- Product
Infrastructure
Applications
Logs
Security
- Code Security
- Software Composition Analysis
- Static Code Analysis (SAST)
- Runtime Code Analysis (IAST)
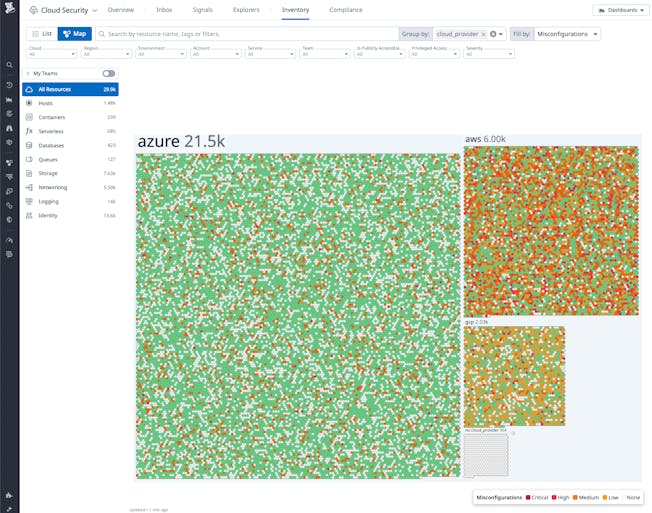
- Cloud Security
- Cloud Security Posture Management
- Cloud Infrastructure Entitlement Management
- Vulnerability Management
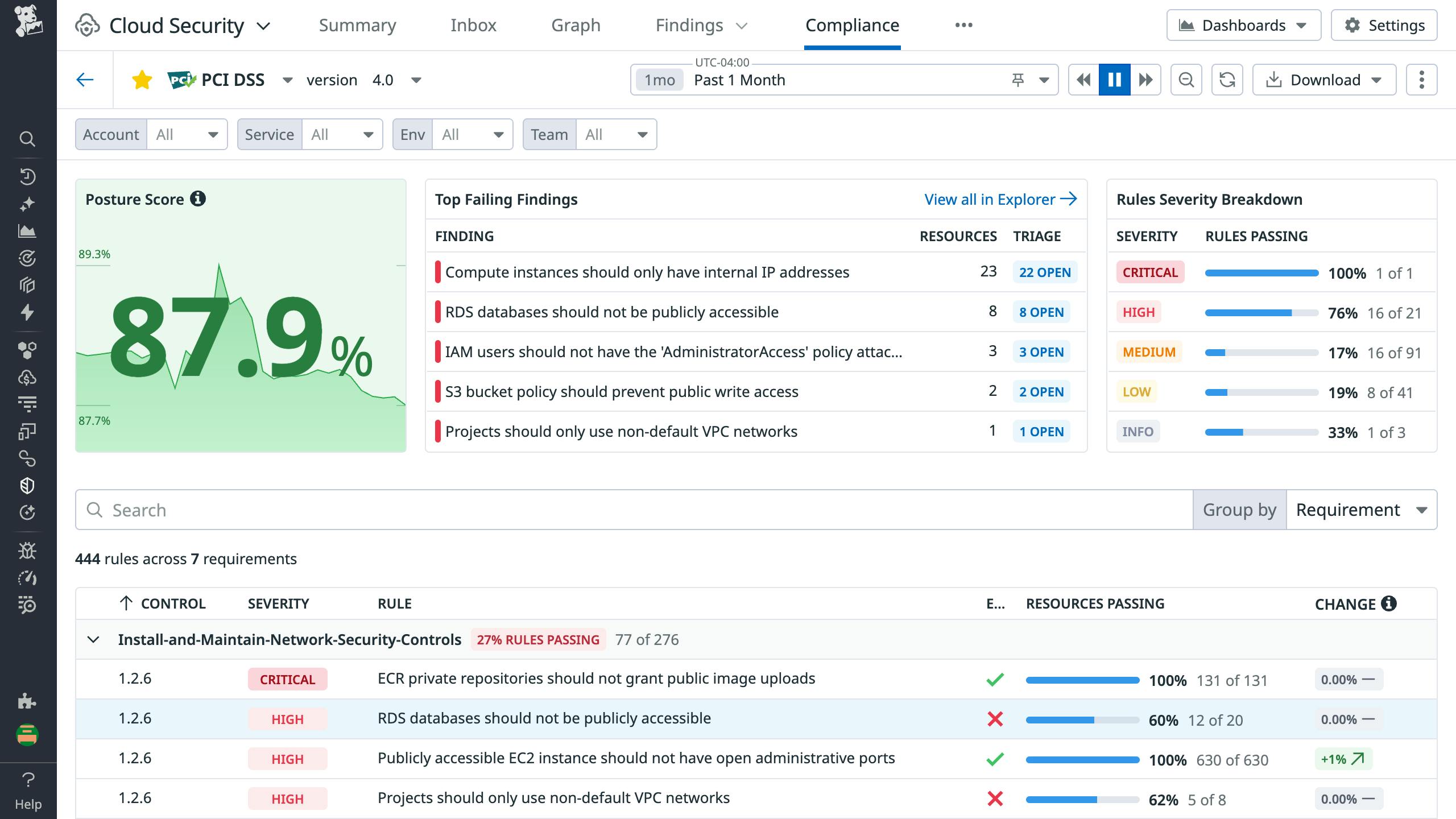
- Compliance
- Cloud SIEM
- Workload Protection
- App and API Protection
- Sensitive Data Scanner
- Security Labs Research
- Open Source Projects
Digital Experience
Software Delivery
Service Management
AI
Platform Capabilities
- Customers
- Pricing
- Solutions
- Financial Services
- Manufacturing & Logistics
- Healthcare/Life Sciences
- Retail/E-Commerce
- Government
- Education
- Media & Entertainment
- Technology
- Gaming
- Amazon Web Services Monitoring
- Azure Monitoring
- Google Cloud Monitoring
- Oracle Cloud Monitoring
- Kubernetes Monitoring
- Red Hat OpenShift
- Pivotal Platform
- OpenAI
- SAP Monitoring
- OpenTelemetry
- Application Security
- Cloud Migration
- Monitoring Consolidation
- Unified Commerce Monitoring
- SOAR
- DevOps
- Shift-Left Testing
- Digital Experience Monitoring
- Security Analytics
- Compliance for CIS Benchmarks
- Hybrid Cloud Monitoring
- IoT Monitoring
- Real-Time BI
- On-Premises Monitoring
- Log Analysis & Correlation
- CNAPP
Industry
Technology
Use Case
- About
- Blog
- Docs
- Login
- Get Started