Many modern applications are regularly accessed by countless users from all over the world, which makes it difficult to identify anomalous patterns in login activity indicative of a security breach. This challenge is compounded by the fact that people travel often and regularly access their accounts from new locations. To detect this common attack vector, the Datadog Cloud SIEM now provides the impossible travel detection rule type which helps you spot suspicious logins with confidence.
When impossible travel detection rules are enabled, Datadog will analyze your logs to determine whether they indicate that a user has traveled between locations at an impossible speed. This is a sign that a bad actor may be trying to gain unauthorized access to your application. For instance, if logs show that only 15 minutes have elapsed between a user’s login attempts in New York City and Paris, the impossible travel detection rule will flag that activity and generate a Security Signal to notify you. In this post, we’ll take a look at how to create effective impossible travel detection rules that can help you improve your organization’s security posture.
Create and apply impossible travel detection rules
Like our other threat detection rules, impossible travel detection rules enable you to use Datadog’s log search syntax to easily specify which logs you want to monitor. You can also add values to the group by dimension of your query and, if a rule is triggered, a Security Signal will be generated for each value added. For instance, if you group a rule by “User,” a Security Signal will be generated for each unique user that sets it off.
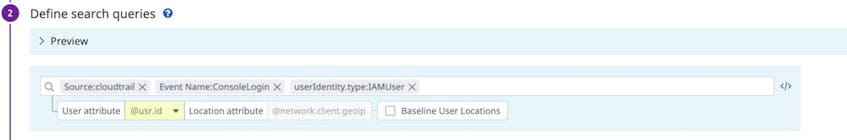
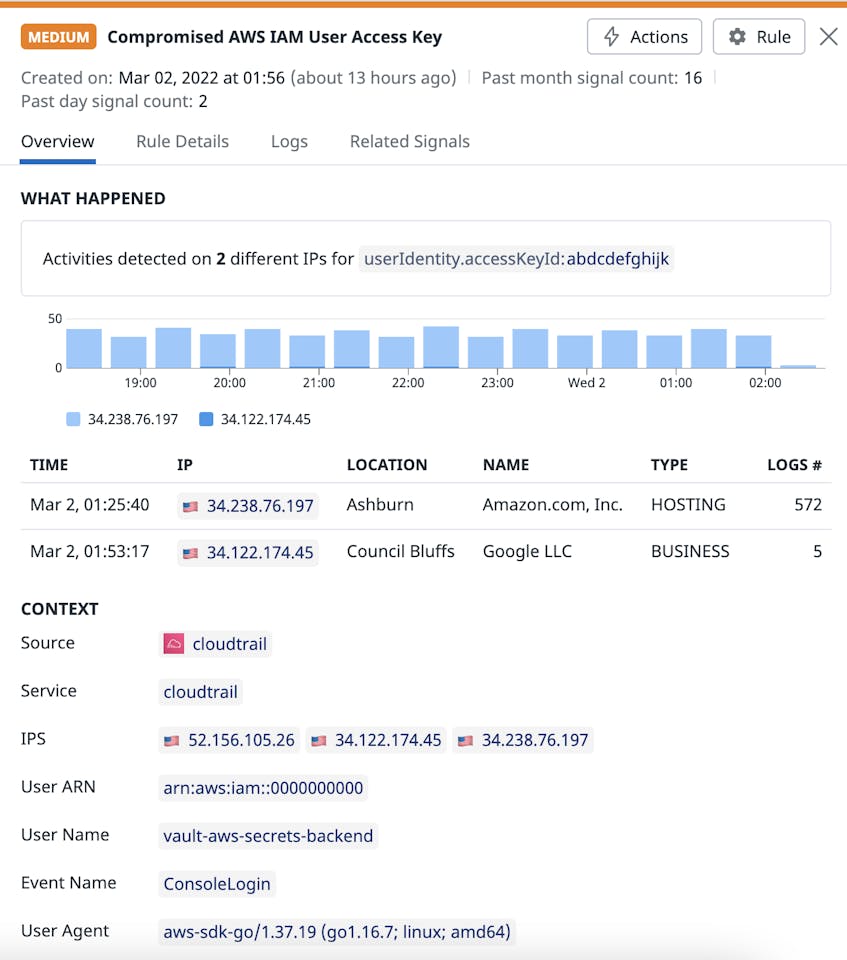
The screenshot above shows the configuration for a new impossible travel detection rule that analyzes CloudTrail audit logs that have recorded ConsoleLogin events. This configuration will detect if someone uses AWS IAM credentials to log into your organization’s AWS environment from a location that’s not possible for them to have traveled to in the time since those credentials were last used. If the analyzed logs trigger the newly configured rule, Datadog will generate a Security Signal to notify you.
Fine-tune your rules
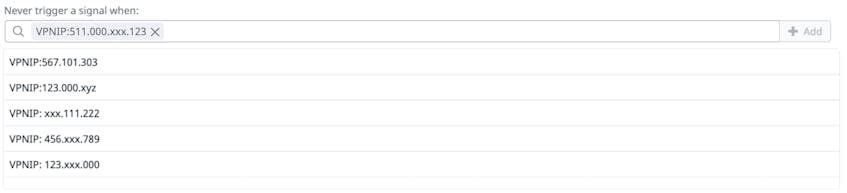
Although detection rules alert you to possible threats, they must be carefully configured in order to minimize false positives. For instance, some trusted users may choose to use Virtual Private Networks (VPNs) for security purposes, which can trigger detection rules by mistake if those VPNs have IP addresses that are hundreds of miles away from users’ usual locations. You can ensure this type of activity does not trigger your rules by using suppression lists, which prevents security rules from triggering on specific users and known IP addresses. To create a suppression list when configuring an impossible travel detection rule, click on the “Advanced” option and add the values you want to exclude. The screenshot below, for example, shows a suppression list that automatically excludes logs from known VPNs.
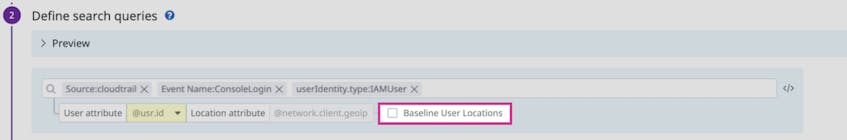
If you do not know the exact values to include in a suppression list, you can enable “Baseline User Locations” when you create an impossible travel detection rule. This setting studies the locations from which your users tend to access your application–and prevents detection rules from being applied to the logs they generate. With this feature, you can ensure the rule is applied only to logs that are most likely to indicate malicious intent.
Getting started
You can detect and investigate suspicious logins by using impossible travel detection rules to identify when a user accesses your application from a location they could not have traveled to in the time since their last recorded login. In order for impossible travel detection rules to run, Datadog requires the queried logs to include the standard @network.client.ip attribute, which our GeoIP Parser uses to extract the location data of a given client. You can learn more about the impossible travel detection rule type, as well as our out-of-the-box detection rules available on our Cloud SIEM platform, by checking out our documentation.
If you’re not already a Datadog customer, sign up for a 14-day free trial.