As healthcare and life sciences organizations move to digitize their operations and automate their workflows, they are encountering new challenges related to HIPAA regulations, which dictate how patient information should be collected and stored. For example, a modern healthcare organization might be responsible for managing millions of patient records across a variety of devices and applications, making it essential for their infrastructure to be able to safely and securely handle enormous data streams coming from every digital asset within their system.
It is particularly important for these organizations to adhere to HIPAA compliance requirements for application logs as they grow and scale. Audit logs must be safely collected from every service within an organization’s system and stored for six years in case they are needed for an internal or HHS investigation. With Datadog’s HIPAA-compliant observability and security solutions, organizations can capture and store monitoring data—including audit logs, distributed traces, RUM events, and more—on a long-term basis. They can also leverage their logs to verify their level of compliance with other HIPAA provisions and automatically detect security threats and misconfigurations in real time.
Observing HIPAA regulations in a changing industry landscape
The Health Insurance Portability and Accountability Act, commonly known as HIPAA, is a set of rules and regulations passed by Congress in 1996 that established standardized requirements for the protection and confidential handling of protected health information (PHI). HIPAA rules were designed to govern healthcare providers, health plans, and similar organizations, which are defined as “covered entities,” as well as vendors of products and services working with healthcare-related organizations, which are defined as “business associates.”
Two of the most relevant HIPAA laws for companies leveraging technology to service their customers are:
- The HIPAA Privacy Rule, which sets access standards for protected health information (PHI), such as medical health records and treatment plans. This information might include a patient’s personally identifiable information (PII), such as their Social Security Number and contact information. This rule applies to HIPAA “covered entities.”
- The HIPAA Security Rule, which implements technical, physical, and administrative safeguards designed to protect electronic personal health information (ePHI). This rule applies both to “covered entities” and “business associates.”
As more and more healthcare and life sciences organizations enlist cloud service providers for their treatment plan processing and administration needs, the Security Rule in particular is profoundly impacting how these organizations, as well as their vendors and service providers, conduct business. HIPAA provides guidance on appropriate administrative, physical, and technical safeguards to protect the confidentiality, integrity, and availability of ePHI. Covered entities are responsible for conducting a periodic risk analysis in order to detect potential vulnerabilities and violations, making it essential that they associate with business partners who not only make compliance easier, but who are HIPAA-compliant themselves.
Monitoring is key for reliable and secure healthcare applications
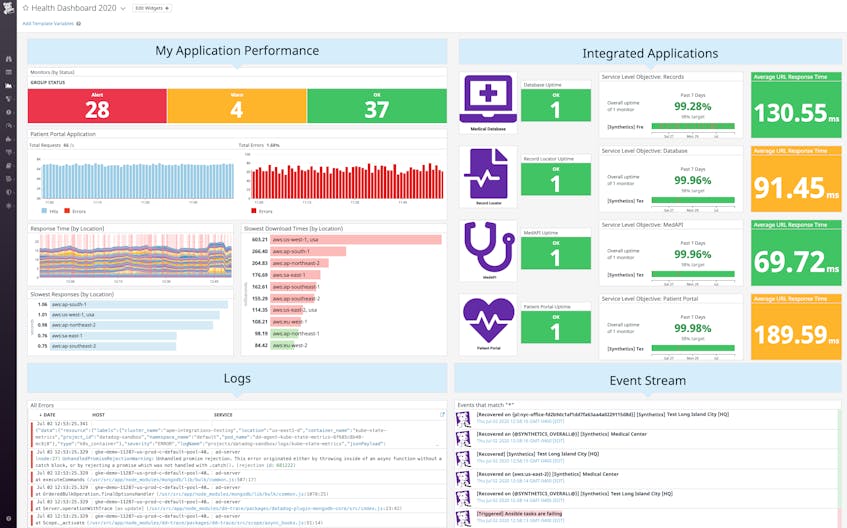
Running healthcare applications in the cloud provides key benefits in terms of efficiency, scalability, and availability. But it also means increased complexity, which creates additional challenges for application reliability and data security. For example, users need to be able to access important services at any time and from any device. Issues in any layer of an organization’s stack can cause problems that affect end users, so unified visibility across all parts of the application is important for teams to quickly identify when something isn’t working. Collecting all relevant data in one place—including metrics, logs, traces, and more—provides needed context for more rapid troubleshooting.
Additionally, healthcare organizations need to protect confidential PII from unauthorized access. It’s vital to continuously monitor the security posture of your entire cloud environment so you can quickly locate and fix misconfigurations or sensitive data leaks, such as a database exposing patient diagnoses to the public internet.
Datadog’s unified platform provides the end-to-end visibility into the health, performance, and security of cloud-based healthcare applications to help ensure they remain reliable and secure for patients.
HIPAA-enabled log management
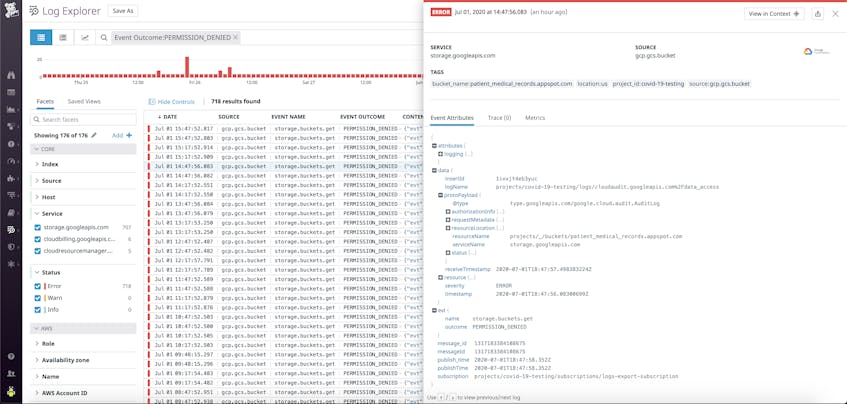
One of the main objectives of organizations that are pursuing HIPAA compliance is the maintenance of proper safeguards for technologies that process ePHI. The Security Rule’s provision on Audit Controls states that covered entities and business associates must “implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use electronic protected health information.” Practically speaking, this means covered entities and business associates must keep detailed audit logs of all activities (such as user logins, data store queries, access control changes, and administrator actions) that occur within their application and infrastructure.
Datadog’s HIPAA-compliant log management solution helps organizations rise to this challenge by collecting and storing their audit logs from a variety of sources, such as electronic health record (EHR) systems, patient survey software, cloud providers’ services, and other third-party applications. The log retention period is customizable, and logs can also be archived for long-term storage in Amazon S3, Azure Storage, or Google Cloud Storage. Archived logs can then be rehydrated if and when they are needed for an investigation.
This comprehensive approach to log management ensures that all activities within an organization’s system—whether they are routine or suspicious—are documented, so organizations can quickly pinpoint and remedy any vulnerabilities. For example, the Security Rule’s stipulation on Access Control requires that covered entities protect against unauthorized access to ePHI. Datadog customers can verify they are in compliance with this portion of the rule by monitoring their logs to detect an increase in users trying to gain access to ePHI without the proper credentials. Additionally, logs can be used to pinpoint user attempts to change or delete patient records—activities that could potentially violate the Security Rule’s provision on Integrity Controls, which is intended to protect ePHI from illicit alterations and deletions.
HIPAA-enabled security monitoring
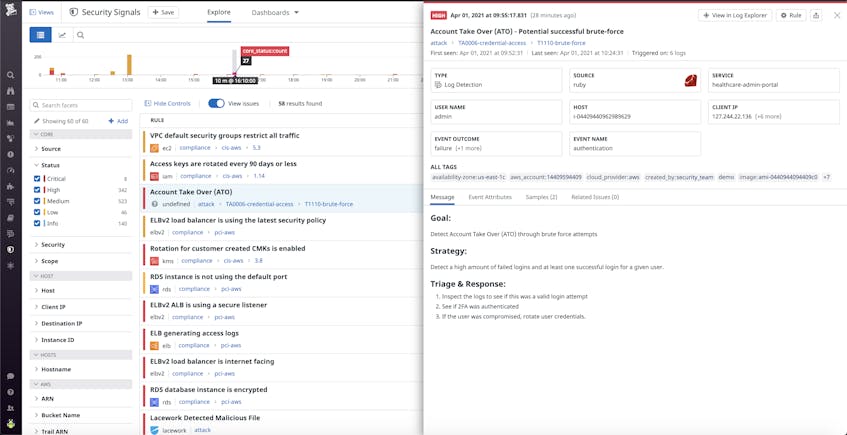
The Security Rule’s administrative safeguard standards, which are outlined in § 164.308(a)(6), state that an effective security incident procedure is one of the requirements for HIPAA compliance. Datadog Cloud SIEM includes several features—such as built-in security integrations, out-of-the-box security dashboards, and customizable threat detection rules—that help companies ensure their security practices adhere to this stipulation. Detection rules apply to the full stream of ingested logs, and if any rule is violated, Datadog will automatically notify the appropriate team members and generate a security signal. You can search and filter all security signals in a unified explorer, or view the details of a particular signal to get more insight into the activity that triggered it, as shown below.
Datadog Cloud SIEM is fully integrated with the rest of the Datadog platform, so users can pivot seamlessly between a potential threat and associated monitoring data in order to investigate and remediate breaches as quickly as possible.
Patient data protection with Sensitive Data Scanner
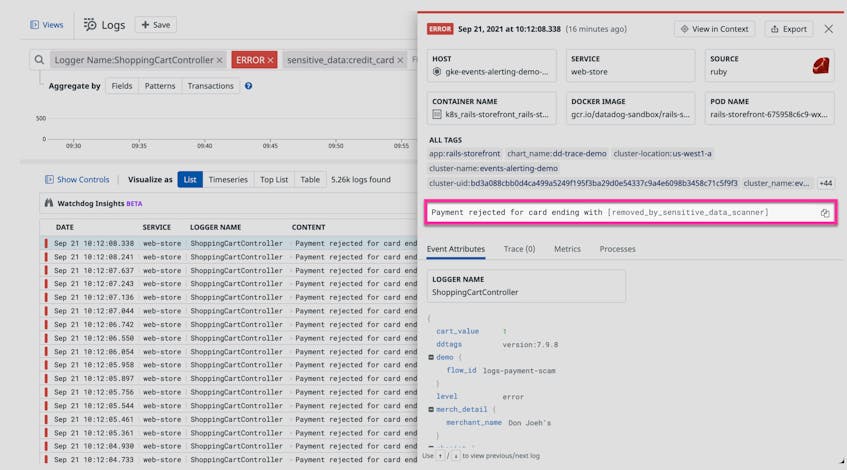
Modern applications are typically composed of numerous services that generate enormous quantities of logs, and small misconfigurations can result in sensitive data leaks. These services are often managed independently of one another, which can limit security teams’ ability to effectively enforce HIPAA compliance requirements across an organization.
The Datadog Sensitive Data Scanner is a low-overhead, cost-efficient solution that allows healthcare institutions, life science organizations, medical service providers, and pharmaceutical companies to discover and classify any sensitive information in their log stream. Teams can leverage out-of-the-box and custom scanning rules to identify sensitive data, such as patient identifiers and credit card numbers, which is then automatically scrubbed to ensure patient privacy. Any log that triggers a rule is tagged with the type of sensitive data that was detected (i.e., sensitive_data:credit_card), enabling teams to configure real-time alerts and build dashboards that accelerate the investigation and remediation process.
HIPAA compliance and security at Datadog
Monitoring solutions that integrate deeply across a healthcare or life sciences organization’s technology stack need to ensure that the ePHI and PII they gather, process, and store is handled in a HIPAA-compliant manner. As a business associate, Datadog is committed to the security and privacy of our customers’ data. For example, Datadog has implemented risk-based security controls and compliance programs to help our customers increase observability while maintaining HIPAA compliance. Furthermore, Datadog has continued to pursue independent third-party assessments and validations of our security and compliance capabilities, including industry-standard certifications and reports, like ISO 27001 and SOC 2 Type II. Finally, Datadog has additional capabilities to further secure the usage of the Datadog platform across distributed tracing and APM, log management, and the Agent.
Datadog provides real-time visibility into application performance, device hardware, and user experience for healthcare and life sciences organizations as they adopt increasingly complex technologies to service their patients and their health records. If you’re already a Datadog customer and you would like more information about enabling Datadog’s HIPAA-compliant observability and security solutions, please contact Datadog support. New to Datadog? Get started with a free 14-day free trial.