integration with Datadog APM and real-time network data, ASM provides organizations with an up-to-date view of the composition and state of their systems before, during, and after requests.
In this post, we’ll look at how you can use distributed tracing and Datadog ASM for system modeling and threat elicitation to build effective threat models.
Develop accurate system models with distributed tracing
Creating threat models for small systems or new system components is relatively straightforward. In these environments, organizations typically have end-to-end visibility into development and deployment, so they can easily see how each piece of a system fits together. But for long-running systems with sprawling, complex infrastructure—where operational knowledge is often limited to a few team members—threat modeling sessions can be impacted by substantial gaps in visibility. On top of that, the implementation of a system might not match its initial design, and outdated system models and documentation can muddy the process.
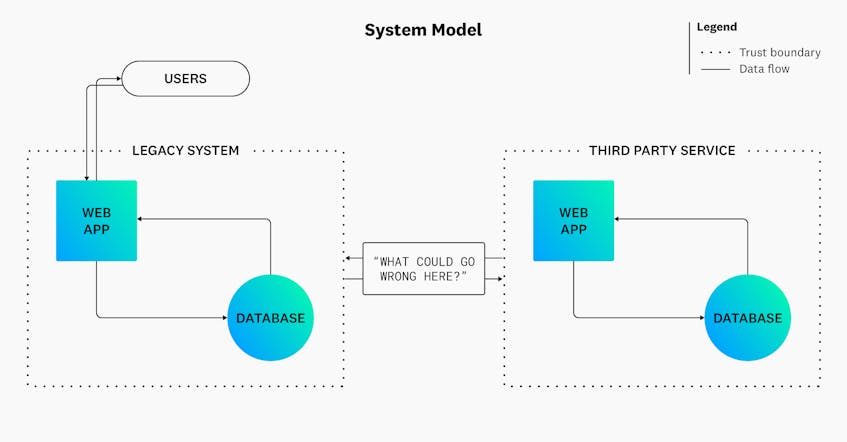
Threat modeling sessions can become even more complex when integrating modern services with legacy systems. In these (quite common) scenarios, critical data flows between system components—as well as their primary entry points, such as open ports—can become obfuscated. As illustrated in the following diagram, integrating a third-party service with an organization’s legacy system can introduce blind spots in data flows:
Without visibility into what can go wrong in this scenario, you may overlook signs of malicious activity. Installing a web application firewall (WAF) and restricting traffic here could be good first steps towards controlling input. But there may still be other design flaws that could leave the environment vulnerable to an attack. To eliminate blind spots efficiently, organizations can use distributed tracing to develop a comprehensive, accurate view of their entire system, including any new integrations.
Visualize systems and their dependencies
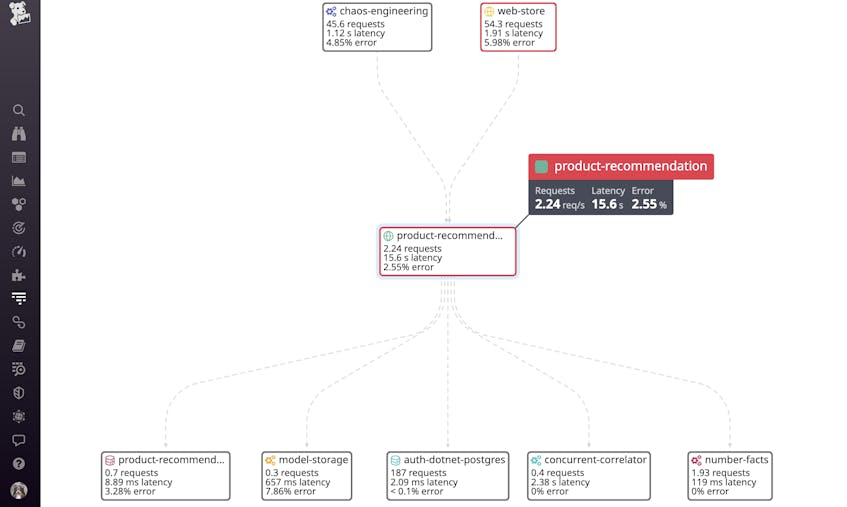
Distributed tracing captures the flow of requests between systems and their components. Organizations can leverage distributed tracing tools like the Service Map to visualize all the connections between their system components. This tool strengthens an organization’s threat modeling sessions by allowing them to not only map their complex infrastructure but also to better understand their attack surface.
As illustrated in the following screenshot, the Service Map automatically breaks down a system into its individual components and dependencies, and outlines request flows between them in real time:
This enables organizations to map how data flows through their systems, including from external sources. Clicking on the affected service provides teams with more information about the source of the requests, so they can determine how a threat actor would target their infrastructure.
Identify service owners to support productive threat modeling sessions
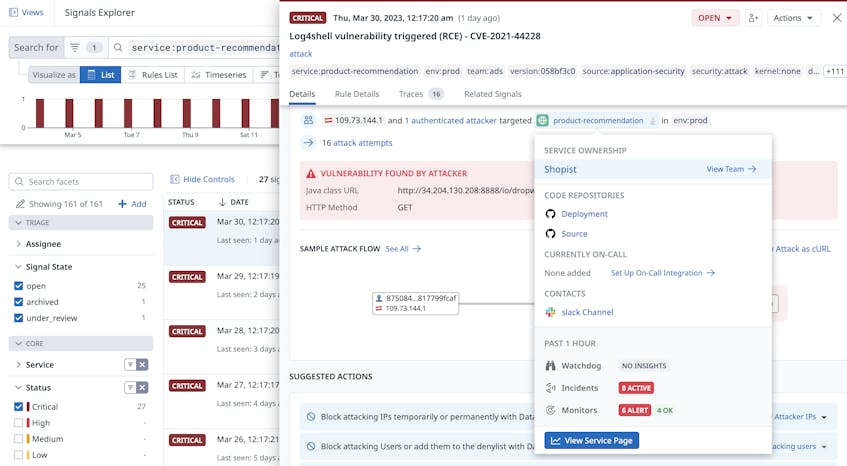
Another pain point in developing threat models for complex infrastructure is being unable to identify who owns a particular component, such as the interface with the third-party service in the previous example. Visibility into ownership is critical because it establishes a point of contact in case of a security-related issue. It also helps organizations quickly confirm the relationship between the component and the rest of the system, which fosters more productive threat modeling sessions.
Just as it visualizes system dependencies at a high level, the Service Map can also offer a starting point for identifying the owners of a particular service and facilitate communication between teams. Organizations can pivot from a service they are investigating in the map to other integrated visualizations like the Host Map, where they can review all the service’s underlying hosts to determine who created them. Organizations can use this information to update their threat models accordingly and supplement their service documentation through ASM’s integration with the Service Catalog, which provides quick access to services’ metadata.
For example, when ASM identifies a vulnerability, it will generate a security signal that includes information about who owns the targeted service:
This critical insight enables organizations to successfully fill the visibility gaps that traditional threat modeling sessions may create.
Mitigate threats by anticipating the flow of an attack
As previously mentioned, threat modeling is an iterative process that should adapt to an organization’s dynamic systems. But attacks are also rapidly changing in nature, scope, and impact. Organizations need to ensure that their threat models anticipate what can happen to their mapped systems by answering questions like:
- How quickly can a particular attack scale?
- Which parts of a system are susceptible to DDoS attacks?
- How much will recovery cost if an attack is successful?
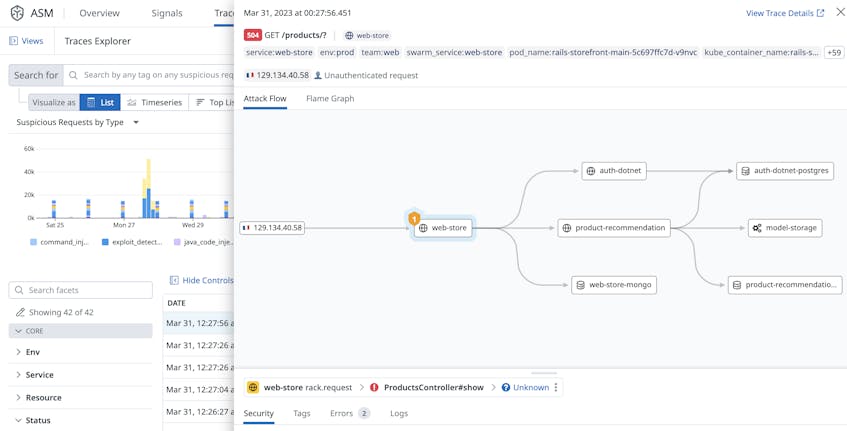
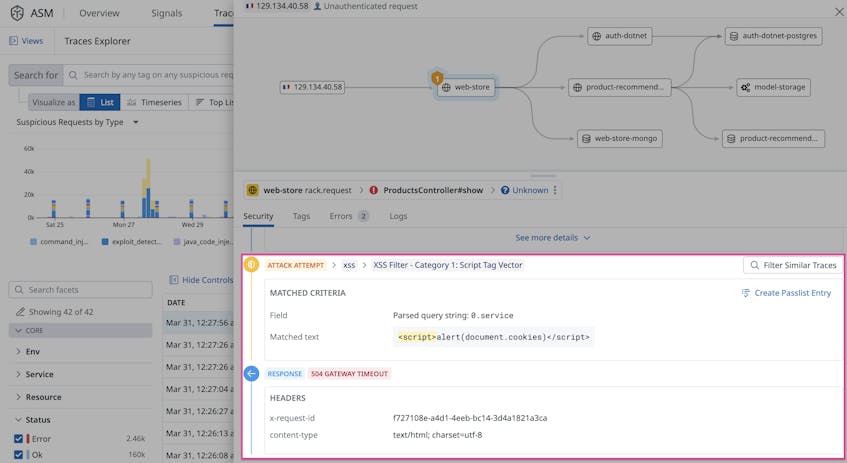
That’s why ASM—and the tracing abilities it inherits from APM—can be a crucial part of threat modeling. It captures the complete flow of an attack, giving organizations a reliable, up-to-date view into how their systems became vulnerable. As illustrated in the following screenshot, ASM captured the entire path of a cross-site scripting (XSS) attack, from its source to all affected downstream services:
ASM also provides additional information about an attack, such as its type, the targeted function, and how the affected system responded to the event:
With this rich security context, organizations can make informed decisions on how to keep their threat models up to date. They can also use this information to validate their models and confirm that documented mitigation steps work as expected. For example, they can verify that connections from known-malicious IP addresses are automatically blocked via ASM’s In-App WAF.
Develop threat models with confidence
Datadog ASM enhances threat modeling sessions through its deep integration with the APM platform. By leveraging distributed tracing, ASM enables organizations to easily visualize the composition of their systems and understand how underlying components interact with each other. In addition, ASM identifies legitimate threats to their systems by automatically generating code-level security insights. Together, these capabilities help organizations develop valuable threat models for their systems and use them with confidence.
To see Datadog Application Security Management in action, you can request a personalized demo. If you don’t already have a Datadog account, you can sign up for a 14-day free trial today.