Cryptocurrency mining (or crypto mining) can be a lucrative yet resource-intensive operation, so cyber threat actors are targeting more organizations in order to take advantage of their cloud resources for mining. Datadog Cloud SIEM can now help you monitor your cloud-based systems for unwanted crypto mining via a built-in detection rule. All you need to get started is to configure your resource logs with Datadog’s @network.client.ip standard attribute.
Crypto mining attacks, known as resource hijacking, can quickly produce a significant amount of strain on servers and cloud-based systems, leading to hundreds of thousands of dollars in unexpected computing costs. Datadog’s crypto mining detection rule scans log data from all your cloud resources for activity from IP or domain addresses that are known to be associated with a mining server or pool.
Accelerate investigations and find the source of mining activity
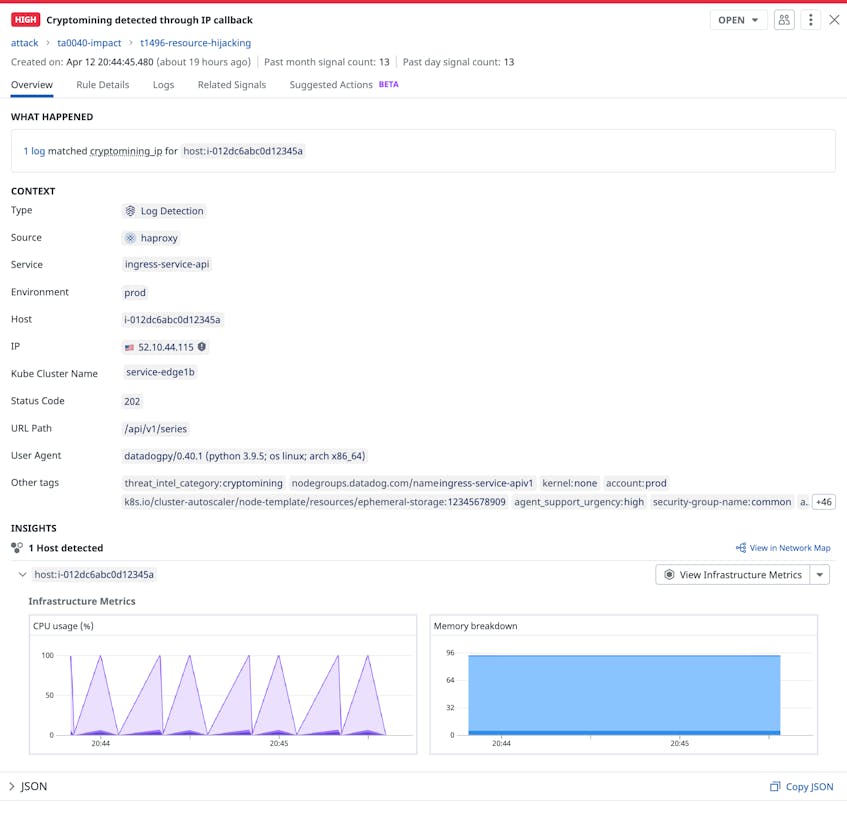
Once the rule is enabled, Datadog Cloud SIEM will generate a security signal as soon as it detects a flagged IP or domain in your logs. Each signal provides key insights about affected hosts, such as performance metrics and a list of running processes. You can leverage this information to investigate additional signs of mining activity in your environment, such as sudden spikes in a host’s CPU or RAM usage or several hosts suddenly running the same unauthorized process.
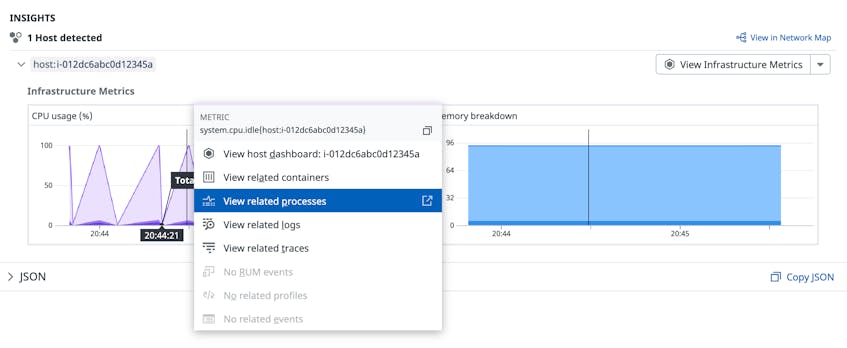
The example signal above shows a significant spike in CPU usage for a host that Datadog determined was communicating with a crypto mining server. If a particular host does not typically execute CPU-intensive operations, the sudden increase may indicate that an attacker has successfully installed a mining client and is actively using it. You can confirm your theory by pivoting to related processes running on the affected host in order to search for any that are unexpected or unauthorized. For example, you might observe a tool like apt-get downloading a shell script from an unknown IP address. This type of activity can be the initial sign of a threat actor attempting to download a cryptominer onto a host.
Identifying the processes associated with a cryptominer can also help you determine the scope of an attack. For example, a threat actor may only run cryptominers on a few compromised hosts at a time in order to avoid detection. You can easily search for other hosts that are running the same suspicious processes in order to determine which ones are compromised. To mitigate this kind of activity, you can kill unauthorized processes and remove associated clients from compromised hosts. You can also block a threat actor from your environment by adding the IP or domain address captured in the signal to your firewall’s deny list, which reduces the risk of another attack from the same source.
Fine-tune rules with suppression lists
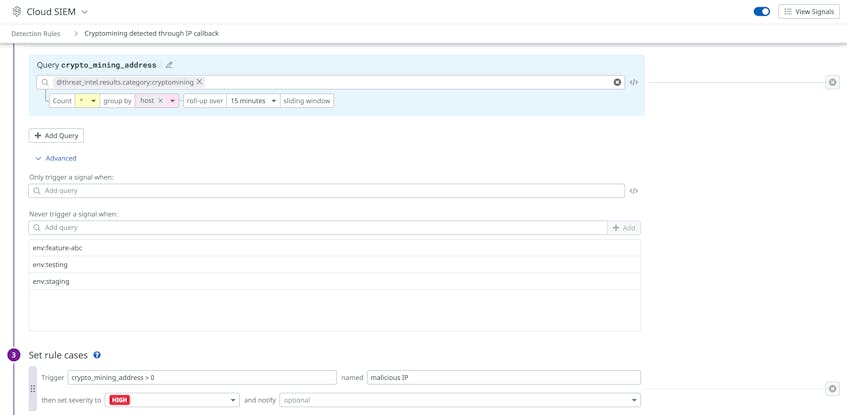
Datadog suppression lists enable you to reduce false positives by controlling when security signals are generated for mining activity. For example, some organizations may support legitimate cryptocurrency applications or services, so activity from these sources should not generate a signal. You can account for these use cases by adding a suppression list to the crypto mining rule, which will prevent it from triggering security signals for specific hosts, environments, or IP addresses.
The example list above includes a group of environments that are used for testing new features for a cryptocurrency application, which would otherwise be flagged as malicious activity because it is associated with mining servers.
Detect cryptocurrency mining with Datadog
Datadog Cloud SIEM enables you to quickly catch signs of unwanted mining activity in your environment, so you can protect your cloud resources, maintain application performance, and prevent unexpected costs. To learn more about the crypto mining detection rule, as well as our other available rules, check out our documentation. If you don’t already have a Datadog account, you can sign up for a free 14-day trial.