Amazon FSx for Windows File Server is a fully managed file storage service built on Windows Server. Migrating on-premise Windows file systems to a managed service like FSx enables organizations to reduce operational overhead and take advantage of the flexibility and scalability of the cloud. But having visibility into file access activity across their environment is key for security and compliance requirements, particularly in sectors such as financial services and healthcare. In order to provide this visibility, AWS recently added file access auditing to the Amazon FSx service. With this update, Amazon FSx now publishes and stores audit event logs that summarize file system access activity at user-level for all files, folders, and file shares.
As an AWS Partner solution, you can use Datadog as an endpoint to send Amazon FSx audit event logs for retention and real-time analysis. You can use Datadog’s Log Explorer to easily search for file access events of interest or use Datadog Cloud SIEM to look for and alert you to any unusual activity. This way, in addition to monitoring FSx metrics via Datadog’s integration, your teams can audit any suspicious or unauthorized activity and take immediate steps to address any detected violations.
In this post, we’ll look at what information these logs contain and how you can use Datadog to:
- Monitor access activity across your file systems
- Create security rules to alert you to possible threats
Analyze and monitor Amazon FSx audit event logs in Datadog
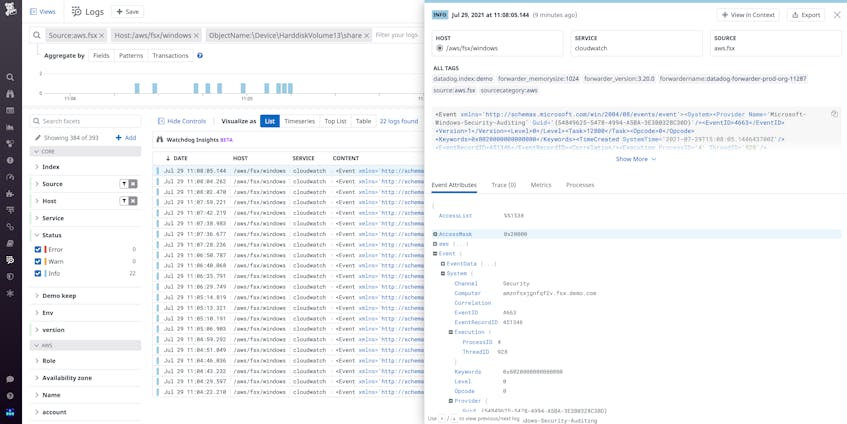
Amazon FSx audit event logs record all user attempts to access, create, modify, or delete a file share or individual file or folder object. Each log follows the standard Windows event log format and contains important information regarding the access event, including:
- the type of event (indicated by the
EventID) - the user who performed the action (
SubjectUserName) - the object being accessed (
ObjectNameorShareName) - whether it was successful (
Keywords) - in the case of file shares, the access action performed (
AccessMask).
Datadog’s built-in log processing pipeline parses and extracts these key fields from your logs as attributes, which you can then use to query, sort, and filter your logs. This enables you to perform complex analysis of user and file activity across your logs. For example, you can easily search for activity related to particularly sensitive folders.
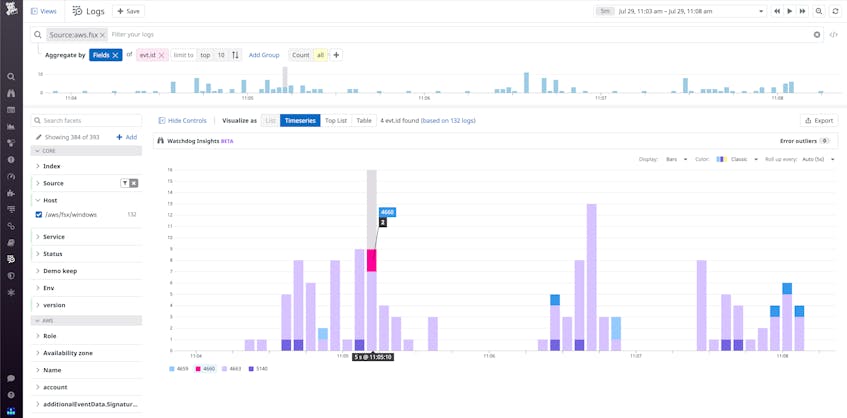
It’s also important to track overall trends in file system activity to surface any unusual behavior. For example, aggregating logs by file access event type, like create, modify, or delete, makes it easy to spot anomalous spikes in certain activity. You can then dive into the relevant logs to look at the users behind the spikes.
Using the Keywords attribute, you can further break down events by whether they were successful or not. This can help you identify spikes in failed operations, which might indicate an unauthorized user trying to access files.
Automatically detect security threats to your FSx file system
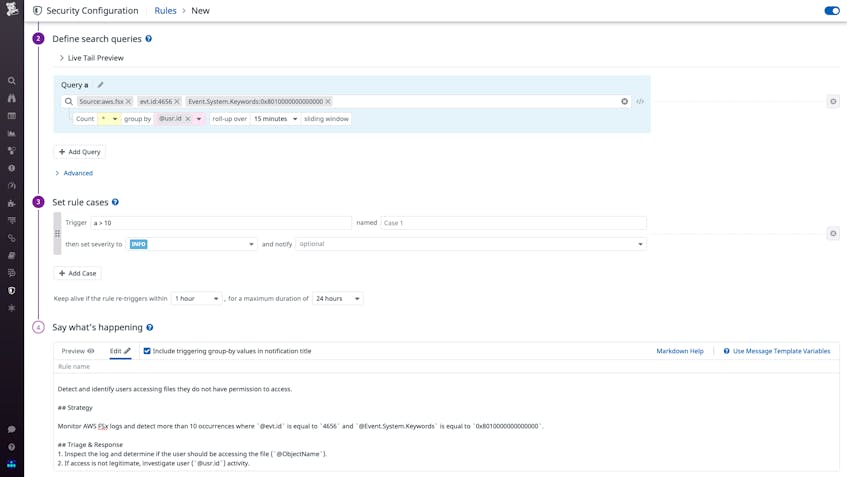
Real-time knowledge of potentially suspicious activity across your file system is key to ensuring the security of your sensitive data. Datadog Cloud SIEM provides out-of-the-box Threat Detection Rules to notify you when Datadog identifies specific activity. For example, the rule below looks for more than 10 failed file access attempts from a single user, which might indicate someone attempting to access files they don’t have permissions for.
You can easily create custom rules for your specific environment. For example, if you have particularly important file shares (ShareName), or even entire file systems (Computer), you can create rules to monitor them for any delete or modify attempts. You might also want to be alerted to any file share event from an IP address outside your organization. You can create a new term–based rule that notifies you of any activity from an address that Datadog hasn’t seen before, helping alert you to a possible threat.
Whenever a rule is triggered, Datadog generates a Security Signal that includes key metadata about the relevant event, so you can determine if you need to take further action, such as adjusting security policy settings to modify who can access certain files.
Get deeper insight into your Amazon FSx file systems
Amazon FSx’s file access audit event logs give your teams immediate visibility into activity across your Windows Server file directory that, when paired with Datadog’s log management and security platforms, helps ensure that your files are secure. You can send your Amazon FSx logs to Datadog either with our Forwarder Lambda function or by using a Kinesis Firehose data stream. See our documentation to get started. Or, if you’re not a Datadog customer, sign up today for a free 14-day trial.