Classless Inter-Domain Routing (CIDR) is the dominant IP addressing scheme in the modern web. By enabling network engineers to create subnets that encapsulate a set range of IP addresses, CIDR facilitates the flexible and efficient allocation of IPs in virtual private clouds (VPCs) and other networks.
When investigating network traffic, engineers and analysts are often required to scope traffic logs to a particular subnet in order to monitor network errors, latency, or security threats. Datadog Log Management offers an intuitive syntax for CIDR queries, so you can search for logs within a subnet by filtering on its corresponding CIDR block. In this post, we’ll talk about how CIDR works and then show how you can use CIDR notation queries in Datadog Log Management in a variety of troubleshooting, analytics, and security monitoring use cases.
Explore network traffic in Datadog Log Management
Using CIDR blocks to implement supernetting within a VPC helps improve network traffic efficiency by allowing request data to reach the destination address without taking unnecessary paths. CIDR works by defining “blocks” of IP addresses in a fixed range defined by a base address and corresponding subnet mask (a bit operator used to resolve the upper and lower bounds of the range). For example, the CIDR block 10.1.1.32/24 contains 256 unique addresses ranging from 10.10.1.0 to 10.10.1.255.
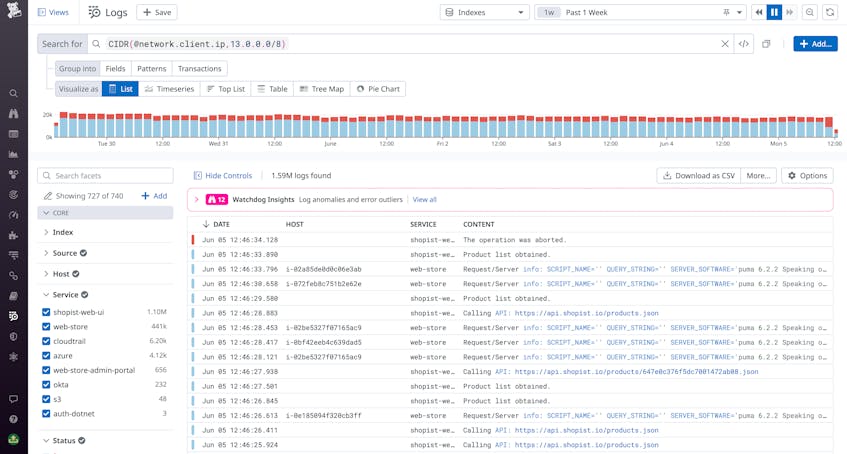
Since CIDR blocks are such a critical part of how organizations define their network topology, network engineers and other analysts often need to filter their traffic logs by CIDR block. Datadog Log Management’s CIDR syntax makes this easy—you can apply CIDR notation filters to your queries simply by using the CIDR() operator and supplying the IP attribute label and one or more CIDR block addresses. For example, let’s say your organization’s VPC has CIDR blocks that define its public and private address spaces, and you want to query the public address space to see which of its IPs are communicating most frequently. The following screenshot shows traffic logs filtered by the CIDR block 13.0.0.0/8 using the network.client.ip attribute. The resulting top list shows the 10 most common IP addresses in these logs.
Next, we’ll discuss some key use cases for CIDR notation queries in security analysis, performance analysis, and troubleshooting scenarios.
Identify traffic from unexpected sources
VPC network traffic logs are a key data source for security analysts looking to observe network communication in their organization’s private networks and root out bad actors. Since CIDR blocks are essentially partitions of all of the valid addresses in these networks, CIDR queries can help security experts spot unauthorized communication from malicious IPs.
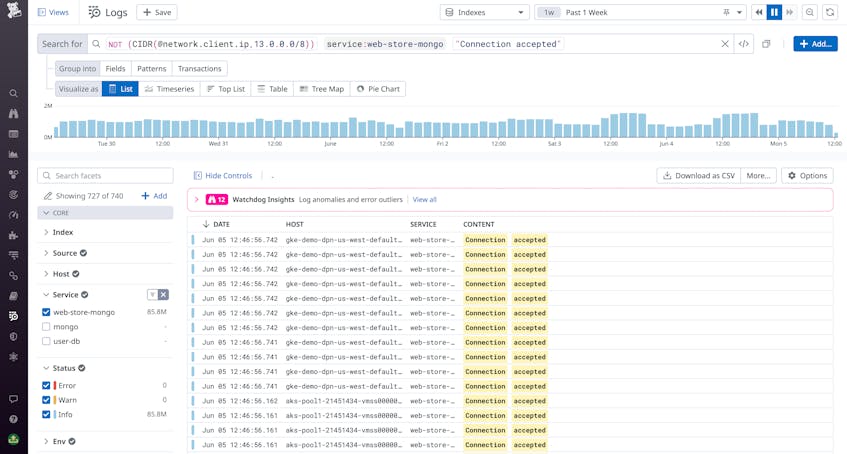
For example, let’s say you have a VPC siloing off a database that stores customer records, alongside a few virtual machines running logic that enables the database to communicate with the rest of your application. The host IP addresses within this VPC are provisioned using a CIDR block. You want to monitor requests to the database from unauthorized sources, so you can query request logs from your database service that don’t originate from an IP within the CIDR block. This ensures that you can easily find any unauthorized traffic and take remediation steps.
Using this query, you can drill into individual log events for suspicious requests and determine if any sensitive data was successfully accessed. By setting up a log monitor, you can automatically notify your team when new suspicious requests occur, so your security engineers can respond quickly and limit the scope of potential breaches.
In another case, you can use a CIDR notation query to spot impossible travel cases, where a single user shows up as logging in from two geographically distinct corporate IPs (defined in CIDR) within an impossible time span. This can indicate that the user might be spoofing one of your corporate IP addresses or has unauthorized access to systems across regions. Simply query for the CIDR block that contains your corporate IPs, then filter the logs by location. Datadog Log Management enriches network traffic logs with geolocation attributes and enables you to create custom geomap visualizations to easily analyze the distribution of origin addresses in your network traffic.
Analyze network performance and spot failures
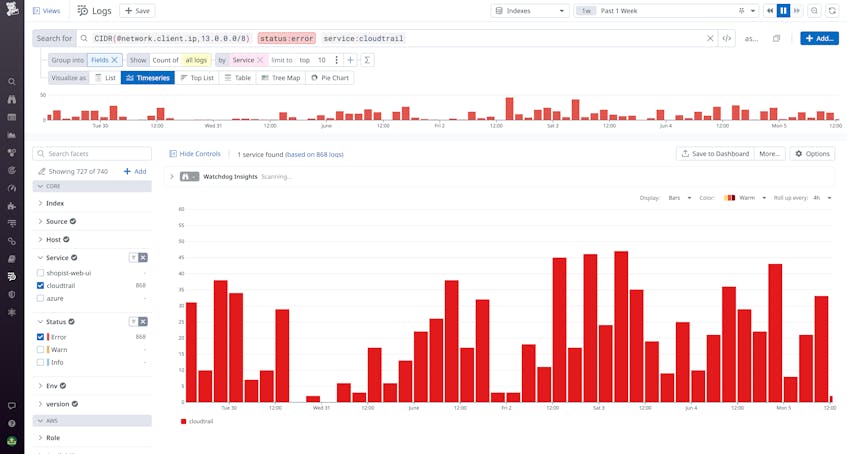
CIDR block queries can also be crucial for network engineers looking to analyze their services’ traffic and spot failed communication. For example, let’s say you have a service with an allocated CIDR block containing its hosts’ IPs, and you want to look for errors in the requests made to that service. By using a CIDR notation query, you can easily surface the request logs for API calls to this service. Then, you can visualize these logs in a timeseries graph to show the error rate for the specified time span. By forming a log-based metric from the query, you can then capture this insight for longer retention and easy integration with dashboard and monitors.
In another case, you might want to see traffic logs from multiple subnets representing a subset of the services running in your VPC. Log Management lets you compose requests with complex Boolean operations to join together CIDR blocks in your queries. For example, let’s say your organization is running an Envoy proxy to handle networking between a set of internal services. You want to investigate network failures occurring in one of these services in HTTP requests due to upstream dependencies. By using CIDR notation in your query, you can easily specify a complex set of relevant IP addresses to filter the logs by the IPs of all these dependencies, as well as HTTP response flags indicating failed communication:
@envoy.access.response_flags:(LH OR UT OR UR OR UC OR DPE) CIDR(@envoy.access.client_address, 10.228.80.0/20, 121.10.1.0/24, 13.10.5.0/29)This query elegantly joins logs from four different subnets representing hundreds of allocated IPs. By using this query, you can surface all of these subnets’ network traffic logs and diagnose any misconfigurations leading to the network failure.
Get started with CIDR queries
As the dominant addressing scheme for modern cloud networks, CIDR is a critical tool for defining network topology. By allowing your network practitioners to build log queries with CIDR block filters, Datadog Log Management makes it easy for DevOps engineers, security analysts, and other personnel to analyze network performance and track malicious traffic. CIDR queries are now generally available for all Log Management customers—for more information, see our documentation. Or, if you’re brand new to Datadog, get started with a 14-day free trial.