The popularity of serverless architectures continues to grow as organizations seek to simplify scalability and eliminate the need to provision and manage infrastructure. In our most recent State of Serverless report, we found that there has been significant serverless adoption across Azure, Google Cloud, and AWS.
While serverless architectures have shifted the responsibility of server-side security to trusted cloud providers, customers are still responsible for securing their applications against application-level attacks such as Command/SQL injection, Cross Site Scripting (XSS), and more. Securing serverless applications is uniquely challenging because they are highly distributed and comprise several ephemeral stateless components. This requires security at different layers; serverless functions need to be secured not only in the code but also at the invocation level, which further complicates application security as functions are often invoked millions or billions of times a month. This new attack surface offers more opportunities for attackers to exploit vulnerable applications and compromise the integrity of applications and underlying data.
Datadog Application Security Management helps improve your security posture by detecting threats to applications built on AWS Lambda. Datadog ASM leverages the same Datadog tracing library as Application Performance Monitoring (APM), which means you can monitor threats to your applications without any additional agents or instrumentation.
ASM monitors the traffic of your serverless application to generate security signals and provide insight into attacks attempting to exploit vulnerabilities in serverless applications.
In this post, we’ll look at how we address the challenges of securing serverless architectures by letting you:
- Detect critical attacks across your serverless applications
- Investigate attacks with distributed traces
- Respond within existing workflows and tools
- Detect vulnerabilities in third-party libraries
Detect critical attacks across your serverless applications
Because every invocation of a serverless application could be an attack attempt, securing them requires visibility into every invocation. Without visibility into the full scope of a request, it can be difficult to distinguish between legitimate and malicious traffic, giving an attacker more time to successfully exploit a vulnerability.
Datadog ASM operates at runtime and monitors on an invocation basis. Once enabled, ASM will monitor requests across your Lambda functions to detect and alert you of security threats. To explore ways to enable ASM, please see our documentation.
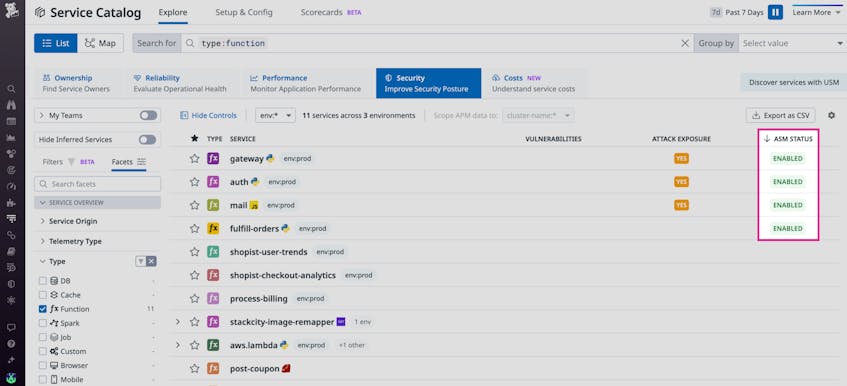
You can see the attack exposure across your serverless applications in the Service Catalog. If you notice that a Lambda function received attack attempts but isn’t being monitored by ASM, you can quickly enable ASM to ensure it’s well-protected and secure.
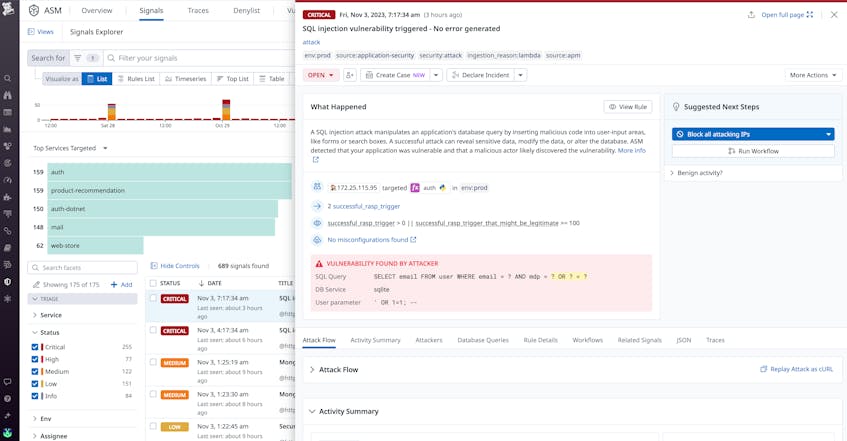
ASM includes out-of-the-box detection rules that automatically flag harmful attacks—including OWASP Top 10 attacks such as Local File Inclusion and business logic attacks such as account takeovers—with the added functionality of creating your own custom rules. When an attack is detected, Datadog will generate a security signal to notify you.
Investigate attacks with distributed traces
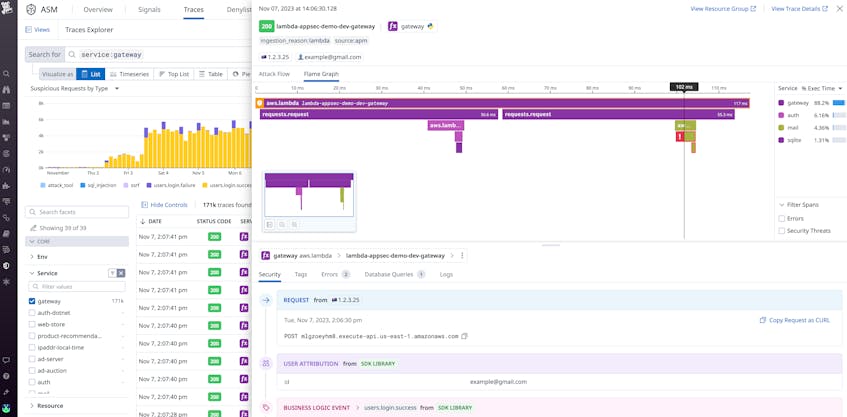
Another challenge to securing serverless architectures is the ephemeral nature of Lambda functions, which makes it difficult to determine the scope of an attack and how best to respond. Datadog APM distributed tracing addresses this challenge and helps you identify the most urgent ongoing attack attempts by tracing requests as they spread across your serverless application. Within ASM, you can pivot from a security signal directly to its related traces, letting you immediately investigate with the context you need to understand what happened and determine the best way to respond and remediate.
Distributed tracing also enables you to see Attack Flows that show how an attack propagated across functions to understand its blast radius and gain the context you need to determine the appropriate response. In the screenshot below, you can see that a Server-Side Request Forgery (SSRF) attack has occurred on a web-store service that’s upstream of a sensitive MongoDB database, and therefore calls for immediate action.
Respond within existing workflows and tools
Datadog ASM also helps facilitate your response by enabling you to create or run a Workflow directly from a security signal, which triggers a series of preset actions that help with responding to specific issues or threats. For example, in the event you receive a security signal about an SQL injection attack, you can immediately run a Workflow that tells your AWS web application firewall (WAF) to block all the listed malicious IPs from reaching your application. Additionally, you can further collaborate with other teams through various integrations, such as Slack notifications or Jira tickets.
Detect vulnerabilities in third-party libraries
Serverless developers often rely on third-party libraries and packages to extend the functionality of their serverless functions. This third-party layer introduces new complexities and potential security vulnerabilities into your serverless ecosystem that could go undetected if you don’t have an efficient monitoring strategy in place.
Datadog ASM offers Open Source Vulnerability Detection, which continuously monitors for vulnerable third-party dependencies in your AWS Lambda functions that present active risks in production. You can see all detected vulnerabilities in the Vulnerability Explorer grouped by desired criteria—such as highest severity—so you can immediately see which is in most need of attention. You can then click on that vulnerability to get additional information, such as the nature of the vulnerability and remediation recommendations.
Secure your serverless applications with Datadog ASM today
Datadog Application Security Management provides insight into attacks throughout your serverless architecture, enabling you to understand an attack’s blast radius and respond quickly. This means you can spend less time investigating and responding to threats and more time developing and shipping new features to your customers.
ASM serverless support is now generally available for AWS Lambda. Open Source Vulnerability Detection for AWS Lambda is currently in public beta.
To start monitoring your serverless functions for threats, enable ASM today by checking out your AWS Lambda functions in the Service Catalog.
If you aren’t already using Datadog, sign up today for a 14-day free trial.