Open source libraries have become an indispensable part of modern applications. Approximately 90 percent of organizations use open source software to support their services, but monitoring these dependencies can be difficult when environments run thousands of ephemeral services. The complex nature of modern applications, in combination with the challenge of keeping a competitive edge in a fast-moving market, can make it difficult for organizations to identify and remediate threats in a timely manner. This challenge ultimately leads organizations to risk compromising their applications and exposing them to costly security-related incidents.
Datadog Application Security Management (ASM) enables teams to detect threats against their services in production. Now, ASM is extending its capabilities with Application Vulnerability Management to help organizations automatically identify and resolve vulnerabilities. Application Vulnerability Management targets vulnerabilities in open source dependencies (generally available) and custom code (in private beta)—all out of the box, with no additional configuration needed. In this post, we’ll look at how engineering and security teams can use ASM and Application Vulnerability Management to do the following:
- Understand an application’s attack surface
- Prioritize the most critical vulnerabilities
- Detect drift in application code
Understand an application’s attack surface
Open source libraries provide the benefit of enabling organizations to accelerate software delivery. But they also have a potential drawback: their use can increase an application’s attack surface, or the number of entry points that can be exploited by a threat actor. Although engineering teams may already have a vulnerability monitoring tool in place, it’s often disconnected from their other observability tools. This gap in visibility increases the number of times teams need to context switch between their monitoring tools, so they may not always be aware of when one of their production services is using code from a compromised library. For example, the widely used Log4j Java logging library introduced a critical vulnerability that allowed threat actors to trigger malicious payloads via standard service logs. To mitigate this risk, it’s important for organizations to proactively monitor all their application services for vulnerabilities so that they discover them before they turn into a security threat.
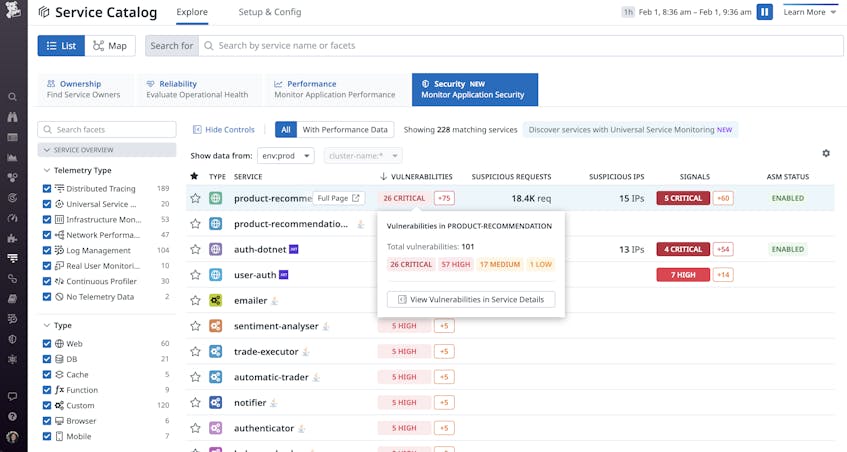
Datadog Application Vulnerability Management is deeply integrated with the Service Catalog and its built-in Security View, so engineering teams can work together with DevOps and security to review vulnerabilities across all their production services, in one place.
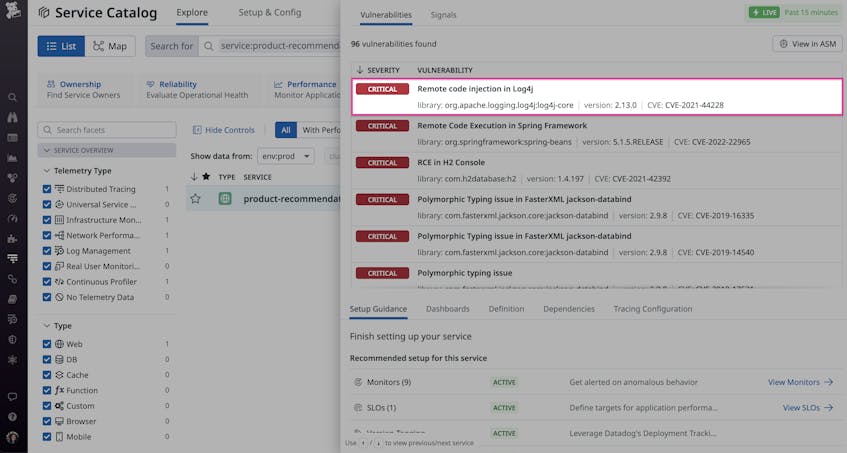
To learn more about a service’s vulnerabilities, teams can click the service to review additional details. Datadog ASM automatically provides a detailed description of an active vulnerability and any associated threats—as well as remediation steps—directly within the Service Catalog view.
To determine next steps, teams can pivot from this view to ASM for more security context. ASM closes the visibility gap between a team’s infrastructure and application data, enabling service owners to fully understand their services’ overall attack surface and which dependencies are most at risk.
Prioritize the most critical vulnerabilities
Monitoring production services for vulnerabilities is an important step towards application security, but determining which ones are more likely than others to become active threats can be difficult. On top of that, organizations need to be able to balance any remediation efforts with delivery timelines. Datadog Application Vulnerability Management helps teams quickly surface all active vulnerabilities via the Vulnerability Explorer. Through the Vulnerability Explorer, teams can search for and filter active threats based on the criteria of their choice, such as the severity level or the specific libraries affected.
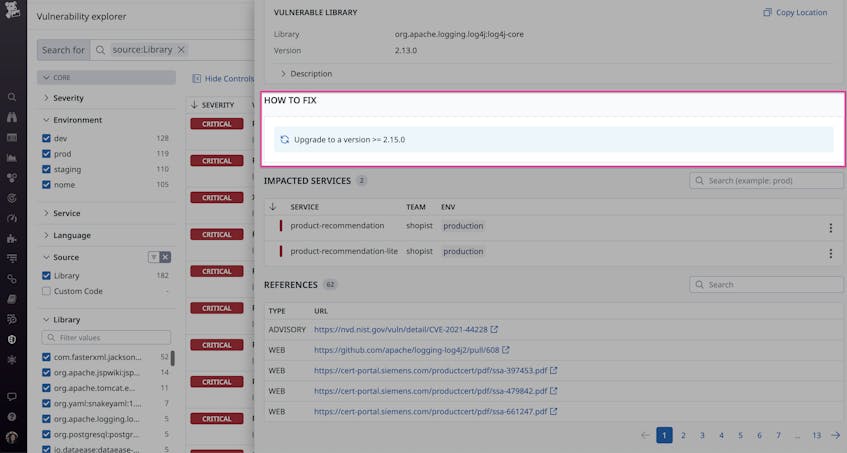
Just as they could in the Service Catalog, teams can select a particular vulnerability in the Vulnerability Explorer to access more context. This view provides critical details for understanding how widespread the issue is, such as the number of impacted services and how long they have been exposed to it. And to help engineers quickly resolve the issue, Application Vulnerability Management also provides the exact step(s) they need to take to remediate the vulnerability, as shown in the following screenshot:
In this case, upgrading the Log4j library to a newer version for all affected services will remove its vulnerability from the environment. To determine exactly where the fix needs to be applied, teams can pivot directly from this view to all affected infrastructure (including containers) by clicking the hamburger menu (three stacked dots) next to an impacted service.
Detect drift between development and production code
Modern environments are dynamic by design, and they become more complex as applications scale to support more features and customers. Code drift—when production artifacts do not match source code—is a common byproduct of this growth and can easily occur as a result of an overlooked environment change or misconfigured CI/CD pipeline. Drift introduces risk for organizations because their production code may not always be up to date with the latest security patches. In addition, most scanning tools focus on static code in repositories and miss vulnerabilities in live code as a result.
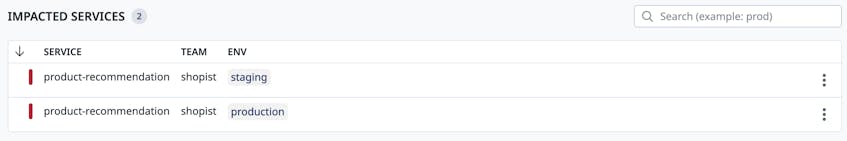
Datadog Application Vulnerability Management provides real-time visibility into code drift by automatically surfacing hidden risks in both open source and custom code in production environments. This allows teams to identify any inconsistencies within their entire codebase. For example, engineering teams can select a vulnerability in the Vulnerability Explorer to review which services and associated environments are affected, as seen in the following screenshot:
In this example, the selected vulnerability for the product-recommendation service is present in both staging and production environments but not in dev. This inconsistency could indicate that a security patch for the vulnerable library has not been deployed to live code as expected. Engineering teams can work with DevOps to determine if a faulty CI/CD pipeline is to blame.
Proactively manage vulnerabilities
Datadog Application Vulnerability Management enables organizations to automatically identify vulnerabilities in all their services’ open-source libraries and custom code, in addition to providing them with the exact steps needed to remediate the most critical issues. Application Vulnerability Management is also deeply integrated with the rest of the Datadog platform, so organizations can efficiently monitor their code alongside the rest of their infrastructure. To get started, you can learn more about identifying open-source vulnerabilities exposed in production with Datadog Application Vulnerability Management or enroll in-app. If you don’t already have a Datadog account, you can sign up for a 14-day free trial.